Policy Awareness & Compliance
“Guiding Principles That Govern How We Work”
Welcome to NT’s official repository of Company Policies and Processes — your central reference point for understanding how we operate, govern, and deliver with consistency and compliance. This section provides structured access to the latest approved policies, standard operating procedures (SOPs), and process documentation that guide our day-to-day work across all functions.
All documents are developed and maintained in alignment with NT’s Business Excellence Framework, Saudi labor regulations, and international standards such as ISO 9001, 14001, 45001, and 27001. Whether you're seeking clarity on internal procedures, need to align with client expectations, or are simply looking to ensure compliance in your role, this section ensures you always have access to the most up-to-date and authoritative references.
Business, Personnel, Conduct & Human Resources Policies
Document Ref. No.: | SS-TA-PY-07 |
Effective Date: | 31/03/2025 |
Last Review Date: | 31/03/2025 |
Next Review: | 31/03/2026 |
Policy Owner: | Shared Services (Talent Acquisition) |
1. Objective
The purpose of this policy is to establish a formal framework for Talent Acquisition (TA) within NT, ensuring a consistent, transparent, and compliant approach to hiring the right talent. Talent Acquisition is a strategic function aimed at securing individuals whose competencies align with organizational goals, support national employment mandates, and ensure continuity in project and business delivery.
This policy provides a structured pathway for raising manpower requisitions, sourcing candidates, conducting evaluations, and finalizing hires. It emphasizes digitization, role clarity, and accountability at each stage of the recruitment lifecycle. The implementation of this policy shall reduce recruitment cycle time, increase the quality of hires, and enhance adherence to legal, regulatory, and internal governance standards.
2. Scope
This policy applies to all NT departments, business units, and affiliated entities involved in recruiting human capital. It governs recruitment for permanent, contract-based, temporary, project-based, and intern positions across operational and support functions. The scope further extends to recruitment through head-hunters, outsourced agencies, and joint venture channels, subject to compliance with this policy.
The policy is applicable to all categories of candidates: Saudi nationals, local expatriates (with transferable Iqama), and overseas candidates. It is also binding on all stakeholders involved in recruitment, including Requesting / Hiring Managers, Recruiters, Shared Services, Finance, CEO/COO, and System Administrators. However, the policy does not cover the engagement of independent consultants, third-party vendors, or external advisors who fall under procurement or contractual arrangements.
3. Definition
The following definitions are provided to ensure a consistent understanding of key terms used within this policy:
Terms | Definition |
HRMS |
(Human Resource
Management System) The central platform used for all HR-related transactions, including manpower
requisitions, workflow approvals, and employee records.
|
MRF | (Manpower Requisition Form) A system-generated request form raised by a department to initiate the hiring of a new or replacement resource. |
ATS | Applicant Tracking System - A digital platform integrated with the HRMS for managing candidate applications, screening, interviews, evaluations, and records. |
JD | Job Description - A centralized, system-managed digital archive where all approved job descriptions are stored and linked to positions. |
Saudization
|
A government-mandated initiative requiring the
prioritization of Saudi nationals in employment as per the Ministry of Human
Resources and Social Development (MoHRSD)
|
GOSI / Qiwa
|
Official government systems used for
registration and compliance with Saudi social insurance and labour mobility
regulations.
|
4. Roles and Responsibilities
The implementation and enforcement of this policy requires coordinated efforts across several functions. Each stakeholder has a defined responsibility to ensure the Talent Acquisition process remains transparent, compliant, and aligned with NT’s strategic workforce needs.
- Chief Executive Officer (CEO) / Chief Operating Officer (COO): Provide final approval for critical or executive-level recruitment decisions. Ensure strategic alignment between hiring plans and organizational direction.
- Head of Talent Acquisition: Owns the policy and is accountable for its implementation across the organization. Ensures that recruitment practices comply with legal, procedural, and governance standards. Reviews escalations and oversees the continuous improvement of recruitment processes.
- Head of Business Excellence & Governance (BXG): Responsible for maintaining the policy, overseeing version control, and ensuring alignment with NT’s broader policy framework. Supports compliance reviews and policy audits.
- Requesting Managers: Initiate manpower requisitions based on verified operational needs. Collaborate with the Talent Acquisition team to finalize job descriptions and participate in the interview and evaluation process. Ensure that hiring decisions are merit-based and documented.
- Talent Acquisition Team: Manage the end-to-end recruitment lifecycle, from sourcing to offer issuance. Ensure the use of approved tools and systems, maintain recruitment records, and uphold compliance with the policy. Serve as the primary liaison between business units and candidates.
- Finance Department: Validate that budget allocations are available and that proposed hires are within approved financial plans. Approve recruitment requisitions from a cost management perspective.
- HR Shared Services: Facilitate onboarding activities post-offer acceptance. Coordinate employment documentation, statutory registrations (e.g., GOSI, Qiwa), and internal mobilization steps to ensure timely and compliant integration of new hires.
5. Policy Principles
5.1 Manpower Requisition
5.1.1
All recruitment activities within NT must be initiated through a formally approved manpower requisition process. The objective of this requirement is to ensure that all hiring actions are aligned with the organization’s workforce planning strategy, budget allocations, and operational priorities.
5.1.2
Manpower requisitions must be submitted by authorized personnel using the organization’s designated system, ensuring that each request is supported by a defined business need and a validated job description. The approval of requisitions shall follow the predefined governance hierarchy, including Talent Acquisition, Finance, and Executive Management.
5.1.3
Under no circumstances may recruitment proceed—whether internal or external—without prior approval of the manpower requisition. This control mechanism ensures financial discipline, workforce alignment, and accountability in hiring decisions across the organization
5.2 Job Description Management
5.2.1
A clearly defined and approved Job Description (JD) is a mandatory prerequisite for initiating any recruitment process at NT. Job Descriptions serve as the foundational document that outlines the purpose, scope, duties, qualifications, and reporting structure of each position. They are critical to ensuring alignment between organizational needs and the candidate selection process.
5.2.2
All job descriptions must be standardized, reviewed, and maintained within the official JD Repository, which is governed by the Talent Acquisition function. Any creation or modification of a JD must be reviewed for accuracy, consistency, and alignment with organizational structures, and must be formally approved before it can be used in a requisition or posted for sourcing.
5.2.3
Job Descriptions shall not be altered informally or shared outside the approved channels. Ensuring the integrity and version control of JDs is vital to maintaining consistency in recruitment, performance management, and role clarity across the organization.
5.3 Candidate Sourcing Strategies
5.3.1
Candidate sourcing and job advertising activities at NT shall be conducted in a manner that promotes transparency, equal opportunity, and alignment with organizational objectives. All sourcing efforts must reflect the approved job description and be targeted to attract candidates who meet the defined criteria, while also supporting diversity, inclusion, and local employment mandates.
5.3.2
Talent Acquisition shall ensure that all job postings are advertised only through authorized channels, including internal job boards, external portals, social media, approved recruitment agencies, and referral networks. The selection of sourcing channels shall be determined based on the role’s strategic importance, hiring timelines, and target talent demographics.
5.3.3
All job advertisements must adhere to NT's branding guidelines and be free of discriminatory language. The use of any sourcing vendor or external head-hunter must be pre-approved, and their engagement must comply with NT’s vendor governance and data privacy requirements. Unauthorized sourcing or informal referral-based hiring is strictly prohibited.
5.4 Evaluation and Selection
5.4.1
All candidate evaluation and selection activities must be based on merit, consistency, and role-specific criteria defined within the approved job description. NT is committed to ensuring that all hiring decisions are made fairly, transparently, and without bias, in alignment with applicable labour laws and organizational values.
5.4.2
The evaluation process shall incorporate structured interviews and, where appropriate, additional assessments to determine the candidate’s suitability in terms of qualifications, competencies, behavioural alignment, and cultural fit. All evaluations must be documented and recorded through approved systems, ensuring traceability and accountability throughout the selection process.
5.4.3
Selection decisions must be supported by a panel-based consensus and must not be based on informal recommendations or unrecorded assessments. The final hiring decision is the responsibility of the authorized hiring authority and must be substantiated by objective assessment outcomes and reference verification. Any deviation from the approved evaluation procedure must be formally justified and approved by the Head of Talent Acquisition.
5.5 Interview Management
5.5.1
Interviewing is a formal and structured component of the candidate evaluation process at NT. All interviews must be conducted in a manner that upholds the principles of fairness, confidentiality, and professionalism, while ensuring compliance with applicable legal and organizational standards.
5.5.2
Interview panels shall be constituted based on the nature and level of the role, and must include at least one subject matter expert, the hiring manager, and a representative from Talent Acquisition. All interviewers are expected to be briefed on the evaluation criteria and must avoid any form of discriminatory or subjective questioning. Standardized interview templates and scoring rubrics, maintained by the Talent Acquisition team, must be used to ensure consistency across candidates.
5.5.3
The scheduling, conduct, and documentation of interviews must be managed through the designated Applicant Tracking System (ATS) or equivalent approved platform. Informal, undocumented interviews are not permitted. Interview outcomes shall be documented and retained as part of the recruitment record for audit and compliance purposes.
5.6 Reference Checks and Background Verification
5.6.1
Reference checks and background verifications are mandatory steps in NT’s recruitment process and serve as essential risk mitigation measures. These checks ensure that all selected candidates possess the integrity, professional history, and qualifications claimed during the recruitment process.
5.6.2
All reference checks must be conducted by the Talent Acquisition team or their designated representative and must include verification with at least two professional referees, preferably former direct supervisors. The feedback obtained must be relevant to the role under consideration and documented as part of the candidate’s assessment record. Informal or undocumented references shall not be considered valid.
5.6.3
Where applicable, background verification may include, but is not limited to, confirmation of academic qualifications, employment history, criminal record checks, professional certifications, and regulatory clearances. All background checks must comply with local laws and NT’s data privacy policy. A candidate may only proceed to offer issuance upon successful completion of both reference and background verification processes. Any adverse findings must be escalated to the Head of Talent Acquisition and, if necessary, Executive Management for final decision.
5.7 Decision Making Process
The decision-making process for candidates who have been interviewed for a job position should follow these steps:
5.7.1
The hiring manager or the interview panel should review the assessment results and compare them with the job requirements and selection criteria.
5.7.2
The hiring manager or the interview panel should rank the candidates based on their overall performance and suitability for the role, taking into account their qualifications, skills, experience, fit and potential.
5.7.3
The hiring manager or the interview panel should verify the references and background checks of the top candidates and confirm their availability and interest in the position.
5.7.4
The hiring manager or the interview panel should make a final decision and select the best candidate for the job offer, based on the evidence and data collected throughout the hiring process.
5.7.5
The hiring manager or the interview panel should notify the successful candidate and discuss the terms and conditions of the employment contract, as well as the start date and orientation plan.
5.7.6
The hiring manager or the interview panel should also inform the unsuccessful candidates of the outcome and thank them for their participation and interest in the organization. They should also provide them with an opportunity to ask for feedback and learn from their experience.
5.8 Offer Management and Hiring Decision
5.8.1
The issuance of an employment offer at NT represents the formal conclusion of the candidate selection process and must be based on objective evaluation outcomes, validated credentials, and successful completion of all mandatory checks. No offer may be extended without the prior approval of the designated hiring authority and in accordance with the organization’s recruitment governance.
5.8.2
All employment offers must be prepared and issued through the approved HR system or official correspondence channels, ensuring consistency with approved compensation structures, employment terms, and contractual conditions. Offers must clearly specify role details, grade, reporting line, location, and joining date, and must adhere to NT’s internal salary guidelines and authorized budget allocations.
5.8.3
Verbal commitments or informal confirmations of selection are strictly prohibited. The Talent Acquisition team shall ensure that all offer documentation is reviewed, approved, and logged appropriately before being shared with the candidate. Any counter offers, changes to terms, or exceptions to standard policies must be documented and escalated to the Head of Shared Services (Talent Acquisition) and, where applicable, to Executive Management for approval.
5.9 Onboarding and Transition to HR Operations
5.9.1
Upon formal acceptance of the employment offer by the selected candidate, responsibility for the onboarding process transitions from the Talent Acquisition function to HR Operations and Shared Services. This handover must be seamless, structured, and fully documented to ensure consistent and compliant onboarding experience.
5.9.2
All candidate records, approvals, and documentation relevant to the recruitment process must be compiled and transferred to the HR Operations team through the designated system. This includes the signed offer letter, approved Manpower Requisition, interview evaluations, reference check outcomes, and any supporting verification documents.
5.9.3
The onboarding process, including medical insurance registration, GOSI/Qiwa formalities, asset allocation, induction scheduling, and system access provisioning, shall be carried out in accordance with NT’s approved onboarding procedures. The Shared Services team shall ensure that all post-selection activities are completed prior to the candidate’s official start date and that the employee is fully compliant with internal and statutory requirements upon deployment.
6. Compliance and Legal Considerations
6.1 Equal Employment Opportunity
6.1.1
The recruitment department is committed to ensuring equal employment opportunity for all applicants and employees in accordance with the laws and regulations of the Kingdom of Saudi Arabia. The recruitment department will not discriminate on the basis of race, color, religion, gender, age, disability, national origin, or any other protected characteristic, except where it is required by law or necessary for the effective performance of the job. The recruitment department will also adhere to the Saudization requirements and objectives set by the Ministry of Human Resources and Social Development and strive to recruit, develop, and retain qualified Saudi nationals for various positions within the organization. The recruitment department will implement fair and transparent procedures and criteria for selecting, assessing, and hiring candidates based on their qualifications, skills, and suitability for the job. The recruitment department will also foster a culture of diversity and inclusion within the organization and provide equal opportunities for training, development, promotion, and recognition for all employees.
6.2 Data Privacy and Security
The recruitment department is committed to protecting the personal data and privacy of all applicants and employees in accordance with the laws and regulations of the Kingdom of Saudi Arabia and the international best practices.
6.2.1
The recruitment department will collect, use, store, disclose, and dispose of personal data only for legitimate purposes related to the recruitment and employment processes.
6.2.2
The recruitment department will obtain consent from the data subjects before collecting and processing their personal data, unless it is otherwise permitted or required by law.
6.2.3
The recruitment department will also inform the data subjects about their rights and obligations regarding their personal data, such as the right to access, correct, delete, or object to the processing of their data.
6.2.4
The recruitment department will ensure that the personal data is accurate, relevant, complete, and up-to-date, and that it is not retained longer than necessary.
6.2.5
The recruitment department will also implement appropriate technical and organizational measures to safeguard the personal data from unauthorized access, use, disclosure, alteration, or loss.
6.2.6
The recruitment department will report any data breaches or incidents to the relevant authorities and the data subjects as soon as possible.
6.2.7
The recruitment department will also comply with any requests, inquiries, or complaints from the data subjects or the authorities regarding their personal data.
6.2.8
The recruitment department will review and update this policy periodically to reflect any changes in the laws, regulations, or best practices.
6.3 Recordkeeping Requirements
The recruitment department will maintain accurate and complete records of all its activities and processes, such as job descriptions, vacancy announcements, applications, assessments, interviews, selection decisions, reference checks, employment contracts, and orientation materials.
6.3.1
The records will be stored in a secure and confidential manner, either electronically or in paper form, and will be accessible only to authorized personnel.
6.3.2
The records will be retained for at least six months after the completion of the recruitment process, or longer if required by law or contractual obligations.
6.3.3
The records will be disposed of securely and in compliance with the data protection laws and regulations.
6.3.4
The recruitment department will also keep track of any metrics, indicators, or statistics related to its performance, such as time-to-hire, cost-per-hire, turnover rate, diversity rate, or candidate satisfaction.
6.3.5
The recruitment department will use these data to evaluate its effectiveness and efficiency, identify areas of improvement, and report on its achievements and challenges.
7. Continuous Improvement
7.1
NT recognizes that Talent Acquisition is a dynamic and evolving function that must continuously adapt to internal business needs, market conditions, technological advancements, and regulatory requirements. As such, a culture of continuous improvement shall be embedded within all recruitment-related activities to enhance efficiency, responsiveness, and quality of hires.
7.2
The Talent Acquisition team, in coordination with the Business Excellence & Governance (BXG) department, shall periodically assess the effectiveness of recruitment strategies, sourcing methods, evaluation tools, and system workflows. Feedback from candidates, hiring managers, and recruitment stakeholders shall be collected and analysed to identify improvement opportunities and address pain points in the end-to-end process.
7.3
Key performance indicators (KPIs), compliance findings, and process reviews will serve as inputs for process enhancements, system configuration updates, training interventions, and policy refinements. Improvement actions shall be documented, tracked, and reviewed as part of the broader governance and reporting framework to ensure accountability and measurable outcomes.
7.4
Any significant changes to recruitment procedures resulting from these improvement initiatives shall be reflected in the supporting SOPs and communicated to all relevant users through formal training and internal communications.
8. References
This policy shall be read in conjunction with NT’s broader governance framework and applicable legal and regulatory requirements. The following references provide the foundation and contextual alignment for the principles outlined in this document:
- NT Interview Guidelines Document: Establishes standardized practices for conducting interviews, including panel composition, question formulation, candidate evaluation, and compliance with anti-discrimination laws.
- NT Recruitment and Onboarding SOP: Provides detailed procedural guidance for each stage of the talent acquisition lifecycle, including requisition processing, candidate screening, interview coordination, and onboarding.
- NT Policy and Process Lifecycle Management Policy: Governs the development, approval, and maintenance of all policy documents within the organization.
Document Ref. No.: | SS-TA-PY-07 | Version No.: | 2.0 |
Issue Date: | 31/03/2025 | Last Review Date: | 31/03/2025 |
Policy Owner: | Shared Services (Talent Acquisition) | Next Review: | 31/03/2026 |
1. Introduction
Norconsult Telematics (NT) is committed to fostering a professional, respectful, and legally compliant work environment. This Code of Conduct serves as a foundational guide for all employees, contractors, executives, and affiliates of NT, outlining the behavioural expectations and ethical standards required in all business interactions. The policy is designed to ensure alignment with Saudi Arabian Labor Law, including the Saudi Labour Law issued by Royal Decree No. M/51 and amended regulations, as well as applicable KSA-specific compliance requirements. Everyone at NT, regardless of position, has an equal responsibility to adhere to this Code. It promotes a safe, inclusive, and productive workplace where diversity is respected, and professionalism is upheld. Violations of the Code may result in disciplinary action. By fostering accountability and integrity, this policy ensures NT continues to operate with transparency and trust.
1.1 Scope
1.1.1
Applies to all NT employees, contractors, consultants, and executives working under any form of agreement or engagement.
1.1.2
Covers behavior both within and outside the workplace, including remote settings, online environments, and while representing NT at external functions.
1.1.3
Ensures all individuals, regardless of rank or role, are subject to the same behavioral and accountability standards.
1.1.4
Aligns with Saudi Labour Law, local governance requirements, and NT’s internal compliance framework.
1.1.5
Reinforces a unified approach to professional conduct, ethics, and legal responsibility.
1.1.6
Applies to all work sites and subsidiaries under NT's operational umbrella.
1.2 Roles and Responsibilities
1.2.1
All personnel must comply with the policy and report any observed or suspected violations.
1.2.2
Supervisors and Managers are responsible for ensuring their teams understand and implement the policy.
1.2.3
Human Resources must provide ongoing training, maintain compliance documentation, and manage investigations when needed.
1.2.4
Top Management is accountable for setting the tone and upholding ethical leadership practices.
1.2.5
Contractors and temporary staff must adhere to this Code as a condition of their contract.
1.2.6
Everyone shares the responsibility to create a respectful, ethical, and inclusive workplace.
1.3 References
1.3.1
Saudi Labour Law (Royal Decree No. M/51)
1.3.2
Personal Data Protection Law (PDPL)
1.3.4
Anti-Corruption Regulations (Nazaha Guidelines)
1.3.5
NT Internal Policies and Procedures
2. Our Core Principles
This Code is underpinned by key principles that guide conduct and decision-making across the organization. Integrity ensures that all actions are performed ethically and honestly. Compliance means observing all applicable laws and NT policies, including KSA regulatory frameworks. Respect promotes inclusive behaviour and discourages any form of harassment or discrimination, aligning with Saudi Arabia's anti-discrimination mandates.
Accountability
reinforces responsibility for one’s actions, while confidentiality demands that
personal and company-sensitive information is protected at all times. These
principles are not just guidelines but essential values that support a positive
workplace culture and stakeholder trust. Employees must model these principles
daily, whether in internal collaboration or external dealings. Commitment to
these values strengthens NT's reputation and promotes operational excellence.
These principles are reinforced through leadership, training, and regular
policy reviews.
Key Points:
- Uphold honesty, ethical conduct, and legal compliance in all interactions.
- Respect individual dignity, culture, and perspectives in the workplace.
- Avoid and report unethical conduct, discrimination, or unfair treatment.
- Exercise confidentiality when handling sensitive information.
- Embrace accountability and transparency in daily work.
- Reinforce ethical standards through training and leadership modelling
3. Professional Conduct Expectations
All individuals engaged with NT are expected to exhibit professional conduct that reflects well on the organization. This includes punctuality, reliability, ethical judgment, and respectful communication in accordance with Saudi Labor Law provisions. Employees must refrain from actions that may cause reputational damage or internal conflict. Conduct extends beyond the physical workplace and includes online interactions and representations. It is essential to remain impartial, avoid favouritism, and act in the best interest of NT at all times.
Misconduct, including abusive language, insubordination, or misuse of authority, undermines team morale and will not be tolerated. Maintaining professionalism promotes mutual respect and a safe working environment for everyone. Where uncertain, employees should seek guidance to ensure their behaviour aligns with NT’s standards and national legal expectations.
Key Points:
- Demonstrate professionalism, punctuality, and respectful communication.
- Refrain from harassment, misconduct, or misuse of authority.
- Maintain ethical behaviour in online and offline interactions.
- Comply with organizational rules and Saudi legal requirements.
- Represent NT with integrity during official engagements.
- Seek guidance when unsure about conduct expectations
4. Conflict of Interest
A conflict of interest occurs when personal interests compromise or have the potential to compromise professional judgment and objectivity. At NT, employees must avoid situations where their decisions could be influenced by external relationships or financial interests. This includes working with or awarding contracts to relatives or investing in competitor firms without disclosure. Conflicts may arise intentionally or unintentionally; however, both must be reported to a supervisor or HR immediately.
Transparency in declaring potential conflicts ensures fairness and protects organizational integrity. Managers are responsible for resolving conflicts swiftly and fairly to avoid any perception of bias. Failure to declare a conflict of interest may result in disciplinary action, including termination as per Saudi Labour Law regulations.
Key Points:
- Avoid situations where personal interest may compromise objectivity.
- Disclose all potential or actual conflicts to management.
- Refrain from making decisions that benefit family or external relations.
- Transparency builds trust and prevents organizational bias.
- Non-disclosure may lead to corrective or legal consequences.
- Managers must resolve conflicts promptly and fairly.
5. External Employment and Directorships
NT recognizes the right of Saudi national employees, to engage in external employment, consulting, or board roles. However, such engagements must not interfere with the performance of NT duties or create a conflict of interest. In accordance with KSA labour policies, prior written approval from a supervisor is required before accepting any external role that may intersect with NT’s operations. Individuals must not use NT resources, branding, or confidential information in connection with their external work. The reputation and operational effectiveness of NT must be preserved at all times. If external commitments compromise job performance or raise ethical concerns, the employee may be asked to resign from such roles. Periodic declarations may be requested to ensure ongoing compliance. This promotes transparency and organizational trust.
Key Points:
- Notify NT management before taking any outside role or board position.
- Avoid external roles that conflict with NT duties or performance.
- Do not use NT branding or data for external work.
- Maintain separation between NT work and outside obligations.
- Submit periodic declarations as required.
- External commitments must not jeopardize NT operations or image.
6. Relationships with Clients and Suppliers
Professional boundaries must be maintained in all dealings with NT clients, vendors, and suppliers. Employees must avoid favouritism, self-interest, or preferential treatment that may arise from financial investments, gifts, or close personal relationships. All business decisions should be made objectively and in NT's best interest. Engaging in transactions that benefit an employee personally, without disclosure, is strictly prohibited.
Employees involved in procurement or vendor selection must follow NT’s procurement policies to ensure fairness and transparency, in alignment with fair competition and anti-bribery standards in KSA. The appearance of impropriety can be just as damaging as actual misconduct; therefore, caution and honesty are essential. Any potential conflict must be disclosed immediately. Failing to do so may result in serious disciplinary consequences.
Key Points:
- Maintain professional distance in vendor or client relationships.
- Refrain from favouritism, undue influence, or preferential treatment.
- Disclose any financial or personal interests tied to business dealings.
- Follow NT procurement protocols to ensure transparency.
- Avoid actions that could damage NT's credibility.
- Declare conflicts immediately to avoid ethical violations.
7. Gifts, Hospitality, and Entertainment
To maintain impartiality and avoid any perception of impropriety, NT employees must not accept or offer gifts, hospitality, or entertainment that could influence business decisions. Modest gestures may be acceptable in some cases (e.g., a token gift during cultural festivals), but lavish or frequent offerings must be declined or reported. Employees should consult their manager when in doubt about a gift’s appropriateness.
All reportable items must be documented, especially those received from clients or contractors. Accepting high-value gifts without disclosure may lead to disciplinary action. Giving or receiving bribes, cash equivalents, or items of significant value violates NT's anti-corruption policy and applicable KSA regulations, including those outlined by the National Anti-Corruption Commission (Nazaha). Transparency and good judgment must guide all such interactions.
Key Points:
- Accept only nominal gifts that do not influence business decisions.
- Report all gifts or entertainment offers to your supervisor.
- Decline expensive or frequent gifts, especially during contract periods.
- Avoid giving or receiving bribes or items of high value.
- Comply with Nazaha anti-corruption laws and internal protocols.
- When unsure, always err on the side of transparency.
8. Use of Company Assets
All physical, financial, and digital resources provided by NT are to be used solely for legitimate business purposes. Employees must not misuse or abuse company assets for personal benefit or unauthorized activities. This includes office equipment, software licenses, vehicles, or intellectual property. Misuse may include excessive personal use of company internet, unauthorized installations, or lending equipment to others. Individuals are responsible for safeguarding assets under their control and reporting any damage, loss, or misuse.
Unauthorized use of NT funds, including fraudulent expense claims, will result in disciplinary action. Proper stewardship of company resources reflects accountability and professionalism. Periodic audits may be conducted to ensure compliance in line with KSA corporate governance frameworks.
Key Points:
- Use NT property, vehicles, and tools for business purposes only.
- Safeguard equipment and digital resources under your control.
- Report misuse, theft, or damage of any company asset.
- Never use NT funds or licenses for personal gain.
- Comply with software usage rights and security protocols.
- Internal audits may be conducted to ensure accountability.
9. Accurate Records and Communication
Accurate, truthful, and timely documentation is essential for NT’s operational success and legal compliance. Employees involved in financial reporting, project documentation, or customer records must ensure all data is correct and free of misrepresentation. Any attempt to falsify documents, inflate results, or hide information is strictly prohibited and may lead to legal consequences.
Internal and external communications should be professional, respectful, and aligned with NT's communication standards and KSA's regulations on commercial and labour documentation. Unauthorized disclosure of company information, misleading marketing, or impersonation is not tolerated. All reports, invoices, and statements should reflect actual conditions and events. Managers must ensure their teams understand the importance of documentation integrity.
Key Points:
- Maintain accurate records across all functions (HR, Finance, Projects).
- Avoid falsifying documents or misrepresenting information.
- Ensure communications reflect actual performance and conditions.
- Uphold NT’s integrity in all public or client-facing messages.
- Managers must lead by example in reporting transparency.
- Align all documentation with Saudi business regulations.
10. Privacy, Confidentiality, and Data Protection
NT is committed to protecting the privacy and confidentiality of all personal, client, and corporate data in accordance with Saudi Arabia's Personal Data Protection Law (PDPL). Employees must collect only the data necessary for business purposes, store it securely, and share it only with authorized personnel. Confidential information must not be discussed in public areas or disclosed without consent. Any data breach, loss, or unauthorized access must be reported immediately to IT and HR.
Employees must follow all internal data protection protocols, including password management and secure document storage. Regular training will be provided to ensure awareness. Mishandling of data may result in both disciplinary and legal action.
Key Points:
- Follow Saudi PDPL requirements for data use and protection.
- Only collect and store necessary business-related personal data.
- Share confidential data only with authorized personnel.
- Secure devices and documents to prevent unauthorized access.
- Report breaches immediately to IT and HR.
- Participate in data protection training regularly.
11. Respect, Diversity, and Inclusion
NT celebrates diversity and promotes an inclusive culture that respects all individuals, in alignment with KSA's national human rights frameworks for workforce empowerment. Discrimination, harassment, or exclusionary behaviour is strictly prohibited. Inclusive practices ensure all voices are heard, valued, and empowered to contribute. Managers must foster team environments that encourage collaboration, equity, and respect.
Language and behaviour must be free of bias, slurs, or stereotypes. NT upholds the principles of workplace equality and integrates cultural competency into training and leadership practices. Nationals and expatriates alike are entitled to fair treatment. Breaches of inclusion standards are taken seriously and addressed promptly.
Key Points:
- Foster inclusion and respect for all cultures and backgrounds.
- Eliminate discriminatory language or behaviour.
- Ensure equal access to opportunities for all staff.
- Address and report incidents of bias or harassment.
- Managers should encourage diverse participation and respectful dialogue.
12. Reporting and Whistleblower Protection
NT encourages everyone to report misconduct, unethical behaviour, or breaches of this Code in good faith. Reports may be made to direct supervisors, HR, or through anonymous email to nthr@ntww.com. The identity of whistleblowers will be protected to the fullest extent practical, and retaliation of any kind is strictly prohibited. All reports are thoroughly and confidentially investigated. If misconduct is confirmed, appropriate corrective actions will be taken, including disciplinary measures or legal reporting if required. Whistleblower protections align with Saudi Arabian anti-corruption and labour transparency mandates. NT supports a culture where accountability and ethical behaviour are prioritized. Regular awareness sessions are conducted to promote safe reporting practices.
Whistleblower protection is a fundamental aspect of our ethical framework. NT encourages all individuals to speak up without fear if they witness or suspect any unethical, illegal, or non-compliant activity. Whistleblowers are not only protected from retaliation but are supported throughout the reporting and investigation process. Reports can be made confidentially or anonymously, and all disclosures are taken seriously and reviewed promptly. NT upholds transparency and confidentiality in every case to ensure trust and participation. The goal is to maintain integrity while safeguarding the rights of those who come forward.
Key Points:
- Reports can be submitted directly to your manager, Program Manager, HR, or anonymously to: nthr@ntww.com.
- Whistleblowers' identities will remain confidential unless disclosure is legally required.
- NT prohibits retaliation or victimization of individuals who raise concerns in good faith.
- All complaints will be investigated fairly, objectively, and in a timely manner.
- NT encourages documentation of observations to support investigations.
- The whistleblower will be informed of the outcome wherever appropriate.
- Awareness training and posters will be maintained to ensure all employees know how to report concerns
13. Disciplinary Action
Violations of this Code may result in disciplinary action depending on the nature and severity of the breach. Actions range from verbal or written warnings to suspension, demotion, or termination in accordance with Saudi Labour Law. Legal consequences may also apply for serious violations such as fraud or harassment. All allegations are investigated fairly, confidentially, and in accordance with applicable KSA employment law and NT's internal procedures.
Employees will have the opportunity to respond to allegations before decisions are made. Managers are responsible for documenting all violations and consulting HR before initiating any action. The aim is not only to correct behaviour but to prevent recurrence and uphold NT’s values. Repeated or wilful violations indicate incompatibility with NT's workplace culture.
Key Points:
- NT uses a fair and consistent process to handle misconduct.
- Disciplinary measures include warnings, suspension, or dismissal.
- Legal action may be pursued for fraud, violence, or severe breaches.
- All reports are investigated confidentially and without bias.
- Employees have the right to respond before decisions are made.
- Documentation and HR consultation are mandatory before action.
14. Acknowledgment and Acceptance
All employees, contractors, and representatives of NT must read, understand, and comply with this Code of Conduct. By continuing your association with NT, you acknowledge your responsibility to uphold the principles and behaviours outlined herein. A electronically acknowledged declaration may be requested annually or upon policy updates.
Ignorance
of the Code will not be accepted as an excuse for violations. It is your duty
to seek clarification if any part of this document is unclear. Leadership is
expected to model the Code visibly and consistently. Updates will be
communicated promptly and made available through internal systems. This Code is
a living document, integral to NT’s culture and operational success. For any
queries regarding this policy, please get in touch with the HR Dept. at nthr@ntww.com
In progress
Policy Name |
Employee
Training and Development Policy
| Document Ref. No | SS-HR-PY-03 |
Version Number | 1.0 | Issue Date | 15/03/2025 |
Access Level: | Limited to NT Employees | Next Review | 31/03/2025 |
1. Purpose
This policy establishes the framework for planning, implementing, and managing employee training and development activities within NT. The objective is to ensure that employees possess the knowledge, skills, and competencies necessary to perform their roles effectively, adapt to evolving business requirements, and contribute to organizational excellence.
Training and development initiatives are designed to align with NT’s strategic goals, comply with Saudi Labour Law requirements, and promote a culture of continuous learning and professional growth.
1.1 Scope
This policy applies to all permanent NT employees. It covers all types of learning and development activities such as orientation, on-the-job training, e-learning, professional certifications, workshops, seminars, conferences, and leadership programs.
The scope includes both mandatory compliance training and optional developmental programs that enhance employee performance, career progression, and organizational capability.
1.2 References
- Saudi Labour Law – Provisions related to employee rights, training, and development.
- NT Strategic Plan – Organizational goals and workforce capability development strategies.
- ISO 9001:2015 – Quality Management System requirements related to competence and training (Clause 7.2)
2. Roles and Responsibilities
2.1 Human Resources (HR) Department
Responsible for identifying training needs in consultation with department heads, designing training plans, coordinating delivery, and maintaining training records.
2.2 Department Heads
Responsible for nominating employees for relevant training, ensuring participation, and monitoring post-training performance improvements.
2.3 Employees
Responsible for actively participating in training programs, applying acquired skills in their roles, and providing feedback on training effectiveness.
3. Policy Statement
NT is committed to providing equitable access to training and development opportunities that support employees’ current roles and future career aspirations. All training programs shall be designed and delivered in accordance with recognized industry standards, with measurable objectives and outcomes.
Training will be prioritized based on business needs, job requirements, and individual performance assessments, ensuring optimal allocation of resources while minimizing impact on day-to-day operational activities.
4. Training Needs Identification
Training needs will be identified through a combination of performance appraisals, skills gap analysis, strategic business objectives, compliance requirements, and employee feedback. Eligibility criteria to qualify for training are as follows:
4.1 General Criteria
- Employees must have completed a minimum of 6 months with the company.
- A performance rating of 3 or higher in the annual review is required.
- Priority
is given to project-critical roles, high performers, and roles with skill gaps.
4.2 Special Exceptions
- Project Managers may recommend specific training to address skill deficiencies.
- Client-nominated employees are eligible regardless of internal performance rating.
- Employees under skill-development probation can be nominated, subject to post-training re-evaluation.
5. Types of Trainings
- Mandatory Training: Compliance-related, health and safety, and regulatory requirements.
- Job-Specific Training: Skills and knowledge necessary for effective job performance.
- Professional Development: Courses, certifications, and programs for career growth.
- Leadership Development: Programs aimed at preparing employees for managerial roles.
6. Training Delivery Methods
Training may be delivered via in-person sessions, online learning platforms, blended learning, workshops, mentoring, job rotations, or external training providers. Where applicable, NT will leverage the Learning Management System (LMS) to track enrolment, completion rates, and training outcomes.
6.1 Online Training (e.g., LinkedIn Learning / Coursera:
- Valid for all eligible categories.
- Access is granted for a maximum of 6 months.
- Completion of assigned courses is mandatory before undertaking additional learning.
6.2 Specialized Training (Classroom / Instructor-led:
- Reserved for Competence Building and High-Performance categories.
- Includes certifications, client-specific workshops, or advanced project methodologies.
- May be conducted locally or internationally depending on training value and availability.
6.3 Conferences and Seminars:
- Offered selectively to strategic resources.
- Participation must yield learning outputs such as internal presentations or summaries.
7. Evaluation of Training Effectiveness
Post-training evaluation will be conducted to measure learning outcomes, behavioural changes, and business impact. Evaluation methods will include participant feedback forms, knowledge assessments, and performance reviews.
Results of evaluations will be analysed by HR and shared with relevant department heads to ensure continuous improvement of training programs.
8.0 Records and Documentation
All training records, including attendance, completion certificates, and evaluation results, will be maintained digitally in NT’s HRMS/LMS system.
All records are stored in digital format and updated as part of our Management Review Cycle. It is the responsibility of each process owner to ensure that these documents remain up to date and are available during audits or upon request.
9.0 Compliance
This policy will comply with Saudi Labour Law and other relevant regulations. Any updates in legal requirements will be reflected in subsequent revisions of the policy.
10.0 Review and Amendments
The policy will be reviewed annually by the HR Department in collaboration with the Business Excellence & Governance function to ensure relevance, compliance, and effectiveness.
Amendments will be communicated to all employees via official channels and updated on the corporate intranet.
Policy Name |
Work
Equipment and Digital Services Use Policy
| Document Ref. No | SS-HR-PY-03 |
Version Number | 2.0 | Issue Date | 15/03/2025 |
Access Level: | Limited to NT Employees | Next Review | 31/03/2025 |
1. Introduction
This policy governs the use, care, and responsibility associated with all company-issued equipment, including laptops, mobile phones, tablets, PPE kits, SIM cards, routers, and related digital or protective tools. These resources are essential for daily operations and project execution, and are provided to enhance employee performance, maintain safety, and support communication. The policy ensures responsible use, minimizes risk, and upholds data protection laws applicable in the Kingdom of Saudi Arabia.
NT relies on a wide range of technological and protective tools to support its service delivery model. From communication devices and IT equipment to safety gear required in field environments, these assets remain the property of the company and must be used with integrity and accountability. This document defines the terms of issuance, acceptable usage, misuse, and return of such resources.
1.1 Scope
- Applies to all NT employees, contractors, and authorized personnel issued with equipment.
- Covers IT hardware (laptops, tablets, phones), telecom services (SIMs, routers), and safety gear (PPE).
- Applicable across all NT project sites, offices, and remote working environments.
1.2 Roles and Responsibilities
1. Employees
are responsible for ensuring that company-issued equipment is used appropriately, securely, and only for business-related purposes. They are also responsible for timely reporting of issues or damage.
2. IT Department
is responsible for provisioning, asset tagging, tracking, repairing, and decommissioning all IT-related equipment. It also enforces software compliance and cybersecurity standards.
3. Admin & HSE Teams
handle issuance, training, and condition assessments for PPE kits and coordinate replacements as required.
4. Finance Department
manages telecom billing controls and recovers cost in case of abnormal usage or loss.
Legal and Regulatory References:
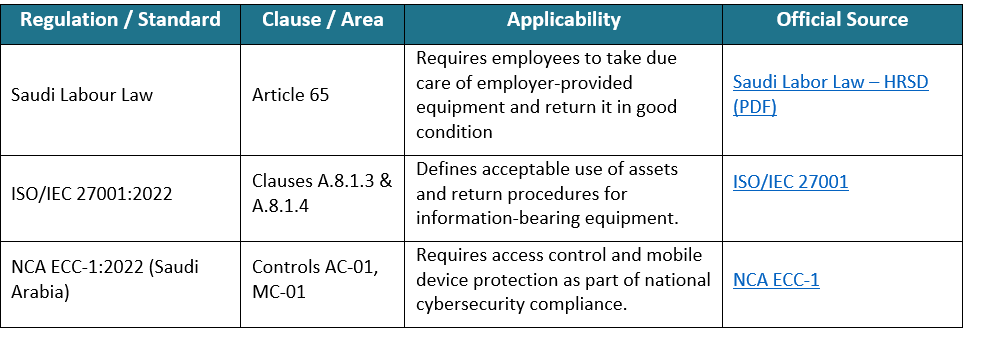

2. Issuance and Assignment
NT ensures that equipment issuance is streamlined and transparent. At the start of employment or when transitioning into a new role, employees may be eligible for company-provided equipment. The assignment is role-based and prioritized for individuals whose work demands continuous access to digital tools, connectivity, or physical safety gear. Issuance is coordinated by the IT or Admin team depending on the asset type and is subject to inventory availability and management approval.
2.1 Initial Issuance Protocol:
- Equipment needs are reviewed during onboarding or upon departmental request.
- Items are prepared and tagged with asset IDs by the IT or Admin team.
- Employees receive a briefing on proper usage and care guidelines.
- A checklist is signed confirming receipt, condition, and serial number of issued items.
Company-provided equipment is issued based on an individual's job role, project requirements, or travel needs. Prior approval from the relevant department head is mandatory. The IT or Admin team maintains a centralized inventory of all assigned equipment, including serial numbers, device IDs, and usernames.
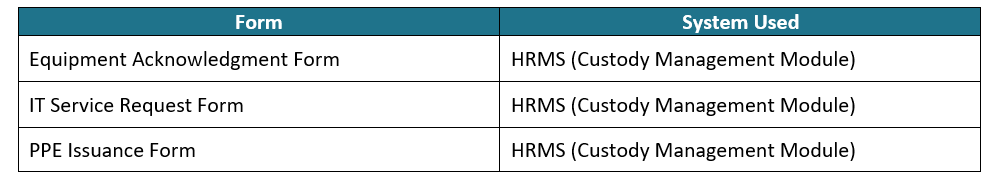
2.2 Process:
- A formal request must be submitted via a Service Request Form.
- Department Heads validate the need and recommend issuance.
- Users must sign an Equipment Acknowledgment Form confirming receipt and responsibilities.
- Equipment is assigned for the duration of the project or employment term and must be returned on demand.
3. Acceptable Use Guidelines
Users must use company-issued devices strictly for performing business activities. All usage is subject to internal audit and must conform to NT's security, ethical, and operational standards. Inappropriate or unauthorized activities may result in suspension of access or disciplinary action.
3.1 Permitted Activities
- Accessing project documentation, client communications, and internal platforms.
- Conducting virtual meetings or using collaborative tools approved by IT.
- Using approved mobile apps for site inspections, reporting, and team coordination.
3.2 Prohibited Activities
- Streaming entertainment, gaming, or excessive personal browsing.
- Installation of unlicensed or unauthorized applications.
- Accessing or sharing offensive, defamatory, or illegal content.
- Sharing devices, SIMs, or routers with non-NT personnel.
3.3 Key Points
- All activity is subject to monitoring via endpoint management systems.
- Policy violations will trigger investigation by HR and IT.
- Security alerts must be reported immediately.
4 Laptop, Tablet, and Smartphone
These devices are essential tools for most job functions. Employees must treat them as critical work assets and ensure their safety and functionality at all times.
4.1 Operational Expectations:
- Devices should only run NT-approved operating systems and software.
- Passwords, screen locks, and encryption must be enabled and never disabled.
- Regular software updates must be installed to maintain cybersecurity standards.
- Users must avoid storing sensitive data locally unless encrypted and approved.
4.2 Travel Use:
- When traveling abroad, roaming data must be disabled unless explicitly approved.
- Carry devices as hand luggage; avoid leaving them in hotel rooms or vehicles.
4.3 Key Points:
- Lost or stolen devices must be reported within 12 hours.
- Repairs must be coordinated through IT; unauthorized servicing is not permitted.
- Equipment issued for remote work must be returned upon reassignment or offboarding.
5 Mobile Phones, SIM Cards, and Routers
Communication and internet access devices are provided to ensure seamless connectivity, especially during field operations. Their use is monitored to ensure cost efficiency and adherence to NT’s telecom policies.
5.1 Usage Limits
- Voice and data usage are capped based on employee category and project demands.
- International roaming, data-heavy downloads, or personal tethering require prior approval.
- Use of NT SIMs or routers for non-work-related streaming or VPN activity is prohibited.
5.2 Data Control
- Finance may deduct excess usage charges if not justified.
- Employees must notify Finance and IT if they expect high usage for operational reasons.
- SIMs are issued for project use and must not be transferred between devices without approval.
5.3 Key Points:
- Devices must remain on and responsive during working hours.
- Roaming settings must be reviewed before travel.
- Use of data-intensive services (e.g., YouTube, Netflix, other social medias) is strictly prohibited.
6. Project Router Usage
Routers are issued to Program Managers (PMs) specifically to support operations where it is not possible to access or utilize client-provided internet services. These routers are critical for maintaining connectivity during project execution, particularly at remote or temporary field locations. Each router is assigned to the PM responsible for that site or activity, and it is the PM's duty to safeguard the device and ensure ethical usage of the internet connection.
6.1 Usage Guidelines:
The router and its network connection must not be used for any criminal, fraudulent, or unlawful activities under any circumstances.
- Routers must be used strictly for official business purposes such as project communications, document uploads, inspections, and application access.
- Any personal use—including video streaming, downloading media, or browsing non-business-related websites—is strictly prohibited.
- All team members who connect to the router are jointly accountable for ensuring responsible use.
- Routers must be locked and secured when not in use and should not be left unattended at project sites.
6.2 Monitoring and Compliance:
- NT reserves the right to monitor data consumption on project routers.
- Any unexplained high usage may trigger an investigation and potential salary deductions.
- PMs must report any technical issues or data abuse concerns to IT and Admin immediately.
Key Points:
- Router is issued only when justified by project conditions.
- Shared responsibility lies with all users connected to the router. Employees shall sign NDAs in adherence to this clause.
- Unauthorized use or negligence will result in disciplinary measures and potential recovery of data charges.
7 Personal Protective Equipment (PPE)
NT issues PPE to employees whose roles require exposure to construction or inspection environments. The use of safety gear is mandatory for field visits and must comply with occupational health and safety standards in Saudi Arabia.
7.1 Issued Items Include:
Based on the project needs, the following PPE are issued: Safety Helmets, High-Visibility vests, Safety Goggles, Gloves, Boots, and Masks.
7.2 Maintenance and Compliance:
- Employees must inspect PPE before use and report defects.
- Replacement requests must include reasons and be verified by HSE.
- Misuse or neglect (e.g., leaving PPE at site or lending it) is not acceptable.
Key Points:
- Wearing PPE is mandatory when site policy requires it.
- Employees may be barred from entering sites without full PPE.
- PPE remains the property of NT and must be returned or replaced on exit.
8 Security and Loss Reporting
Employees are responsible for the physical and digital security of all issued equipment. Devices must be secured when unattended, and loss or theft must be reported immediately.
8.1 Incident Response Protocol:
- Notify IT for devices, Admin for routers, HSE for PPE.
- Lodge a formal report with security or police when necessary.
- Provide a written explanation to HR and retain a copy.
Key Points:
- Employees may be charged for loss due to negligence.
- Theft or vandalism should be accompanied by an official report.
- NT reserves the right to initiate deductions for unreturned assets.
9 Policy Compliance and Violations
Compliance with this policy is mandatory for all employees. Violations may result in suspension of equipment privileges, cost recovery, or disciplinary action depending on severity.
9.1 Examples of Violations:
- Sharing login credentials or hotspot access.
- Using devices for cryptocurrency mining, torrents, or adult content.
- Repeated non-compliance with software update policies.
9.2 Escalation Path:
- First violation: Written warning.
- Second violation: Suspension of equipment access.
- Third violation or severe misconduct: Disciplinary investigation by HR.
Key Points:
- Persistent misuse will impact performance evaluations.
- All violations are documented and stored in employee records.
- IT reserves the right to restrict access to compromised or misused devices.
10. Forms and Systems

1. Purchasing & Procurement
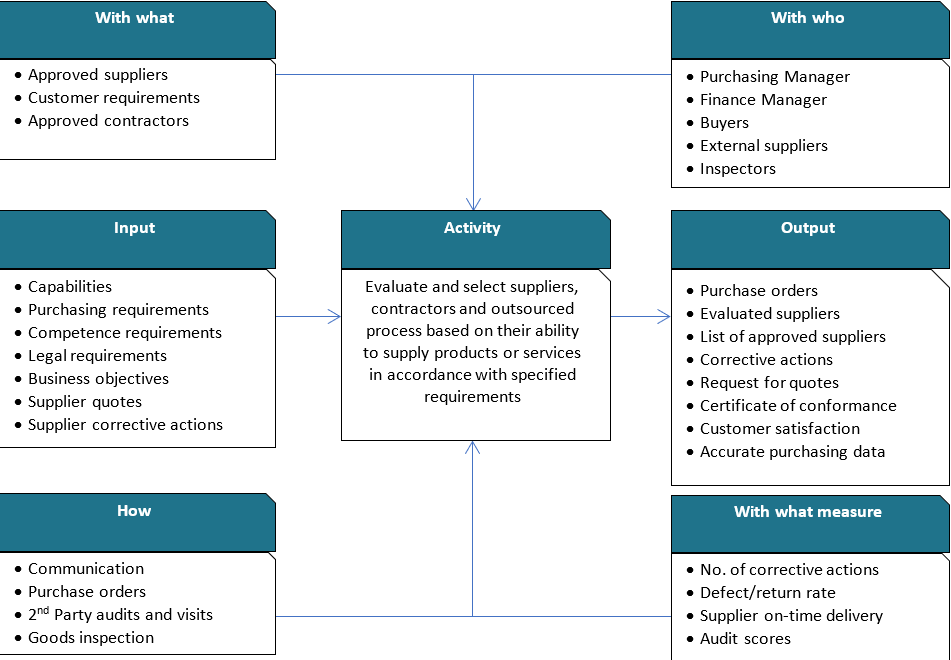
The purpose of this procedure is to define the activities required to ensure that purchased products conform to the specified purchase requirements, by detailing the combination of supplier controls, purchasing requirements and purchased product inspection that takes into account the potential consequences of a non-conforming product being delivered.
1.1.1 Process Turtle Diagram
1.1.2 References
1.1.3 Terms & Definitions

1.2 Application & Scope
This procedure applies to all products and services that NT purchases — whether from suppliers, contractors, or service providers — and whether these are used internally, delivered to clients, or required for project execution.
It covers:
1. Selection and evaluation of suppliers and contractors
2. Issuing and managing purchase orders (POs)
3. Receiving and inspecting purchased goods or services
4. Handling outsourced activities
5. Ensuring all purchased items meet NT’s and the client's requirements.
This procedure applies to both routine purchases (e.g., office equipment, support services) and project-specific procurement (e.g., manpower, technology tools, consultancy subcontracts).
1.3 Supplier Evaluation & Selection
1.3.1 New Suppliers
Before working with a new supplier, NT conducts an evaluation to confirm their ability to meet quality, delivery, and compliance requirements.
This includes reviewing:
1. Technical qualifications
2. Relevant experience
3. Certifications (e.g., ISO, safety standards)
4. References or past performance (if available)
If the supplier meets NT’s criteria, they are added to the Approved Supplier List, and their documentation is maintained for reference.
1.3.2 Existing Suppliers
Approved suppliers are reviewed periodically based on:
1. Delivery timelines
2. Product or service quality
3. Responsiveness and cooperation
4. Compliance with contractual or legal requirements
Performance data may be gathered from project teams, inspection records, or audit findings. Suppliers who consistently meet expectations remain on the Approved List; others may require re-evaluation or corrective action.
1.3.3 Disqualified Suppliers
A supplier may be disqualified if:
1.They repeatedly deliver poor-quality goods or services
2.They fail to meet contractual obligations
3. Safety, environmental, or legal violations occur
Disqualified suppliers are removed from the Approved List, and records of the disqualification, including justification and any correspondence, are retained for audit purposes.
1.3.4 Outsourced Processes
For any outsourced activity that affects the quality or outcome of NT’s services:
1.The outsourced provider is treated as a critical supplier
2.Their ability to meet contract and process requirements is assessed
3.Controls are established to ensure the output meets NT and client expectations
The Head of Business Excellence & Governance (BXG) ensures proper oversight of outsourced processes, especially when they relate to core service delivery.
1.4 Purchasing Information
1.4.1 Purchase Orders
All purchases at NT must be made using an official Purchase Order (PO) that clearly describes:
1. Product or service name
2. Quantity and specifications
3. Delivery requirements (date, location)
4. Applicable drawings, standards, or instructions
5. Any legal, safety, or quality obligations
P.O.s are issued only to suppliers on the Approved Supplier List.
1.4.2 Purchase Order Review
Before issuing a purchase order:
1. The requester or purchasing personnel must review the order for completeness and accuracy
2. Required approvals must be obtained according to NT’s delegation of authority
3.The Head of Business Excellence & Governance (BXG) ensures that all specifications and compliance requirements are properly included
This step helps avoid miscommunication, delays, or non-conforming deliveries.
1.4.3 Verbal Orders
Verbal orders are discouraged. However, in urgent or exceptional cases:
1. A verbal order may be given by an authorized person
2. It must be followed by a formal PO or written confirmation within the same day
3.The details must match the verbal instructions given
Verbal orders without proper follow-up are considered non-compliant.
1.4.4 Procurement Records
Records related to procurement include:
1. Supplier evaluations
2. POs and contracts
3.Delivery receipts
4. Inspection reports
5.Corrective actions (if applicable)
These records are maintained digitally in line with NT’s Documented Information Control Procedure and must be available during audits or management reviews.
1.5 Verification of Purchased Product
NT verifies that all purchased products and services meet the specified requirements before acceptance.
Verification steps may include:
1. Checking quantities and specifications upon delivery
2. Reviewing inspection certificates or compliance documents
3. Conducting visual inspections or functional checks
4. Verifying conformance with project or contractual standards.
If a purchased item is found to be non-conforming:
1. It is reported immediately to the Purchasing Department and the Head of Business Excellence & Governance (BXG)
2. The item may be rejected, returned, or accepted under concession (with documented justification)
3. Corrective action may be initiated with the supplier
All verification results and related records are documented and stored as part of NT’s procurement and quality system.
1.6 Contractors
Contractors are managed using the same sourcing, selection, and documentation process as suppliers.
Before work begins, NT ensures that each selected contractor is qualified and capable of performing the required tasks. Verification includes:
1. Checking past OH&S performance records
2. Ensuring contractor personnel meet required qualifications, experience, and training standards
3. Confirming that resources, equipment, and site readiness are sufficient before work starts.
Each contractor's responsibilities are defined clearly in a contractual agreement, which also includes:
1. How hazards are communicated between NT and the contractor
2. Rules for controlling access to hazardous areas
3. Methods and criteria for monitoring contractor performance
4. Emergency procedures applicable to contractor worksites.
These measures ensure that contractor activities align with NT’s quality, health, and safety expectations.
1.7 Outsourcing
When NT decides to outsource a process or part of a process that affects the quality or compliance of deliverables, specific controls are applied to ensure conformity.
The Head of Business Excellence & Governance (BXG) defines these control measures, which may include:
1. Personnel competence verification
2. Inspection and quality control criteria
3. Requirement for product conformity certificates
4. Adherence to specifications and project documentation.
The level of control over the outsourced process depends on:
1. The external provider’s ability to meet NT’s QEHS system requirements
2. The provider’s technical expertise and control systems
3. The impact of the outsourced task on NT’s ability to meet OH&S outcomes
4. Whether the process is shared or fully outsourced
5. The ability to manage the task through NT’s procurement process
6. Opportunities to improve process effectiveness.
Outsourcing does not relieve NT of responsibility for compliance with client, legal, or regulatory obligations. Instead, these controls are intended to strengthen supply chain oversight and ensure outsourced work aligns with NT’s standards.
All outsourced processes are governed through formal purchasing or contractual agreements.
1.8 Forms & Records
All records related to purchasing and procurement are managed according to NT’s Documented Information Control Procedure. These records help ensure traceability, compliance, and support during audits and performance reviews.

All records are stored in digital format and updated as part of our Management Review Cycle. It is the responsibility of each process owner to ensure that these documents remain up to date and are available during audits or upon request.
1. Introduction
Business travel is an essential part of NT’s operations, allowing employees to engage with clients, participate in industry events, support remote projects, and coordinate with internal teams across locations. While enabling these activities, it is important to balance operational goals with financial prudence and compliance requirements. This policy provides a comprehensive framework for managing travel in a way that is transparent, efficient, and aligned with NT’s values. It ensures that all travel and related expenses are authorized in advance, adequately documented, and responsibly incurred in accordance with legal and organizational expectations. Travelers are expected to conduct themselves professionally and represent NT’s standards wherever they go.
The NT Business Travel and Expense Policy sets clear expectations and procedures for employees and authorized personnel who travel on behalf of the company. This policy ensures that business travel aligns with NT’s mission, promotes fiscal responsibility, and provides consistent guidelines for approvals and reimbursements. As a responsible organization operating under Saudi Arabian Labour Law and aligned with corporate governance standards, NT emphasizes transparency, accountability, and fairness in handling business-related travel expenses. This policy not only governs bookings and financial claims but also ensures the well-being and operational preparedness of traveling staff.
1.1 Scope:
v Applies to all NT employees, contractors, consultants, and any representative undertaking approved travel for company purposes.
v Encompasses domestic and international travel for meetings, training, client engagement, site visits, and business development.
v Includes airfare, accommodation, meals, local transport, visa costs, and reimbursable incidentals.
v Aligns with project budgets, internal approval workflows, and NT’s financial monitoring procedures.
v Complies with Saudi Arabian financial regulations, travel safety protocols, and labor laws.
1.2 Roles and Responsibilities:
v Employees must initiate travel requests, follow booking channels, retain documentation, and submit accurate expense claims.
v Line Managers review travel justification and ensure alignment with project or departmental needs.
v Department Heads / Program Managers validate whether travel fulfils operational requirements.
v Finance Department checks for compliance, cost justification, and documentation before processing reimbursement.
v Executive Management (COO, CEO, CTO) approves strategic, international, or high-value travel activities
2. Business Travel Approval Procedure
Travel requests must be submitted and approved before any arrangements are made, regardless of the trip’s duration or destination. This structured process safeguards NT from unnecessary or excessive expenditure and ensures that travel aligns with project timelines and client requirements. It also allows relevant department heads and executives to assess the necessity of the trip in the broader context of business priorities.
Adherence to this procedure is mandatory and helps maintain visibility, accountability, and compliance. Unapproved travel, even if executed in good faith, may result in reimbursement being denied. All stakeholders are encouraged to plan ahead to accommodate approval lead times.
Business travel must follow a structured approval chain before bookings or commitments are made. This ensures trips are aligned with NT’s operational strategy, budget allocations, and client commitments.
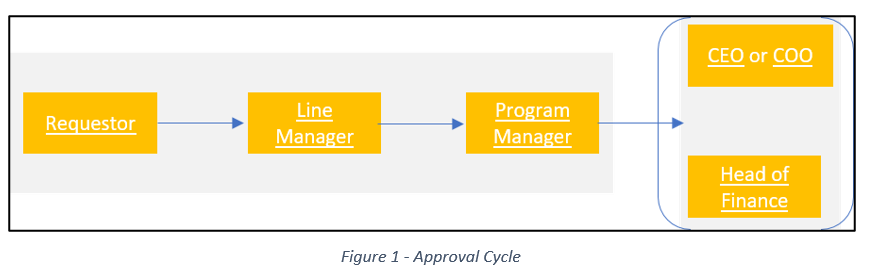
Approval Steps:
1. Employee completes and submits the Business Travel Request Form on HRMS.
2. Line Manager review’s purpose, duration, and benefit of travel.
3. Department Head or Program Manager verifies if travel is essential for project success.
4. COO or CEO reviews broader business needs and strategic alignment.
5. Finance assesses cost implication and allocates budget approval.
Key Points:
1. Submit requests a minimum of 7 working days prior to travel (14 days for team/group trips).
2. Emergency travel must be documented and justified within 48 hours of return.
3. Bookings and arrangements proceed only after full sign-off.
4. Late submissions or unapproved travel will not be reimbursed.
3. Travel Booking and Coordination
NT emphasizes the importance of central coordination in travel arrangements to control costs and avoid duplication. Centralized booking also allows for better tracking of travel trends, vendor negotiations, and risk mitigation (especially in crisis situations or emergencies). Designated travel coordinators play a key role in managing logistics, ensuring policy adherence, and supporting travellers before and during trips. Employees should refrain from booking outside approved channels unless explicitly instructed. NT reserves the right to reject reimbursements for bookings made outside of the authorized system without prior justification.
All travel bookings should be centralized and managed through designated NT travel coordinators to optimize cost efficiency, streamline logistics, and comply with negotiated vendor terms.
Procedures:
1. All air tickets, hotel bookings, and related reservations must be coordinated through the NT Travel Coordinator.
2. Projects managed by the Cyprus office must channel approvals via the Cyprus Finance Controller and Office Administrator.
3. Travel Coordinators ensure bookings follow lowest-cost available fares and preferred hotel partnerships.
Key Points:
1. Travel bookings must reflect NT’s standards on class of travel and accommodation level.
2. Justifications are required for any deviation from the preferred options.
3. Corporate discounts and loyalty programs must be used where applicable.
4. Air Travel Guidelines
Air travel arrangements must strike a balance between cost-efficiency and employee wellbeing. NT’s policy of Economy Class travel for all business trips reflects this principle, encouraging responsible spending while ensuring safe and timely travel. Exceptions are discouraged and must be clearly justified based on business criticality. NT discourages last-minute bookings unless necessitated by urgent client or project demands. Employees must also take responsibility for cancelling or adjusting bookings in case of changes, to help the company recover costs. Compliance with this section contributes to consistent travel behaviour and budget management across departments.
Air travel must be conducted in the most economical and efficient manner possible. NT mandates the use of Economy Class for all employees traveling on business, unless exceptional authorization is granted.
Requirements:
1. All flight bookings must use Lowest Fare Routing (LFR) at the time of reservation.
2. Business Class or First-Class travel is not reimbursable unless approved in writing by the CEO or COO.
3. Employees must cancel or modify bookings promptly to avoid losses.
Key Points:
1. Advance booking is essential to reduce fare costs.
2. Employees must notify the travel coordinator of unused or cancelled tickets.
3. Refunds and rebooking must follow company procedures to retain value.
5. Accommodation and Hotel Stays
When staying overnight for work, employees must choose accommodations that are safe, comfortable, and economical. NT maintains a list of preferred hotels that meet quality, security, and pricing benchmarks. Employees are expected to use these vendors wherever possible. Bookings should be made well in advance, especially for international travel, to ensure availability within budget. If travellers need to book directly due to timing or location constraints, the Travel Coordinator must be informed immediately. All bookings must reflect business needs and reasonable standards; personal upgrades are not covered by the company unless pre-authorized.
Hotel accommodation should reflect NT’s standards for safety, convenience, and affordability. Travelers must use approved or preferred hotels, and bookings must be arranged centrally.
Guidelines:
1. Rooms must be standard single occupancy and booked by the Travel Coordinator.
2. Upgrades (e.g., suite, deluxe) are not covered unless required for business meetings or approved by executive management.
3. Cancellations made directly by employees must be documented with cancellation numbers.
Key Points:
1. Only approved hotel tariffs will be reimbursed.
2. Personal extras such as minibar, laundry, or in-room entertainment are not claimable.
3. Direct bookings are discouraged unless coordinated with Finance and Travel Team.
6. Car Rental Policy
Car rentals are permissible only when public transportation, taxis, or ride-sharing services are unavailable, impractical, or significantly more expensive. The selected vehicle should match the needs of the trip (e.g., city meetings versus long-distance intercity travel) while maintaining a focus on cost-effectiveness. Employees must ensure proper documentation is retained, including the rental agreement and receipts. Insurance coverage must be obtained to limit liability. Any upgrades or changes to the vehicle category must be justified and approved. Personal use of rented vehicles is strictly prohibited, and non-compliance may result in non-reimbursement.
Employees may rent cars only when it is operationally justified, cost-effective, and approved prior to travel.
Rules:
1. Only compact or intermediate vehicles may be rented unless otherwise justified.
2. Rentals are approved only when public transport or ride-sharing is impractical.
3. Personal use of rental cars is prohibited.
Key Points:
1. NT does not cover premium or luxury car rental expenses.
2. Receipts and rental agreements must be submitted with expense claims.
3. Damage liability insurance must be included in rental agreements.
7. Per Diem Allowance
NTs per diem allowance policy simplifies the process of compensating employees for daily expenses incurred during business travel. It eliminates the burden of collecting and processing minor receipts while still ensuring fair compensation. The per diem rate is based on the trip's location and is paid on a calendar-day basis, including travel days. Employees must ensure that business travel is pre-approved to qualify for per diem payment. The allowance is not intended to supplement personal travel or entertainment expenses. If meals or other daily costs are already covered (e.g., via conference catering or client provisions), NT reserves the right to reduce or withhold the per diem accordingly.
To streamline minor daily expenses (e.g., meals, transport, tips), NT provides a per diem allowance during business trips. This removes the need to submit receipts for incidental costs and supports travel budgeting.
Per Diem Rates:
Guidelines:
1. Per diem is paid for each approved overnight stay.
2. No receipts are required; however, travel must be pre-approved.
3. Per diem does not cover accommodation or airfares which are reimbursed separately.
4. If meals are fully covered by NT or a client (e.g., in a training program), per diem may be adjusted accordingly.
8 Expense Reimbursement and Documentation
Reimbursement of business travel expenses is subject to timely submission, proper documentation, and compliance with the policy. NT provides standardized forms to ensure consistency, and travelers are responsible for completing these accurately. All supporting documents must clearly indicate the nature, timing, and cost of the expense. Expense claims not supported by appropriate receipts or justification may be delayed or denied. Travelers are encouraged to maintain a daily record of their expenditures to ease the reimbursement process. Claims submitted after the deadline without valid reason may be considered non-compliant.
Accurate and timely submission of expense claims ensures, proper accounting and prompt reimbursement. All claims must be supported by original receipts and submitted via the official NT claim form.
Submission Guidelines:
1. Submit claims within 7 calendar days of return from travel.
2. Long-duration travellers may submit interim claims every two weeks.
3. Receipts must include vendor name, date, expense description, and proof of payment.
Key Points:
1. Claims with missing or altered receipts require COO exception approval.
2. Approvers must verify costs and purpose before authorizing.
3. Submission delays beyond 30 days may lead to forfeiture of reimbursement.
9. Exceptions and Non-Reimbursable Items
This section provides guidance on expenses that fall outside the boundaries of NT's reimbursement policy. Employees should carefully assess whether their planned expenditures align with company expectations. While certain business needs may occasionally require exceptions, these must be clearly documented and pre-approved. Any claim that lacks transparency, appears excessive, or deviates from policy principles will be subject to further review. Employees who repeatedly submit inappropriate expenses may be subject to disciplinary action. This policy safeguards NT’s financial interests while promoting fairness and consistency across the organization.
Employees are expected to avoid incurring costs outside of the policy. NT reserves the right to deny claims that are inconsistent, excessive, or unsupported.
Examples of Non-Reimbursable Items:
v Hotel upgrades, minibar, or personal entertainment.
v Alcoholic beverages, tobacco, or personal gifts.
v Travel or expenses without prior written approval.
v Tips exceeding local norms or not covered under per diem.
Key Points:
1. Exceptions must be authorized by the Program Manager and the Head of Finance or designated approver.
2. Always verify in advance when unsure if an expense qualifies.
3. Expense audits are conducted periodically to ensure compliance.
10. Policy Compliance and Audits
To maintain accountability and transparency, NT enforces this policy through periodic audits and compliance checks. The Finance Department is authorized to inspect travel and expense claims for accuracy, legitimacy, and alignment with company standards. Employees are expected to cooperate fully during audits and provide additional documents when required. Failure to follow this policy may result in financial penalties, suspension of reimbursement privileges, or formal HR action. NT encourages employees to ask for clarification in advance to avoid policy violations. Continuous improvement and regular training will support the effective implementation of this policy.
Adherence to this policy is mandatory. NT reserves the right to audit all travel expenses and investigate discrepancies. Non-compliance may result in disciplinary action.
Compliance Expectations:
1. Submit all required documentation truthfully and completely.
2. Cooperate fully during finance audits or management reviews.
3. Repeated violations may lead to written warnings or further HR measures.
4. Fraudulent claims may result in legal and employment consequences.
11. Forms and References:

1. Introduction
This policy outlines the conditions,
responsibilities, and conduct expected from all NT employees and contractors
who operate company-provided vehicles or drive on official business in Saudi
Arabia. It is designed to promote safe, lawful, and responsible vehicle use,
ensure alignment with Saudi traffic laws and NT’s operational requirements, and
protect company assets. NT provides vehicles for official duties and expects
drivers to exercise high standards of care, ethics, and compliance at all
times. Any deviation from this policy may result in corrective or disciplinary
action.
1.1Scope:
1. Applies to all NT staff, contractors, and representatives using company-provided vehicles or driving on company business.
2. Includes both permanent fleet vehicles and short-term rentals.
3. Encompasses driving within the Kingdom of Saudi Arabia and any cross-border use where approved.
1.2 Roles and Responsibilities:
1. Employees must hold a valid Saudi or internationally recognized driver’s license, follow all traffic laws, and adhere to this policy.
2. Supervisors/Managers are responsible for ensuring only authorized personnel are assigned company vehicles.
3. Fleet Coordinator or Admin Officer manages vehicle records, maintenance schedules, and insurance compliance.
4. HR & Compliance Teams ensure drivers receive orientation on safety, penalties, and reporting requirements.
2. Authorized Use of Vehicles
Company-provided vehicles are intended strictly for business purposes, including travel to project sites, official meetings, and transport of approved personnel or materials. Personal use is not permitted unless authorized in writing. Unauthorized passengers—such as friends, or hitchhikers—are strictly prohibited.
Key Points:
1. Vehicles may not be lent or shared with unauthorized individuals.
2. Transportation of non-NT staff requires prior management approval.
3. NT has the right to inspect vehicle use logs and GPS data.
3. Driver Qualifications and Licensing
All vehicle operators must maintain a valid driving license that is legally accepted in Saudi Arabia. This includes a Saudi-issued license or an international license for visitors, subject to legal limits. NT reserves the right to review driving records before assigning vehicles.
Key Points:
1. Drivers must be medically fit and capable of operating vehicles safely.
2. Expired or suspended licenses must be reported immediately.
3. Driving privileges may be withdrawn for safety or legal violations.
4. Vehicle Care and Maintenance
Drivers are responsible for keeping vehicles clean, roadworthy, and mechanically safe. Smoking inside company vehicles is strictly prohibited. Preventive maintenance must be performed as per the manufacturer’s recommendations, and drivers must report any warning indicators or damages immediately.
Key Points:
1. Regular service schedules must be adhered to.
2. Unreported damage or negligence may result in cost recovery.
3. Vehicles must be parked securely, locked, and keys stored safely.
5. Safety and Driving Rules
Safety is the top priority in all vehicle operations. Drivers must comply with Saudi traffic laws, NT’s internal safety procedures, and general safe driving practices. Mobile phone usage while driving is prohibited unless using approved hands-free devices.
Key Points:
1. Seatbelt use is mandatory for all occupants.
2. Driving under the influence of alcohol or drugs will lead to immediate termination.
3. Drivers must not operate vehicles while ill, fatigued, or distracted.
4. Report any fines or violations within 24 hours to the Admin Officer.
6. Fuel Expense Reimbursement
Fuel expenses incurred during the use of company-provided vehicles for official business purposes are eligible for reimbursement, provided proper documentation is submitted. Employees must retain original fuel receipts, clearly indicating the date, fuel station name, and amount paid. Reimbursement claims should be submitted within five working days through the designated expense reporting system.
Guidelines:
1. Fuel receipts must be itemized and match the travel period and route.
2. Only fuel costs for company-authorized routes will be reimbursed.
3. Claims without original receipts or with unclear entries will not be processed.
4. Misuse or falsification of claims may lead to disciplinary action.
5. Abnormal or excessive fuel usage beyond expected mileage or usage pattern will not be accepted and may be flagged for investigation.
6. Electric vehicle charging, if applicable, must follow the same documentation process.
Key Points:
1. Claims must be submitted through the Finance-approved format.
2. Reimbursement is only allowed for approved business use.
3. Any disputes will be reviewed jointly by Admin and Finance departments.
7. Accidents and Incident Reporting
In case of an accident, drivers must follow Saudi protocols, including contacting Traffic Police or Najm (insurance support authority) depending on the incident severity. Immediate reporting to NT Management is required.
Response Steps:
1. Secure the scene and ensure everyone’s safety.
2. Call 920000560 (Najm) or Traffic Police in case of injury or fire.
3. Take photos, note vehicle and driver details, and wait for instructions.
4. Do not admit fault or settle without official assessment.
Key Points:
1. Accident reports must be submitted to NT Admin and Insurance Team within 24 hours.
2. Costs incurred due to negligence or fault may be recovered from the employee.
3. Substance use at the time of incident results in full liability and termination.
8. Penalties and Legal Obligations
Drivers must be aware of and comply with Saudi Arabia’s evolving traffic regulations. Repeated violations will result in suspension of vehicle privileges or further disciplinary action. Common fines include:
Sample Penalties (as per Saudi Traffic Law):
1. Using a phone while driving: SAR 500–1,500 and up to 24 hours jail.
2. Running red lights: SAR 3,000 and potential vehicle impound.
3. Eating while driving: SAR 150.
Key Points:
1. NT is not responsible for personal traffic or parking violations.
2. Repeated offenses will be escalated to HR for review.
3. Employees may be charged for repair, replacement, or downtime caused by reckless use.
4. To know more about traffic violations, please visit: https://www.moi.gov.sa/
1 Vehicle Return and Handover
Vehicles must be returned in clean, operable condition at the end of assignment, project, or employment term. Any damages or issues must be reported during the handover process.
9. Vehicle Return and Handover
Vehicles must be returned in clean, operable condition at the end of assignment, project, or employment term. Any damages or issues must be reported during the handover process.
Key Points:
1. Final inspection must be documented.
2. Fuel levels, cleanliness, and physical condition will be assessed.
3. Missing accessories or damage will be charged to the driver if not justified.
10. Policy Compliance and Review
All users must sign the Vehicle Acknowledgment Form before being assigned a vehicle. NT reserves the right to audit vehicle usage, maintenance logs, and driver behavior as part of compliance enforcement. This policy is subject to periodic review in line with new traffic regulations, insurance laws, or business requirements.
Key Points:
1. Signed acknowledgment is mandatory for policy enforcement.
2. Policy will be reviewed annually or as needed.
3. Drivers must seek clarification from HR or Admin for any ambiguities.
11. Forms and References
Integrated Management System (IMS) Policy (ISO 9K, 45K, 14K)
In progress
In progress

1.Organizational context
1.1 Introduction and Purpose
The purpose of this procedure is to explain how Norconsult Telematics (NT) identifies internal and external factors that influence its ability to provide professional consultancy services. This also includes understanding the needs and expectations of interested parties that affect our Integrated Management System (IMS) and influence our strategy and day-to-day operations.
Our goal is to ensure that our services are aligned with our strategic direction, operational goals, and customer expectations by regularly reviewing relevant business contexts and stakeholder needs.
1.1.1 Process Turtle Diagram
1.1.2 References
1.1.3 Terms & Definitions

1.2 Application and Scope
This procedure applies to all departments and services offered by Norconsult Telematics (NT). It supports compliance with Clause 4.0 of ISO 9001:2015 (Quality), ISO 14001:2015 (Environmental), and ISO 45001:2018 (Occupational Health & Safety).
The purpose is to help NT identify and respond to internal and external factors that affect our ability to deliver high-quality consultancy services. This includes:
1. Understanding laws, regulations, and market trends that apply to our sectors (Telecom, ICT, Power Utilities, and Government).
2. Monitoring competitors, technologies, and customer expectations.
3. Aligning our policies, objectives, and resources with business opportunities and risks.
4. Using this understanding to make informed decisions and manage risks effectively across all functions.
5. This procedure lays the foundation for risk-based thinking and ensures we are proactive in managing change and delivering consistent value to our clients.
1.3 Organizational Context
NT’s approach to planning and maintaining its Integrated Management System (IMS) is built on a continuous improvement model. We regularly assess internal and external factors that could affect our consultancy services, strategic direction, and ability to meet client expectations.
We use established tools such as SWOT (Strengths, Weaknesses, Opportunities, Threats) and PESTLE (Political, Economic, Social, Technological, Legal, Environmental) analysis to:
1. Understand our business environment
2. Identify challenges and opportunities
3. Assess organizational capabilities and gaps
4. Guide our strategy and operational planning
Only the issues that directly affect NT’s ability to meet its objectives are prioritized. For each key issue identified, we take the following steps:
1. Determine whether the issue needs immediate action or further study.
2. Develop realistic strategies and allocate resources to address it.
3. Link these findings to our risk management process and improvement plans.
This process ensures NT remains aligned with client needs, regulatory requirements, and changes in our operating environment—locally, regionally, and globally. It also strengthens our ability to plan effectively, manage risk, and seize opportunities.
We conduct a formal review of this context at least once a year, or sooner when launching new services, projects, or strategic initiatives.
1.3.1 Internal Issues
NT’s internal context focuses on the people, systems, values, and resources that influence how we operate. Understanding our internal strengths and weaknesses helps us make informed decisions and improve how we deliver services.
We use the Context & Interested Parties Matrix and SWOT Analysis Template to capture and analyze these internal factors.
1.3.1.1 Strengths
These are the qualities that give NT an edge in the consultancy market:
v What do we do better than others?
v What capabilities set us apart in terms of client delivery, quality, or innovation?
v How do our tools, frameworks, or talent give us an advantage?
Examples may include our experienced consultants, proven methodologies, client relationships, and digital enablement capabilities.
1.3.1.2 Weaknesses
These are internal areas where we need to improve:
v What are our recurring issues or bottlenecks?
v Are there skill gaps or outdated processes?
v What do internal reviews or client feedback tell us we could do better?
This helps us focus on areas such as resource allocation, cross-functional coordination, or system upgrades.
1.3.1.3 Opportunities
These are trends or conditions NT can leverage to grow:
v Are there new client needs in digital transformation or public sector reform?
v Are there market or regulatory changes creating new service opportunities?
v Are there technologies we can adopt to increase our efficiency?
v We also look at global best practices to identify gaps we can fill in our current offerings.
1.3.1.4 Threats
These are risks that may affect our ability to deliver or grow:
v Are there potential disruptions due to regulatory changes or economic instability?
v Are there new competitors in the Saudi or regional markets?
v Could staffing issues, such as turnover or skills shortages, pose a risk?
Understanding these threats allows NT to take proactive actions through risk mitigation and strategic planning.
1.3.2 External Issues
Understanding external factors helps NT align its services with the evolving business environment. These external factors are identified using the Context & Interested Parties Matrix and further analyzed through the PESTLE Analysis Template. The goal is to recognize external risks and opportunities that may impact NT's consultancy services across sectors such as Telecom, ICT, Power Utility, and Government.
1.3.2.1 Political
We examine political factors that can affect how we operate, such as:
v National regulations on local content or Saudization
v Government incentives or restrictions on foreign consultancy services
v Public-sector restructuring initiatives (e.g. Vision 2030 reforms)
v Political stability and government leadership priorities
v Influence of lobbying groups and policy shifts
1.3.2.2 Environmental
We consider environmental aspects that affect our business directly or indirectly:
v Environmental regulations applicable to client sectors (e.g. utilities, infrastructure)
v Government focus on sustainability and green energy projects
v Clients’ environmental performance requirements
v Stakeholder expectations for environmental reporting or responsibility
v Market shifts toward environmentally responsible services
1.3.2.3 Technological
Technology developments shape how NT delivers services and competes:
v Emerging digital tools (e.g. AI, BIM, Digital Twin) relevant to consulting
v Automation of client operations requiring advisory support
v Advancements in telecom and smart infrastructure
v Demand for integrated project monitoring systems
v Risks of cybersecurity and data handling in digital consultancy work
1.3.2.4 Social/Cultural
Social trends influence the needs and expectations of clients and employees:
v Shifts in consumer or citizen expectations (e.g. demand for digital services)
v Rising importance of local employment and workforce development
v Changes in workforce demographics and lifestyle preferences
v Public demand for transparency, especially in government contracts
v Evolving norms around remote work, inclusion, and knowledge sharing
1.3.2.5 Legislative
We monitor laws and regulations affecting our services and operations:
v Compliance with Saudi Labour Law, MISA, GOSI, MoF, and Local Content Authority
v Evolving procurement rules and public sector contracting guidelines
v ISO compliance requirements (9001, 14001, 45001, 27001)
v Legal responsibilities for data protection and client confidentiality
v Licensing, tax, and registration obligations in KSA and other regions
1.3.2.6 Economic
We assess how economic factors impact our business environment:
v Government spending on infrastructure and digital transformation
v Inflation, interest rates, and budget allocations for key sectors
v Oil price fluctuations and their impact on project investments
v Growth in adjacent markets like smart cities or energy efficiency
v Foreign investment trends and diversification strategies in the region
1.4 Interested Party Requirements
NT acknowledges that various stakeholders influence our ability to deliver consistent, high-quality consultancy services. Some expectations—such as legal or contractual obligations—are mandatory. Others, such as industry standards or voluntary commitments, may be adopted to enhance value or reputation.
Once we identify and agree to an expectation, we treat it as a requirement within our Integrated Management System (IMS).
1.4.1 Identifying Interested Party Requirements
Each department manager, in coordination with the QEHS Manager, is responsible for identifying stakeholders (interested parties) related to their function. These may include:
v Clients and end users
v Government regulators and municipalities
v Employees and subcontractors
v Partners and vendors
v Certification bodies and auditors
Their needs and expectations are captured using the Context & Interested Parties Matrix. We assess how these needs may affect:
v Our ability to meet NT’s objectives and service quality
v Compliance with ISO and legal standards
v Client satisfaction and retention
Each Head of the Business Unit in conjunction with the Head of Business Excellence and Gov. ranks the interested parties according to their degree of Priority and their Relevance (1 low, 4 high) to current objectives, policies and conformity of products and services. The spreadsheet multiplies these scores to generate an overall Power score that represents the Risk Priority Number (RPN) that is used to prioritize the adoption of any relevant need or expectation.
1. Relevance – effects upon organizational activities
2. Priority – effects on decisions the organization makes
3. Power – combined effects of influence the interested party has (Risk Priority Number RPN)
1.4.2 Interested Party Scoring Matrix
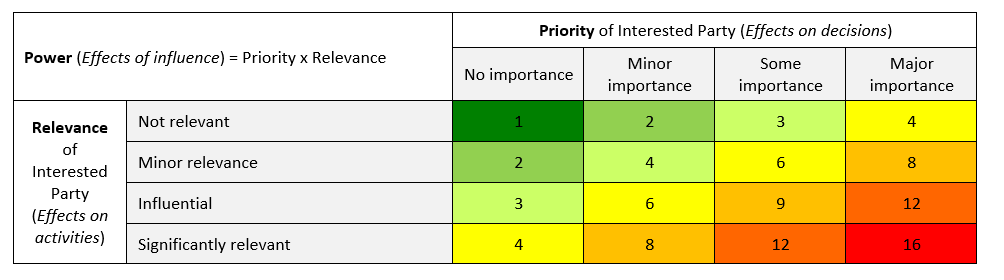
1.4.3 Action Matrix
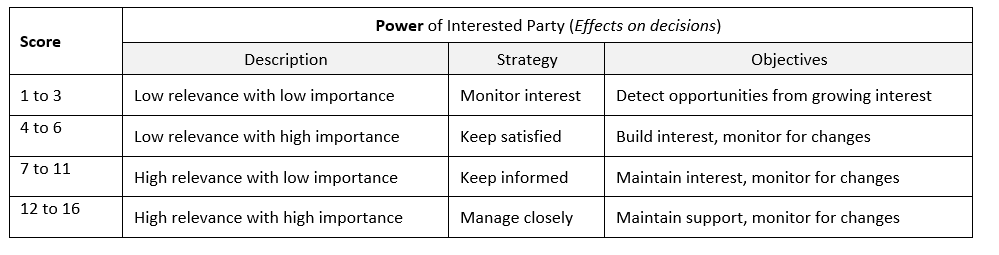
Department Managers, together with the Head of BXG, decide on how to address each need—either by updating internal processes, adjusting project activities, or aligning objectives. These decisions are submitted to Top Management for review and approval using the QEHS Context & Interested Parties matrix.
1.4.4 Monitoring and Review
Each Department Manager must reassess stakeholder needs:
v When new parties are identified
v When requirements or regulations change
v During audits or reviews
v When mitigation strategies require revision.
Reassessments include updates to plans, resource allocations, and timelines. Any major changes must be reviewed with Top Management. The effectiveness of actions taken is monitored and evaluated regularly.
1.5 Process Matrix & Application
1.5.1 Process Matrix
NT uses a dedicated Process Matrix Template to map how each requirement of ISO 9001:2015, ISO 14001:2015, and ISO 45001:2018 is applied across our operations.
This template:
v Aligns each ISO clause with NT’s core, management, and support processes
v Shows how processes interact and depend on each other
v Helps ensure that all applicable ISO requirements are addressed within the IMS
The Head of BXG, together with Top Management, is responsible for preparing, reviewing, and updating the Process Matrix to ensure it remains current and reflective of NT’s evolving service landscape.
1.5.2 Process Application
NT also uses a Process Application Template to clearly define how ISO requirements are applied at the functional level. This tool:
v Maps ISO clauses to specific functions, departments, or project teams
v Shows how responsibilities for quality, environmental, and OH&S requirements are distributed
v Supports cross-functional coordination and helps assign accountability
v Forms the basis for NT’s internal audit program
Together, the Process Matrix and Process Application templates serve as a roadmap for NT’s Integrated Management System. They are used by internal teams, auditors, and external stakeholders to understand how our processes align with ISO standards and contribute to continuous improvement.
These templates also ensure our consultancy services are delivered consistently across different domains, including Telecom, ICT, Power Utility, and Government sectors.
1.6 Forms & Records
All documents and records generated through this Organizational Context procedure are managed as per NT’s Documented Information Control Procedure. This ensures proper storage, version control, access rights, and retrieval.
The following templates and forms are used to support this procedure:
All records are stored in digital format and updated as part of our Management Review Cycle. It is the responsibility of each process owner to ensure that these documents remain up to date and are available during audits or upon request.
1. Introduction & Purpose
The purpose of this procedure is to ensure that all relevant documented
information and organizational knowledge which forms an integral part of our
quality management system is managed under controlled conditions and that all
documented information is reviewed and approved by authorized personnel prior
to issue.
1.1 Process Activity Map
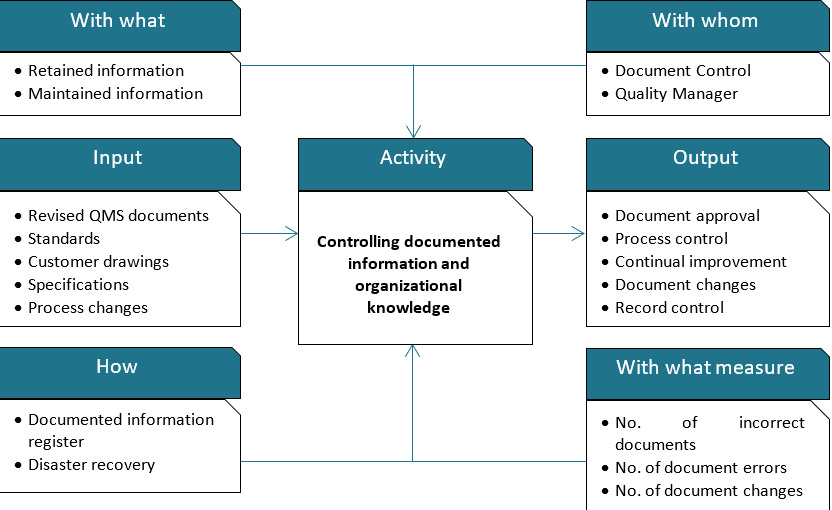
1.2 References
1.3 Definitions
2. Application and Scope
2.1 Application
The Document Control Policy applies to all departments, employees, contractors, and external parties involved in the creation, review, approval, distribution, storage, and archiving of organizational documents. It is mandatory for all official documents, including but not limited to policies, procedures, work instructions, forms, contracts, reports, project records, and external communications. The policy ensures consistent document management practices across the organization to support operational efficiency, quality assurance, and regulatory compliance.
2.2 Scope
This policy encompasses all types of documents generated, utilized, or maintained by the organization, including physical and digital formats. It includes the following aspects:
1. Document Creation and Identification: Establishing clear guidelines for naming, coding, and categorizing documents to ensure ease of identification and retrieval.
2. Version Control: Managing document revisions to maintain accuracy, traceability, and integrity.
3. Approval and Authorization: Ensuring that all documents are reviewed and approved by designated authorities before dissemination.
4. Access and Distribution: Defining access levels and distribution methods to protect document confidentiality and ensure availability to relevant stakeholders.
5. Retention and Archiving: Establishing protocols for document retention periods, secure storage, and systematic archiving for future reference.
6. Compliance and Auditing: Ensuring that document management practices align with internal policies, industry standards, and regulatory requirements.
This policy applies across all operational, managerial, and strategic levels within the organization, reinforcing a unified approach to document control and governance.
3. Policy Description
3.1 Business Units and Function Codes
3.2 Document Types and Related Code
4. Document Standards
4.1Document Coverage
This section covers formatting, layout and document arrangement issues. It defines text fonts, heading styles, table of contents, logos and other similar issues linked to achieving that “uniform look”.
The requirements of this document cover all documents, reports, offers, contracts, presentations, and other types of documents that are prepared for and by NT. The requirements of this document apply to all word documents. For spreadsheets (Excel) and presentations (PowerPoint), the requirements apply as far as practical for each type of document.
Some items are marked “Optional” in the detailed description that follows. A certain flexibility and “freedom” are allowed for these items, however, the description included here for these items should be considered a guideline to achieve conformity between documents and should not be deviated from unless clear benefits otherwise may be achieved.
The templates will be available for download from the NT SharePoint server.
4.2 General Standard Issues
The following table lists common and general document standards. The templates described in Appendix B are set up to match these requirements.
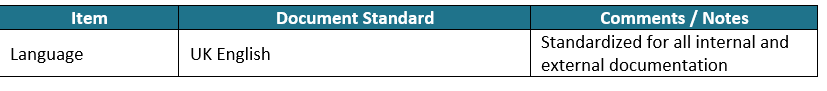
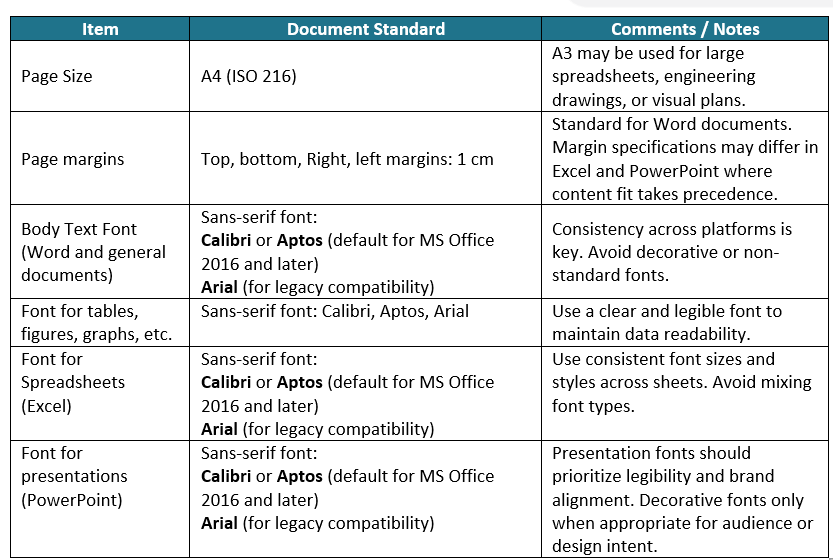
4.3 Usage of NT Logo
All official NT documents shall include the approved NT logo to ensure consistency and alignment with corporate branding guidelines.
v For Word and Excel documents, the NT logo must be positioned in the top right corner of the page. Refer to the header of this document as a standard example.
v For PowerPoint presentations, employees must use the official NT presentation template, which incorporates the logo and design elements in accordance with NT branding standards. This template is available for download from the designated company repository.
4.3 Document Control Page
All documents that formally represent NT—whether for external submission or internal governance—must include a Document Control Page. This ensures that the document has been properly prepared, reviewed, and approved in accordance with NT’s established quality standards.
v Documents Requiring a Document Control Page Include:
o External documents such as:
§ Reports, studies, technical analyses, and similar deliverables
§ Offers, proposals, quotations, and related commercial submissions
§ Company presentations shared with clients or external stakeholders
o Internal documents that define or govern:
§ Work performance standards
§ Business policies and procedures
§ Operational methodologies and frameworks
v Exemptions:
A Document Control Page is not required for internal documents that:
§ Present informal ideas or viewpoints
§ Serve as early-stage drafts or internal working documents
§ Are not intended for formal approval or external circulation
v Required Contents of the Document Control Page:
The Document Control Page must include the following sections:
§ Document Identification: Title, document reference number, and version number
§ Revision History: Version log, issue dates, and a summary of key changes
§ Approval Information: Names and roles of the document owner (creator), reviewer(s), and final approver(s)
5. Principles of Document Naming, Numbering and Structure
The Naming and Numbering Standard is established to ensure consistency, traceability, and efficiency in document and data management. Its primary objectives are to:
v Enable accurate identification of items or documents
v Facilitate quick and efficient retrieval of information within an acceptable time frame
v Prevent duplication, particularly instances where the same item is stored under different names
v Support grouping and comparison of similar items through the use of unique, identifiable characteristics
5.1 Document Reference Number
Any NT document of a level and significance that requires a Document Control Page (ref. section 4.4) shall be issued a Document Reference Number. The reference number shall be built according to the applicable procedure. In principle this consists of:
For non-project-oriented documents, this represents the relevant NT business unit and its Functional section, as per the NT Structure. It consists of:
v Level 1 - Business Area Identifier
This block defines the main business area and functional unit to which the document belongs. Business Unit Code (e.g., FM for Finance)
v Level 2 - Functional unit
v Level 3 - Document Type
v Level 4 - Sequential Document Number
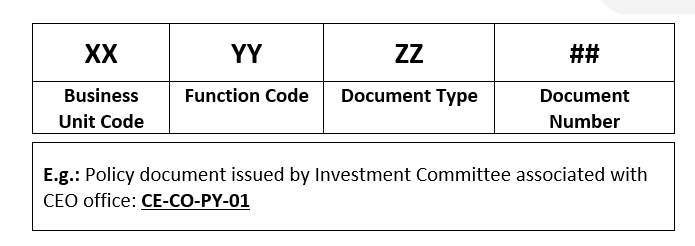
5.2 Document Structure
Each document must be assigned a distinct and descriptive title to ensure clear identification and easy reference. The title should prominently appear at the top of the first page of the document, serving as the primary identifier. Additionally, the title must be included in the header section of every subsequent page to maintain consistency and facilitate document navigation.
The footer of every official document must include the following mandatory elements to ensure proper identification, version control, and traceability:
1. Document Reference Number: A unique identifier assigned to each document to facilitate easy categorization and retrieval within the document management system.
2. Version Number: The current version of the document, indicating its revision history and helping users confirm they are referring to the latest approved version.
3. Issue Date: The date on which the current version of the document was officially released, ensuring clarity regarding its validity and relevance.
4. Page Number: Sequential numbering of pages to ensure clarity in navigation and to prevent misplacement or confusion in multi-page documents.
These elements are essential to maintain consistency, enhance usability, and support effective document control practices across the organization. By standardizing footer content, the organization ensures that documents are easily traceable, up-to-date, and compliant with internal and external audit requirements. This policy applies to all documents issued, revised, or maintained within the organization.
5.3 Document Revision Guidelines
5.3.1 Unique Revision Sequence
Each document must be assigned a unique revision sequence to maintain clarity and version control. The revision sequence should be prominently displayed on the first page of the document and included in the footer section of all pages for consistency. For example, the initial version of a document could be labelled as “Version 1.0.”
5.3.2 Minor Changes and Decimal Versioning
Any modifications to non-substantive or quality-related aspects of the documents such as changes to the header, footer, spacing, privacy levels, numbering, formatting, or correction of typographical errors—must be reflected through an incremental decimal version change. For instance, minor updates will result in a version change from "V1.0" to "V1.1."
5.3.3 Department-Specific Changes in Cross-Functional Documents
If a revision impacts only a single department within a cross-functional process (involving multiple departments) and does not affect the other departments:
· Approval for the changes must be obtained from the competent authority of the relevant Business Unit.
· The Head of Corporate Governance must also approve the changes.
· Other stakeholders must be notified of the revisions as deemed necessary to ensure transparency and alignment.
5.3.4 Tracking Changes in Decimal Versions
To facilitate easy identification of modifications, all changes corresponding to decimal version updates (e.g., "V1.1") must be visually indicated. This can be done by placing a vertical line in the left margin of the page adjacent to the revised content.
5.4 Document Review
Each document must undergo a review or update process either when required or at least once every thirty-six (36) months from its effective release date, based on the main version. Additionally, if a specific review period is defined in the document template, the document should be reviewed in accordance with that period. The earlier of these two timelines should always be adhered to, ensuring the document remains relevant, accurate, and compliant with current standards and practices.
· This policy ensures that all documents:
o Reflect the latest operational, regulatory, or procedural updates.
o Maintain consistency with organizational goals and industry standards.
o Are regularly evaluated to avoid outdated or obsolete information, reducing the risk of errors or non-compliance.
By adhering to this schedule, organizations can maintain a robust document management system that supports operational excellence and continuous improvement.
6. Protection of Documents
6.1 Availability and Controlled Access
All approved documents must be securely stored and made available within the Document Library (E-Library). Access to these documents should be governed by predefined access privileges, ensuring that only authorized personnel can view or edit the content based on their roles and responsibilities. This approach helps maintain the integrity, confidentiality, and security of organizational documents, preventing unauthorized access or unintended alterations.
6.2 Printed Copies and Control Status
Any document printed from the Document Library (E-Library) will be classified as an uncontrolled copy. This means that the printed version is not guaranteed to reflect the most current or accurate information, as updates and revisions are managed exclusively within the E-Library. To mitigate risks associated with outdated or unauthorized use, employees should always refer to the digital version in the E-Library for official and up-to-date content.
6.3 Digital Access Control
The E-Library ensures that documents are centrally managed, with automated version control to maintain accuracy. This minimizes the risk of outdated or conflicting versions circulating within the organization.
6.4 Printed Document Disclaimer
To emphasize the uncontrolled status of printed documents, a disclaimer (e.g., "This is an uncontrolled copy. Refer to the Document Library for the latest version.") should be included on all printed pages. This ensures users are aware of the potential limitations of printed versions.
6.5 Enhanced Security
Access privileges provide an additional layer of security, ensuring that sensitive or classified documents are only available to individuals who need them, in alignment with organizational policies.
7. Announcement of Approved Documents
The Quality Assurance team shall distribute approved documents according to the defined distribution levels. This distribution will occur on a weekly basis, provided there are new documents approved and ready for announcement during that period.
1. Legal & Compliance Requirements
1.1 Introduction & Purpose
The purpose of this procedure is to outline Norconsult Telematics’ methodology for identifying, complying with and monitoring environmental compliance obligations and OHS legal requirements. The compliance and legal requirements relate to the environmental aspects and health and safety hazards that are identified when analyzing the context of our operations and product life cycle(s).
1.1.1 Process Turtle Diagram
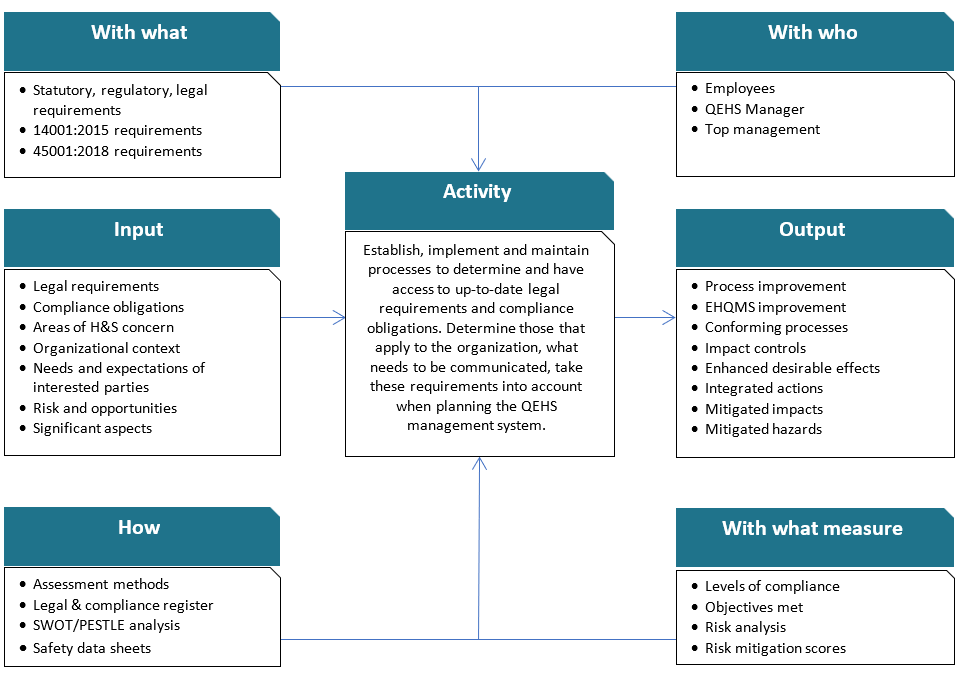
1.1.2 References
1.1.3 Terms & Definitions
1.2 Application & Scope
This procedure applies to all departments and functions at Norconsult Telematics (NT) that are responsible for ensuring legal and compliance obligations are met—particularly those related to environmental protection and occupational health and safety.
It supports NT’s commitment to:
1. Complying with all applicable laws and regulations
2. Fulfilling contractual and voluntary commitments
3. Reducing harm to personnel, clients, and the environment
4. Proactively identifying new compliance obligations
5. Integrating compliance management into NT’s broader risk and opportunity framework
This procedure ensures that NT’s Legal & Compliance Register is actively maintained and that any new or updated requirements are assessed, documented, communicated, and acted upon.
1.3 Compliance Obligations
1.3.1 General
The Head of Business Excellence & Governance (BXG) is responsible for maintaining up-to-date knowledge of legal and compliance obligations and ensuring they are clearly communicated to relevant NT personnel and stakeholders.
All Department Managers must ensure that their teams are aware of and follow applicable legal requirements related to their functions, particularly those affecting:
1. Environmental protection
2. Occupational health and safety
3. Quality and operational performance
1.3.2 Evaluating Obligations
NT evaluates its compliance obligations through:
1. Review of applicable environmental and OH&S legislation
2. Analysis of stakeholder requirements and voluntary commitments
3. Monitoring changes via official publications, legal portals, and advisory sources
Relevant laws are compiled into the Legal & Compliance Register, and updates are tracked through recognized sources. For environmental obligations, NT uses trusted databases and regulatory updates from Saudi authorities and other applicable bodies.
1.3.3 Applicable Legislation
Legislation applicable to NT’s operations is reviewed for relevance and added to the Legal & Compliance Register. Each new or revised law is:
1. Reviewed by the Head of BXG
2. Evaluated for potential impact
3. Assigned to the relevant department or process owner
Examples of legislation relevant to NT may include:
1. Saudi Environmental Law and Regulations
2. Ministry of Environment, Water and Agriculture (MEWA) compliance directives
3. Ministry of Human Resources and Social Development (MHRSD) occupational health and safety requirements
4. Local Municipality environmental permits
5. ISO 14001 and ISO 45001-linked compliance criteria.
The legislation list should reflect NT’s actual geographic and operational footprint, and outdated or UK-based references should be excluded from final documentation.
1.3.4 Monitoring Compliance Obligations
NT uses a formal monitoring process to ensure that all compliance obligations are continually assessed for effectiveness and relevance.
Monitoring includes:
1. Internal audits, reviews, and inspections
2. Self-assessments by functional teams
3. Legal watch updates from recognized KSA regulatory platforms and government bulletins
4. Periodic validation of entries in the Legal & Compliance Register.
The Head of Business Excellence & Governance (BXG) ensures that environmental and OH&S compliance indicators are tracked and reported regularly, and that any non-compliance or change in legislation is addressed promptly.
1.3.5 Updating the Legal & Compliance Register
NT’s Legal & Compliance Register is reviewed and updated at least quarterly. The process includes:
1. Screening for new laws or amendments applicable to NT’s sectors
2. Assessing the relevance of new requirements
3. Assigning responsibilities for implementing controls
4. Communicating updates to departments or process owners
5. Retaining a record of each review for audit and management purposes.
Updates must be reflected in the register and communicated within one calendar month of receipt. This ensures NT stays compliant and avoids legal or operational risks due to outdated information.
1.4 Legal & Other Requirements
1.4.1 General
In addition to legal obligations, NT also monitors other requirements that it voluntarily adopts or agrees to—such as client-imposed standards, ISO frameworks, and industry guidelines.
The Head of Business Excellence & Governance (BXG) tracks these obligations through:
1. Official regulatory websites
2. Legal advisory platforms specific to the KSA region
3. Internal and external audits
4. Alerts from certification and industry bodies (e.g. ISO, GAC, MHRSD).
These requirements are assessed for relevance and integrated into NT’s Legal & Compliance Register.
1.4.2 Evaluating Legal Requirements
The Head of BXG works with Department Managers to:
1. Identify applicable legal and voluntary requirements related to NT’s environmental and OH&S responsibilities
2. Evaluate the impact of these requirements on NT’s processes, risks, and opportunities
3. Determine appropriate mitigation or control actions for non-compliance scenarios
4. Record outcomes and actions in the Legal & Compliance Register.
This evaluation is reviewed regularly, particularly when new regulations are introduced, services are added, or organizational changes occur.
1.4.3 Applicable Legislation
NT monitors a wide range of legal areas, including:
1. Occupational Safety & Health regulations from MHRSD
2. Fire Safety, Equipment, and Facility Use standards
3. Environmental permits and restrictions from MEWA and Municipalities
4. Employee health protection mandates from the Ministry of Health
5. ISO-related obligations and audit recommendations.
NT does not include foreign or irrelevant legislation (such as UK-specific acts) in its documentation.
1.4.4 Monitoring Legal Requirements
The Head of BXG ensures legal requirements are kept current and that:
1. Any changes are evaluated for relevance
2. Assigned departments are informed promptly
3. Records of all evaluations and decisions are maintained
4. Legal compliance is verified through routine audits and inspections.
1.4.5 Updating the Legal & Compliance Register
Like with compliance obligations, the Legal & Compliance Register is updated at least quarterly, with:
1. Reviewed entries documented
2. Responsibility assigned for each item
3. Communication issued to affected functions
4. Follow-up during internal audits and management reviews.
1.5 Management Review
During NT’s management review meetings, the status of legal and compliance obligations is assessed to ensure ongoing alignment with:
1. Client expectations
2. Regulatory changes
3. NT’s own environmental and OH&S policies.
The Head of Business Excellence & Governance (BXG) presents an update on:
1. New or revised legislation relevant to NT operations
2. Compliance status and areas needing improvement
3. Actions taken to manage or mitigate legal and compliance risks
4. Summary of updates to the Legal & Compliance Register
5. Integration of new or updated laws into operational controls.
Special attention is given to:
1. High-risk aspects and hazards
2. Instances of non-compliance
3. Emerging legal trends that could affect NT’s consultancy services
Based on this review, NT may adjust its objectives, targets, and programs to ensure continued compliance and alignment with ISO 14001 and ISO 45001 requirements.
1.5.1 Training
NT ensures that all personnel involved in managing environmental and OH&S compliance have the necessary knowledge and skills to understand their responsibilities and meet legal obligations.
1. Training is coordinated by the Human Resources Department, with technical support from the Head of Business Excellence & Governance (BXG) and includes.
2. Annual compliance training covering key environmental and safety laws relevant to NT operations
3. Induction programs that explain legal responsibilities for new joiners
4. Ad-hoc training sessions for departments impacted by new or updated legislation
5. On-the-job training using policies, procedures, job descriptions, and performance review discussions.
Training content is tailored to reflect NT’s consultancy work and the regulatory frameworks relevant to our sectors in the Kingdom of Saudi Arabia. These sessions help build awareness and accountability across all teams.
1.6 Communication & Participation
Effective communication is essential to ensuring NT staff understand and comply with legal and compliance obligations.
The Head of Business Excellence & Governance (BXG), in collaboration with department heads and HR, ensures that:
1. Legal updates are shared through email alerts, intranet announcements, or internal circulars
2. Key compliance messages are communicated during team meetings and awareness sessions
3. Staff are engaged through workshops and feedback loops when new requirements affect their responsibilities
4. Lessons learned from audits, incidents, or changes in legislation are cascaded across relevant departments.
Awareness and participation are evaluated through:
1. Internal compliance audits
2. Review of documentation and records
3. Site inspections and walkthroughs
4. Staff appraisals and compliance discussions
5. Feedback gathered during management reviews.
This ongoing dialogue helps embed a culture of compliance and ensures NT remains responsive to legal obligations and best practices.
1.7 Forms & Records
All documentation and records generated through NT’s legal and compliance management process are retained and controlled according to the Documented Information Control Procedure. All records are stored in digital format and updated as part of our Management Review Cycle. It is the responsibility of each process owner to ensure that these documents remain up to date and are available during audits or upon request.

1.Risk and Opportunities
1.1 Introduction & Purpose
The purpose of this procedure is to outline Norconsult Telematics’ risk and opportunity management framework when planning for the management system and the activities that comprise it. The risk and opportunity management framework defines our current risk management process, which includes methodology, risk appetite, methods for training and reporting.
1.1.1Process Turtle Map
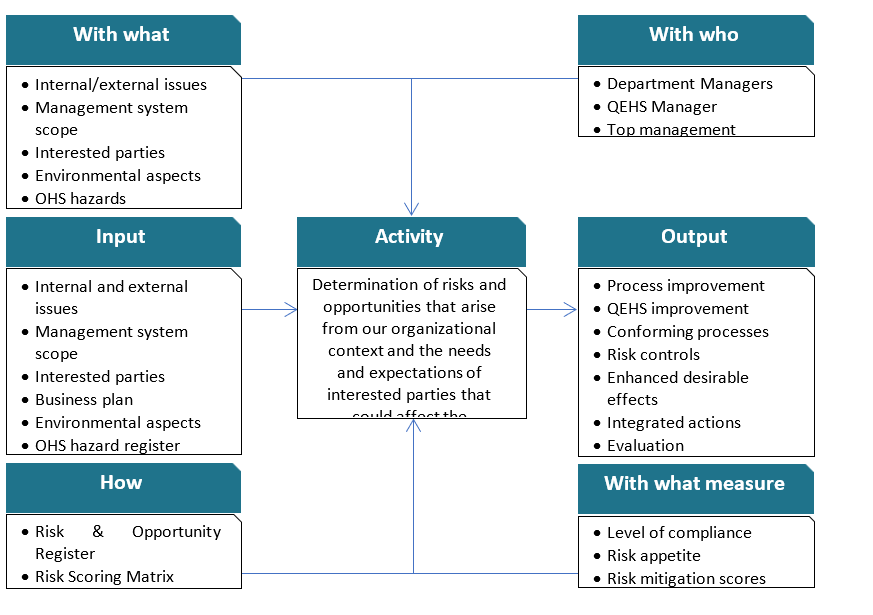
1.1.2 References
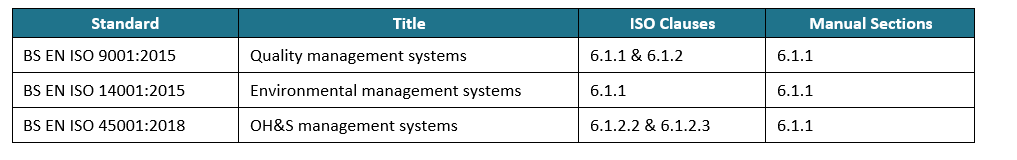
1.1.3 Terms and Definitions

1.2 Application & Scope
At Norconsult Telematics (NT), a risk is defined as anything that could potentially prevent us from achieving our objectives or disrupt the performance of our Integrated Management System (IMS). An opportunity is anything that could enhance our performance, efficiency, or reputation.
This procedure applies to all business units, service lines, and support functions within NT that contribute to our consultancy offerings across Telecom, ICT, Power Utility, and Government sectors.
Risk and opportunity management at NT is:
1. Embedded in strategic planning and project execution
2. Used to support evidence-based decisions and proactive improvement
3. Applied to quality, environmental, health and safety, compliance, financial, and operational aspects
Relevant to both internal operations and external engagements with clients, regulators, and partners
By identifying and addressing risks and opportunities early, NT ensures that we can maintain consistent service delivery, fulfil stakeholder expectations, and strengthen our long-term business sustainability.
1.3Risk Management Process
NT follows a structured, iterative process to identify, assess, manage, and monitor risks that could impact our services, compliance, or strategic goals. The QEHS Manager leads this process, supported by Department Managers and Top Management.
Risks related specifically to environmental aspects and occupational health and safety (OH&S) are also tracked in separate dedicated registers for focused management.
The key responsibilities include:
1. Maintaining up-to-date Risk & Opportunity Registers for all NT projects and departments
2. Evaluating risks across various categories—quality, cost, schedule, compliance, and third-party interactions
3. Ensuring that risk management is practiced consistently across teams
4. Engaging qualified staff and relevant stakeholders in all stages of risk evaluation and treatment.
1.3.1 Context
NT begins risk management by understanding the strategic and operational context of our business:
v Strategic factors include market conditions, regulatory trends, stakeholder strategies, and competitive positioning
v Operational factors include NT’s structure, internal capabilities, past audit findings, KPIs, and resource availability.
This context-setting step ensures that risks are evaluated in relation to NT’s real-world environment and client-specific situations.
1.3.2 Risk Identification
NT identifies risks through a combination of proactive and reactive methods:
1. Workshops and focus groups (e.g. using SWOT, PESTLE techniques)
2. Management interviews and lessons from past projects
3. Intranet submissions for capturing internal incidents or alerts
4. Review of business plans, hazard logs, and legal/compliance registers
Each risk is documented with:
Its cause and effect
1. The assigned Risk Owner who has the authority to manage it
2. Entry into the Risk & Opportunity Register for monitoring and follow-up.
Risks are revisited regularly to ensure they reflect current conditions—such as project milestones, strategy shifts, or performance data (e.g. recurring nonconformities or audit findings).
1.3.3 Risk Assessment
NT uses a qualitative risk matrix to evaluate:
1. Probability (likelihood) of the risk occurring
2. Impact on cost, reputation, compliance, or service delivery
3. Effectiveness of existing controls
The assessment process includes:
1. Documenting existing proactive and reactive control measures
2. Scoring each risk’s likelihood and impact after applying current controls
3. Entering these scores into the Risk Register to define its severity
This allows NT to focus efforts where they are most needed, ensuring the most critical risks are addressed first.
1.3.4 Risk Scoring Matrix
NT uses a risk scoring system to measure the severity of each identified risk and prioritize actions accordingly. Each risk is evaluated using four key criteria:
A. Impact (e.g., financial loss, service disruption, reputational harm)
B. Legal Requirement (e.g., regulatory non-compliance)
C. Likelihood (e.g., probability of occurrence)
D. Frequency (e.g., how often the issue could arise)
Each of these is scored on a scale of 1 (low) to 4 (very high), based on the following table:
Risk Significance Criteria (S1)
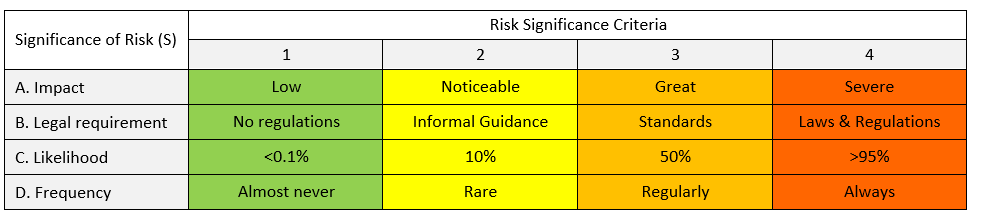
Significance Score (S2)
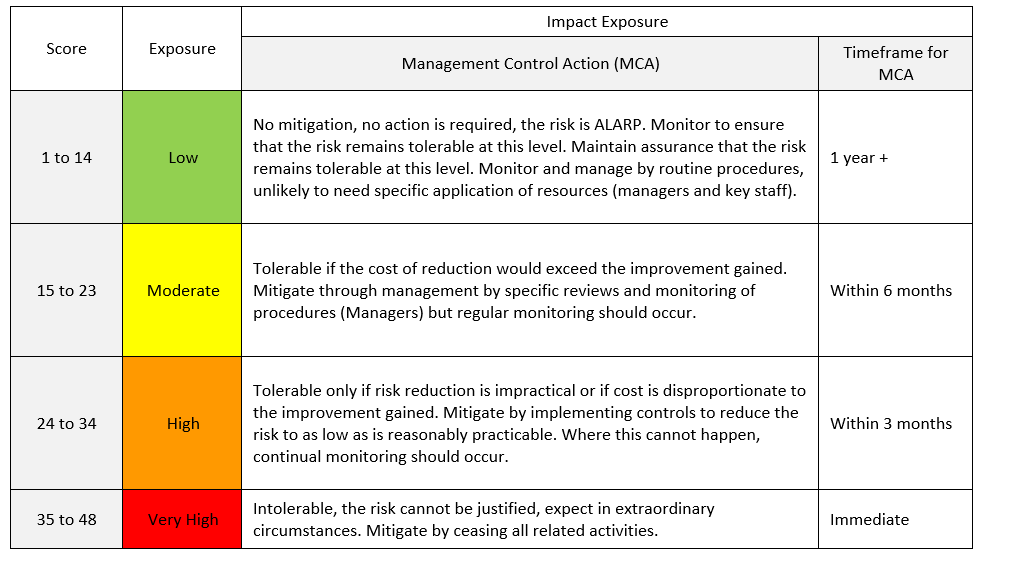
1.3.5 Risk Treatment
Once risks are assessed, NT develops appropriate treatment plans based on their severity and alignment with our risk appetite. The goal is to reduce risks to acceptable levels while ensuring business continuity and compliance.
For each risk, the Risk Owner—with support from the Accountable Manager—will:
1. Decide on the most suitable treatment strategy.
2. Develop specific control actions using the SMART criteria (Specific, Measurable, Achievable, Relevant, Time-bound).
3. Assign an Action Owner who accepts responsibility for implementing the treatment.
1.3.6 Risk Treatment Options
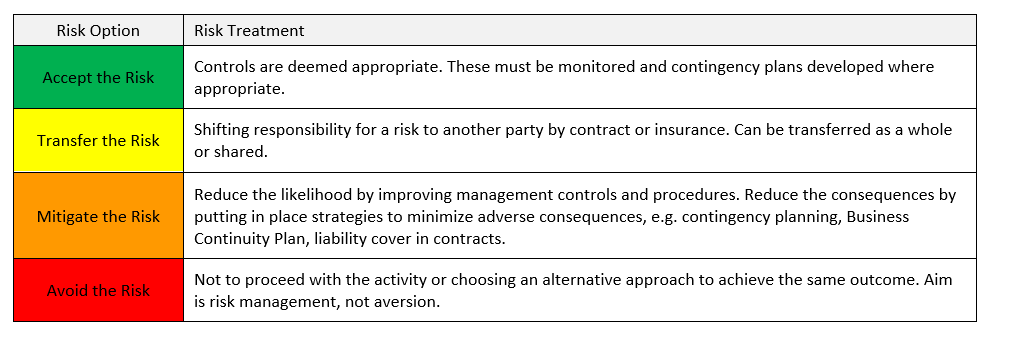
1.3.7Risk Appetite
At NT, risk appetite refers to the level and type of risk we are willing to accept in pursuit of our strategic objectives and value creation. Our tolerance may vary depending on the nature of the project, operational conditions, and stakeholder expectations.
Key factors influencing NT’s risk appetite include:
1. Our capacity to absorb potential impacts (financial, operational, reputational)
2. The criticality of the objective or service
3. Evolving market and regulatory conditions
4. Client requirements and public sector risk sensitivity
5. The level of innovation or change involved in a project.
Risks are always reviewed in light of NT’s current appetite. If a risk exceeds acceptable thresholds, it must be escalated or restructured before proceeding.
1.3.8 Reviewing & Reporting
Regular reviews help NT ensure that risks and opportunities are being effectively managed and that decisions are based on current, accurate information.
The QEHS Manager is responsible for:
1. Engaging with Risk Owners to verify that controls and response actions are still effective
2. Challenging outdated or insufficient mitigation plans
3. Approving the finalized Risk & Opportunity Register for reporting
4. Requesting updates or additional actions if controls are inadequate
Reports generated from the register are used to:
1. Inform Top Management of risk trends, status, and treatment progress
2. Ensure risks are being managed in line with our objectives and risk appetite
3. Provide assurance to internal and external stakeholders, including clients and auditors
All reporting is based on up-to-date data in the risk register and must be completed ahead of scheduled review cycles.
1.3.9 Monitoring
NT carries out continuous and structured monitoring of risk and opportunity processes to ensure compliance, effectiveness, and timely response to changes.
Monitoring activities include:
1. Self-assessments, inspections, and internal audits
2. Performance indicators linked to risk control actions
3. Independent expert reviews, where applicable.
The Head of Business Excellence & Governance (BXG) ensures that each department’s risk controls are operating as intended and that improvements are implemented when performance deviates from targets.
1.3.10 Escalation
At NT, some risks—especially those related to health, safety, or regulatory compliance—may require intervention beyond the authority of a department or process owner.
In such cases, the Head of Business Excellence & Governance (BXG) is responsible for:
1. Escalating unresolved or critical risks to the appropriate level of management
2. Ensuring that risks requiring broader action are reviewed during leadership meetings
Preparing summary reports that highlight:
1. Unassessed or overdue risks
2. Incomplete action plans
3. Systemic issues across departments
Escalation ensures that the right people with sufficient authority and resources are engaged to resolve serious or systemic risks quickly and effectively.
1.3.11 Opportunity Management Process
At NT, an opportunity is defined as any condition or situation that could lead to positive outcomes—such as improved performance, innovation, efficiency, or client satisfaction.
Opportunities may arise from:
v new technologies or service models
v Emerging markets or regulatory changes
v Lessons learned from risk controls (e.g. a safety measure improving morale)
v Internal suggestions or improvement initiatives.
The process to manage opportunities includes:
1. Identification – Opportunities may be logged during project reviews, audits, stakeholder feedback sessions, or as part of risk assessments.
2. Evaluation – Each opportunity is reviewed to assess its potential benefit, cost, and associated risks (including the risks of not acting).
3. Prioritization – High-value opportunities are included in the Risk & Opportunity Register and monitored like any other improvement action.
4. Implementation – Approved opportunities are assigned to an owner who is responsible for planning and executing the improvement.
By actively managing opportunities, NT enhances its ability to innovate, exceed client expectations, and maintain a competitive edge in consultancy services.
1.3.12 Risk & Opportunity Registers
NT maintains structured registers to document, track, and manage all identified risks and opportunities across its operations and service lines.
These registers are maintained by the Head of Business Excellence & Governance (BXG) and are updated in coordination with relevant Department Managers and Risk Owners.
The following registers are used:
1. Risk & Opportunity Register – Consolidates all strategic and operational risks and opportunities.
2. Aspects Identification Register – Tracks environmental aspects and their potential impacts.
3. Hazard Identification Register – Focuses on occupational health and safety hazards.
Compliance & Legal Requirements Register – Captures applicable laws, regulations, licenses, and contractual obligations.
These registers serve as the official source of information during audits, management reviews, and decision-making sessions. They help ensure that risk-related actions are consistently tracked, evaluated, and closed in a timely manner.
1.3.13 Communication
Effective communication is a key element of NT’s risk and opportunity management framework. It ensures transparency, promotes ownership, and fosters a proactive culture across all levels of the organization.
The Head of Business Excellence & Governance (BXG) is responsible for coordinating communication and participation efforts, which include:
1. Sharing updates on identified risks and opportunities with relevant stakeholders
2. Communicating changes in risk ratings, control measures, or treatment strategies
3. Encouraging participation in risk identification through workshops, feedback channels, and project reviews
4. Promoting awareness of the risk framework during onboarding, training, and internal events.
This open approach helps ensure that those responsible for managing risks understand the reasons behind decisions and are equipped to take timely action. It also promotes a shared responsibility across departments and teams.
1.3.14 Forms & Records
All documents and records related to NT’s risk and opportunity management process are maintained in line with the company’s Documented Information Control Procedure.
All records are stored in digital format and updated as part of our Management Review Cycle. It is the responsibility of each process owner to ensure that these documents remain up to date and are available during audits or upon request.
The following templates and registers are used to support this procedure:


1. Competence & Awareness
1.1 Introduction & Purpose
The purpose of this procedure is to define your organization’s process for undertaking the necessary actions and responsibilities for ensuring that the competencies needed to meet customer and other external or internal requirements, applicable to our business, are defined and actions are taken to meet these needs. This procedure also defines the responsibilities for planning, reporting and retaining associated records.
Process Turtle Diagram
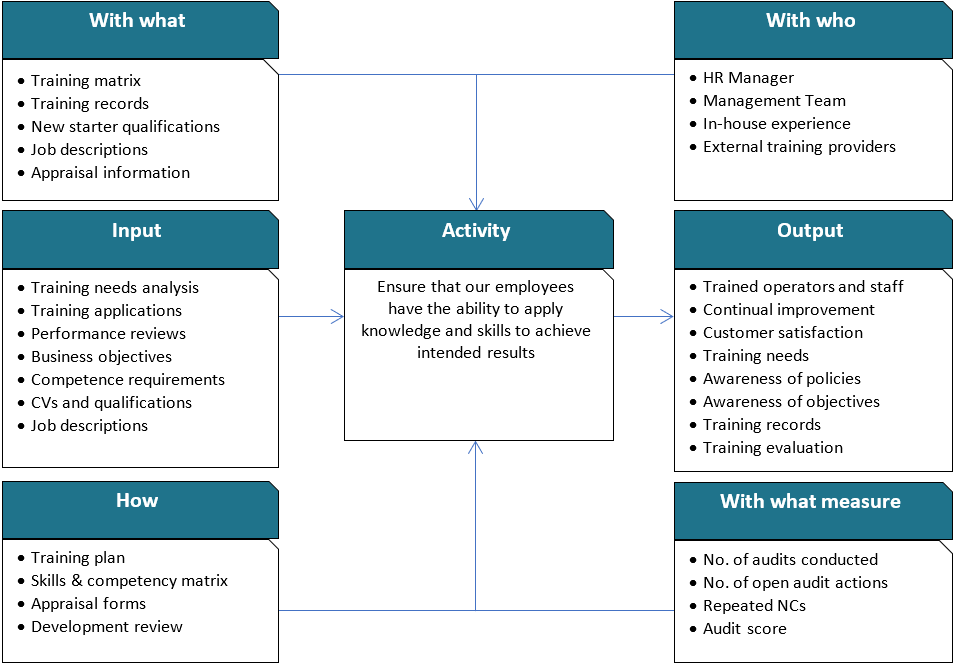
1.1.1 References
1.1.2 Terms & Definitions
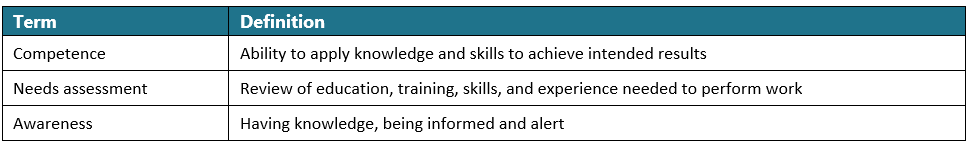
1.2 Application and Scope
1.2.1 Application & Scope
This procedure applies to all NT employees, contractors, and outsourced personnel whose work can affect the quality of services, client satisfaction, or compliance with legal and regulatory requirements.
It covers:
1. Identifying competency needs
2. Providing and tracking training
3. Conducting awareness sessions
4. Reviewing personnel performance and development.
The scope includes both technical and non-technical roles across all departments, projects, and functions within NT.
1.3 Competence & Training
1.3.1 Training Requirements
Each role within NT has defined competencies outlined in job descriptions. Training requirements are identified by:
1. Department Managers based on project or operational needs
2. HR and the Head of BXG based on compliance, audits, or performance gaps
Training needs may also arise from changes in:
1. Client requirements
2. Technology or tools
3. Legal and regulatory updates
1.3.2 Competency Review
Competency is reviewed through:
1. Evaluation of training records
2. Job performance observations
3. Feedback from supervisors or project leads
If a gap is identified, further training or coaching is arranged. Records of competency reviews are maintained in employee files.
1.3.3 Induction Training
All new employees must complete an induction program, which includes:
1. NT’s mission, values, and organizational structure
2. Health, safety, environmental, and quality policies
3. Code of conduct and confidentiality expectations
4. Introduction to key systems, tools, and processes
The induction ensures that all new hires understand their responsibilities from day one.
1.3.4 Development of Skills
NT supports the ongoing development of its employees through:
1. Internal and external training sessions
2. Workshops and seminars
3. Cross-functional exposure
4. Access to relevant learning platforms
Training is aligned with both individual goals and organizational needs.
1.3.5 On-the-Job Training
Where applicable, employees are trained directly within their work environment under the guidance of a qualified supervisor or mentor.
This type of training is used for:
1. New tools or systems
2. Project-specific tasks
3. Process changes or upgrades
Progress is monitored and documented.
1.3.6 Personnel Performance Review
Employee performance is reviewed at least annually and includes:
1. Achievement of objectives
2. Application of learned skills
3. Feedback from peers and clients
4. Adherence to NT’s policies and procedures
Performance reviews are used to identify new training needs and development opportunities.
1.3.7 Review
Training programs and competency development plans are reviewed regularly to:
1. Ensure effectiveness
2. Incorporate employee feedback
3. Adapt to changes in client expectations or business needs
The Head of BXG and Department Managers ensure that improvements are implemented as required.
1.4 Awareness Training
NT ensures that all employees are aware of the organization’s policies, procedures, and their individual roles in achieving quality, environmental, and occupational health & safety goals.
Awareness training includes:
1. NT’s Integrated Management System (IMS) objectives and policies
2. The impact of individual tasks on service quality and compliance
3. Legal, regulatory, and client-specific requirements
4. Emergency procedures and reporting protocols
5. Consequences of not following documented procedures
Awareness is promoted through regular briefings, posters, internal communications, and refresher training sessions.
1.5 Training Evaluation
NT evaluates the effectiveness of all training and awareness sessions to ensure they result in improved competence and performance.
Evaluation methods may include:
1. Feedback forms or surveys completed after training
2. Observation of job performance by supervisors
3. Post-training assessments or quizzes
4. Tracking improvements in KPIs or reduced errors
If training is found to be ineffective, it is revised or replaced, and additional support may be provided to affected employees.
The Head of BXG and HR ensure training evaluation results are reviewed and acted upon.
1.6 Forms and Records
All training and competency records are manta
Records
ined according to NT’s Documented Information Control Procedure. These records ensure traceability, support audits, and provide evidence of compliance with ISO requirements.

All records are stored in digital format and updated as part of our Management Review Cycle. It is the responsibility of each process owner to ensure that these documents remain up to date and are available during audits or upon request.

1.Customer Satisfaction
1.1Introduction & Purpose
The purpose of this procedure is to describe the methods for measuring, monitoring and interpreting customer perception information to determine whether Norconsult Telematics is meeting customer requirements. Norconsult Telematics recognizes that the customer feedback process has important links and interfaces between other management system process that include, but are not limited to; customer communication, design and development validation, design and development changes and process validation.
1.1.1 Process Turtle Diagram
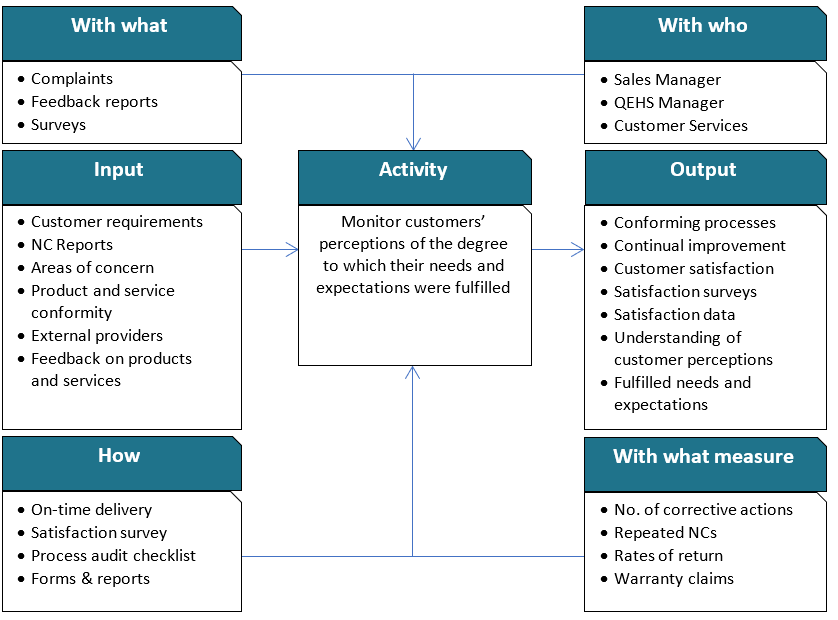
1.1.2 References
1.1.3 Terms and Definitions
1.2 Application and Scope
This procedure applies to all NT departments and projects that interact with customers. It covers how customer satisfaction is:
1. Collected through surveys and direct feedback
2. Monitored by analyzing data and trends
3. Evaluated to identify improvement opportunities
4. Used to enhance services and strengthen relationships
The process ensures NT consistently meets customer needs and uses feedback to drive continuous improvement across the organization.
1.3 Responsibilities
1.4 Controlling Customer Satisfaction
1.4.1 Customer Satisfaction Surveys
NT conducts periodic customer satisfaction surveys to evaluate the quality of its services and interactions. These surveys are shared:
1. At the end of major projects
2. On an annual basis
3. Or when requested by clients
Surveys cover areas such as communication, technical performance, delivery timelines, support, and overall satisfaction.
Responses are reviewed by the Head of BXG, and the results are compiled and analyzed to identify strengths and areas for improvement.
1.4.2 Customer Feedback
In addition to formal surveys, NT welcomes and records all feedback received through:
1. Emails and phone calls
2. Verbal comments during meetings or site visits
3. Social media or digital platforms (if applicable)
Feedback is shared with relevant teams for action. Positive feedback is recognized, while concerns or complaints are logged and followed up through the complaints process.
1.4.3 Customer Data Analysis
Collected feedback and survey data are:
1. Analyzed to identify patterns and trends
2. Measured against performance indicators or targets
3. Used to inform decisions at management reviews
The Head of BXG prepares summary reports and shares them with Top Management to ensure visibility and accountability.
1.4.4 Returns and Warranty Claims
Although rare in a consulting environment, if any service component must be reworked or a client raises a claim:
1. The issue is logged as a non-conformity
2. The responsible department investigates the cause
3. Corrective action is taken to address the concern and prevent recurrence
Records of such cases are maintained for analysis and included in performance reviews.
1.4.5 Monitoring Effectiveness of Operation Control
NT tracks how well its processes are performing in meeting customer expectations. This includes monitoring:
1. Service delivery timelines
2. Issue resolution turnaround
3. Client communication and responsiveness
4. Overall satisfaction scores from surveys
Ineffective controls are escalated to Top Management, and corrective actions are taken where needed.
1.4.6 Review
All customer satisfaction data is reviewed regularly by the Head of BXG and during Management Review Meetings.
The review includes:
1. Trends in feedback and complaints
2. Survey response rates and satisfaction levels
3. Impact of improvement actions taken
Opportunities to enhance customer engagement and service quality.
1.5 Forms and Records
All records related to customer satisfaction are maintained as per NT’s Documented Information Control Procedure. These documents provide evidence of customer interaction, feedback trends, and actions taken.
The following are the key forms and records used:

All records are stored in digital format and updated as part of our Management Review Cycle. It is the responsibility of each process owner to ensure that these documents remain up to date and are available during audits or upon request.
1.6 Customer Complaints Process Map
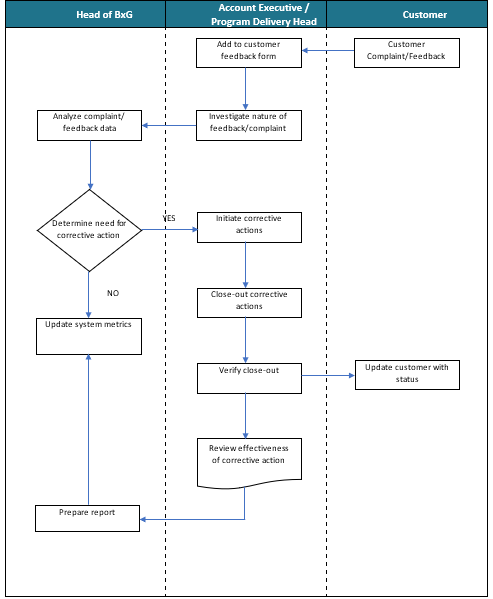

1 Management Review
1.1 Introduction & Purpose
The purpose of this procedure is to define Norconsult Telematics’ process for undertaking management reviews in order to assess the effectiveness of the application of our integrated management system and its compliance to ISO 9001:2015, ISO 14001:2015 and ISO 45001:2018. This procedure also defines the responsibilities for planning, conducting, reporting results and retaining associated records.
1.1.1 Process Turtle Diagram
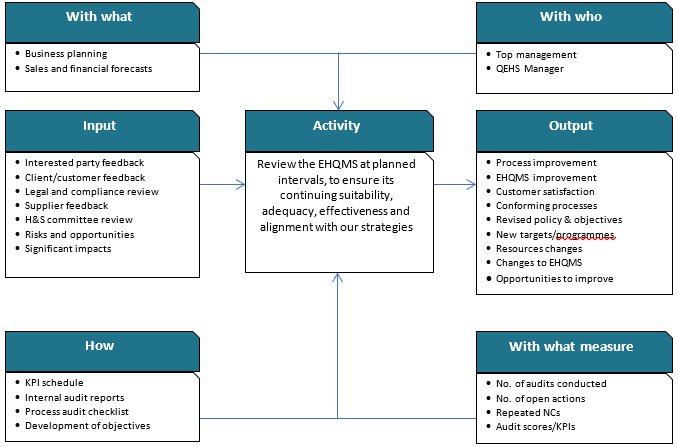
1.1.2 References
1.1.3 Terms and Definitions
1.2 Application & Scope
This procedure applies to all functions and departments within NT. It governs how Management Reviews are conducted to evaluate the performance of the Integrated Management System (IMS), covering:
1. Quality (ISO 9001)
2. Environmental (ISO 14001)
3. Occupational Health & Safety (ISO 45001)
The reviews assess whether the system remains suitable, adequate, and effective, and whether it aligns with NT’s strategic goals and legal obligations. This process also helps prioritize actions for improvement across all operational areas.
1.3 Management Review
1.3.1 General
NT’s Management Reviews are conducted at least once a year by Top Management. These reviews are planned and facilitated by the Head of Business Excellence & Governance (BXG) and may include additional sessions based on:
1. Client or regulatory requirements
2. Significant internal or external changes
3. Major incidents or performance issues
The goal is to ensure the Integrated Management System is working effectively, supports NT’s objectives, and remains compliant with ISO standards and client expectations.
1.3.2 Review Input
Management Review meetings must include the following inputs:
1. Status of actions from previous management reviews
2. Results of internal and external audits
3. Customer feedback and satisfaction trends
4. Process and service performance (including KPIs)
5. Status of preventive and corrective actions
6. Updates on risks and opportunities
7. Changes in legal, regulatory, or contractual obligations
8. Resource adequacy (staffing, tools, training)
9. Follow-up from previous reviews
10. Feedback from interested parties
11. Recommendations for improvement
All inputs are compiled and submitted ahead of the meeting to ensure informed discussion and decision-making.
1.3.3 Policies, Objectives & KPIs
During the review, NT’s policies, objectives, and KPIs are evaluated to confirm that:
1. They remain relevant and aligned with the organization’s strategic direction
2. Targets are being met or adjusted based on trends and risk assessments
3. Any changes in customer expectations, technology, or regulations are reflected in updated objectives
The review may lead to revisions of NT’s policy statements, updated KPIs, or redefined departmental targets.
1.3.4 Review Output
The outcomes of the Management Review include:
1. Decisions and action plans for improving the effectiveness of the IMS
2. Changes to policies, objectives, or resource allocations
3. Actions to improve customer satisfaction
4. Opportunities for process optimization or system enhancement
5. Assignments of responsibility and due dates for follow-up actions
All decisions and actions from the meeting are documented in the Management Review Minutes and tracked until completion.
1.4 Forms & Records
All records related to Management Reviews are managed in accordance with NT’s Documented Information Control Procedure. These records provide evidence of leadership involvement, system evaluation, and continual improvement actions.
The following documents are maintained:

All records are stored in digital format and updated as part of our Management Review Cycle. It is the responsibility of each process owner to ensure that these documents remain up to date and are available during audits or upon request.
1.5 Management Review Process Map
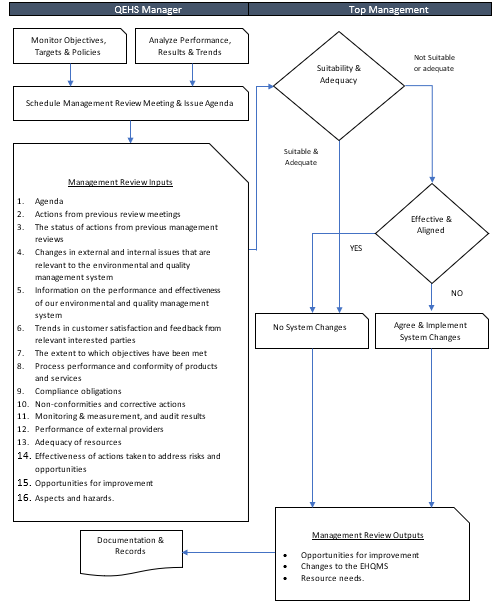

1. Internal Audits
1.1 Introduction and Purpose
The purpose of this procedure is to define Norconsult Telematics’ process for undertaking internal audits, process audits, and supplier audits in order to assess the effectiveness of the application of our QEHS management system and its compliance to ISO 9001:2015, ISO 14001:2015 and ISO 45001:2018. This procedure also defines the process for programming and conducting internal audits, reporting results and retaining associated records.
1.1.1 Process Turtle Diagram
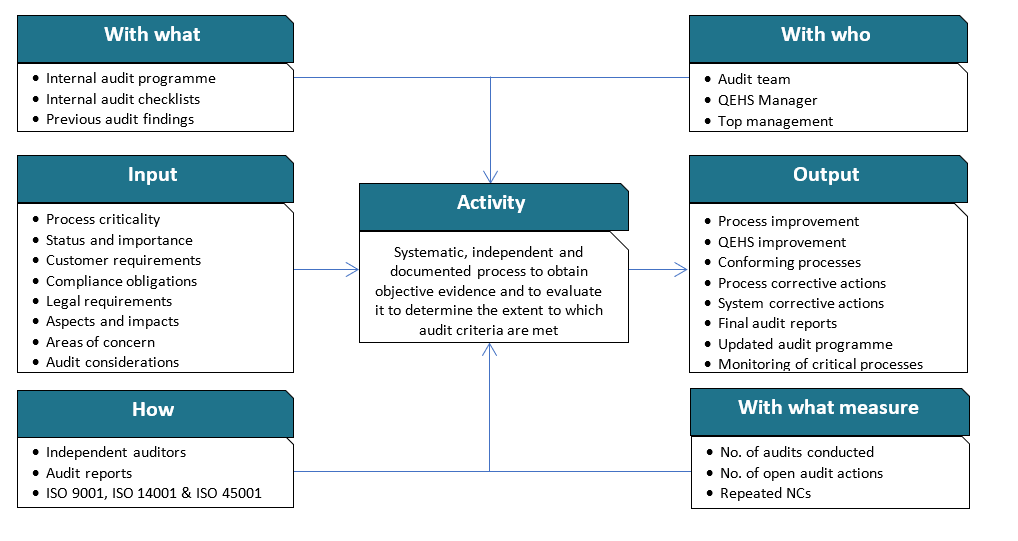
1.1.2 References
1.1.3 Terms & Definitions
1.2 Application & Scope
This procedure applies to all NT departments, processes, and projects where the Integrated Management System (IMS) is implemented. It includes audits related to:
1. Quality (ISO 9001)
2. Environment (ISO 14001)
3. Occupational Health & Safety (ISO 45001)
Audits may be scheduled or unscheduled and can be full-scope (covering the entire system) or focused (targeting high-risk or underperforming areas).
Audits verify that:
1. Policies and procedures are followed
2. Risk controls are effective
3. Legal and contractual obligations are met
4. Continual improvement is actively pursued.
1.3 Selecting Internal Auditors
Audits are conducted by trained NT personnel who are independent of the areas being audited to maintain objectivity.
The Head of Business Excellence & Governance (BXG) is responsible for:
1. Maintaining a list of approved internal auditors
2. Assigning auditors with the appropriate technical knowledge and impartiality
3. Ensuring auditors are trained in ISO 19011 and NT’s audit procedures
4. Rotating auditors periodically to enhance impartiality and bring fresh insight.
Internal auditors must:
1. Understand applicable ISO standards and NT procedures
2. Apply systematic, evidence-based auditing techniques
3. Respect confidentiality and neutrality throughout the process.
1.4 Audit Planning
Audit planning ensures that audits are focused, efficient, and aligned with NT’s business priorities and risks.
The Head of Business Excellence & Governance (BXG) is responsible for developing an Annual Internal Audit Plan based on:
1. The significance and complexity of processes
2. Results of previous audits and recurring issues
3. Areas with high risk, change, or regulatory exposure
4. Management priorities and upcoming external audits
The plan includes:
1. Audit objectives, scope, and criteria
2. Department or process to be audited
3. Assigned auditor(s)
4. Audit schedule and frequency.
The plan is reviewed quarterly and adjusted as needed based on:
1. New services or projects
2. Major process changes
3. Non-conformities or incidents
4. Client or regulatory concerns.
1.4.1 Preparing for an Audit
Before each audit:
1. The auditor reviews relevant documents (procedures, KPIs, past audits, complaints, risk assessments)
2. An Audit Plan is prepared, including:
a. Audit objectives and scope
b. Locations and departments
c. Audit team members
d. Time schedule and meeting plan.
3. Audit checklists may be developed based on ISO clauses and NT internal controls.
1.4.2 Opening Meeting
An opening meeting is conducted with:
1.The Process Owner
2. Departmental representatives
3. Assigned internal auditors
The auditor explains:
1. The audit objective and scope
2. Roles and expectations
3. Confidentiality and impartiality
4. The audit schedule and methods.
Any questions from the auditees are addressed before starting the audit.
1.5 Conducting the Audit
During the audit, internal auditors:
1. Collect objective evidence through:
a. Interviews with staff
b. Review of documents and records
c. Direct observation of activities and conditions
2. Use a risk-based approach to focus on:
a. Critical controls and processes
b. Areas with past non-conformities or complaints
3. Record all findings clearly and factually
4. Note positive practices or improvement opportunities.
Auditors maintain professionalism, neutrality, and discretion throughout. If a major concern is identified during the audit, it is immediately escalated to the Head of Business Excellence & Governance (BXG).
1.6 Audit Findings & Reporting
Audit findings are categorized as:
1. Conformities – Requirements are met
2. Observations – Areas with potential for improvement
3. Non-conformities – Requirements not met, requiring corrective action
After completing fieldwork:
1. The auditor conducts a closing meeting with the auditee and relevant stakeholders
2. A draft Audit Report is prepared and reviewed by the Head of BXG
3. The final report includes:
a. Audit scope, date, and participants
b. Summary of findings and evidence
c. Details of non-conformities
d. Agreed corrective actions and responsible owners
e. Deadline for action closure.
Reports are submitted within five working days of audit completion. They are logged and tracked using NT’s Audit Tracking Register.
1.7 Corrective Actions & Follow-Up
All non-conformities identified during internal audits must be addressed through corrective action.
Responsibilities:
1. Process Owners are accountable for.
a. Investigating root causes
b. Developing corrective action plans
c. Implementing and documenting solutions within agreed timelines.
The Head of Business Excellence & Governance (BXG):
1. Reviews and approves corrective actions
2. Tracks closure through the Corrective Action Log
3. Provides support and clarification when needed
Deadlines for closure are based on the severity of the issue and are monitored weekly. If deadlines are missed without valid justification, escalation to Top Management occurs.
1.8 Review of Effectiveness
The effectiveness of each corrective action is verified through:
1. Re-audits
2. Review of updated records and procedures
3. Evidence of sustained improvement.
If the issue persists or recurs:
1.The corrective action is reopened
2. The root cause analysis is reassessed
3. Further action is taken, which may include retraining, process redesign, or escalation.
Effectiveness reviews ensure that changes are fully integrated and that risks have been addressed in a lasting way.
1.9 Forms & Records
All audit-related documentation is maintained according to NT’s Documented Information Control Procedure. These records provide a transparent history of compliance performance and continuous improvement.
The following forms support the internal audit process:
1.10 Internal Audit Process Map
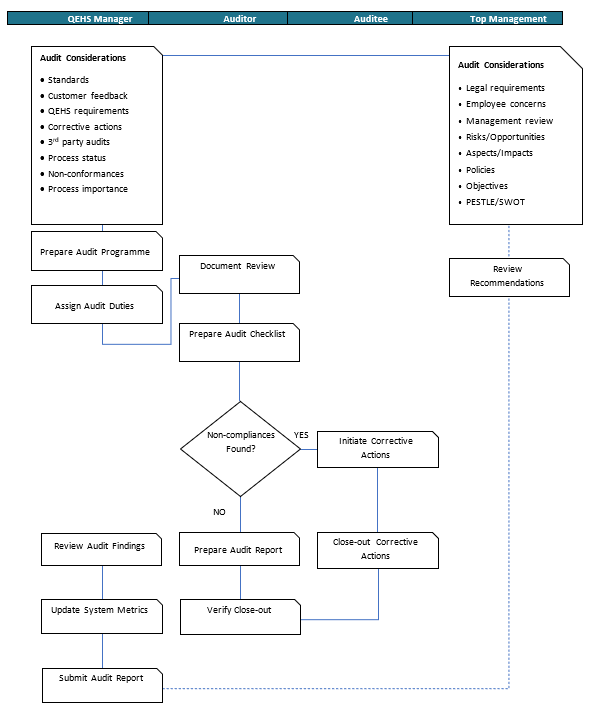

1. Data Analysis & Evaluation
1.1 Introduction & Purpose
The purpose of this procedure is to establish and define the roles and responsibilities for analyzing and reporting management system data in order to drive continual improvement and to facilitate a factual approach to decision making.
1.1.1 Process Turtle Diagram
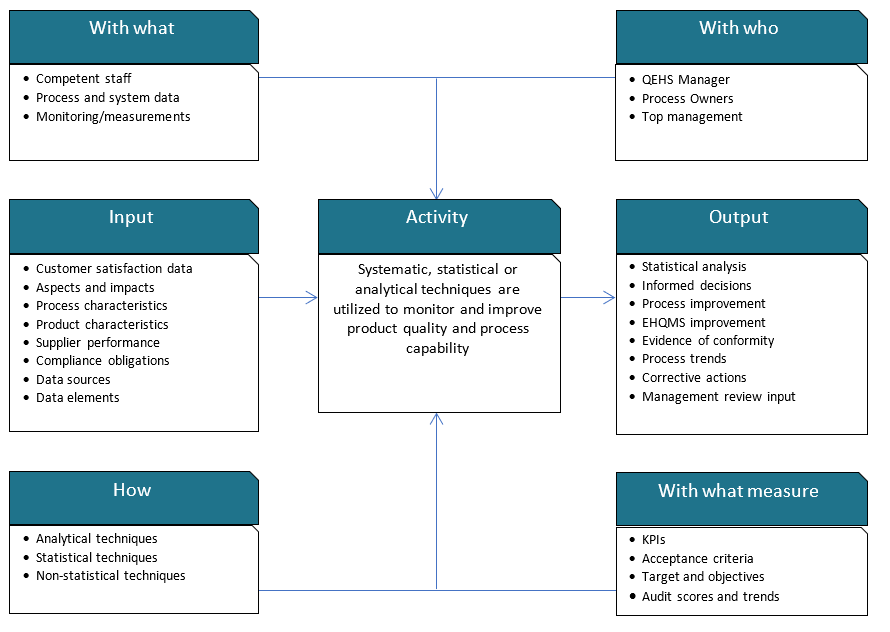
1.1.2 References
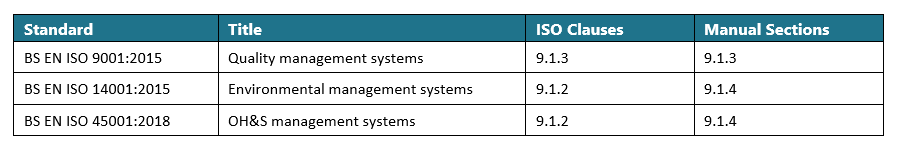
1.1.3 Terms & Definitions
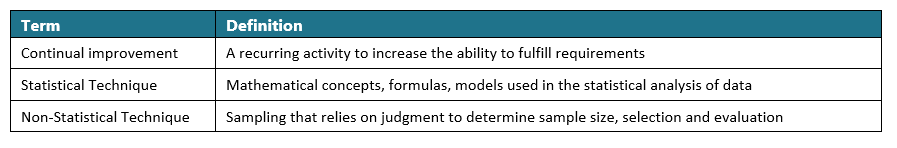
1.2 Application & Scope
This procedure applies to all functions, departments, and projects at NT that generate, process, or rely on data related to:
1. Quality of deliverables and client satisfaction
2. Environmental aspects and compliance metrics
3. Occupational Health & Safety performance
4. Supplier and contractor performance
5. Audit results, incident data, and internal controls.
The procedure ensures consistent data analysis practices that enable NT to make informed decisions, drive performance, and fulfil the requirements of ISO 9001, ISO 14001, and ISO 45001.
1.3 Responsibilities
Process Owners are responsible for:
1. Collecting accurate and relevant data from their functions
2. Submitting data according to the agreed reporting schedule
3. Participating in data review meetings and action planning
Head of Business Excellence & Governance (BXG) is responsible for:
1. Defining data analysis methods and reporting structures
2. Consolidating cross-functional data into dashboards and reports
3. Leading evaluation sessions with Top Management
4. Recommending actions based on trend and performance analysis
5. Ensuring alignment with legal and ISO obligations.
Top Management is responsible for:
1. Reviewing organizational performance based on analyzed data
2. Taking decisions on strategy, resources, and priorities based on findings.
3. Tracking effectiveness of past actions and improvements.
1.4 Data Collection, Monitoring & Analysis
NT applies a structured and consistent approach to collect, monitor, and analyze data relevant to its Integrated Management System.
1.4.1 Monitoring Requirements
Data is collected for areas including:
1. Client satisfaction (surveys, complaints, feedback logs)
2. Project performance (schedule, cost, scope adherence)
3. Process KPIs (effectiveness and efficiency measures)
4. Supplier/Contractor performance (delivery, quality, compliance)
5. Audit results (internal, external, third-party)
6. OH&S incidents (near misses, injuries, unsafe conditions)
7. Environmental metrics (waste, energy, emissions)
8. Corrective and preventive actions (status, closure, recurrence)
Monitoring frequency and sources are defined in NT’s relevant procedures (e.g., Risk Register, KPI Tracker, Audit Plan).
1.4.2 Evaluation Methods
The Head of BXG, with support from Process Owners, evaluates data using a mix of:
1. Statistical tools (trend charts, Pareto, histograms, control charts)
2. Root cause tools (Ishikawa/Fishbone, 5 Whys)
3. Comparative analysis (benchmarking, baseline vs. actual)
4. Dashboards and scorecards (for executive-level decision support)
Key questions include:
1. Are objectives being met?
2. Are there any recurring issues or deviations?
3. Is there evidence of continual improvement?
4. Are risks being effectively managed?
1.4.3 Reporting and Review
Performance results are shared via:
1. Monthly/quarterly management reports
2. Functional reviews with department heads
3. ISO-related Management Review Meetings
Identified issues may lead to corrective actions, updates to objectives, or escalations.
Data from across functions is aggregated to enable holistic decision-making and alignment with NT’s strategic direction.
1.5 Evaluation of Compliance
NT conducts periodic evaluations to confirm that its operations comply with applicable legal requirements, client-imposed obligations, and ISO standards (9001, 14001, and 45001). This ensures ongoing alignment with contractual expectations and regulatory frameworks within the Kingdom of Saudi Arabia.
The Head of Business Excellence & Governance (BXG) is responsible for:
1. Scheduling compliance evaluations based on risk, operational complexity, and legal change frequency
2. Coordinating with functional heads to gather supporting evidence (e.g., permits, licenses, audit logs)
3. Assessing compliance with:
a. Internal IMS procedures
b. Client and stakeholder requirements
c. National laws and regulations relevant to quality, environmental, and OH&S performance.
Outcomes of compliance evaluations are:
1. Documented in the Compliance Register
2. Shared with Top Management and reviewed during Management Review Meetings
3. Used to trigger corrective actions when gaps or risks are identified.
Where applicable, evaluations also feed into legal registers and may support external audits or certification surveillance visits.
1.5.1 Applicable Legislation
NT stays up to date with legal and regulatory changes by monitoring:
1. Laws and regulations issued by Saudi regulatory bodies
2. Industry-specific directives related to occupational safety, environmental protection, and quality
3. Contractual clauses from public and private clients requiring specific compliance
Sources include official government portals, client circulars, and legal consultants where needed.
All applicable laws and their updates are:
1. Documented in the Legal & Compliance Register
2. Reviewed periodically to ensure relevance and applicability
3. Communicated to relevant departments through internal notices and briefing sessions.
1.6 Forms & Records
All records related to data monitoring, evaluation, and compliance are managed in accordance with NT’s Documented Information Control Procedure. These records ensure transparency, audit readiness, and support evidence-based decision-making.
1.7 EHQMS Data Points Process Map
|
Service & Product |
Manufacturing/Engineering |
Management System |
|
Reports and complaints |
Nonconformities and defects |
Nonconformities and complaints |
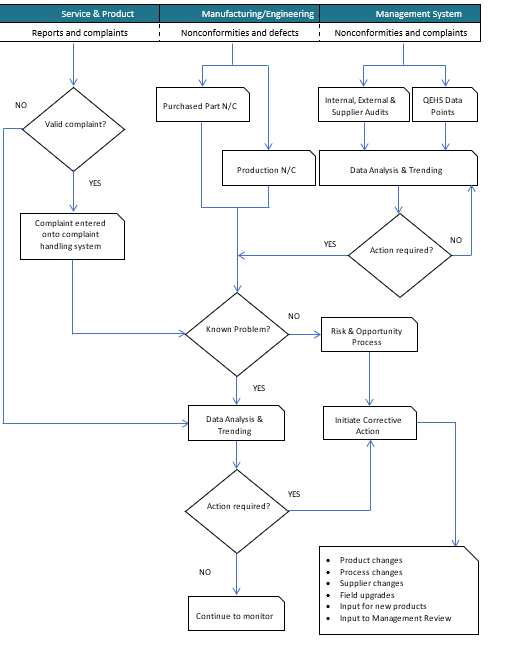
1. Non-conformity & Corrective Action
1.1 Introduction & Purpose
The purpose of this procedure is to establish the process for identifying, documenting and analyzing non-conformities and implementing appropriate corrective action(s). Norconsult telematics’ management system is geared toward the proactive elimination of actual and potential failures. Non-conformities arising from complaints, product and service outputs, and management system processes are investigated and action implemented to prevent their occurrence.
1.1.1
![]() Process Turtle Diagram
Process Turtle Diagram
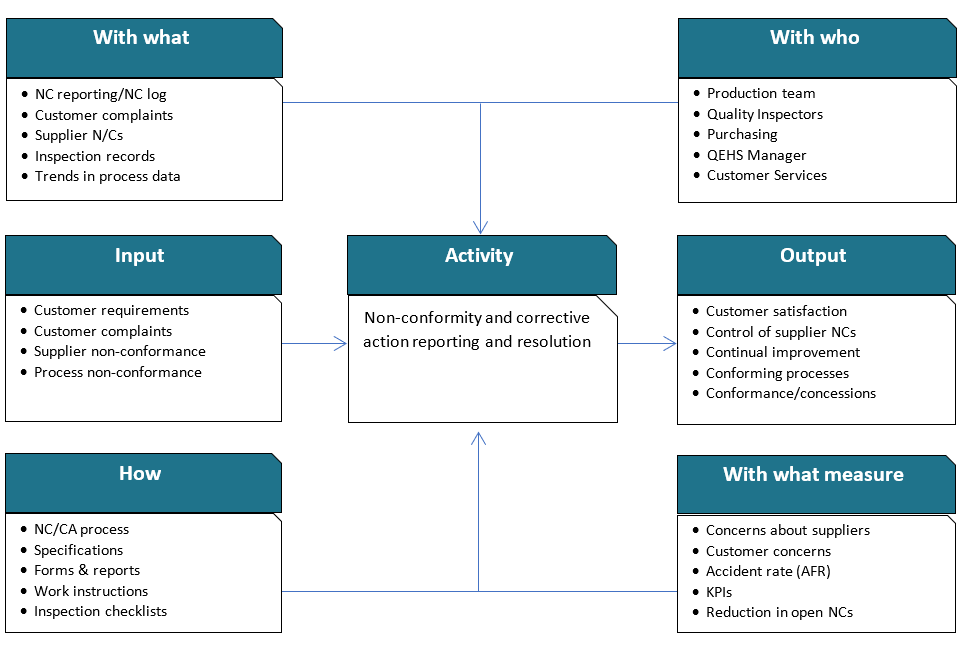
1.1.2 References
1.1.3 Terms & Definitions
1.2 Application & Scope
This procedure applies to all NT departments, services, and operations. It covers:
1. Non-conformities related to products, services, internal processes, or management systems
2. Customer complaints and supplier issues
3. OH&S and environmental system failures
4. Any deviation from procedures, policies, or contractual obligations.
Corrective actions are evaluated based on the severity and risk of the non-conformity and are implemented accordingly. Root cause analysis is mandatory for all significant or repeated issues.
1.3 Responsibilities
All Employees and Process Owners are responsible for:
1. Identifying and reporting non-conformities promptly
2. Supporting containment, investigation, and corrective actions
3. Preventing recurrence through adherence to revised procedures.
Head of Business Excellence & Governance (BXG) is responsible for:
1. Reviewing non-conformity reports and confirming the level of action required
2. Leading root cause analysis and assigning corrective actions
3. Maintaining the Corrective Action Log and related documentation
4. Verifying that corrective actions are closed effectively and prevent recurrence
5. Escalating repeated or major non-conformities to Top Management.
1.4 Reacting to Non-conformities
When a non-conformity is identified, whether from internal reviews, client feedback, or supplier performance, the Head of Business Excellence & Governance (BXG) determines the necessary containment, investigation, and corrective actions.
Repeated or significant non-conformities are escalated to Top Management for resolution.
1.4.1 Customer Returns
When a customer rejects a product or service:
1. The issue is reported to the BXG for review and logging
2. The item is tagged, quarantined, and evaluated for liability
3. If valid, a formal Customer Complaint Report is created
4. A cross-functional team investigates the root cause
5. All findings are recorded, and if requested, shared with the client
6. Site visits are arranged when necessary to review resolution in person.
1.4.2 Supplier Returns
When purchased materials or services are non-conforming:
1. The item is tagged and placed in a designated quarantine area
2. The BXG reviews the case and decides whether to:
a. Rework,
b. Accept under concession,
c. Reject and return to supplier.
Rejected items are logged, and the Finance team is notified to manage credit claims. Suppliers may be required to host corrective action reviews at their facilities.
1.4.3 Process & Management System Non-conformities
If internal processes or system controls fail:
1. Employees report the issue using a Non-Conformity Report or via internal audit
2. The BXG evaluates whether systemic changes are needed
3. Root causes are investigated, and actions are tracked in the corrective action system.
1.4.4 Corrective Action Impact
Where relevant, corrective actions are extended to other similar processes or departments to prevent recurrence elsewhere. These actions are tracked in the Corrective Action Log.
1.4.5 Corrective Action Review
The BXG is responsible for:
1. Reviewing the issue and identifying the root cause
2. Planning, implementing, and verifying corrective actions
3. Updating documentation and revising procedures if needed
4. Escalating unresolved or repeated issues to Top Management.
1.4.6 Implementing Containment Action
Before the root cause is addressed, containment measures must be implemented to:
1. Isolate the issue
2. Prevent escalation or further impact
3. Record initial actions and findings in the Corrective Action Report.
1.4.7 Determining the Causes
Non-conformity and opportunity for improvement may be identified by employees, customer complaints or by management system audit reports. By whichever means a non-conformance is identified, the underlying cause of the non-conformance is investigated.
The Head of Business Excellence & Governance (BXG) reviews any issues raised and completes a non-conformance report to identify root cause and evaluate the level of action required. Repeated non-conformances of the same nature or significant deviations from procedures or the policies are reported to Top management for action and resolution.
1.4.8 Evaluating the Need for Action
Actions are prioritized based on risk:
1. Major: Where client satisfaction, regulatory compliance, or system integrity is compromised
2. Minor: Where internal procedures are not fully followed but do not affect output quality or safety
All major actions are tracked through the Continual Improvement Program and reviewed during Management Review.
1.4.9 Implementing Action
Responsible staff must implement corrective actions within the agreed timeframe. The BXG:
1. Follows up for status updates
2. Verifies closure based on documented evidence
3. Ensures permanent actions are embedded into processes
1.4.10 Verifying the Effectiveness of Actions
Verification is performed by the original requestor or, when necessary, the BXG. If actions are ineffective:
1. A new corrective action is opened
2. Root cause and solution are reassessed
3. Improvements are tracked until resolved
1.4.11 Review
All corrective actions are reviewed during Management Review Meetings to evaluate:
1. Long-term effectiveness
2. Opportunities for replication across other departments
3. Contribution to NT’s business excellence goals.
1.5 Reacting to OHS Non-conformities
If a workplace incident results in serious harm, potential harm, or a near miss, NT responds in accordance with the Incident Investigation Procedure.
If the investigation reveals a failure in the OH&S management system:
1. It is recorded as a formal non-conformity
2. Root cause analysis is conducted
3. Corrective actions are initiated to address both the incident and the system deficiency
4. Effectiveness is verified and reviewed during safety audits and management review meetings.
1.6 Reacting to EMS Non-conformities
Environmental incidents—such as spills, emissions, or permit violations—are handled in accordance with the Emergency Preparedness & Response Procedure.
If the root cause is linked to a weakness in the environmental management system:
1. A non-conformity is logged
2. The Head of Business Excellence & Governance (BXG) leads an investigation to identify root causes and systemic failures
3. Corrective actions are taken to prevent recurrence and minimize environmental impact
4. Follow-up is documented and reviewed by Top Management as part of compliance assurance.
1.7 Forms & Records
All documents and records related to non-conformities and corrective actions are retained and managed in accordance with NT’s Documented Information Control Procedure.

1.8 Non-conformity & Corrective Action Process Map
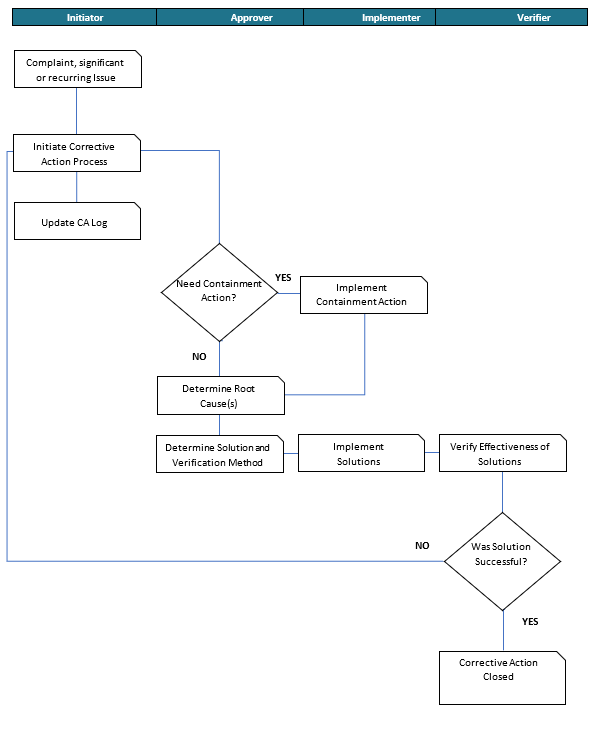
Information Security and Management System (ISMS) Policy (ISO 27K)
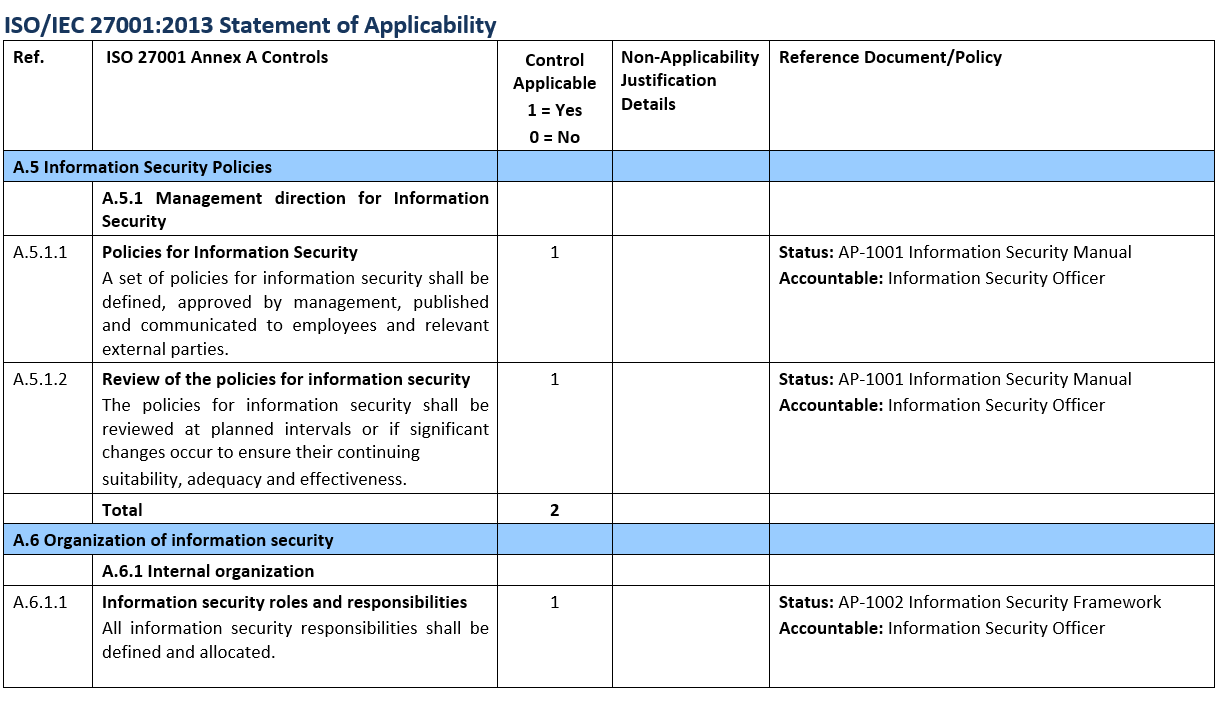
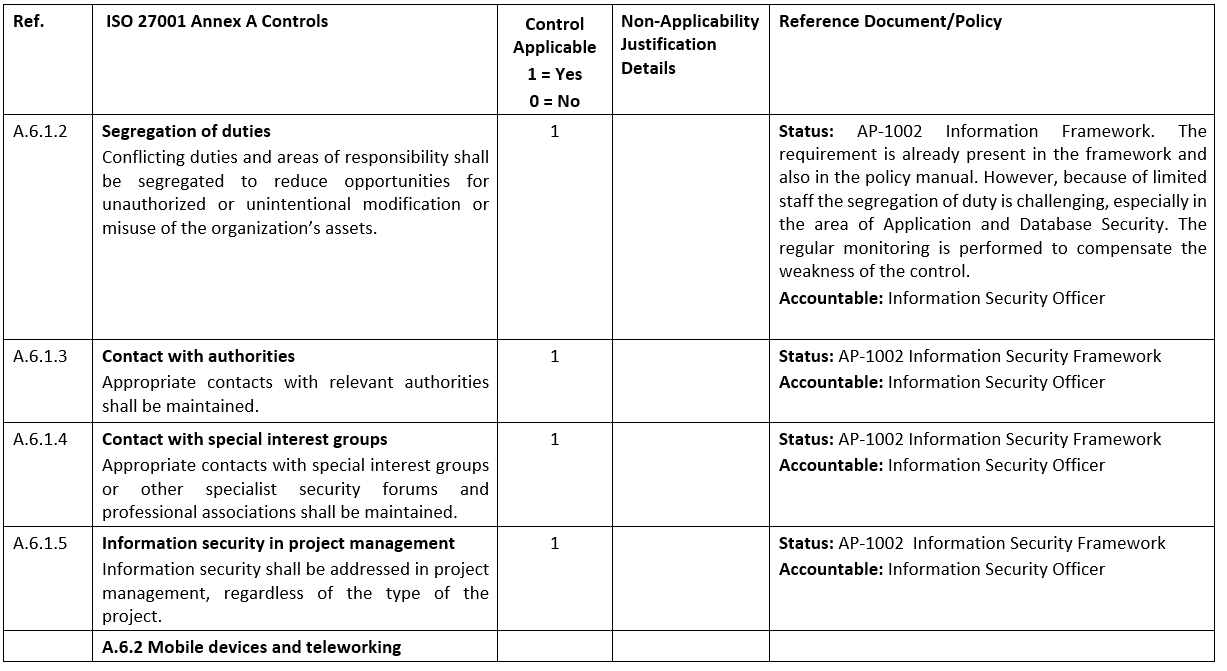
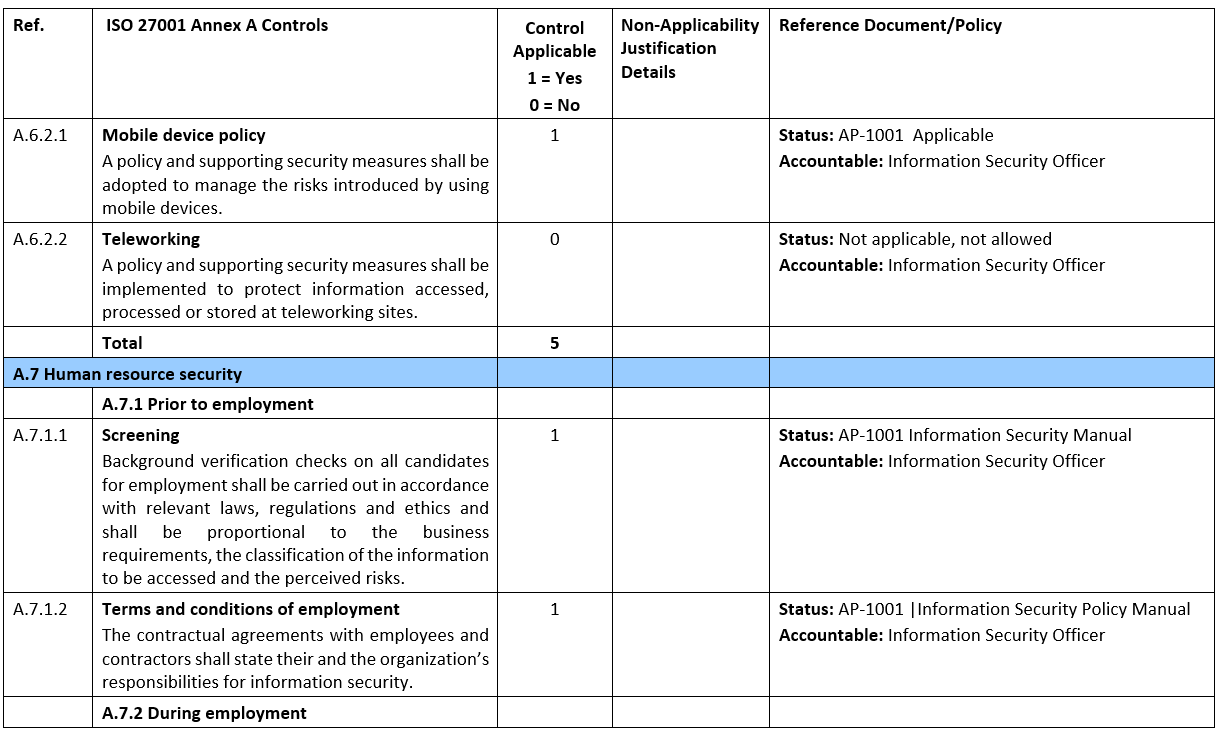
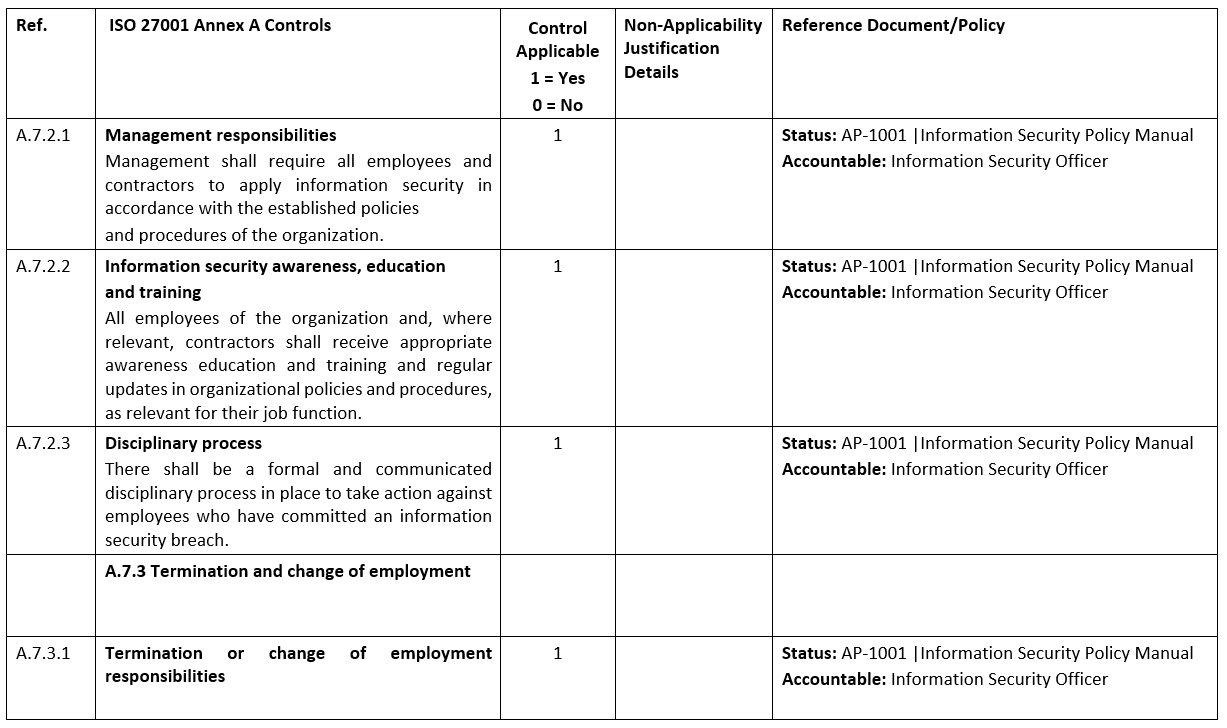
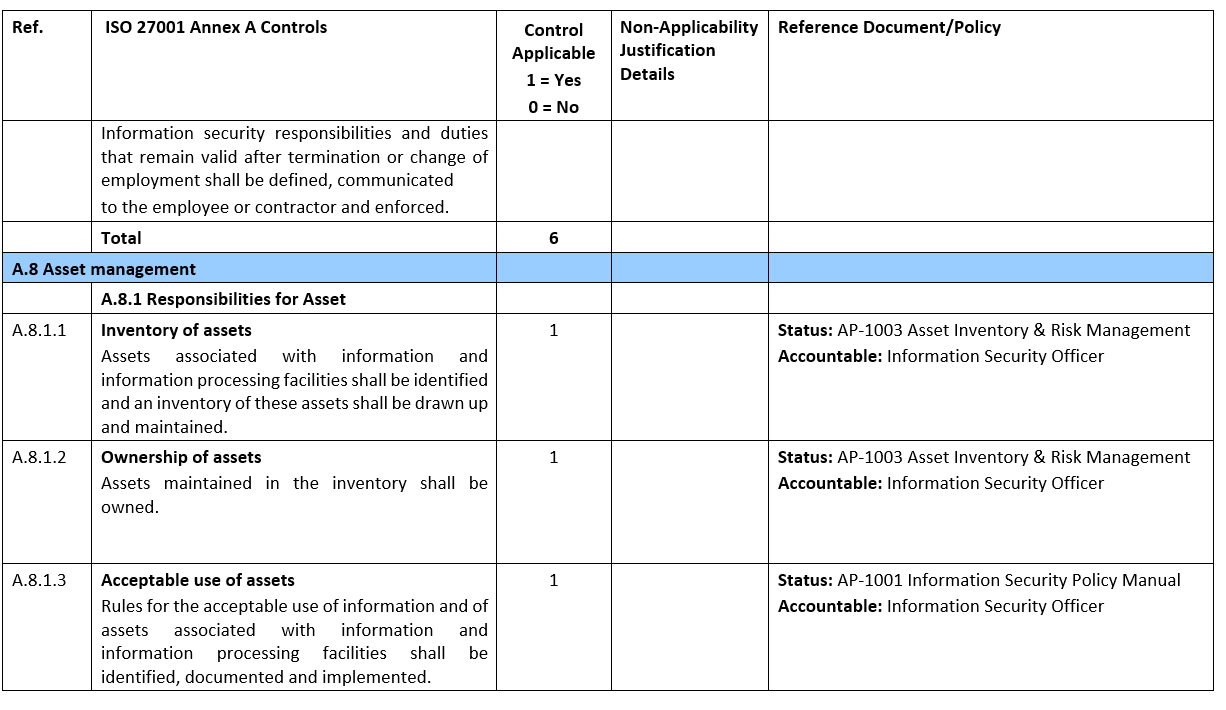
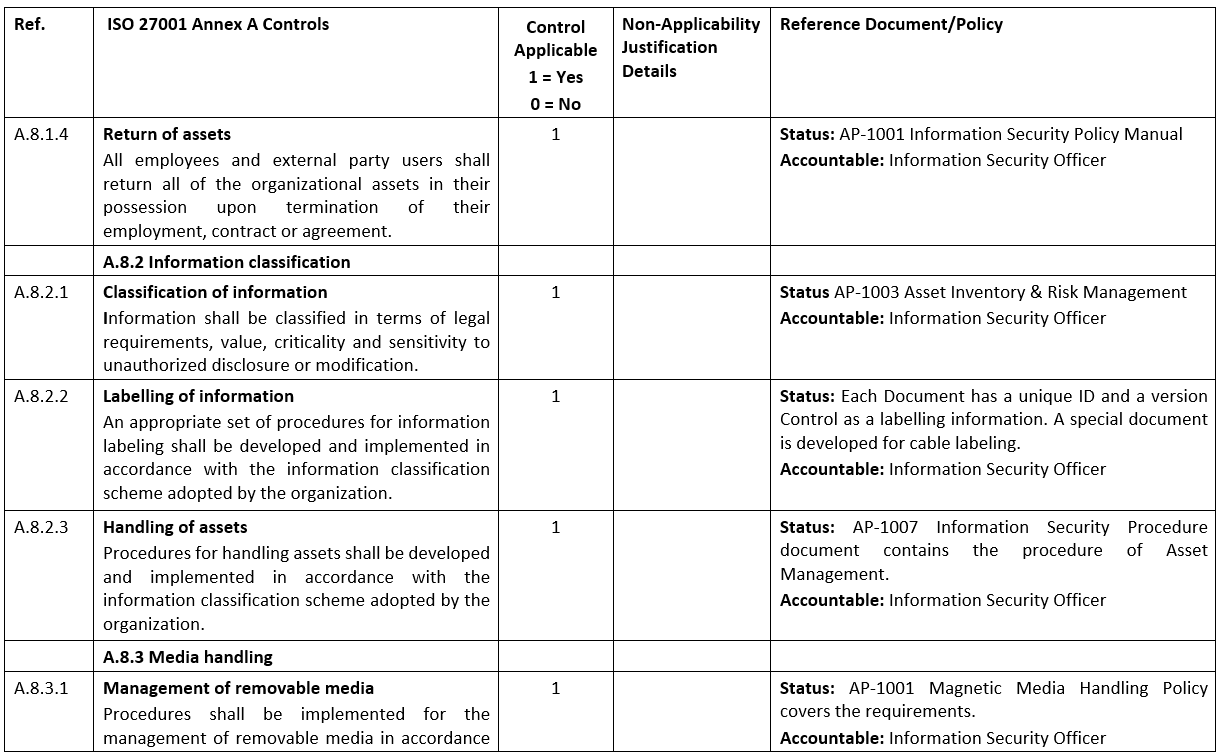
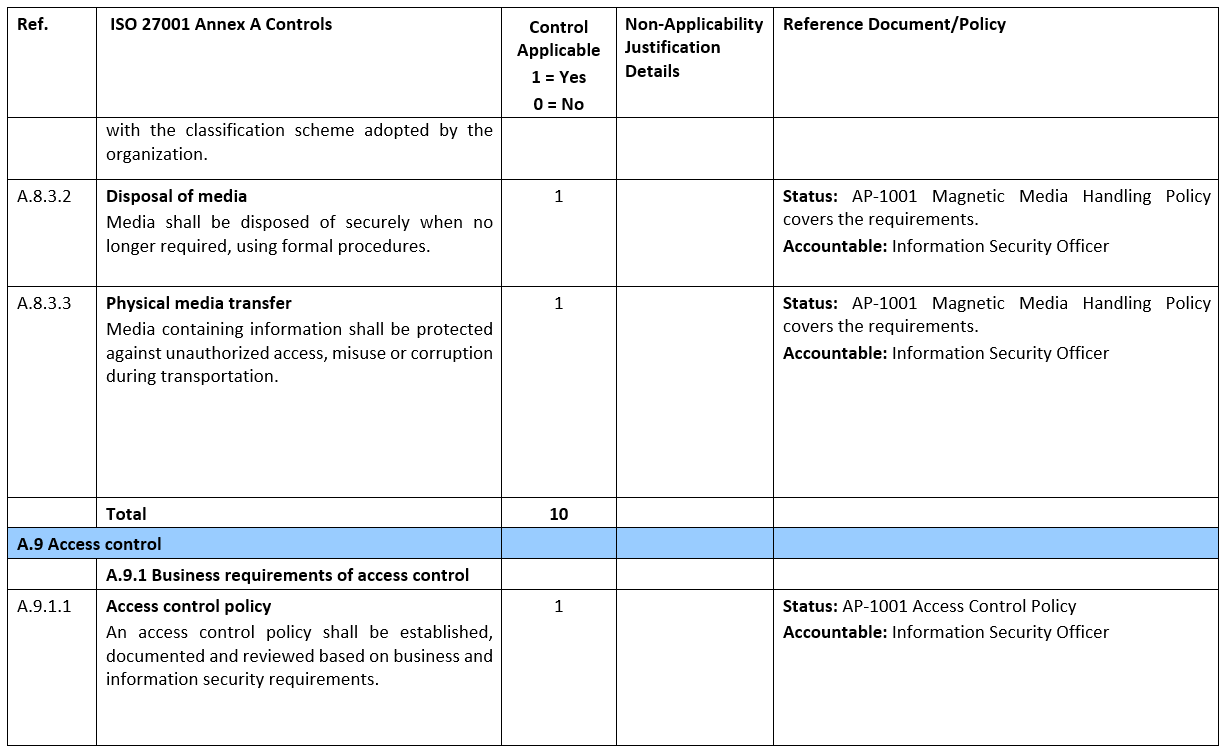
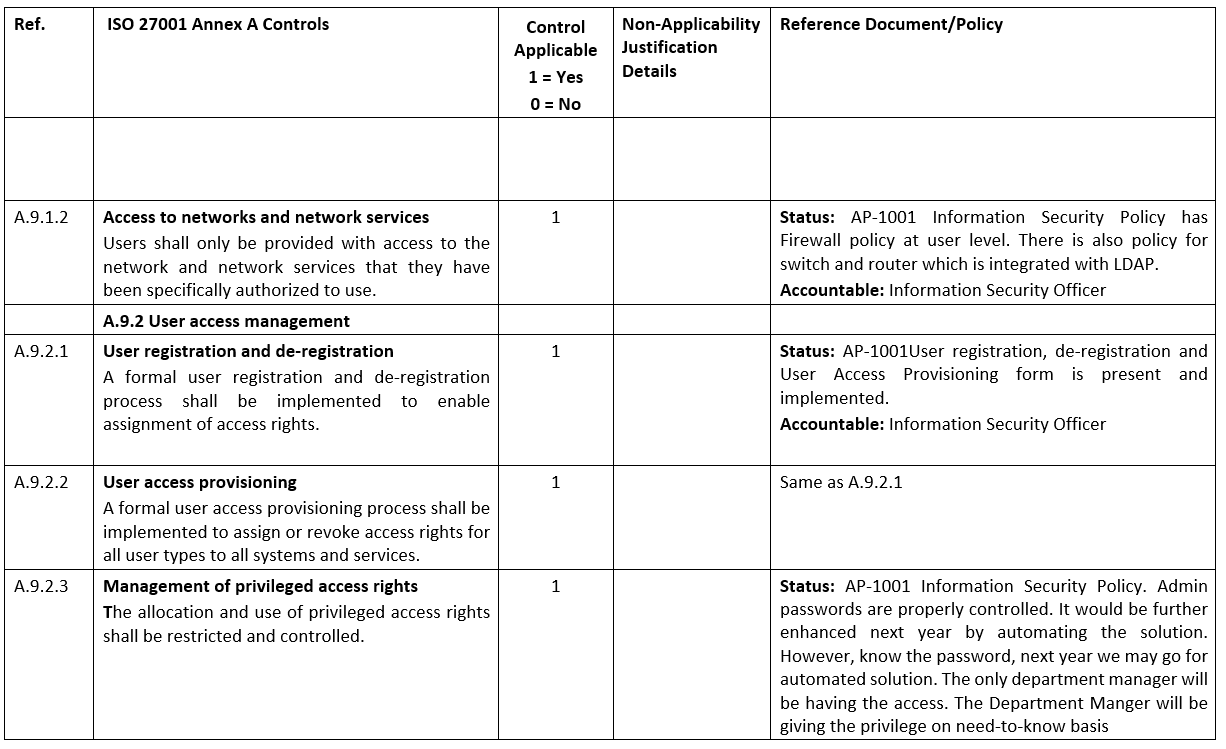
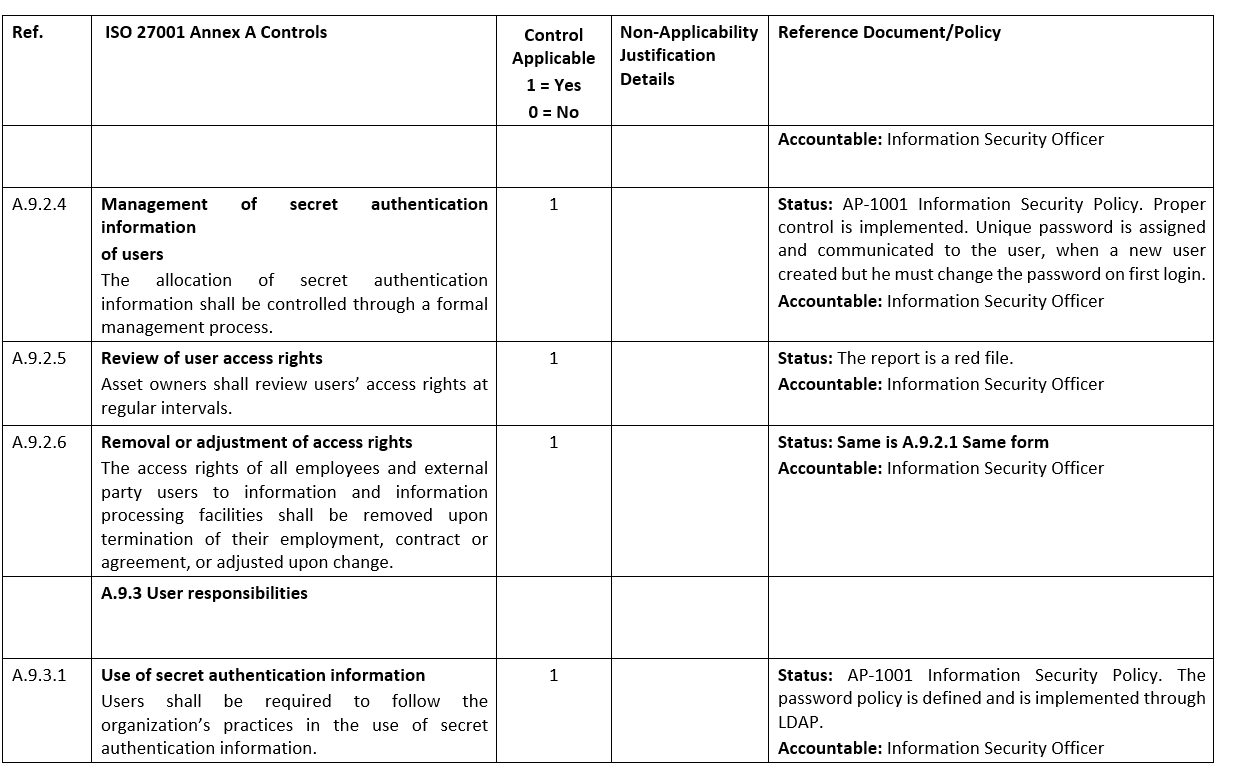
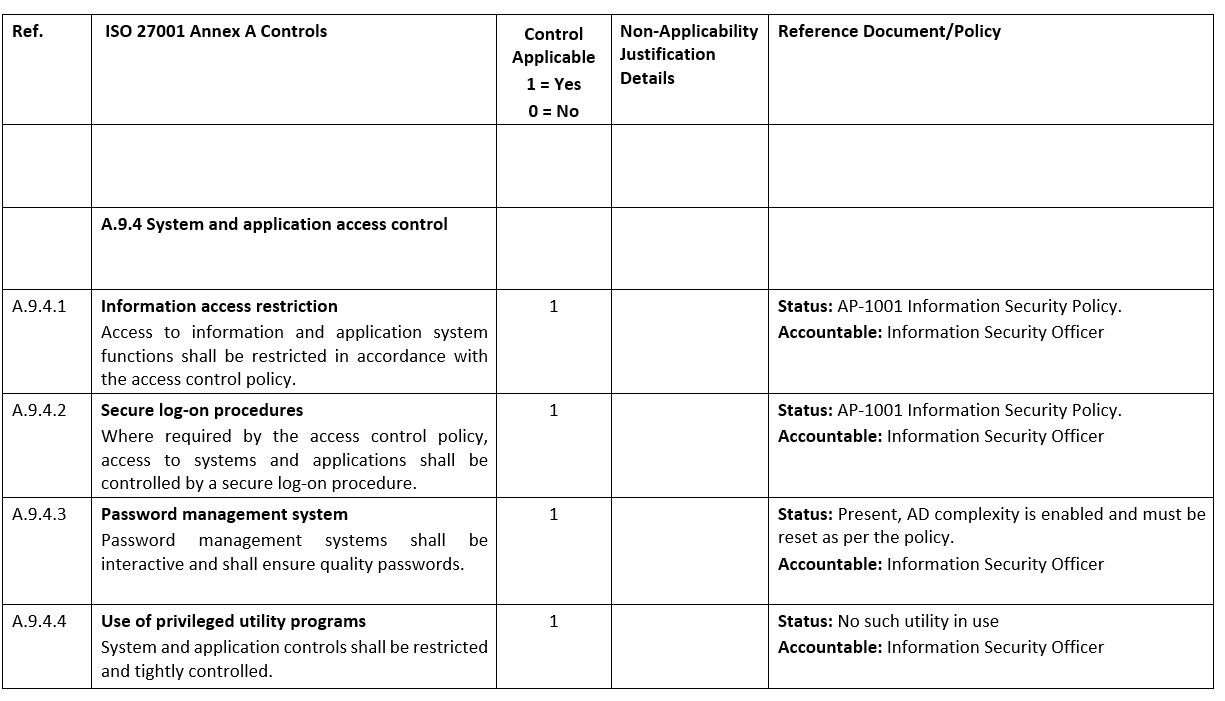
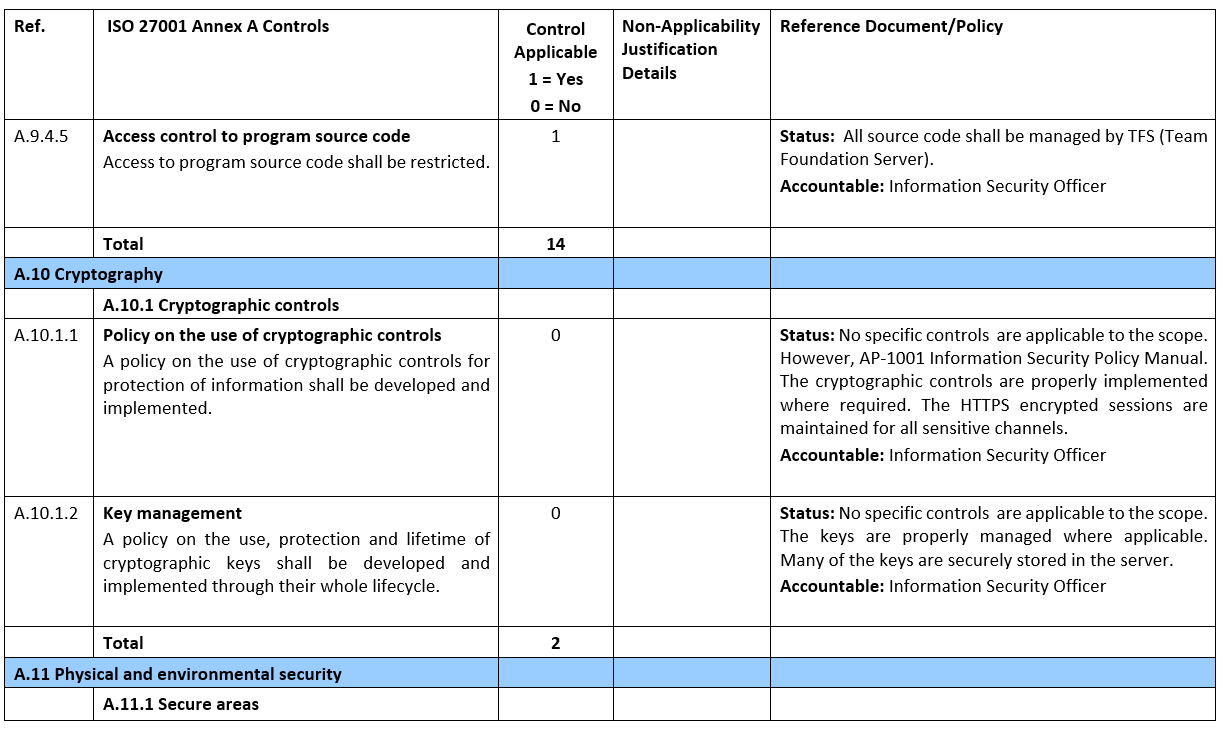
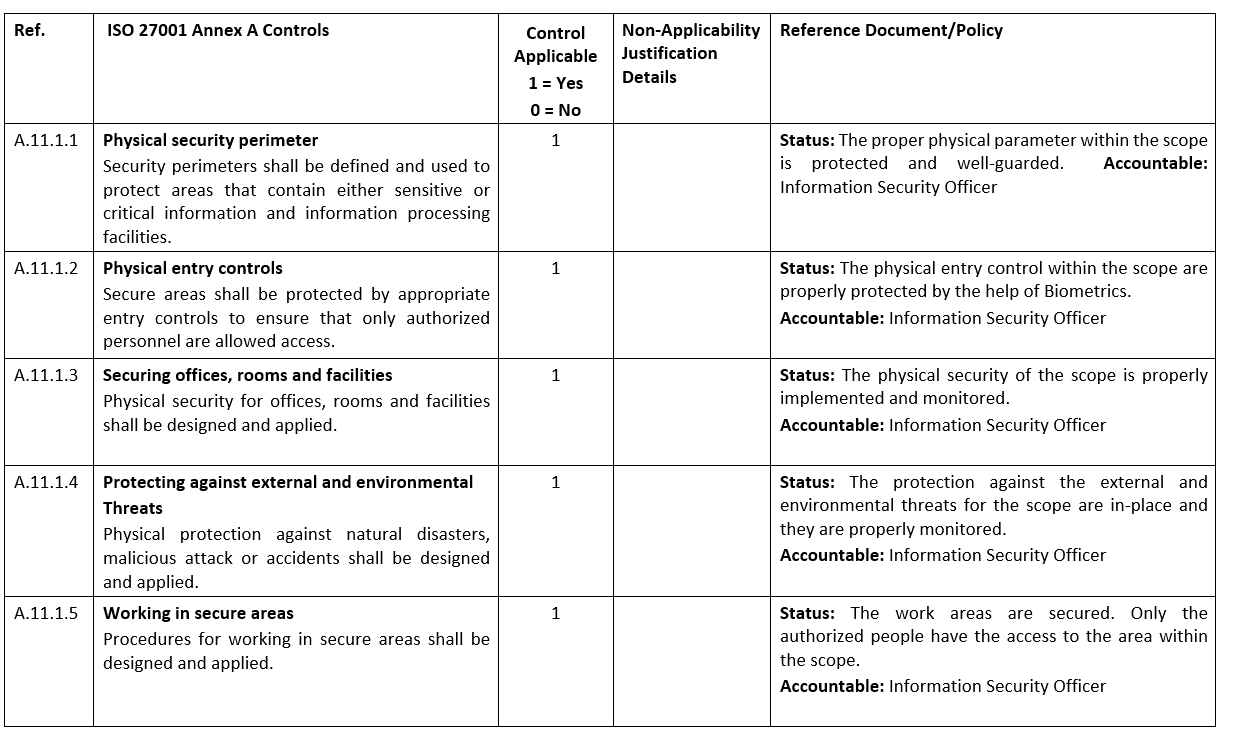
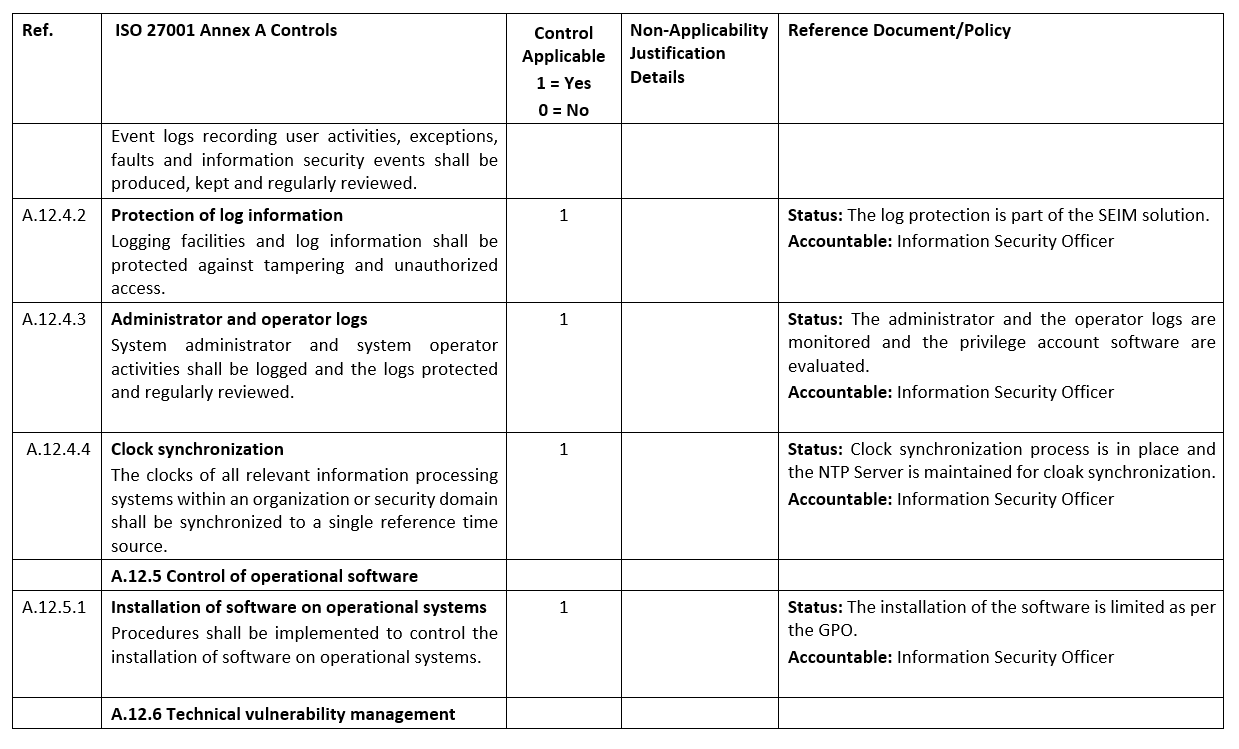
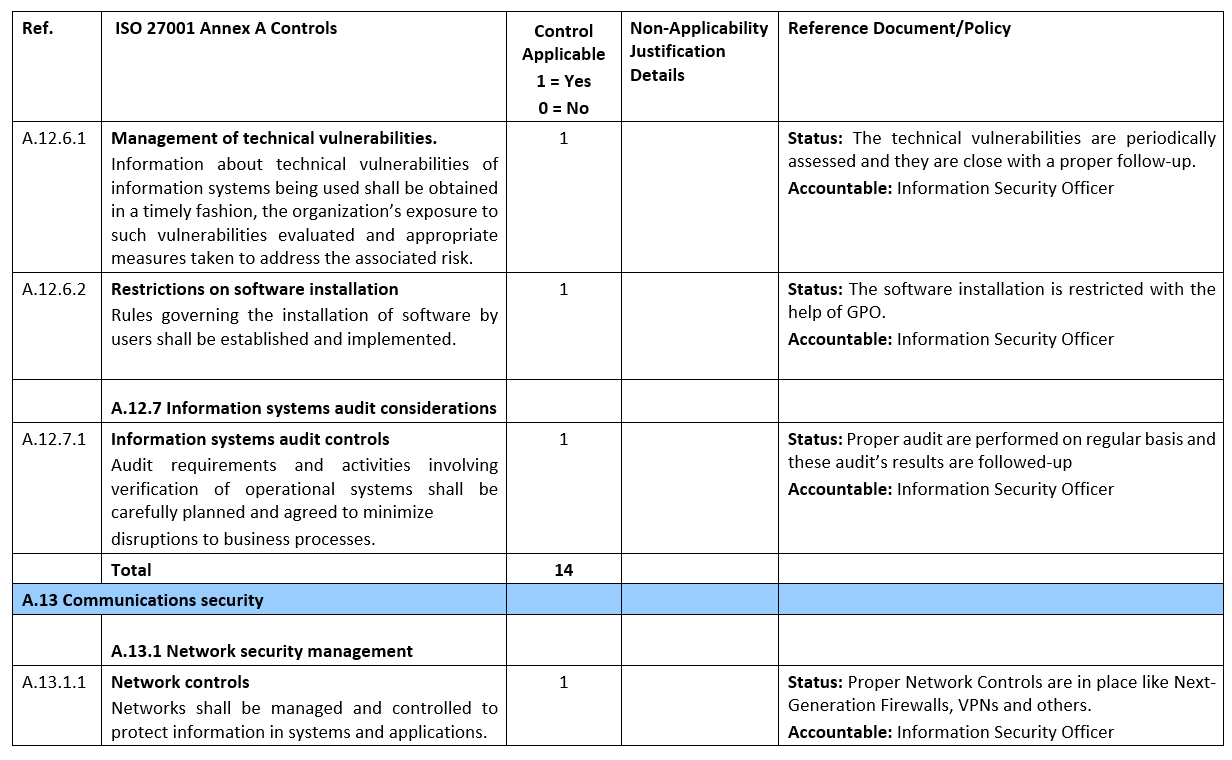
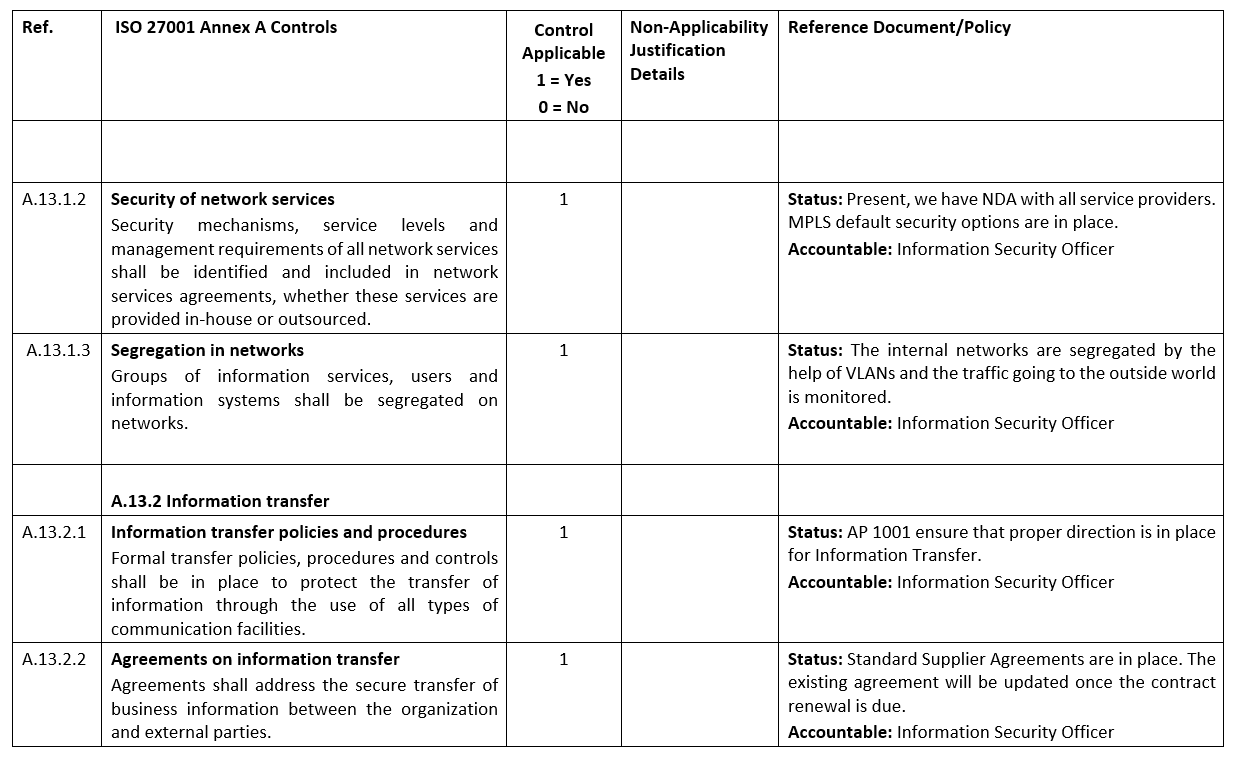
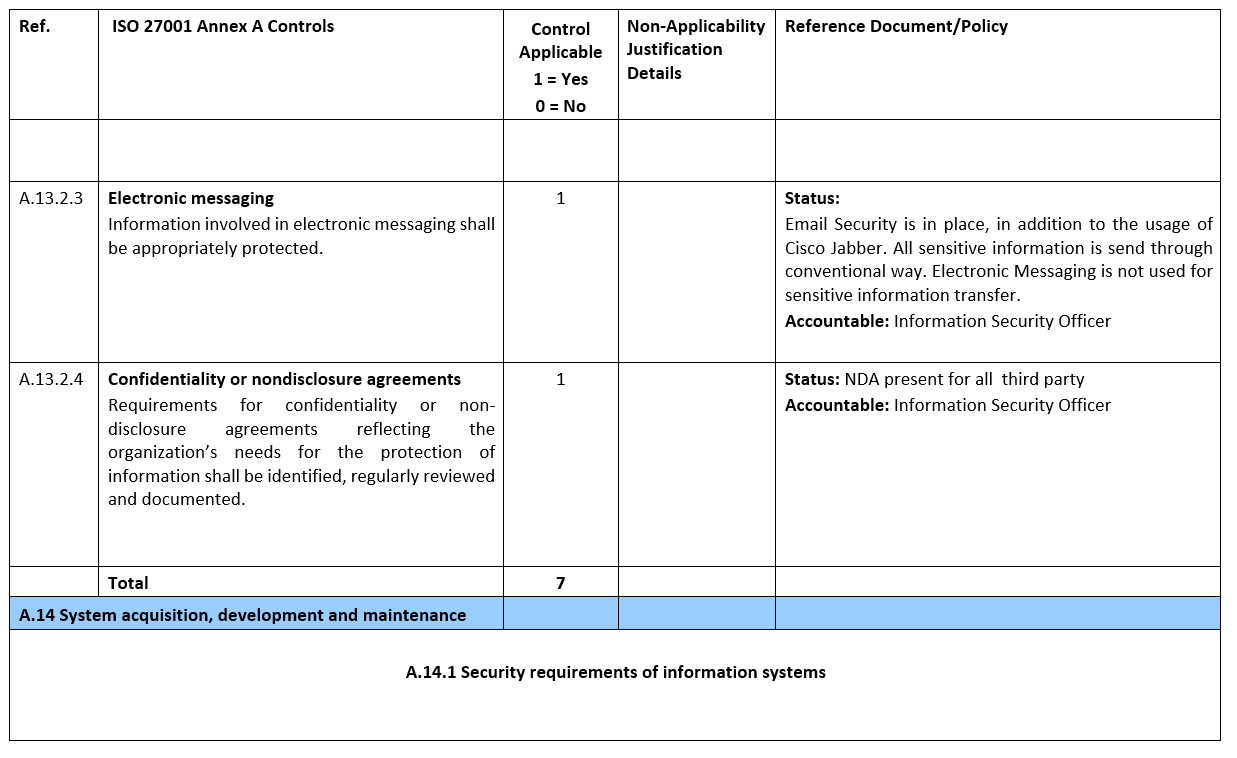
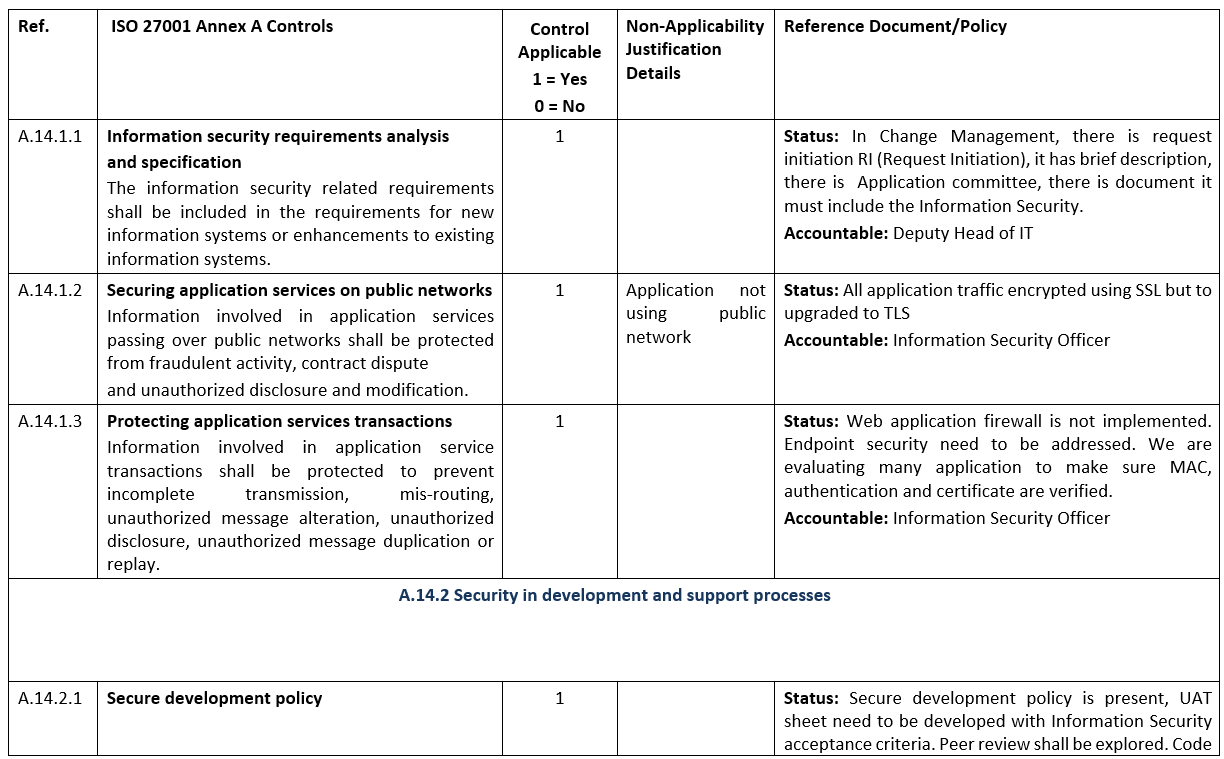
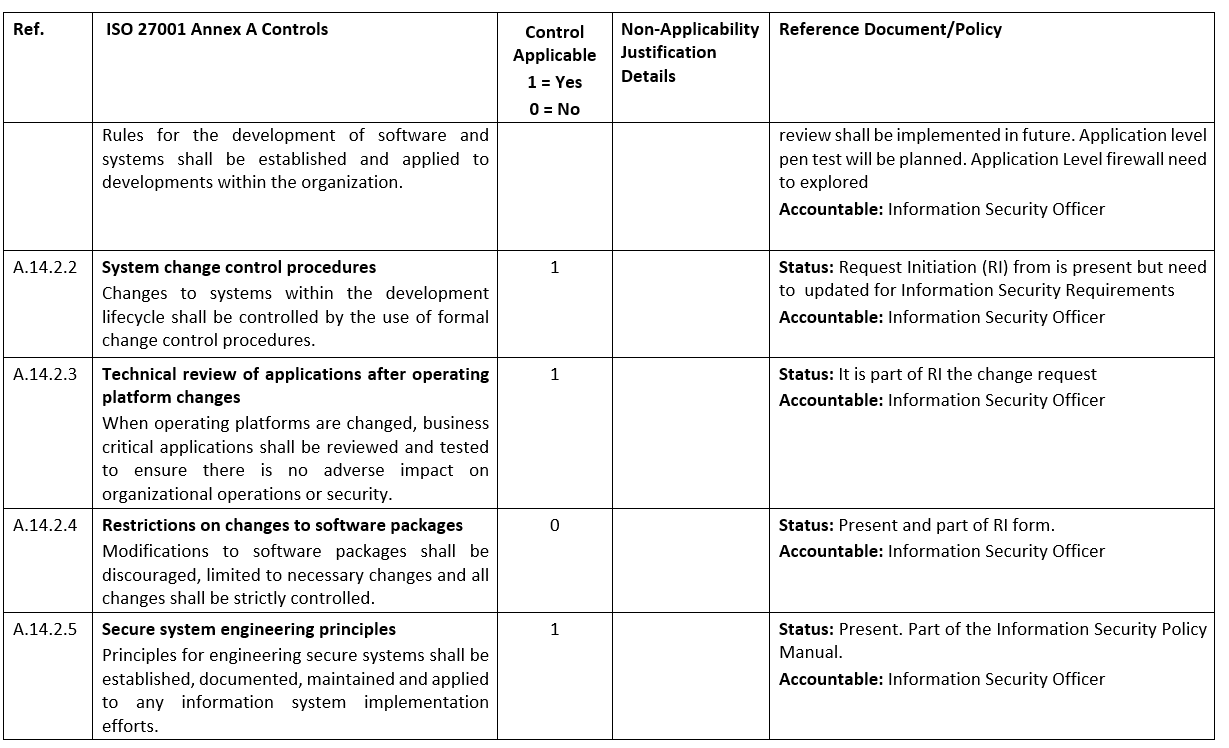
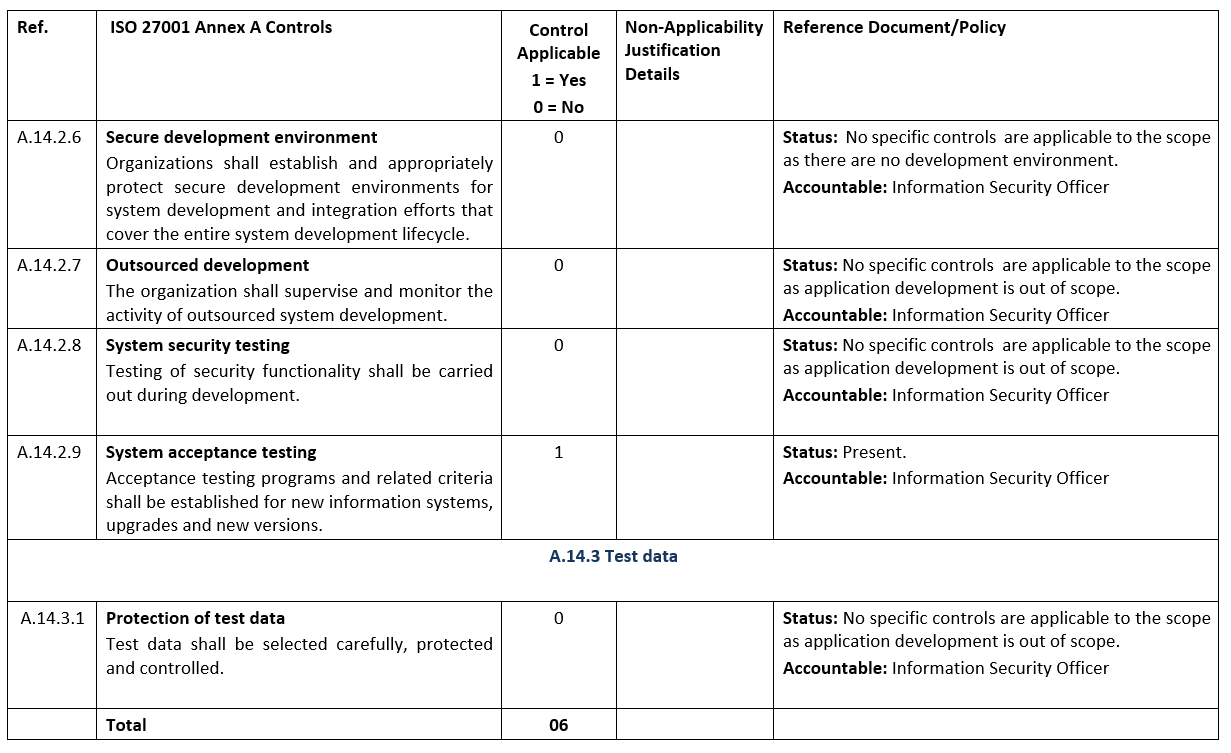
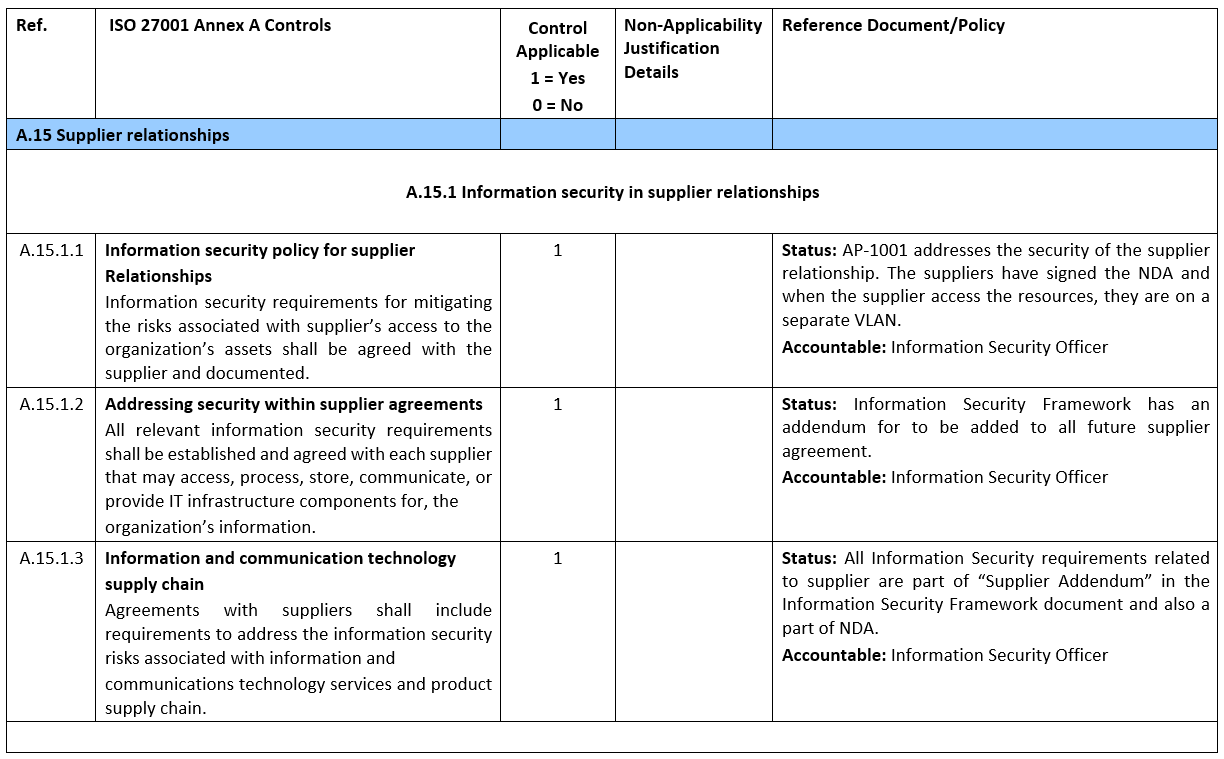
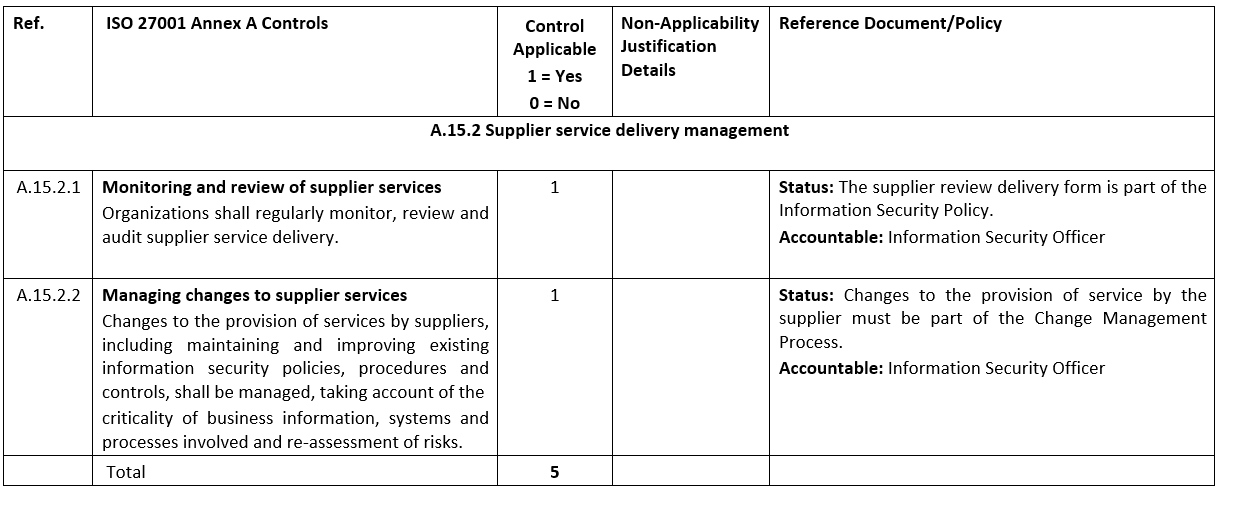
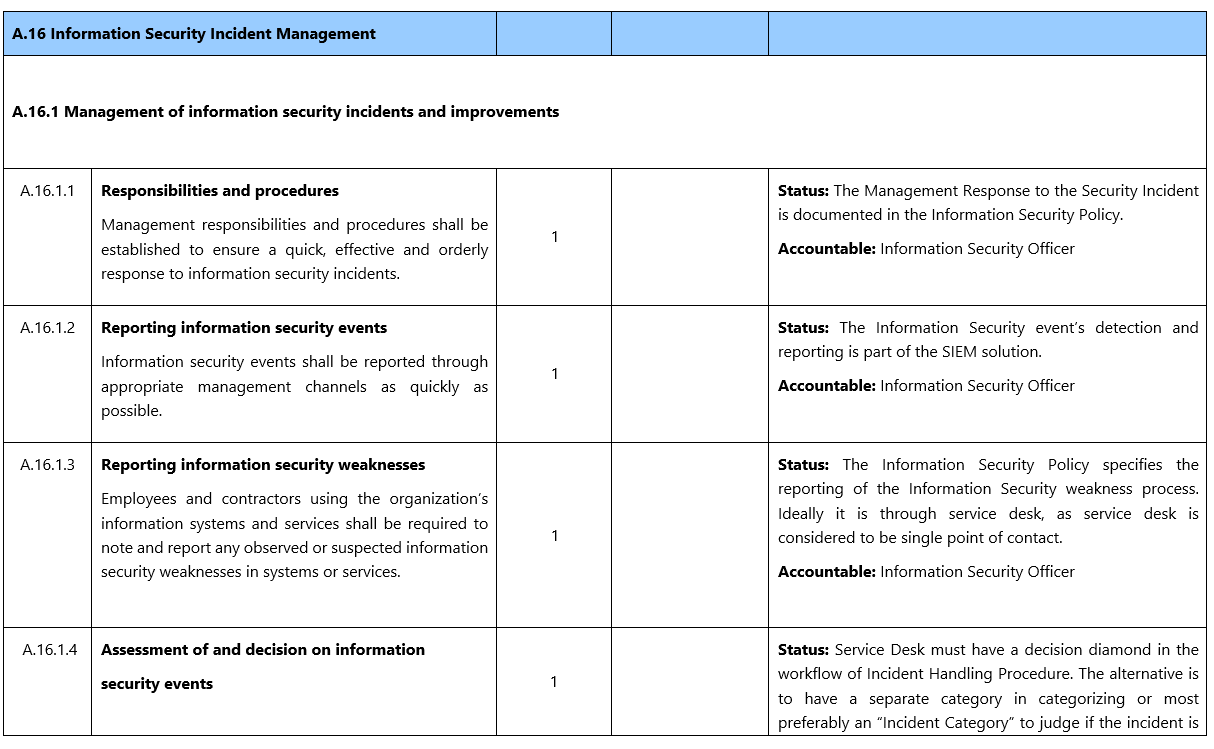
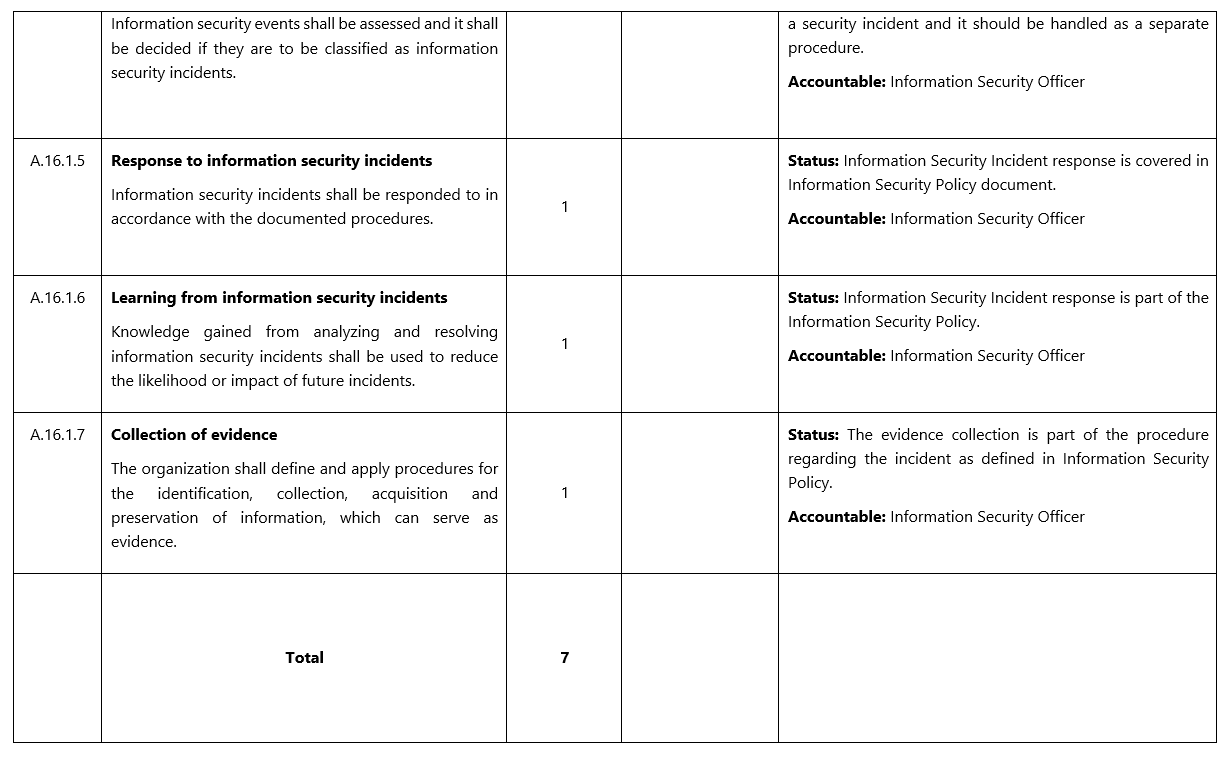
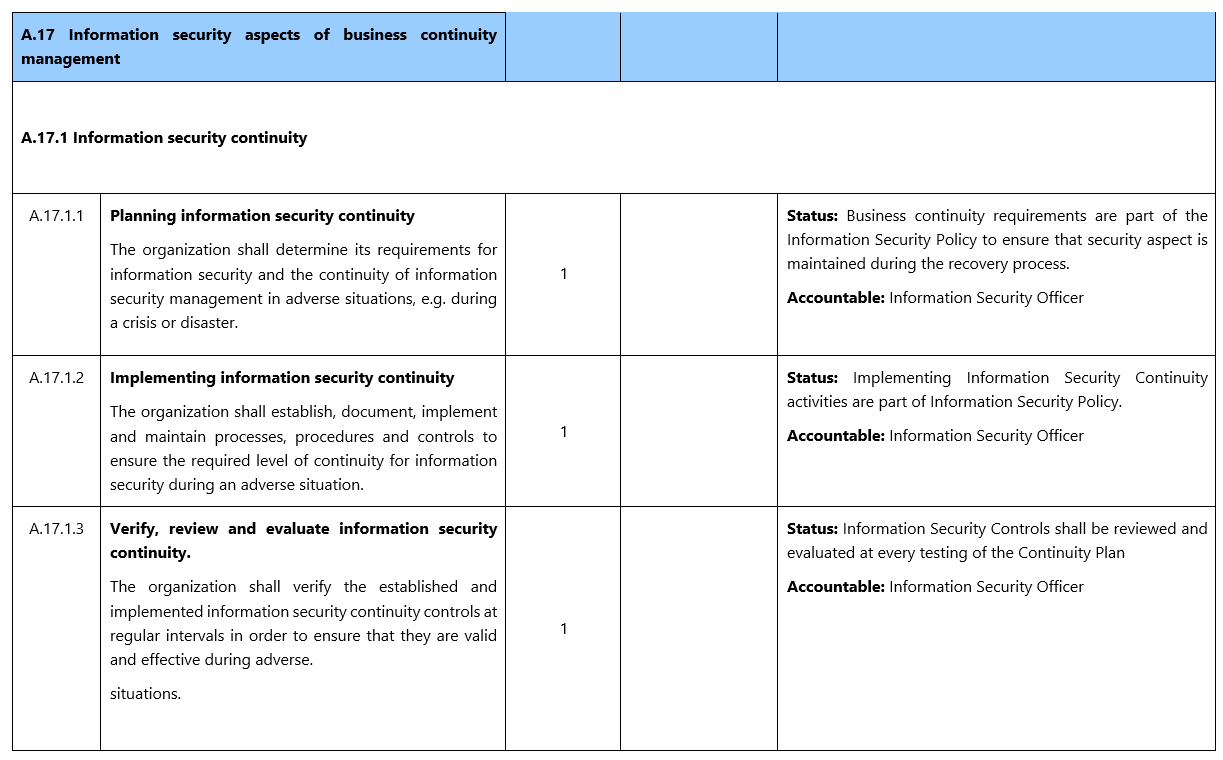
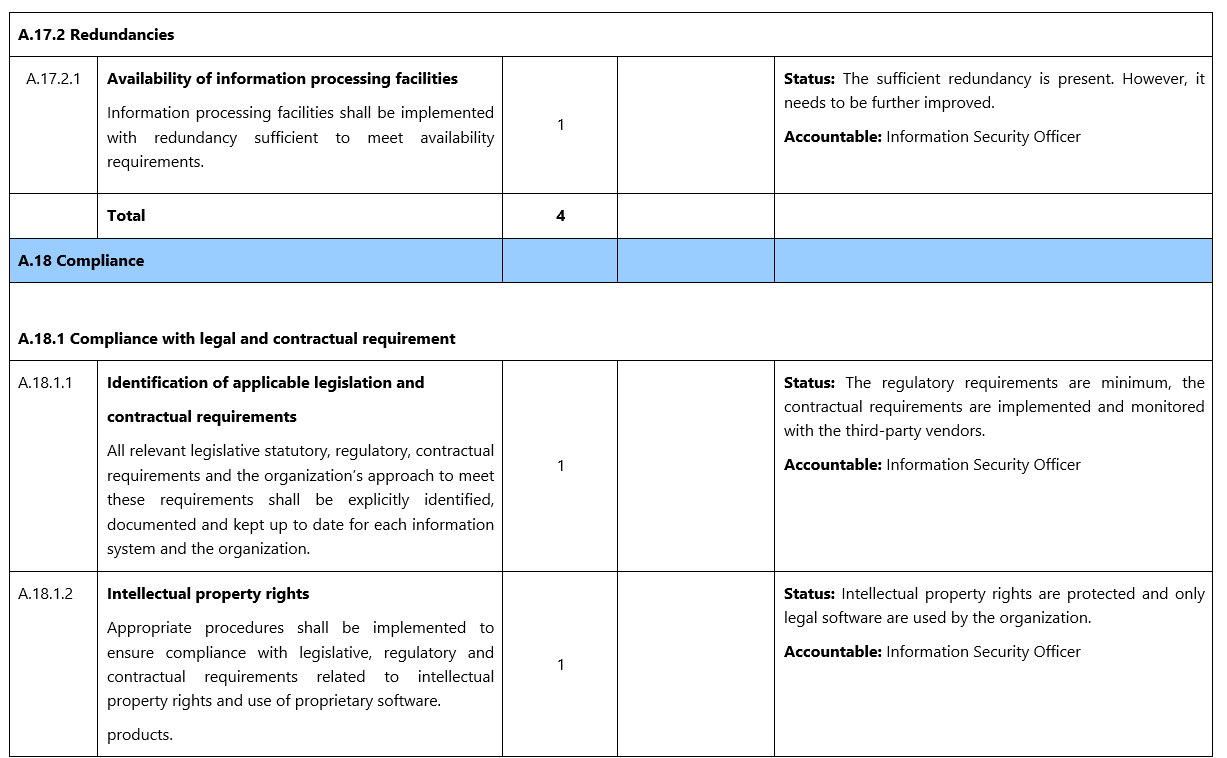
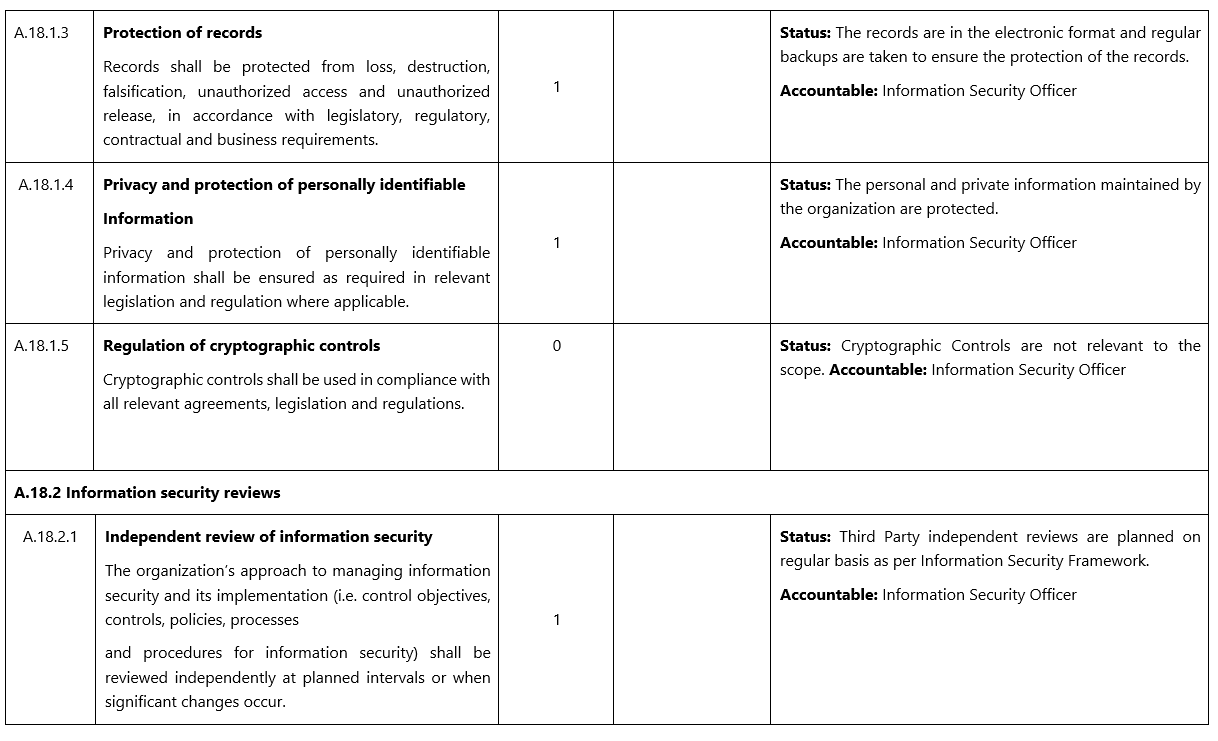
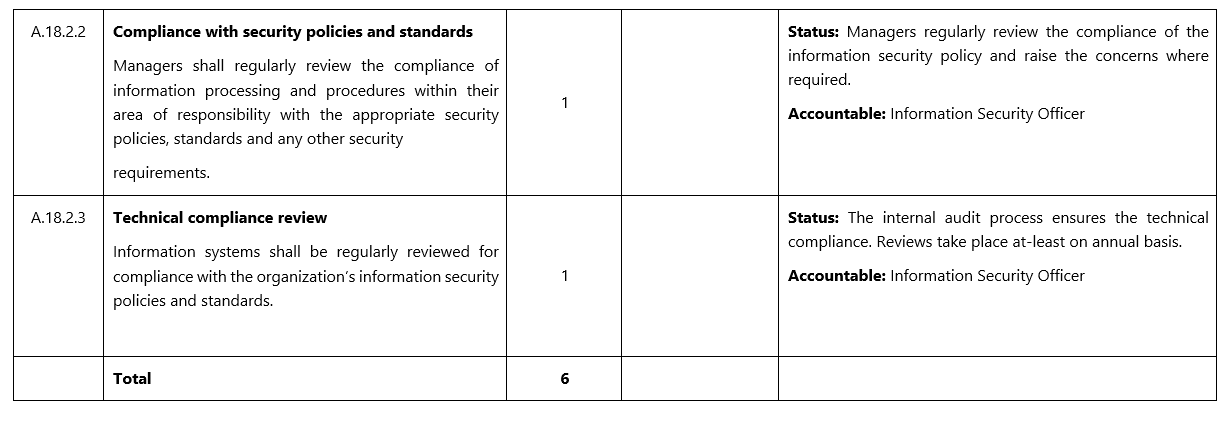
ISO/IEC 27001:2022 Updates
1.1 Threat Intelligence
Policy Statement:
Threat intelligence shall be systematically gathered, analyzed, and utilized to enhance the organization's ability to anticipate, identify, and respond to information security threats. A structured approach to integrating threat intelligence into the existing security processes will be adopted, ensuring timely updates to defense mechanisms and incident response protocols.
Implementation:
Scope and Objective: To identify and mitigate threats proactively through intelligence gathering.
Activities: Regular threat assessments, collaboration with external intelligence providers, and continuous monitoring.
Responsible: Information Security Officer
Reference Document: Threat Intelligence Management Procedure (AP-1005)
1.2 Information Security for the Use of Cloud Services
Policy Statement:
Security measures shall be implemented to ensure the protection of information assets when utilizing cloud services. This includes compliance with cloud provider security standards and regular assessment of cloud service configurations.
Implementation:
Scope and Objective: To secure data and applications residing in cloud environments.
Activities: Risk assessments for cloud services, regular security reviews of cloud providers, encryption of data at rest and in transit.
Responsible: Head of IT Operations
Reference Document: Cloud Security Management Policy (AP-1006)
1.3 ICT Readiness for Business Continuity
Policy Statement:
Information and Communication Technology (ICT) systems shall be prepared to support business continuity plans. This includes ensuring redundancy, backup, and recovery capabilities to maintain critical business operations during disruptions.
Implementation:
Scope and Objective: To maintain ICT services during adverse situations.
Activities: Regular testing of backup and recovery plans, ensuring alternative communication channels are available.
Responsible: Information Security Officer, Head of Infrastructure
Reference Document: Business Continuity Plan (AP-1007)
1.4 Physical Security Monitoring
Policy Statement:
Physical security measures shall include continuous monitoring to detect and respond to unauthorized physical access attempts promptly. This will involve surveillance systems, access control logs, and regular audits of physical security controls.
Implementation:
Scope and Objective: To prevent unauthorized access to sensitive areas.
Activities: Installation and maintenance of surveillance systems, regular reviews of access logs.
Responsible: Information Security Officer
Reference Document: Physical Security Policy (AP-1008)
1.5 Data Masking
Policy Statement:
Data masking techniques shall be applied to protect sensitive information from unauthorized access during testing, development, and analysis activities. This approach will ensure that data privacy and compliance requirements are maintained.
Implementation:
Scope and Objective: To prevent exposure of sensitive data.
Activities: Implementation of data masking tools, policies for handling masked data.
Responsible: Information Security Officer, Head of Application Development
Reference Document: Data Protection Policy (AP-1009)
1.6 Data Leakage Prevention
Policy Statement:
Controls shall be established to detect and prevent data leakage incidents, ensuring that sensitive information does not leave the organization without appropriate authorization. This includes implementing Data Loss Prevention (DLP) technologies and policies.
Implementation:
Scope and Objective: To safeguard against data breaches.
Activities: Deploy DLP solutions, conduct regular audits, employee training on data handling.
Responsible: Information Security Officer
Reference Document: Data Leakage Prevention Procedure (AP-1010)
1.7 Monitoring Activities
Policy Statement:
Continuous monitoring of systems and networks shall be conducted to detect and respond to security incidents promptly. This includes monitoring for unauthorized access, policy violations, and other security events.
Implementation:
Scope and Objective: To ensure real-time detection of security incidents.
Activities: Implement SIEM solutions, regular log reviews, incident response drills.
Responsible: Information Security Officer
Reference Document: Security Monitoring and Incident Response Plan (AP-1011)
1.8 Web Filtering
Policy Statement:
Web filtering controls shall be implemented to manage and monitor access to web content, preventing access to malicious sites and ensuring compliance with organizational policies.
Implementation:
Scope and Objective: To protect against web-based threats.
Activities: Configuration of web filters, periodic reviews of access logs, updating filtering rules.
Responsible: Head of IT Operations
Reference Document: Web Access Control Policy (AP-1012)
1.9 Secure Coding
Policy Statement:
Secure coding practices shall be integrated into the software development lifecycle to prevent vulnerabilities in application code. This includes adhering to coding standards, regular code reviews, and security testing.
Implementation:
Scope and Objective: To ensure the security of application development.
Activities: Implement secure coding guidelines, conduct security training for developers, perform regular code audits.
Responsible: Head of Application Development
Reference Document: Secure Coding Guidelines (AP-1013)
1.Introduction
This document contains confidential information that is proprietary to the organization. Unauthorized access, copying, or disclosure is prohibited.
1.1 Executive Summary
Objective of the Penetration Test: To identify vulnerabilities, assess the security posture, and ensure compliance with ISO 27001:2022.
Scope of Testing: Includes the organization's external-facing web applications, internal networks, and key information systems.
Summary of Findings: A total of 12 vulnerabilities were identified, categorized into 3 high-severity, 5 medium-severity, and 4 low-severity vulnerabilities.
Conclusion and Recommendations: Immediate remediation is recommended for high-severity vulnerabilities. Medium and low-severity vulnerabilities should be addressed in the next security cycle.
1.2 Introduction
Purpose of the Report: This report provides an overview of the penetration test conducted, the findings, and the recommendations for improving the organization's security posture.
Background: The organization requested this penetration test as part of its annual security assessment and compliance verification with ISO 27001:2022.
Methodology: The test followed a black-box testing approach, using both automated tools and manual techniques. The testing was conducted over a period of two weeks.
1.3 Scope and Objectives
Defined Scope: The penetration test included the organization's public-facing web applications, internal network segments, and critical infrastructure components.
Testing Objectives: The primary objectives were to identify security weaknesses, test the effectiveness of existing security controls, and evaluate the organization’s compliance with ISO 27001:2022.
1.4 Methodology and Tools Used
Testing Phases: The testing was conducted in several phases:
- Reconnaissance
- Vulnerability scanning
- Exploitation
- Post-exploitation analysis.
Tools and techniques used:
- Eg Custom scripts, Nmap, Metasploit, etc
2.Findings
Pen Test Briefing for SIRT:

2.1 Top Ten Events by Product Type
2.2 Vulnerability Resolution Matrix Summary
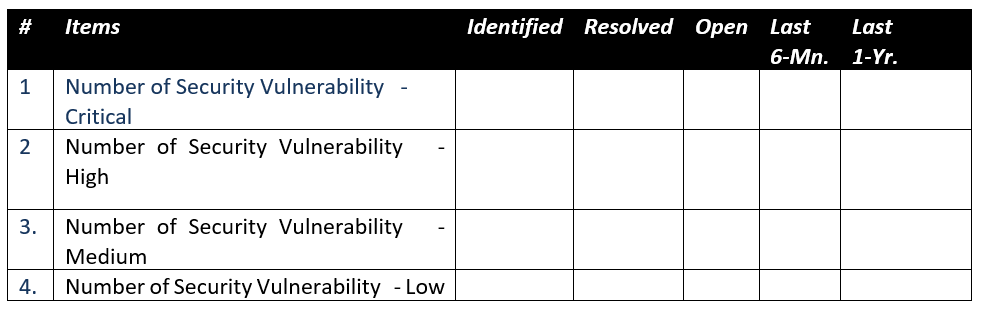
3. Vulnerabilities - Details
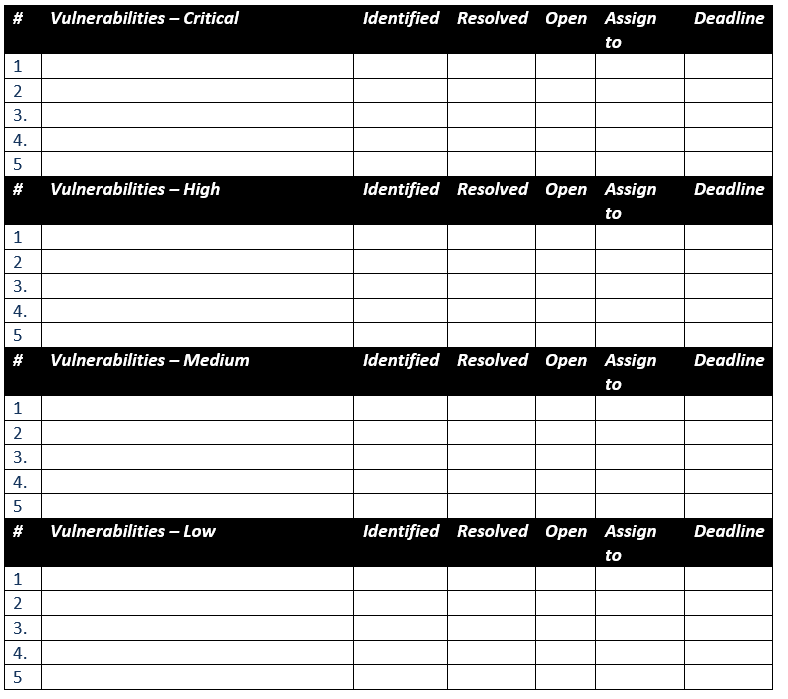
4.Security Patches and Service Packs Status & Trends
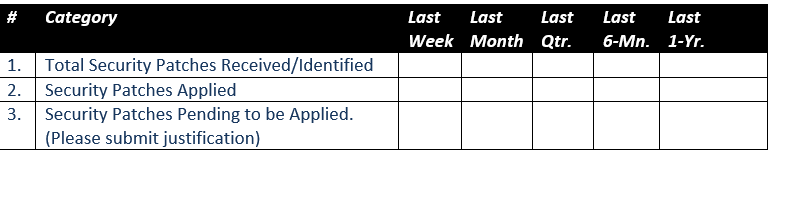
5.Spam Emails and Phishing Status & Trends
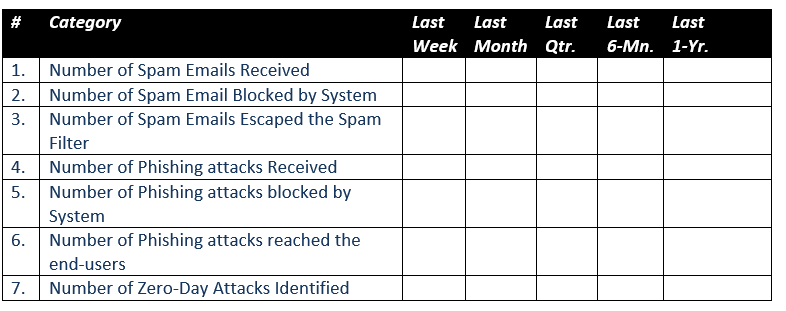
6. Total Number of Hits by Country
7.Unsupported System Running in the Organization
8. Impact Analysis
9. Recommendations
10. Conclusion
11. Compliance Mapping
ISO 27001:2022 Controls Mapping: A mapping of the findings and recommendations to specific ISO 27001:2022 controls.
Annex A Controls: Identification of relevant Annex A controls and how addressing the vulnerabilities contributes to compliance.
Appendices
Nomination of SIRT Team
The following Security Incident Response Team (SIRT) is being nominated:
Security Incident Management and Coordination Baseline
(To be used during Annual Audit/Periodic Audit)
ü The follow six major steps should be performed to handle the incidents, which are following:
o Preparation
o Detection
o Containment
o Eradication
o Recovery
o Follow-up
ü Preparation step follows:
o All detection tools are available
o IPS, Server, Firewall are up and running
o Contact list of SIRT is available
o Minimum 1 person for each technology is available on call /onsite
ü Detection step covers:
o Review the external Vulnerability Assessment report
o Review the log of the critical systems
§ Firewall
§ VPN
§ IPS
§ Windows Server
§ SUN Server
§ Others
o Run Co-relation manually/software to co-relate the events
o In-depth analysis of the following:
§ Syslog
§ Security Log
§ Set UID file
§ Get GID files
o In case of Unix also check following:
§ SU
§ Net Stat
§ Ifconfig
§ du
§ df
§ sync
o Examine file run by ‘cron’ and ‘at’
o Senior Management must be informed about the status
ü Containment
o Compromised system is isolated
o Backup of compromised system is taken
o Compromised system is put in safe custody for Forensic
o Copy of archived system is used for investigation
o Impact of the breach is analysed.
o Senior Management is briefed regarding the containment
ü Eradication
o Root cause of incident is analysed
o Fix or patches are applied
o Systems are thoroughly tested for the confirmation of eradication
ü Recovery
o After thorough testing, system are brought back to production environment
o Rollback procedures are available and tested if required
ü Follow-up
o System is kept under continuous monitoring
o Security rules of relevant equipment are updated.
o Lesson Learnt are updated
o With the approval of Senior Management the incident is closed
ü Senior Management are informed regarding all issues and concerns
ü Incident trend analysis is performed.
1. Threat Intelligence
This control provides processes and references for identifying, collection, analysis and managing, mitigating threats and to produce threat intelligence and communicate emerging threats with respect to the organisation’s information Security requirements.
2. Purpose
The
purpose of this policy is to set the requirements for proper facilitation and
operation of the NT threat intelligence program. The development of a threat
intelligence program will support the continuous improvement of the overall
network security, as well as offering the opportunity to engage in in-depth
collection, analysis and communication of the Indicators of the Compromise (IOCs)
prior to Cyber security incident occurs while providing visibility into our
immediate threat landscape to identify red flags before they turn into
full-blown issues.
3. Scope
This Policy is applicable to all NT’s business processes and data, information systems, employees and third-party users(clients) and physical areas.
3.1 Principles
Existing and emerging threats are identified and mitigated via the Risk Management Process and Continual Improvement Process.
4. Objectives
4.1.1 Identifying Existing and Emerging Threats
Using internal and external data sources, existing and emerging threats will be identified. In addition, the use of audit processes such as internal audit, external audit and penetration testing, and vulnerability assessment and compliance tools will be used.
4.1.2 Assess Risk and Impact
Threats will be analyzed for the relevance to the NT. Where a relevant threat is identified, it will be added to the risk register and managed via the risk management process.
4.1.3 Communicate
Threats intelligence will be shared with the Security Review Team and then with the Management as part of the updates.
4.1.4 Improve the Information Security Management System (ISMS)
Threats intelligence that identifies emerging and existing threats will be managed via the Risk Management process and any changes or improvements will be managed via the continual improvement process.
5.Information Sources
5.1 Internal
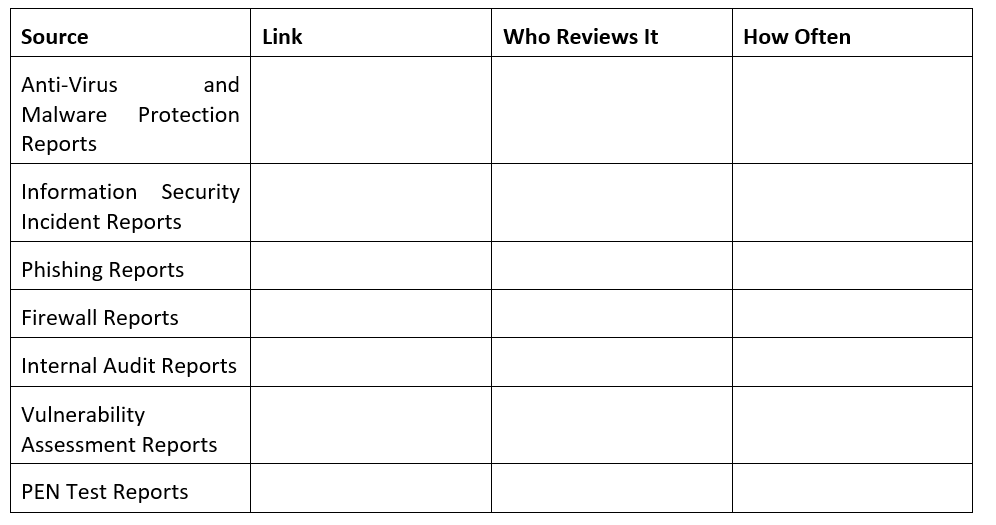
5.2 External
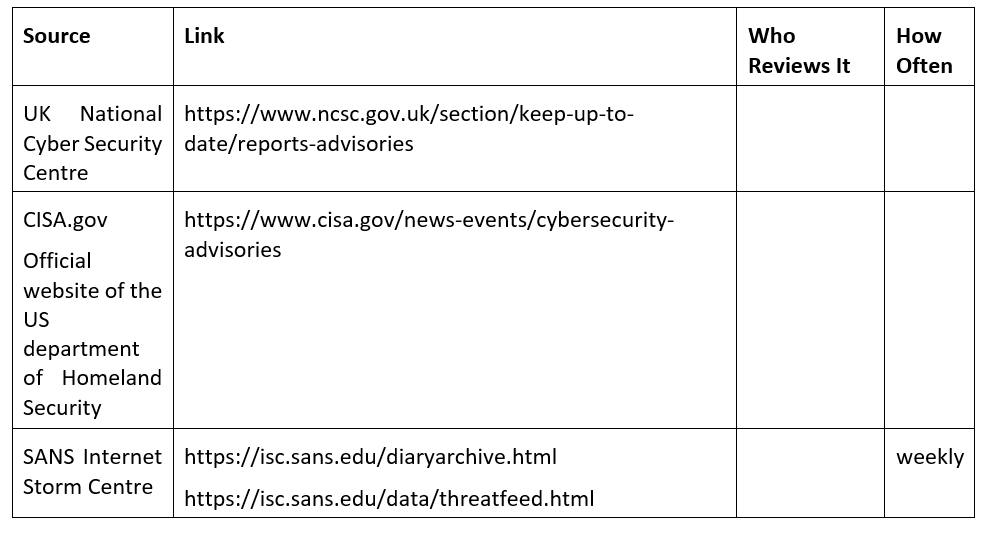
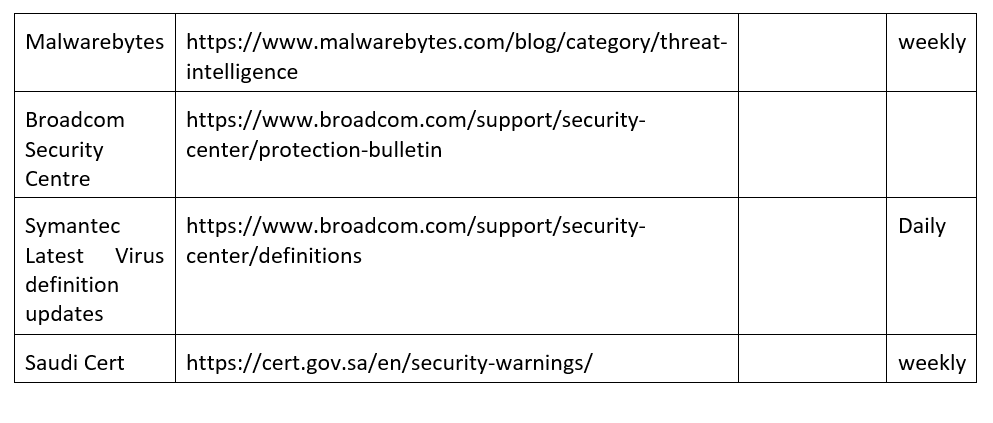
6. Roles and Responsibilities
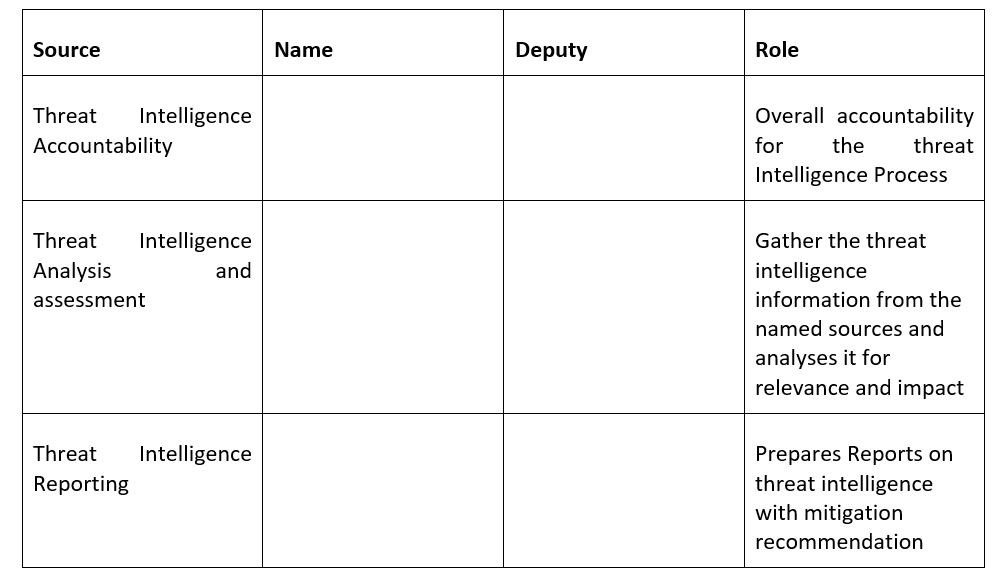
7. Threat Intelligence Reporting
A Threat intelligence report is created and shared with the IT Dept and IT Security Team.
• The Threat intelligence Report is shared at least at the Management Review Team meeting if a significant threat is identified.
• Threat Intelligence reports are kept for at least 12 months.
• Progress of Threat Mitigation is reported via Risk Management Process.
7.1 Threat Intelligence Report
7.1.1 Threat Summary
The Threat Intelligence Report gives a high-level threat summary and records.
Source: The source of the threat, either a link or description in words of how the threat is identified.
Threat level: Using a simple, easy to understand rating of High / Medium and Low the initial rating is a subjective rating on the potential risk and impact to the NT Operations.
7.1.2 Threat Detail
For each threat in the summary table a more detailed report is provided that includes recommendations on next steps, whether it is added to the risk register and if so a risk reference.
8. Process Compliance
8.1 Compliance Measurement
The Information Security management team will verify compliance to this process through various methods, including but not limited to, Risk register action taken reports. Internal and External audits and feedback to the process owner.
8.2 Exceptions
Any Exception to the process must be approved and recorded by the Information Security Manager in advance and reported to the Management Review Team.
8.3 Non-Compliance
An Employee found to have violated this process may be subject to disciplinary action, up to and including termination of employment.
9. Exit
The effectiveness results are recorded, analysed and appropriate action taken for further improvement.
10. Output
Threat Intelligence report prepared, and Risk Register filled and acted upon it.
11. Review and Update
The Threat Intelligence Procedure shall be reviewed annually or when significant changes occur in the organization’s environment, technology, or regulatory requirements or when serious threat emerges or a security/Threat incident occurs.
Updates to the procedure shall be approved by the Information Security Officer and senior management.
12 Definitions and Terminology
Indicators of compromise (IOCs): IOCs refer to data that indicates a system may have been infiltrated by a cyber threat. They provide cybersecurity teams with crucial knowledge after there has been a breach of data or another breach in security.
Cyber Security Incident: An occurrence or event that (1) actually or imminently jeopardizes, without lawful authority, the integrity, confidentiality, or availability of information or an information system; or (2) constitutes a violation or imminent threat of violation of law, security policies, security procedures, or acceptable use policies.
ISO 27001:2022: An international standard for information security management systems, providing a systematic approach to managing sensitive information.

1. Configuration Management
This control provides processes and tools to make sure that NT IT Dept. have enforced established configurations for software, hardware (security configurations), network and services (cloud services), for newly installed systems as well as for operational systems over their lifetime documented, monitored and reviewed.
2. Purpose
To ensure hardware, software, services and networks function correctly
with required security settings, and configuration is not altered by
unauthorized or incorrect changes.
3. Scope
This Policy is applicable to all critical NT applications, data, information systems devices and services.
4. Objectives
Changes or amendments on part of maintenance staff and or vendors or software developers are reviewed and tested before deployment / implementation thereby minimizing the risk of mis configuration and unexpected results, documentation updated, and Version/Change control is maintained.
5.Ownership
Configuration management is solely an administrative task that deals with the maintenance and monitoring of asset-side information and data that is resident on a broad range of devices and applications. As such, ownership resides with the Head of IT, or organizational equivalent, Change Control Manager.
6. Document Configuration Management
Head of IT Dept. of NT identifies based on criticality need to draft and implement configuration management documentation for both new IT systems, applications and hardware and any that are already in use. Internal controls should include business critical elements such as security configurations, all hardware that holds a configuration file and any relevant software applications or systems.
Relevant roles and responsibilities are well defined when implementing a configuration policy, including the delegated ownership of configurations on a device-by-device, or application-by-application basis.
6.1 Criticality and Delegated Owner
6.2 Hardware and Network Infrastructure
6.3 Hardware and Network Infrastructure Roles and Responsibilities
6.4 Software/ Application in use or in development User and Security
6.5 Software/ Application in use or in development User Roles and Responsibilities
7. Security Controls
NT IT Dept. implements the following for use across the organisation, in order to minimise any information security risks:
1. Keep the number of users with administrator privileges to a minimum.
2. Disable any unused or unnecessary identities.
3. Closely monitor access to maintenance programs, utility applications and internal settings.
4. Ensure that clocks are synchronised in order to log configuration correctly, and assist
in any future investigations.
5. Immediately change any default passwords or default security settings that are supplied with any device, service or application.
6. Implement a default logoff period for any devices, systems or applications that have been left dormant for a specified period of time.
7. Ensure that all licensing requirements have been met.
8. Baseline Configurations
NT IT Dept. has a responsibility for documenting baseline configurations. Baselines are documented, formally reviewed and agreed-upon sets of specifications that ensure that IT Assets are properly configured and hardened to reduce vulnerabilities.
Hardening includes removing superfluous programs, account functions, applications, ports, permissions, access, or other configuration changes to reduce attackers’ ability to gain unauthorized access to the IT environment. Types of hardening activities include
application hardening, operating system hardening, server hardening, database hardening and network hardening. Baseline configurations must be updated as needed to ensure system upgrades, patches or other significant changes are addressed according to compliance requirements identified by the IT Vulnerability.
Existing baseline configurations must be reviewed at least annually to ensure they are still applicable.
9. Configuration Change Control
Configuration change control is the documented process for managing and controlling changes to the configuration of a system. Configuration change control includes, but is not limited to:
1. Changes to Baseline configurations for components and configuration items of IT Assets.
2. Changes to configuration settings for information technology products (e.g., operating systems, applications, firewalls, routers, Etc..).
3. Unscheduled/unauthorized changes.
4. Changes to remediate vulnerabilities or bug fixes.
IT Asset Owner’s must ensure proper configuration change control:
1. Determine the types of changes to an information system or IT Asset that impact configuration.
2. Review proposed configuration changes and approve or disapprove with explicit consideration for security impact analysis and document change decisions.
3. Properly test, validate, and document planned changes prior to implementation of approved changes.
4. Coordinate and provide oversight for change control activities through stake holders. Retain previous configurations and records of changes for the life of the system or IT Asset to support audit, incident response and historical information.
5. Audit and review activities associated with configuration changes to the information system or IT Asset, including audit logs and rollback procedures.
10. Managing and Monitoring Configurations
NT organisation has a responsibility to maintain and store configurations, including keeping audit trail of any amendments or new installations, in line with a published document. (see 15-0-3 Control of Documented Information).
Documentation shall contain the following information:
1. Who owns the asset or point of contact information for the asset.
2. A timestamp for the latest Configuration change.
3. The current version of the configuration file/template and its location.
4. Any relevant information that explains the assets relationship with configurations held on other devices or applications or systems.
NT shall consider implementing specialised software to track any changes in a device's configuration, and take appropriate action to address the amendment as soon as possible, either by validating the change or reverting the configuration back to its original state.
11. Process Compliance
11.1 Configuration Change Management plan and Control Sheet
The sheet must be completed in all respects and approved for the process compliance.
11.2 Exceptions
Any Exception to the process must be approved and recorded by the Head of the IT and reported to the Management Review Team.
11.3 Non-Compliance
An Employee found to have violated this process may be subject to disciplinary action, up to and including termination of employment.
12. Output
The effectiveness, results are recorded, analyzed and Configuration file updated and Version document with date for reference.
13. Review and Update
The Configuration management of critical assets and systems shall be reviewed annually or when significant changes occur in the organization’s environment, technology, or regulatory requirements or when major update needs to be implemented, or a security/Threat incident occurs.
14. Other Documents.
14.1 IT Configuration Change Management plan and Control Sheet NT-ISMS-10020-1
01 NT - 15-0-3 Control of Documented Information V2 1

1.Information Deletion
This control provides processes and references for identifying, collection, analysis of the Information stored in information systems, devices or in any other storage media that should be deleted when no longer required.
2. Purpose
The purpose of this policy is to prevent unnecessary exposure of sensitive information and to comply with legal, statutory, regulatory and contractual requirements for information deletion.
3. Scope
This Policy is applicable to all NT’s data, information stored in information systems, in cloud and physical devices or removable media.
4. Objectives
Sensitive information should not be kept for longer than it is required to reduce the risk of undesirable disclosure.
5. Classification
This Procedure provides the process to be followed when considering categorizing the data.
5.1 Data life cycle management (DLM)
Information that is not necessary for the business should not be kept. This principle is known as data minimization, and it is meant to protect against unnecessary and disproportionate harm in the event of a security breach.
DLM must be implemented to manage the flow of an information system's data throughout its life cycle.
The data must be classified as per the following tiers:
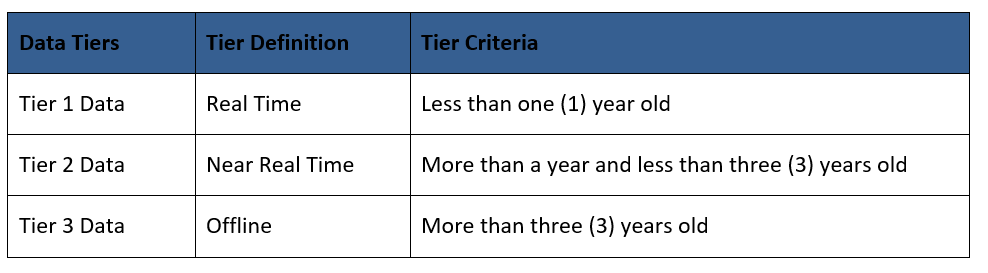
Data migration from one tier to another shall be based on approved criteria.
Data must be secure while it is migrated, proceeded, stored and transferred.
5.2 Identify Sensitivity and Criticality of information
Data to be categorized and Sensitive information should not be kept for longer than is required to reduce the risk of undesirable disclosure.
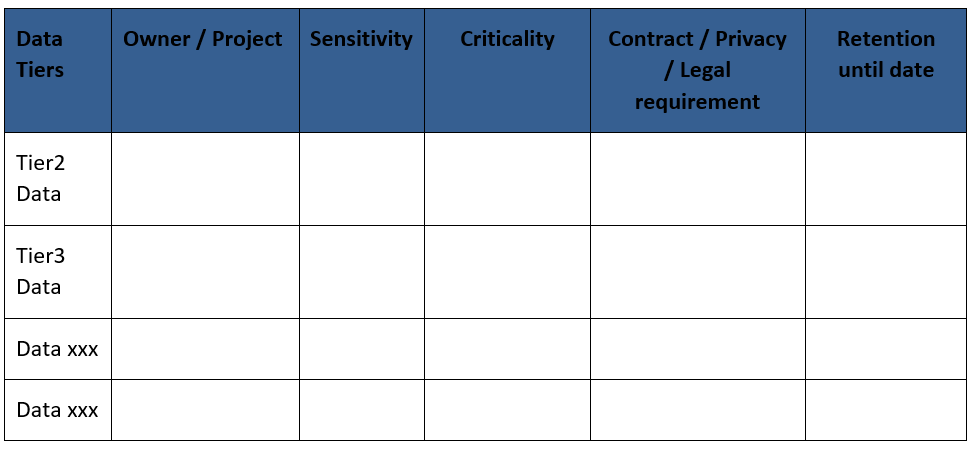
Once the stored data is categorized and retention date is reached, the data no longer needed must be deleted by following the secure deletion procedures.
Please see section 39 Data Life Cycle and Retention policy from
01 NT_ISMS_1001_Information_Security_Policy_Manual_V1.0 for more information.
6 Selecting Deletion Method
In accordance with the NT’s data Tier, sensitivity and criticality classification taking into consideration and relevant regulations, sensitive information should be deleted when no longer required, by:
1.Configuring systems to securely destroy information when no longer required (e.g. after a defined retention period subject to the topic-specific policy on data retention or by subject access request).
2. Deleting obsolete versions, copies and temporary files wherever they are located.
3. Using approved, secure deletion software or encrypted deletion to permanently delete information to help ensure information cannot be recovered by using specialist recovery or forensic tools.
4. Using approved, certified providers of secure disposal services can be considered.
5. Using disposal mechanisms appropriate for the type of storage media being disposed of (e.g. degaussing hard disk drives and other magnetic storage media).
6. Erasure of data on Mobile devices and restoring factory settings or physical destruction to be considered.
7. Where cloud services are used, the organization should verify if the deletion method provided by the cloud service provider is acceptable, and if it is the case, NT should use it, or request that the cloud service provider delete the information.
8. To avoid the unintentional exposure of sensitive information when equipment is being sent back to vendors, sensitive information should be protected by removing auxiliary storage (e.g. hard disk drives) and memory before equipment leaves the organization's premises.
6. Record the results of deletion and logs for future reference and as evidence.
7. Deleting Personal data
NT must only keep personal data as long as necessary and only for the purposes they have specified.
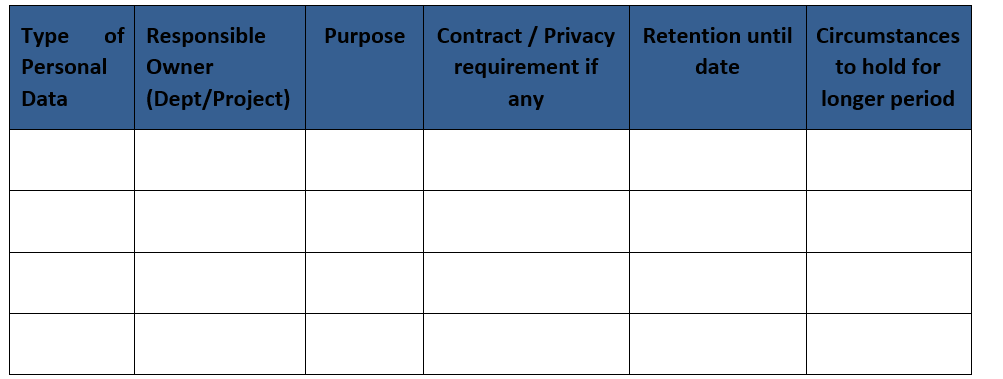
1. Identify the relevant records which have reached their retention period.
2. Notify the relevant business owner to confirm they are no longer needed.
3. Consider any changes in circumstances which may require longer retention of the data.
4. Make a decision on what happens to the data.
5. Document the decision and keep evidence of the action.
6. Consider any changes in circumstances which may require longer retention of the data
Here are different approaches NT can take when the data retention period is reached, such as:
• Delete it - usually the default option.
• Anonymize it.
• Securely destroy it - for physical records, such as HR files.
This deletion process should include backup copies of data. Whilst personal data may be instantly deleted from live systems, personal data may remain within the backup environment, until it is overwritten, in line with an established schedule.
Destruction is the final action for physical records. Physical destruction may include shredding, pulping paper records. Destruction is likely to be the best course of action for physical records when NT no longer needs to keep the data, and when it does not need to hold data in an anonymized format.
8. Process Compliance
8.1 Compliance Measurement
The Head of IT Dept. or his delegated team will verify compliance to this process through approved methods, including but not limited to, sections 5.2, 6 and 7 above. Detailed action taken reports and logs will be maintained and updated with feedback to the Responsible Owner (Dept/Project).
8.2 Exceptions
Any Exception to the process must be approved and recorded by the Information Security Manager in advance and reported to the Management Review Team.
8.3 Non-Compliance
An Employee found to have violated this process may be subject to disciplinary action, up to and including termination of employment.
9. Exit
The effectiveness results are recorded, analysed and appropriate action taken for further improvement.
10. Output
Information Deletion report prepared and shared with Head of IT Dept. and Responsible owner.
11. Review and Update
The Information deletion Procedure shall be reviewed annually or when significant changes occur in the organization’s environment, technology, or regulatory requirements or when serious breach occurs or a security/sensitive/regulatory incident occurs.
Updates to the procedure shall be approved by the Information Security Officer and senior management.
12. Other Documents for Reference
(1) Section 5, Information safeguarding Policy
(2) Section 39, Data Life Cycle and Retention Policy in ISMS policy manual.
(3) Information Deletion Report
1.Introduction
The Information Security Policy is based on the industry’s best practices. It is brief, simple and direct. In today’s business world, messages shall be direct and to the point. For this reason, the policies are set out briefly in one- or two-line sentences, each being easy to follow and understand.
The policy manual is divided into two parts: High-Level Policies and Detailed Policies.
Part I: High-Level Policies. This part discusses policies at a higher level without going into detail. It contains following policies:
From the Desk of Senior Management, the Corporate Security Policy: This is policy set by senior management. It specifies security in very broad and general terms. The primary audience is the departmental mangers, and the secondary audience is all other employees.
Acceptable Usage Policy: This policy summarizes all the generally accepted principles of best practices in information security. This policy contains the minimum that every employee shall know.
Part II: Detailed Policies: This portion has very detailed policies which are covering all domains. This part is mostly used by the technical staff, unlike Acceptable Usage Policy (AUP) which is for all employees of the company. The detailed policies are dynamic and must be reviewed and updated at least once a year or if there is any major change.
Part I: High-Level Policies
2. Corporate Security Policy
This Policy is issued by the senior management. This policy is applicable to all groups and departments.
2.1 Purpose
The purpose of this Policy is to specify requirements and set direction for security from the high-level perspective.
2.2 Scope
The primary audience of this policy are department heads and staff members both in-sourced and out-sourced.
2.3 Policy
2.3.1 The senior management is committed to ensuring that the information is secure and safe.
2.3.2 The senior management is committed to providing the support and resources necessary to implement and maintain a successful Information Security Program.
2.3.3 The Information Security In-charge is appointed to co-ordinate the implementation of all security policies, including Information Security Framework, Information Security Policy and Information Security Procedures.
2.3.4 The Information Security In-charge may escalate any issues or concerns directly to the senior management, if needed.
2.3.5 Information Information shall be protected in terms of confidentiality, integrity and availability (CIA) when it is stored, processed or transmitted, regardless of the storage medium and mode of transmission.
2.3.6 All of the organization’s critical assets (e.g. hardware, software, equipment and data) shall be identified and appropriately protected.
2.3.7 Software developed or procured shall undergo a proper security audit prior to deployment in the production environment.
2.3.8 The organization reserves the right to monitor information traffic on its network. The perimeter network shall be appropriately protected with proper hardware, software and controls.
2.3.9 To provide protection against common threats to the organisation, appropriate safeguards shall be in place, including anti-virus programs, firewalls, intrusion detection prevention (IPS) and other sensors.
2.3.10 All information abuses and security breaches shall be reported to the information security manager.
2.3.11 Business continuity shall be ensured with proper measures.
2.3.12 Information Security Awareness Programs shall be implemented by the Information Security Manager.
2.3.13 Detailed procedures shall be developed for the business’ critical areas.
2.3.14 The information security documents shall be reviewed on yearly basis.
2.3.15 Proper procedures for “incident handling” are in place as a part of management procedure.
2.3.16 The Information Security Manager will ensure that the appropriate training is given to the computer incident response team (CIRT). The CIRT team shall have a documented computer emergency response plan that includes all necessary procedures.
2.3.17 All security incidents, weaknesses and malfunctions shall be reported to the Information Security Manager. The ISM will ensure that the issue is addressed and will devise a mechanism to prevent recurrence in the future.
2.3.18 Appropriate Vulnerability Management will be utilized.
2.3.19 All systems, including the operating systems, shall be hardened to an appropriate level.
2.3.20 Physical security is of prime importance. All efforts shall be made to secure the physical perimeter, physical entry points, office rooms and delivery/loading areas.
2.3.21 All employees shall wear their identity badges when on the company premises.
2.3.22 Discussion of company business information in public places is strictly prohibited.
2.3.23 At the end of a meeting, all white boards shall be cleaned and flip-chart paper removed.
2.3.24 A 'clean desk' policy shall be observed for all sensitive and confidential information.
2.3.25 No games or unauthorized third-party software can be stored or played on company computers.
2.3.26 All advertisements for jobs and help shall be reviewed thoroughly and shall not disclose any sensitive information or future company plans.
2.3.27 In the case where 'specialist advice' is required, an outside consulting company may be approached for help.
2.3.28 All legal requirements must be complied.
2.3.29 Security is everyone’s responsibility. All employees shall follow the security policies applicable to their area.
2.3.30 The resources at this premises are meant for official use only.
2.3.31 The Information Security Manager will be issuing mandatory guidelines and policies.
2.3.32 Any excuse of unawareness of a security policy will not be acceptable.
2.3.33 All of the information stored on or transmitted over network resources remains the official property and management has the right to monitor and audit them.
2.3.34 All confidential information shall be treated in strict confidence. Copying or transmitting the information is strictly prohibited except when required for approved business purpose, written permission must then be obtained.
2.3.35 It is the employee’s responsibility to protect all of the passwords and pass phrases assigned to them. They shall not share these with any other person.
2.3.36 All desktop computers and laptops must have a password-protected screensaver which shall activate after a period of no longer than 10 minutes of non-usage.
2.3.37 All sensitive information stored in a laptop shall be password protected.
2.3.38 All machines shall run the latest antivirus software. No employee is allowed to disable or deactivate the virus detection engine.
2.3.39 The e-mail and internet policies shall be followed while using, e-mail or the internet which are part of the acceptable usage policy.
2.3.40 Unauthorized copying of software is prohibited.
2.3.41 Special care shall be taken when faxing highly sensitive information. All such faxing activities shall be coordinated so that both the person sending the information and the person receiving it are present at the machines at the time of transmission.
2.3.42 Probing and port scanning of external and internal servers is strictly prohibited unless prior permission has been granted.
2.4 Enforcement
In the case of a policy violation, disciplinary action will be taken which may include the termination of employment.
2.5 Responsibility
All employees, departmental managers and the information security manager.
Signature
Date
3. Acceptable Usage Policy
3.1 Purpose
The purpose of the Acceptable Use Policy is to communicate the acceptable behavior of the employee which is necessary to ensure the Confidentiality, Availability and Integrity (CIA) of the systems, assets and information.
3.2 Scope
The scope of this policy covers all permanent/contract employees, consultants and vendor/third parties’ assigned persons working on our premises.
3.3 Policy
3.3.1 Security is everyone’s responsibility every day. All employees should follow the security policies applicable to their area.
3.3.2 All official resources are meant for business use and should be used for business purposes only.
3.3.3 From time to time the nominated Information Security Head will be issuing guidelines that must be followed.
3.3.4 An excuse of unawareness of a security policy will not be acceptable.
3.3.5 All of the information stored on or transmitted over the official resources remains the organization’s property and the management have the right to monitor and audit them.
3.3.6 The confidential information should be treated in strict confidence. Copying or transmitting of the information is strictly prohibited except when required for business purpose through approved permission.
3.3.7 It is the employee’s responsibility to protect all of the passwords and pass phrases assigned to them. They should not share these with any other person.
3.3.8 A password should be changed as per the password policy.
3.3.9 All desktop computers and laptops must have a password-protected screensaver which should activates after a period of no longer than 10 minutes of non-usage.
3.3.10 All sensitive information stored in a laptop should be password protected.
3.3.11 All machines should run the latest antivirus software. No employee is allowed to disable are deactivate the virus detection engine.
3.3.12 The e-mail and Internet policies should be followed while using e-mail or the Internet.
3.3.13 No unauthorized copying of software is allowed.
3.3.14 No official resources should be used to test software as it may malfunction or it may be of malicious in nature. An exception is made for software that is to be used in the commission.
3.3.15 Special care should be taken when faxing highly sensitive information. All such faxing activities should be coordinated so that both the person sending the information and the person receiving it are present at the machines at the time of transmission.
3.3.16 No person is allowed to browse the company network from his PC or any other resource.
3.3.17 Probing and port scanning of external and internal servers is strictly prohibited unless it is part of the official penetration test undertaken by the commission and appropriate counter measures are taken.
3.3.18 No vulnerability probing or similar software should reside on any computer except when being used by the system administrator for the purposes of assessment. As soon as the assessment has been completed, all such software should be removed from the system.
3.4 Enforcement
In the case of a policy violation, disciplinary action will be taken which may include the termination of employment.
3.5 Responsibility
All employees
Part II: Detailed Policies
4 .1 Data Protection and Asset Ownership Policy
4.1 Purpose
The purpose of the policy is to implement proper asset & data ownership for information security. The owner of the asset & data needs to be clearly specified with corresponding duties and responsibilities.
4.2 Scope
The policy applies to all employees who at any time are responsible for data handling, using and owning.
4.3 Policy
4.3.1 The ownership shall be specified for asset & data. The asset & data owner is the person who heads or leads the business unit or function. For example, the finance department manager owns finance data, not the IT Department. IT is merely the “data custodian” or the “data trustee”.
4.3.2 The asset & data owner will communicate the importance of the data, level of sensitivity, controls and monitoring requirements to the data custodian.
4.3.3 The asset & data custodian may not take any action on the data without the permission of the data owner.
4.3.4 It is the responsibility of the asset & data custodian to ensure that asset & data is backed up and stored at a secure place, where applicable.
4.3.5 The asset & data custodian will make sure that there are proper safeguards in place to recover from any disaster.
4.3.6 Any data that is not on the server or is not backed up by the corporate backup facility, e.g. laptop or workstation data will be the responsibility of the end-user to make sure that recovery is possible in the case of system failure or hard disk crash. It is highly recommended to save data on the network drive which is backed up by IT. (Ask IT for the secure network drive access, which is backed up on regular basis. Please also note that the encryption initiative is separate and is not covered in this policy).
4.3.7 The asset & data custodian will make sure that all adequate controls are in place, as specified by the asset & data owner.
4.3.8 The asset & data custodian shall maintain proper documentation of all activities involving the owner's data.
4.3.9 The asset & data custodian will inform the data owner of any risk or shortcomings as soon as they are identified.
4.3.10 Proper Vulnerability Assessment Test shall be performed at a regular interval either on manual basis or on through VA Appliance.
4.4 Enforcement
In the case of a policy violation, disciplinary action will be taken which may include the termination of employment.
4.5 Responsibility
Data Owner, Data Custodians, Information Security Head and Head of IT
5. Information Safeguarding Policy
5.1Purpose
This policy specifies the control and proper safeguard of information generated, stored and transmitted within network.
5.2 Scope
The policy applies to all forms of information regardless of what medium is used for their storage and communication, when viable.
5.3 Policy
5.3.1 The desktop owner will decide about the frequency of their data being backed up, on the basis of importance and retention period of the information.
5.3.2 Corporate server backup frequency and retention shall be defined and implemented by coordination of data owner, CIO and information security manager.
5.3.3 Appropriate backups shall be verified to ensure that it is restorable.
5.3.4 The data owner shall specify the data retention period.
5.3.5 No pirated or other illegal software may be used.
5.3.6 Any software bought from outside vendors or contractors shall be installed only after proper permission from the department head and Information Security Manager have been obtained.
5.3.7 The application program and data shall be separated for security purposes.
5.3.8 All software shall be tested in the test environment prior to being moved to the production machines.
5.3.9 Proper measures such as the installation of anti-virus software, firewalls, IDS, sniffer and others shall be taken to address external and internal threats.
5.4 Enforcement
In the case of a policy violation, disciplinary action will be taken which may include the termination of employment.
5.5 Responsibility
All employees, Departmental Managers and Information Security Manager.
6. Antivirus Policy & Anti-Spam Policy
6.1 Purpose
This document specifies policy related to malicious programs i.e. viruses, worms, Trojans and others.
6.2 Scope
The scope of the policy includes all electronic communication mediums as well as all storage media which can be infected or can store or propagate malicious programs.
6.3 Policy
Antivirus Policy
6.3.1 All machines shall run the latest anti-virus software as approved by commission management.
6.3.2 E-mail with attachments coming from suspicious or unknown sources shall not be opened. All such e-mails and their attachments shall be deleted from the mail system as well as from the trash bin. No one shall forward any e-mail which he thinks may contain virus.
6.3.3 All removable media shall be scanned for viruses before being used.
6.3.4 No pirated software shall be used on the corporate network.
6.3.5 In the case of a virus being found, the Information Security Manager shall be informed immediately. The Information Security Manager will investigate and take proper measures to avoid the event in future.
6.3.6 No user shall clean a virus from a computer unless authorized by the information security manager.
6.3.7 All encrypted material shall be decrypted and checked for viruses before being used.
6.3.8 The e-mail server shall have the antivirus program installed and must check all of the e-mails attachment before sending it to individual mailbox.
6.3.9 All of the updates to the antivirus program shall be automatic from the web or from the central server.
Anti-Spam Checklist
Following are the general points that must be followed:
· E-mails are classified as "potential" spam, and since the proportion of real-spam is very high, the IT department must ensure that measures are in place to filter and delete e-mails that are definitively classified as spam from those that are only suspected as spam.
· The definite spam filter shall use simple rules that look for the presence of known spam words and phrases (such as "Win 7000$ ticket" and all known spelling variants on that word).
· The residual suspected spam e-mails must be reviewed on a daily basis to locate and deliver to the intended recipients those e-mails that are for legitimate business purposes.
· The IT department must put in place and keep up-to-date industry strength tools that automatically identify potential spam and that route such messages for inspection prior to any such messages being passed forward to end-users.
· E-mail from specific and known spam senders must be prevented from being distributed to the recipients. The addresses of such senders are placed in a blacklist.
· The automated identification of potential spam must contain additional measures to prevent e-mail from legitimate business senders from being unnecessarily considered as potential spam. Such measures will be in the form of white-listed sender addresses.
· In the event that the IT department believes it to be beneficial for the business, it may add a legitimate sender address to the whitelist and advise the intended recipient that it has done so.
· IT department tools must scan the content of e-mails to check for the presence of potential malicious software or viruses and route these to a quarantine area.
6.4 Enforcement
In the case of a violation of the security policy, disciplinary action will be taken, up to and including employment termination.
6.5 Responsibility
All employees, CIO and Information Security Manager.
Internet-Related Policies
7. Internet Usage Policy
7.1 Purpose
This document specifies policy related to cyber-surfing and internet usage.
7.2 Scope
The scope of the policy includes all employees, irrespective of their position.
7.3 Policy
7.3.1 Only official Internet connections shall be used. No one is allowed to connect to the Internet through a personal device, as this would open an unsecured backdoor to the corporate network.
7.3.2 Internet facilities will be provided to only those employees who need them for business use. No internet usage for personal purposes is allowed.
7.3.3 While using the internet, no person is allowed to abuse, defame, stalk, harass or threaten any other person, or violate local or international legal rights.
7.3.4 No person is allowed to upload, post, publish or distribute any inappropriate, indecent, obscene, profane, infringing, defamatory or unlawful information or material on the Internet while using the corporate resources.
7.3.5 No person is allowed to post personal advertisements or offer any goods or services using commission’s resources.
7.3.6 In case of the downloading of a file having a size more than 500 MB, prior permission from the respective manager is required.
7.3.7 A visit to any obscene sites or sites which are non-business related will be considered a serious offence.
7.3.8 No one is allowed to use social media unless it is required for the business approve purpose. If any of these are to be used to communicate with a foreign consultant for problem solving or discussion purposes, prior permission from the relevant manager is required.
7.3.9 Internet telephone facilities or internet net meeting shall not be used to discuss sensitive business information.
7.4 Enforcement
In the case of a violation of the security policy disciplinary action will be taken, up to and including employment termination.
7.5 Responsibility
All employees, CIO and Information Security Manager.
8E-mail Usage Policy
8.1Purpose
This document specifies policy related to e-mail usage, including the receiving, replying, forwarding and auto reply functions.
8.2 Scope
The scope of the policy includes all permanent and contract employee irrespective of their position in the commission.
8.3 Policy
8.3.1 The e-mail facility is for business use only. The e-mail address allocated to an employee shall not be used for personal purposes.
8.3.2 No free e-mail facility shall be used to receive or send business-related information.
8.3.3 The e-mail facility shall not be used to spam other users, whether they are inside or outside the network.
8.3.4 No harassing or insulting messages shall be sent inside or outside.
8.3.5 No person is allowed to forward chain letters or pyramid schemes using the organization’s e-mail.
8.3.6 No Confidential document shall be sent to any unauthorized person or any personal free mail account
8.3.7 Official e-mail address shall not be used when posting to newsgroups, as it may disclose internal confidential information. However, business-related newsgroups could be subscribed to using official e-mail address, provided permission is obtained from the respective manager. The attachment to email shall not exceed the limit as communicated by the Information Security officer.
8.3.8 An e-mail program such as outlook shall not be running when employees leave at the end of the workday, as hacker may misuse it.
8.3.9 The e-mail shouldn’t be open when staff leave at the end of the working day, as the hackers may abuse it.
8.3.10 It is prohibited to send any unsolicited email messages including sending "junk mail" or other advertising material to persons who have not specifically requested the material (SPAM emails).
8.3.11 Harassment is prohibited by e-mail, telephone, fax or Paging, in terms of language, frequency or size of messages.
8.3.12 The unauthorized use or falsification of e-mail header information or contents is strictly prohibited.
8.3.13 It is prohibited to create or edit "chain letters" or "Ponzi" or Pyramid Schemes of any kind.
8.3.14 It is strictly prohibited to register with and correspond with newsgroups and blogs (SPAM).
8.3.15 The staff should not expect any privacy for anything they store, send, or receive via the enterprise / agency email system. The organization may monitor messages without notice.
8.3.16 All employees should exercise extreme caution when sending any e-mail from within the organization to outside. Sensitive information should not be passed by any means unless the e-mail message is very important to work and it must be encrypted
8.4 Enforcement
In the case of a violation of the security policy, disciplinary action will be taken, up to and including employment termination.
8.5 Responsibility
All employees, Departmental Managers and Information Security Manager.
Access Control Policies
9. User Account and Login Policy
9.1 Purpose
This policy describes the user account management as it applies to all users, employee, visitor, consultant or other third party.
The policy identifies those regulations that apply to the creation, deletion and revocation to a user account including the access rights and the retention of records of all changes to users’ accounts for a minimum five (5) years.
9.2 Scope
The scope of the policy includes all logins to critical applications and servers, irrespective of their operating platforms.
9.3 Policy
9.3.1 Creation User Account Identification: A user account identification (user-id) will be created based on the request form “NT User-id Request” received from a user department approved by the head of department. To enhance identity verification, accountability, and secure access within the organization, all employees are required to provide / upload a recent and clear photograph to the Microsoft Azure Active Directory (AAD). This measure ensures accurate identification of personnel and supports secure communication, authentication, and compliance with organizational and regulatory requirements as outlined in ISO 27001:2022 controls A.9.2 (User Access Management) and A.9.4.2 (Secure Log-On Procedures).
9.3.2 Access to a system: The access to any system shall be granted based on the role of the user. A formal and pre-approved process shall be followed for assigning access to any individual. The access shall be approved by the immediate manager and the Head of Information Security.
9.3.3 Deletion Access to a system: The access to a system shall be revoked when a person leaves the organization or is assigned a different role.
9.3.4 Revocation of User Account: The revocation of a user account would be performed, based on specific request the head of user department or HRD upon termination of employment of the user.
9.3.5 Review of Users Access Privileges: The roles and privileges shall be reviewed on regular basis. This include but not limited to the review of user’s rights, user deletion and user termination of employment.
9.3.6 Retention of Users Accounts: The department is responsible of retention of all records of user’s accounts for a minimum of five (5) years for audit trails.
9.3.7 Login Policy Conditions:
· Every user shall have a uniquely assigned login name and password to access corporate computer systems.
· Each person is responsible for the login name assigned to him/her.
· User login shall be disabled after three unsuccessful attempts and reactivated upon request to the system administrator.
· A password shall not be displayed the screen.
· In the case where an incorrect login name or password is entered, no response which reveals any information shall be given. For example, systems shall not respond with “incorrect password for xxx login name". This message will reveal that such a valid username exists leaving the attacker having only to crack the password.
· The screen saver shall initiate after fifteen minutes on inactivity.
· In the case where a job function is based on a general user id, the user id shall be changed to a unique one.
· In the case of a “critical corporate core system”, the end user shall not be able to access the operating system command line.
· For the issue of a new login name, a signed form indicating the relevant privileges is required, either in hardcopy or as part of the internal workflow software.
· All login names and privileges shall be reviewed at regular intervals in close co-operation with the human resources functions.
· A login which is not successful shall be logged and the log reviewed at regular intervals.
· In the case of an employee leaving the organization, the department manager will be responsible for making sure that all the employee's system IDs are revoked prior to final settlement.
· All usernames and passwords must be stored, handled and distributed to the systems securely.
· Each user of an IT system must have a unique username and password.
· Common, familiar and general usernames shouldn't be used.
· The user is not allowed to share his username and password with other people under any circumstances. The user shall bear full direct responsibility for all activities carried out through his user account on any of the permitted systems.
· The same username should not be re-issued to other users.
· Username criteria must be consistent with the standard naming standards as per the policy to ensure that the username does not give any impression on the user level, privileges, or access rights, such as verifier or releaser.
· The username is chosen based on the spelling of the name in English as recorded in the employee's identity.
9.4 Responsibility
The Information Security Head is responsible to administer the user account with access rights based on the request received from a user department and HRD (for employee revocation for clearance).
10. Password Protection Policy
10.1 Purpose
This document specifies policy related to password protection, change and maintenance.
10.2 Scope
The scope of the policy includes all employees, irrespective of their position.
10.3 Policy
10.3.1 The password is private property of the user and should not be traded or written in a place can be viewed. The employee's password should not be disclosed at all by e-mail, telephone, internet sites, etc., or to any person, including technical support personnel.
10.3.2 To provide more security for your information, the password must be at least 8 characters long and must be a mixture of letters, numbers, and symbols (a1 $, etc.).
10.3.3 When you set the password, you must avoid guessing words such as:
· Phone number or birth date.
· A sequence of numbers such as (0123456789)
· Duplicate numbers such as (44444444) or a sequence of characters from the keyboard (qwerty).
· Words found in Arabic or other dictionaries such as "password" and other words that can be easily discovered by some programs or people.
10.3.4 Passwords must be changed every 90 days at maximum, and alert messages will be sent automatically two weeks before the current password expires. Please note that once the password expires, the user will be able to access his e-mail from outside the organization only after contacting support. To reconfigure the password.
10.3.5 The passwords for the operational services of some applications and servers, which are affected by changing the relevant systems, are excluded from the previous point.
10.3.6 Passwords must be changed for accounts that are used separately from the Active Folder System, the central identity verification system, every six months, always striving to integrate with this system as much as possible, including network devices such as routers, Switches, firewalls or devices for SMTP Gateways or Internet Proxies
10.3.7 The employee's password should not be disclosed either by e-mail, telephone, internet sites, etc., or to any person, including technical support personnel.
10.3.8 The password should not be changed until at least four days after the last change.
10.3.9 Do not repeat the last three passwords. The word can be repeated after at least three times.
10.3.10 Password encryption must be applied.
10.3.11 The password should not be displayed in the password input field.
10.3.12 When creating of an account for a user, a random password must be issued for use only for the first time and may be communicated to the user orally.
10.3.13 The features of username blocking and password expiration should be determined based on system requirements, classification, importance (being critical systems), and side effects in case of violation.
10.3.14 All default passwords shall be changed by the user prior to use of the system.
10.3.15 No common name or personal information shall be used as a password e.g. date of birth, spouse's name, pet name or phone number.
10.3.16 A password shall always be kept secret and shall never be disclosed to co- workers and colleagues. Other requirements as discussed in AUP (when viable) are as follows:
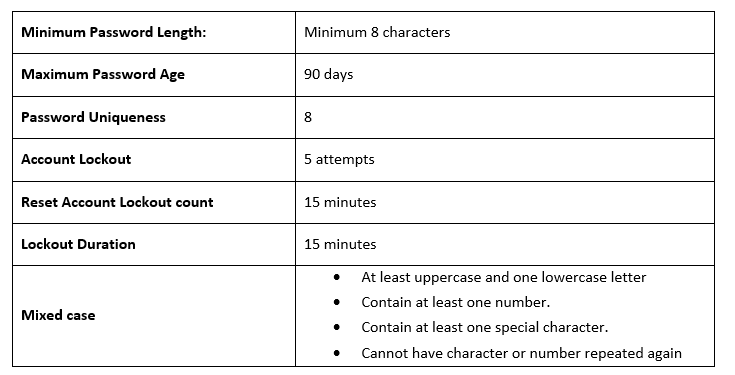
10.3.17 No person shall leave his/her PC or terminal without logging off or password protecting the screen. A password shall not be stored in encrypted format in the system files and shall never be in text format.
10.4 Enforcement
In the case of a violation of the security policy, disciplinary action will be taken, up to and including employment termination.
10.5 Responsibility
All employees, Departmental Managers and the Information Security Manager.
Network Policies
11. Router and Firewall Security Policy
11.1 Purpose
Routers and firewalls are the most vulnerable components of perimeter security. This document provides the minimum-security protection for the perimeter routers and firewalls.
11.2 Scope
The scope covers the firewall and routers at the perimeter network. The policy is also applicable to devices such as proxy servers and others.
11.3 Policy
11.3.1 Routers and firewalls shall be placed in a physically secure area.
11.3.2 Local user accounts shall not be configured on the router. The firewall management terminal shall be separate from the main box.
11.3.3 Strong authentication shall be ensured for all routers, switches and firewall.
11.3.4 The password for routers shall be encrypted using the "enable encryption" option.
11.3.5 If any of the service is not explicitly allowed on firewall shall be denied.
11.3.6 The firewall computer shall be a dedicated machine. It shall not be used to run proxy, web or any other services.
11.3.7 Routers and firewalls shall disallow all invalid IP addresses coming from the internet i.e. 10.0.0.1 to 10.255.255.254 and 172.16.0.1 to 172.16.255.254, 192.168.0.1 to 192.168.255.254
11.3.8 Routers and firewalls shall not allow IP broadcasts.
11.3.9 IP-directed broadcasts shall not be allowed on the firewalls and routers.
11.3.10 Source routing shall be disabled on the routers.
11.3.11 SNMP shall not be enabled on either the firewalls or the routers. In cases where SNMP is needed for system management, a standardized SNMP community string shall be used.
11.3.12 Web-based service is allowed on the router.
11.3.13 The firewall shall be configured to stop SYN attack.
11.3.14 Firewall shall stop IP spoofing, fragmented packets and tear-drop.
11.3.15 The relevant department manager shall approve the list of access rules prior to deployment on routers.
11.3.16 Backup of the configuration files of the firewall and routers shall be stored at a safe place.
11.3.17 The audit log of the firewall shall be regularly checked.
11.3.18 A firewall shall filter the entire ActiveX and java program.
11.3.19 Egress, i.e., the outgoing traffic shall also be checked by the firewall.
11.3.20 Provided performance is not the issue, user level checking shall be done at the firewall level, rather than at IP addresses level.
11.3.21 The login banner on the router shall not display any welcome message. A warning message shall appear: "Warning: This is a Private Network. “Any UNAUTHORIZED ACCESS TO THE SYSTEM IS STRICTLY PROHIBITED”. If you are not authorized logoff now. All activities are logged. Any violator will be prosecuted."
11.4 Enforcement
In the case of a policy violation, disciplinary action will be taken which may include the termination of employment.
11.5Responsibility
Network administrator, Firewall administrator, Information Security Manager.
12. Hotspot Connection Security Policy
12.1 Purpose
This document specifies policy related to Hotspot connections.
12.2 Scope
The scope of the policy includes all Hotspot connections within or outside the organization.
12.3 Policy
12.3.1 No company owned resource shall connect to unsecure Hotspot.
12.3.2 The Hotspot connection shall be avoided to the organization’s desktops and laptops.
12.3.3 If there is any business need to use the Hotspot prior permission is required from the Information Security Head.
12.3.4 Anything downloaded shall be scanned for viruses prior to use.
12.3.5 No Hotspot device must have default username and password.
12.3.6 Privilege Accounts of all Hotspots devices must be changed before putting them in Production environment.
12.4 Enforcement
In the case of a violation of the security policy, disciplinary action will be taken, up to and including employment termination.
12.5 Responsibility
All employees, Departmental Managers and the Information Security Manager.
13DMZ Policy
13.1Purpose
Demilitarized zone (DMZ) is one of the most important components of the organization’s network. This policy defines the requirement for all equipment which is operated within DMZ, whether owned, leased, borrowed or brought by vendors for testing.
13.2 Scope
All DMZ equipment owned by organization or outsourced.
13.3 Policy
13.3.1 Servers accessible from the internet shall be placed on DMZ, where appropriate.
13.3.2 There shall be a defined owner for each DMZ
13.3.3 All equipment shall be hardened to the maximum possible extent. There shall be a system hardening checklist developed by the system administrator for each DMZ component.
13.3.4 All required patches and fixes shall be applied to all components of the DMZ and shall be cross checked.
13.3.5 Only approved hardware, software and operating systems shall be deployed in the DMZ.
13.3.6 All insecure services and protocols which are not needed shall be disabled.
13.3.7 If remote administration is required, a secured channel such as SSH or IPSEC shall be used.
13.3.8 All security-related events shall be logged.
13.3.9 Complete documentation of the system shall be maintained with major emphasis on the following:
· Configuration management
· Change management.
13.3.10 In the case where a DNS is deployed, special care shall be taken to protect the DNS server and to protect against DNS poisoning.
13.3.11 Proper auditing shall be done at regular intervals; all logs of critical systems such as the firewall shall be checked on a regular basis.
13.3.12 Any new service shall be approved by the Information Security Manager prior to being moved to the DMZ production environment.
13.3.13 All equipment belonging to outsourced companies, vendors or service providers must meet the corporate security criteria.
13.4 Enforcement
Any employees who violate the security policy will be subject to disciplinary action, which may include employment termination.
Vendors, outsourced organizations and others may be subject to financial penalties including contract termination.
13.5 Responsibility
All employees, Departmental Managers and the Information Security Manager.
14Virtual Private Network (VPN) Policy
14.1Purpose
The purpose of the VPN policy is to provide guidelines for secure remote access to the local networks.
14.2 Scope
The VPN policy applies to connections to internal network and to third parties including consultant, vendors and contractors.
14.3 Policy
14.3.1
As VPN is an extension of the organization’s network, all of the security rules apply to the remote client as if they were within our network.
14.3.2
All critical connections to the outside shall use the safe channel. The only choice is to use IPSEC for VPN, where available.
14.3.3
It is highly recommended that a one-time password be used.
14.3.4
"Tunnel mode" is preferred whenever the VNP is used. If performance is an issue, "transport mode" may be used. with the permission of the Information Security Manager.
14.3.5
All files transferred through VPNs shall be subject to antivirus scanning.
14.3.6
The VPN timeout period is 30 minutes of inactivity.
14.4 Enforcement
Any policy violation will be subject to disciplinary action, which may go so far as employment termination.
14.5 Responsibility
Network administrator, VPN user and the Information Security Manager.
15 Wireless Communication Policy
15.1 Purpose
The Purpose of the policy is to provide guidelines for network connections via wireless communication.
15.2 Scope
The policy covers all wireless devices such as mobile phones, PDA and laptop computers and others, which are connected to internal network.
15.3 Policy
15.3.1
The Information Security Manager shall approve all wireless devices connected to the corporate network.
15.3.2
A strong authentication server shall be used to grant permission to the wireless devices.
15.3.3
All wireless devices shall use encryption while communicating, where possible.
15.3.4
Prior to the granting of a connection to the network devices, it would be preferable that the authentication server verify the hardware level address check (e.g., the MAC address) or in case of mobile phone the serial number.
15.4 Enforcement
Any policy violation will be subject to disciplinary action, which may go so far as employment termination.
15.5 Responsibility
Network Administrator, mobile equipment user and the Information Security Manager.
16Remote Access Policy
16.1Purpose
This policy describes acceptable ways of connecting to the organization’s network.
16.2 Scope
The scope of the policy covers all connections which are dialed in (rather than dialed-up) by employees and third parties, including consultants, vendors and contractors.
16.3 Policy
16.3.1
Remote access shall be used for the business purpose only.
16.3.2
A remote connection extends the organization’s network, so all corporate policies apply to the remote connection.
16.3.3
For a dial-in remote connection, the call back feature shall be implemented.
16.3.4
The call back feature shall authenticate the call back number, from the authorized list of the database prior to dialling.
16.3.5
The remote connection shall be secured by a strong authentication mechanism as specified by the information security manager.
16.3.6
In the case of remote login, Virtual Private Network (VPN) must be used. The preferred protocols L2TP/IPsec, OpenVPN (VPN protocol secured using TLS, or SSTP/VPN using TLS. The use of PPTP and VPN/SSL must be avoided where possible.
16.3.7
Preferably, dial-in connections shall use the firewall.
16.3.8
An anti-virus check shall be performed on all files downloaded through remote connections.
16.3.9
All remote connections shall be logged and monitored.
16.3.10
In case, intrusion detection system is deployed it shall generate alert to the system administrator if attack is detected.
16.4 Enforcement
A policy violation will be the subject to disciplinary action, which may go so far as employment termination.
16.5 Responsibility
Network Administrator, remote connection user and the Information Security Manager
Application Development Policies
17. General Application Development and Deployment Policy
17.1 Purpose
This policy specifies the requirements for application development both in-house and outsourced.
17.2 Scope
This policy is applicable to all core business software and other software. However, it excludes the operating systems.
17.3 Policy
17.3.1
Formal security specifications are required for all systems developed in-house or Outsourced.
17.3.2
The Application shall not have username and password hardcoded, the authentication must be performed through Lightweight Directory Access Protocol (LDAP).
17.3.3
The application shall not show any information till the Log-on process is complete.
17.3.4
The application shall display a general notice warning that the computer should only be accessed by authorized users.
17.3.5
The application shall not provide help message during the log-on procedure that would aid an unauthorized user.
17.3.6
The application shall validate the log-on information only on completion of all input data. If an error condition arises, the system should not indicate which part of the data is correct or incorrect.
17.3.7
The development of the software shall be as per the Best Practices of System Development Lifecycle SDLC or Agile for small Projects.
17.3.8
Changes to systems within the development lifecycle shall be controlled by the use of formal change control procedures.
17.3.9
When operating platforms are changed, business critical applications shall be reviewed and tested to ensure there is no adverse impact on organizational operations or security.
17.3.10
Modifications to software packages shall be discouraged, limited to necessary changes and all changes shall be strictly controlled.
17.3.11
Principles for engineering secure systems shall be established, documented, maintained and applied to any information system implementation efforts.
17.3.12
Organizations shall establish and appropriately protect secure development environments for system development and integration efforts that cover the entire system development lifecycle.
17.3.13
The organization shall supervise and monitor the activity of outsourced system development.
17.3.14
Testing of security functionality shall be carried out during development.
17.3.15
Acceptance testing programs and related criteria shall be established for new information systems, upgrades and new versions.
17.3.16
Test data shall be selected carefully, protected and controlled.
17.3.17
The application shall protect against brute force log-on attempts.
17.3.18
The application shall log unsuccessful and successful attempts.
17.3.19
The application shall raise a security event if a potential attempted or successful breach of log-on controls is detected.
17.3.20
The application shall display the following information on completion of a successful log-on:
· Date and time of the previous successful log-on.
· Details of any unsuccessful log-on attempts since the last successful log-on.
17.3.21
The application shall not display a password being entered.
17.3.22
The application shall not transmit passwords in clear text over a network.
17.3.23
The application shall terminate inactive sessions after a defined period of inactivity, especially in high-risk locations such as public or external areas outside the organization’s security management or on mobile devices.
17.3.24
The application shall restrict connection times to provide additional security for high-risk applications and reduce the window of opportunity for unauthorized access.
17.3.25
No test account shall be present on the production machine.
17.3.26
The production and development/test environments shall be separate.
17.3.27
Any error in a system shall be reported and must be traced to the programmer who developed the program.
17.3.28
Prior to the system being moved to production, proper documentation shall be done.
17.3.29
No trial version or beta version software may be used in the production environment unless approved by management.
17.3.30
Proprietary business logic shall reside on the central core machine rather than on the desktop systems.
17.3.31
Mission critical software shall have the escrow arrangement, and the software shall be tested and validated by a third party and must be demonstrated to perform as specified.
17.3.32
All computer programs, routines, applets and documentation shall display the copyright statement.
17.3.33
After authentication, the username and password shall not be recorded on the server.
17.3.34
All access shall be on a “need to know” basis.
17.3.35
The application file storing the information shall be password protected.
17.3.36
It is preferred either to own all of the core application source codes or there shall be escrow agreements with the vendors who have provided the applications.
17.3.37
Prior to moving program to the production environment, there shall be exhaustive testing of the application.
17.3.38
No application shall be moved to the production environment without the proper signing of a UAT (user acceptance test).
17.3.39
The developer shall not have any account on the production machine; prior to moving to the production environment all such accounts shall be removed.
17.3.40
Databases shall follow the password policy.
17.3.41
An update to the database shall be carried out on a well-defined, secure channel
17.3.42
In the case where a data warehouse application is used, access shall be restricted to top and middle management.
17.3.43
In future, application software which are either developed in-house or through outsourced party, must implement the essential component of third-party code review or at least peer review for all source code. This review process must be documented.
17.4 Enforcement
A policy violation will be subject to disciplinary action, which may go so far as employment termination.
17.5 Responsibility
CIO, Systems Analyst, Programmer and the Information Security Manager
18. Web Application Development Policy
18.1 Purpose
This policy specifies the requirements for application development in-house or outsourced.
18.2 Scope
This policy is applicable to all web applications currently deployed, developed or would be developed in future.
18.3 Policy
18.3.1
A proper user ID and password shall be created for the web application user. Any web pages that communicate password and username data shall use the SSL protocol.
18.3.2
The web application password shall not be displayed on the screen. The “copy and paste" feature on the password field shall be disabled.
18.3.3
The password shall preferably be stored in a one-way hash.
18.3.4
For data that is of confidential nature, a secure channel shall be used.
18.3.5
The 'press back' button shall clear the fields containing sensitive data.
18.3.6
An SSL connection shall have an expiry time.
18.3.7
The application shall be programmed in such a way that in case of an error, there shall be a standard error page rather than a system-generated error (e.g. 404) returned to the user as this would reveal the internal network.
18.3.8
The web server shall not provide banner information.
18.3.9
The input string from the customer shall be validated prior to processing, as it may be manipulated to contain some secret command.
18.3.10
There shall be an incident response procedure if something goes wrong on the server or if there is any security breach.
18.3.11
A penetration test shall be performed on the application as specified by the information security manager.
18.4 Enforcement
Any policy violation will be subject to disciplinary action, which may go so far as employment termination.
18.5 Responsibilities
CIO, Systems Analyst, Webmaster, Web-Programmer and the Information Security Manager.
Physical Security Polices
19General Physical Security Policy
19.1Purpose
This policy specifies the requirements for physical security. No matter how good the security solutions and products, if physical security is weak, everything can be compromised.
19.2 Scope
This policy is applicable to all physical areas of the office/s, including those available now and those which may be added in the future.
19.3 Policy
19.3.1
The Information Security Manager shall define security zones. For example:
A. Zone A: The reception area, where anyone can walk in (minimum security).
B. Zone B: Area accessible to employees and authorized visitors.
C. Zone C: Area to which only selected employees have access such as the computer room and other business-critical areas.
19.3.2
The Information Security Manager shall apply appropriate measures for each of the zones.
19.3.3
Office floor plans and diagrams of telephone, electrical, water and network cabling lines, as well as extinguisher locations shall be documented and maintained.
19.3.4
A proper access control list with corresponding work times shall be maintained.
19.3.5
The entrance shall be properly guarded.
19.3.6
Proper fire prevention and detection mechanisms shall be in place.
19.3.7
A telephone directory for emergency phone numbers shall be maintained and must be easily accessible.
19.3.8
A first aid box shall be provided and must be easily accessible and regularly checked and replenished.
19.3.9
All areas of the office shall be properly lighted.
19.4 Enforcement
A policy violation will be subject to disciplinary action, which may go so far as employment termination.
19.5 Responsibilities
Administration & HR Department/representative and Information Security Manager. In future, some of the tasks relating to physical security may be delegated to the Corporate Security Officer when that post is created. For the time being, the Information Security Office will handle these tasks.
20. Computer Room/Data Center Security Policy
20.1 Purpose
This policy discusses the requirements for safeguarding the computer systems and personnel operating in the computer room/data center.
20.2 Scope
This policy is applicable to computer room and data center, including those which are available now and those which may be added in the future. The Data Center consists of the physical boundaries including the servers’ cabinets, network cabinets, storage, fire suppression system and precession cooling.
The Data Center supporting infrastructure such as UPS and Batteries room, Staging room and generators are not considered part of the Data Center.
20.3 Policy
20.3.1
Access to the Data center will be restricted to authorized persons only.
20.3.2
No public visits or tours of the Data center are allowed.
20.3.3
Vendor and third-party representatives, if they visit the room, shall be escorted.
20.3.4
A time-in and time-out register shall be maintained for the Data center.
20.3.5
A proper fire alarm and fire extinguisher system shall be in place.
20.3.6
Humidity control shall be implemented and monitored.
20.3.7
A proper temperature shall be maintained and monitored.
20.3.8
A proper emergency procedure for the Data center shall be developed and be easily accessible. Personnel shall be trained so that the procedure is executed efficiently, when required. All procedures shall be audited at regular intervals.
20.3.9
The Information Security Manager will co-ordinate the development of Data center standards.
20.3.10
The Information Security Manager will co-ordinate measures to ensure that a reliable power supply to the Data center is in place and that adequate safeguards are there to protect the equipment.
20.3.11
No drinking, eating or smoking is allowed in the Data center.
20.3.12
Use of a cellular phone is prohibited in the data center.
Maintenance Policy for Data Centers
20.3.13
The prior approval of the Director of the Operations, Department of the General Directorate of Information Technology Services shall be obtained if the Data Centers are visited by third party for the purpose of network installation or any work related to IT equipment or services.
20.3.14
The prior approval of the General Department of Safety and Support Services shall be obtained if third party wish to enter the Data Center for the purposes of electromechanical works such as electricity, air conditioning, fire and lighting control systems. The Data Center administrator must be informed by the General Directorate of Information Technology Services.
20.3.15
The information of any person entering the Data Center for the purpose of maintenance shall be recorded by the Operations Department of the General Department of Information Technology Services or the General Department of Safety and Support Services as per the nature of the work as referred in point 20.13 and 20.14.
20.3.16
Any work related to IT equipment or services or electromechanical works shall be carried out under the supervision of a member of the General Directorate of IT Services or the General Department of Safety and Support Services, according to nature of the work.
20.3.17
In case, any interruption of services is expected because of the electromechanical work, it shall be carried out after the official working hours.
20.3.18
No equipment, spare parts, cabinets, shelves, couplings, or furniture should be taken out or taken in from the Data Center without the approval of the Operations Department of the General Directorate of IT Services.
20.3.19
Any work carried out under or on raised floor shall be carried out with the approval of the Data Center Officer from the General Directorate of Information Technology Services and under the supervision of specialists from the General Department of Safety and Support Services. It should be ensured that the raised floor work doesn’t affect the airflow of the cabinets.
20.3.20
Extreme care should be taken to ensure the cleanliness of the Data Center especially during and after maintenance work. It shall be ensured that any work done regarding the cutting, drilling and nailing is performed outside the physical boundary of the Data Center, where possible. This is to ensure that no dust enters the Data Center because of any maintenance work. The maintenance site must be professionally cleaned above and under the raised floor or at other location.
20.3.21
When there is no maintenance on the floor, all tiles must be kept in place, leaving no openings in the floor, so that airflow in the rooms is not affected.
20.3.22
It is prohibited to un-box new equipment from their boxes inside the Data Centers, this task should be performed at the designated areas (staging room) next to the Data Centers. It is also prohibited to keep any boxes, shipping materials or similar waste inside the Data Centers for any reason.
20.3.23
Any magnetic media that will be decommissioned and contain important data will be destroyed, based on the approved destruction policy of the organization and according to the classification of the data it contains.
20.3.24
If any data center device that is not functional, the owner of the devices shall be informed. This device shall be moved to the warehouse after a month from the notice date.
20.3.25
Device removal must be supervised by the General Department of Safety and Support Services. Device’s delivery should be done according to special forms.
Access control
20.3.26
Permanent access rights are granted by the General Department of Safety and Support Services after obtaining the prior approval of the Data Centers Officer in the General Directorate of Information Technology Services.
20.3.27
The list of authorized person having the access to the data center must be reviewed periodically. If the person is no longer required to access the data center, his name shall be removed from the access list.
20.3.28
The authorized visitor or authorized third party access to the Data Center must be granted by the Data Center officer.
20.3.29
Access to the Data Center room shall be granted as per access control verification policy using a biometric measure such as a retina or fingerprint scan, as well as another means, such as a password or smart card.
20.3.30
In case the Data Center automatic access malfunction, the process should be handled manually, with the necessary approvals from the Director of the Operations Department of the General Directorate of IT Services, Director of Buildings Department in the General Administration of Safety and Support Services according to nature of the work required to enter during the system failure.
20.3.31
The Data Center must be equipped with surveillance cameras to record any movement, the recording must be maintained for at least one month.
20.3.32
The access to devices and network in Data Center must be controlled by unique username and password, as per the Access Control & User Naming Policy.
20.3.33
The passwords must not be shared with others and persons must follow the instruction of the password policy.
20.3.34
Any device which is un-attended, either it should be logged off or must be having the screen saving password.
General controls
20.3.35
The doors of Data Center should always be closed, whether an engineer is present or not.
20.3.36
All equipment cabinets and servers must always be closed, except during the maintenance times or when certain work is performed on the cabinet or on the equipment within the cabinet.
20.3.37
All electrical connections must follow the approved standards as issued by the Data Center manager. No unauthorized connection will be used in the Data Centers except in emergency situations and for temporal period.
20.3.38
All devices must be connected to a backup power source through (UPS), which should be able to sustain the equipment for at least 15 minutes. It is preferred to have more than one power source to the equipment.
20.3.39
In case any new equipment or server need to be purchased for the Data Center, a prior permission and specification for the device must be obtained from the General Directorate of IT Services.
20.3.40
Any server in operation which is located outside the Data Center, should be moved into the Data Center to facilitate proper inventory of the devices and the ease of maintenance. This will also facilitate the proper provisioning of ventilation, temperature, humidity and the fire suppression facility.
20.3.41
All software and operating systems on the servers of the Data Centers must be genuine, licensed and certified.
20.3.42
Anti-virus policies must be followed (and Anti-virus software shall be genuine and updated version must be maintained).
20.3.43
Security update policy for the patch update must be followed.
20.3.44
IP Addressing should be done through the General Directorate of IT Services.
20.3.45
The servers must be on a separate network which should be isolated from the users’ network, with sufficient security controls.
20.3.46
All equipment supplied and installed in the Data Centers must be Rack-Mountable and any exception must be obtained for the Data Center Manager providing the justification for the exception.
20.3.47
The level of humidity and temperature shall be maintained and monitored as per the acceptable limits, which shall be provided by the General Directorate of Information Technology Services, based on the accepted standards in this field, such as the ASHRAE standard.
20.3.48
The electromechanical devices in the information centers must be supported by a valid maintenance contract which must mention the specific response time as per the criticality, impact and urgency in case of any technical malfunction or accidental situation. Periodic preventive maintenance should be performed monthly or at least quarterly.
20.3.49
In general, disinfectants, sterilizers and chemical liquids are not allowed to enter Data Centers, except those which are authorized to be used in the Data Center by the relevant specialist.
20.3.50
It is strictly prohibited to bring any food or beverages into the Data Centers except for the designated areas.
20.3.51
It is strictly prohibited to change the air conditioning settings or obstruct the airflow or air conditioning openings or modify them. If required, it should be with the permission from the General Department of Safety and Support Services.
20.3.52
Temperature and humidity sensors in the Data Center rooms should be used and connected to a central monitoring system capable of sending alerts via mail and / or mobile devices.
Illegal use
20.3.53 The Data Center or any of its affiliated resources may not be used in the following:
· Exploitation or use of any other works not assigned to it.
· Hosting any sites before filling out the necessary forms and these sites shall be authorized from Saudi Center for Network Information.
· Any work stipulated by the system of informatics crimes and government regulations issued in this regard.
· Sharing personal accounts with any other person or waiver of those accounts.
20.4 Enforcement
A policy violation will be subject to disciplinary action, which may go so far as employment termination.
20.5 Responsibilities
Information Security Manager and CIO.
21. Magnetic Media Life Cycle and Decommissioning Policy
21.1 Purpose
This policy discusses the requirements for the handling of magnetic media.
21.2 Scope
This policy is applicable to all media, i.e. external hard disk, mirrored hard disk, flash drive, compact disc, magnetic tapes and magnetic tape cartridges
21.3 Policy
21.3.1 An inventory of all critical magnetic media shall be maintained and kept in the secure magnetic media library.
21.3.2 All magnetic media shall be properly labeled.
21.3.3 All magnetic media shall be physically destroyed prior to discarding.
21.3.4 The shelf life of all media shall be ascertained from the respective vendors and shall be monitored.
21.3.5 All media shall be scanned for viruses prior to use.
21.3.6 Media life cycle will have following stages:
A. Magnetic Media Acquisition: The Magnetic Media must be acquired from the pre-approved media like USB Flash Drive, USB hard drive, SD cards and others.
B. Commissioning: Any magnetic media which is used must be tested and for critical data, read-after-write feature shall be enabled through software.
C. Life of the Magnetic Media: At the time of commissioning the actual life must be determined on either of the following basis:
I. Number of usage or
II. Expiry Date
D. Media Decommission and Destruction: the media shall be decommissioned as per the approved procedures. The Magnetic Media shall be physically destroyed and it must not be re-cycled as magnetic media. However, the material used, for example plastic and the steel can be recycled.
21.4 Enforcement
A policy violation will be subject to disciplinary action, which may go so far as employment termination.
21.5 Responsibilities
Information Security Manager and CIO.
22. Server Security Policy
22.1 Purpose
This security policy discusses the issue of securing the internal servers. This is to make sure that there is no unauthorized access to corporate information.
22.2 Scope
This policy applies to all servers either owned or operated by the organization.
22.3 Policy
22.3.1 The production servers shall be located in a physically secure place.
22.3.2 All configurations of the servers shall be documented and approved by the CIO and information security manager.
22.3.3 Each server shall have documentation of configuration, operating system version, patches installed, backup and recovery procedure.
22.3.4 All change management policies shall be strictly implemented on the servers.
22.3.5 The Information Security Manager shall approve all configurations of servers.
22.3.6 Services not required, such as the web server and others, shall be disabled.
22.3.7 The log of the server shall be monitored on a regular basis, as specified by the information security manager.
22.3.8 All security patches shall be installed on the server after confirmation that they will not have any adverse effect on the running applications.
22.3.9 All guests and default accounts will be either disabled or their password changed. The privileged account like super user and root shall only be used when required.
22.3.10 A regular audit would be performed by the information security manager.
22.4 Enforcement
A policy violation will be subject to disciplinary action, which may go so far as employment termination.
22.5 Responsibilities
System Administrators, Information Security Manager and CIO.
Operations Management Policies
23. Configuration Management Policy
23.1 Purpose
This security policy deals with proper documentation for the configuration of critical systems.
23.2 Scope
This policy applies to all servers, network equipment and others, either owned or outsourced.
23.3 Policy
23.3.1 All system configurations, including hardware, software and core business software shall be documented.
23.3.2 Configuration management shall be considered as the documentation baseline. All change from this baseline shall be documented as per change management policy.
23.3.3 Prior to roll out, any modification made to the default configuration shall be documented in the configuration management documentation.
23.3.4 The Information Security Manager shall approve all configuration documentation.
23.3.5 Configuration management and change management documentation shall be used together, in case of recovery.
23.4 Enforcement
A policy violation will be subject to disciplinary action, which may go so far as employment termination.
23.5 Responsibilities
System Administrators, Information Security Manager and CIO.
24. Change & Release Management Policy
24.1 Purpose
This security policy sets out the proper change management documentation for the all critical systems.
24.2 Scope
This policy applies to all critical servers, network equipment and business-critical software owned or outsourced.
24.3 Policy
24.3.1 Standardized methods and procedures shall be used for the efficient and prompt handling of the changes and revision control.
24.3.2 All changes shall be documented and prior approval must be obtained for all changes made to critical production systems.
24.3.3 A "change request" shall be presented to the relevant manager for approval. The Information Security Manager will co-ordinate the workflow for change approval.
24.3.4 All requested changes shall be evaluated and have their impact assessed before approval or disapproval.
24.3.5 All changes, once approved, shall be scheduled in such a way as to ensure the availability of a time slot for a rollback, shall something unexpected happen.
24.3.6 Documentation for a change request shall be accompanied by detailed, step-by-step procedures to do the change. It shall also include a detailed roll back procedure in case the change fails and desired result is not achieved.
24.3.7 Whenever there is a need to change the application software, system software, LAN or any hardware, the change shall be appropriately authorized and approved.
24.3.8 Every change shall be thoroughly tested and fully documented.
24.3.9 Changes shall be made when there is minimum or no activity on the system. In case, where there is more than one change to be carried out at a given time, the changes shall be queued on the basis of business and technical priority.
24.3.10 Changes shall only be approved after adequate consideration of the associated impact and implications.
24.3.11 Changes, once accepted, shall be entered into the change management log.
24.3.12 The change shall be fully tested and the result presented to the respective manager.
24.3.13 A change management summary report shall be presented to higher management on a weekly basis.
24.3.14 The change must be moved into the production environment through release management.
24.3.15 The Release Manager shall issue a release ticket.
24.3.16 Release will be classified as a Release Unit or Release Package. The Release Unit shall correspond to single Request for Change (RFC) whereas Release Package will combine number of RFCs in one Release Ticket.
24.3.17 The release will be the responsibility of the Release Manager and he shall ensure that proper testing is performed prior to the acceptance of the release.
24.3.18 Each release must have a back-out procedure or the roll-back plan to ensure that if a release fails the system can be restored to the previous baseline.
24.3.19 There must be a Post-Implementation review after the release to ensure the effectiveness of the release process.
24.3.20 ITIL Best Practices shall be followed while managing the Release Management process.
24.4 Enforcement
A policy violation will be subject to disciplinary action, which may go so far as employment termination.
24.5 Responsibilities
System Administrators, Information Security Manager and CIO.
25. Printed Output and Distribution Policy
25.1 Purpose
This security policy sets out the requirements for printed output and its distribution.
25.2 Scope
This policy applies to all critical servers, network equipment and business-critical software owned or outsourced.
25.3 Policy
25.3.1 All computer-generated sensitive reports shall have a classification level, based on the sensitivity of the report.
25.3.2 The owner of the application will decide the classification level.
25.3.3 In case where the report classification is not 'general', the first page shall be the banner page and must indicate the "classification level" and “username” for whom the report has been printed.
25.3.4 The Information Security Manager will ensure that a procedure exists that ensures that the report goes only to the authorized individual.
25.3.5 The person who prints the report is responsible for ensuring the proper protection of the information it contains.
25.3.6 Shall someone find a report that is classified and is not intended for him/her, he/she shall inform the information security manager.
25.4 Enforcement
A policy violation will be subject to disciplinary action, which may go so far as employment termination.
25.5 Responsibilities
Report Printing User, Information Security Manager and CIO.
Business Continuity Policies
26. General Business Continuity Policy
26.1 Purpose
The purpose of this policy is to provide directions regarding business continuity.
26.2 Scope
This policy applies to all business-critical systems as referred to in the business impact analysis and risk assessment in the corporate security policy.
26.3 Policy
26.3.1 The Information Security Manager will ensure that the availability of the business-critical system is ensured as per the risk assessment requirement of the corporate policy.
26.3.2 Depending on the risk assessment report (as per the corporate security policy), Senior management will decide the scope of the recovery plan.
26.3.3 Crucial systems, as per the risk assessment, shall have reliable recovery procedure in case of disaster.
26.3.4 The word “disaster” needs to be defined and the respective risk evaluated by senior management. The Information Security Manager shall coordinate this task.
26.3.5 All documentation related to business continuity shall be regularly updated.
26.3.6 The requirements shall be determined regarding information security in-case of the adverse events like disaster.
26.3.7 Special care must be taken to control the required level of continuity for information security during an adverse situation.
26.3.8 The effectiveness of continuity controls must be evaluated at regular intervals in order to ensure that they are valid and effective during adverse situations.
26.3.9 Information processing facilities shall be implemented with redundancy sufficient to meet availability requirements.
26.3.10 The Information Security Manager will ensure that there is an appropriate contingency plan and emergency response plan” are in place.
26.4 Enforcement
A policy violation will be subject to disciplinary action, which may go so far as employment termination.
26.5 Responsibilities
Business Department Heads, Information Security Manager and CIO.
27. Backup and Recovery Policy
27.1 Purpose
This security policy specifies the backup and recovery standards.
27.2 Scope
This policy applies to all critical servers, network equipment and business-critical software owned or outsourced.
27.3 Policy
27.3.1 Backup of all critical devices, including the server, communication equipment and mission-critical hardware and software, shall be undertaken.
27.3.2 Frequency of the backup will be decided according to the nature of the application being used.
27.3.3 The preferred backup method is "full backup" followed by a "differential backup".
27.3.4 Unless there is justification, the “incremental backup” method shall be avoided because in the case of a data recovery, one backup failure may make the entire backup process fail.
27.3.5 When storing historical data, the shelf life of the media shall be considered.
27.3.6 The timing of "distributed backups" shall be planned to have the minimum impact on the corporate network.
27.3.7 The backup process shall not violate the confidentiality of the system.
27.3.8 No public computers shall be used for backing up sensitive data.
27.3.9 All archive data must be tested on a regular basis.
27.3.10 All backups shall be verified to check the validity of the media. The “read after write” option shall be chosen, where available.
27.3.11 In the case where distributed backup agents are not available, business-critical data shall be put in a directory on the server to be backed up. Information security officer will make the necessary arrangements.
27.3.12 The information security manager, in consultation with the CIO, will make arrangement for electronic vaulting i.e., storing of the backup data at an off-site location.
27.3.13 Once the backup media is no longer usable, it shall be physically destroyed or preferably burnt. However, for the time being it will be kept until approved by the regulator.
27.4 Enforcement
A policy violation will be subject to disciplinary action, which may go so far as employment termination.
27.5 Responsibilities
All employees, Information Security Manager and CIO.
Personnel and Third Party Polices
28 Personnel/HR Policy
28.1 Purpose
This security policy specifies guidelines and standards related to Human Resource (HR) with special reference to Information Security.
28.2 Scope
This policy applies to all permanent and contract employees.
28.3 Policy
28.3.1 Prior to hiring a prospective employee, HR must do a background check, contact references and validate the education testimonial.
28.3.2 Employees shall sign the undertaking accepting responsibility for adherence to security policies.
28.3.3 HR will ensure that security responsibility is included in the job responsibilities of the employee.
28.3.4 The Terms and Conditions of employment shall mention the information security policy for each employee.
28.3.5 HR will ensure that segregation of duties and job rotation is implemented, where possible.
28.3.6 When an employee leaves the employ of the company, HR will ensure that an exit interview is conducted.
28.3.7 HR will ensure that the person has all computer accounts removed prior to his/her final settlement and assets are returned.
28.3.8 In the case where employment is terminated without the consent of the employee, he/she shall be escorted from the premises.
28.4 Enforcement
A policy violation will be subject to disciplinary action, which may go so far as employment termination.
28.5 Responsibilities
HR, Information Security Manager and Department and CIO.
29. Third Party & Supplier Management Policy
29.1 Purpose
This security policy specifies the standard and guidelines for the third party and outsourcing.
29.2 Scope
This policy applies to parties whether they are vendors, contractors, consultant or outsourced professionals.
29.3 Policy
29.3.1 The risks associated with third party involvement and outsourcing shall be identified and appropriate measures taken to address them.
29.3.2 A non-disclosure agreement is essential before sensitive information is shared with a third party.
29.3.3 The role and responsibilities of the third party shall be clearly defined.
29.3.4 Third party access to the corporate computer system will be given only after the signing of a formal contract which shall contain all security requirements by which the third party is to abide.
29.3.5 All third party and external users, if defined on the system, shall have a mandatory expiry date.
29.3.6 Third party or outsourced tasks which require dial-in and dial-up privileges, shall be restricted and monitored.
29.3.7 Information security requirements for mitigating the risks associated with supplier’s access to the organization’s assets shall be agreed with the supplier and documented.
29.3.8 All relevant information security requirements shall be established and agreed with each supplier that may access, process, store, communicate, or provide IT infrastructure components for, the organization’s information.
29.3.9 Agreements with suppliers shall include requirements to address the information security risks associated with information and communications technology services and product supply chain.
29.3.10 The supplier agreements shall be regularly monitored, reviewed and audited.
29.3.11 Changes to the provision of services by suppliers, including maintaining and improving existing information security policies, procedures and controls, shall be managed, taking account of the criticality of business information, systems and processes involved and re-assessment of risks.
29.4 Enforcement
A policy violation will be subject to disciplinary action, which may go so far as employment termination. For third party it may lead to contract termination.
29.5 Responsibilities
Department Heads, HR, Information Security Manager and CIO.
Security Awareness
30. Security Awareness Policy
30.1 Purpose
The purpose of this policy is to keep employees up to date with information security which is changing at an astonishing pace.
30.2 Scope
The policy applies to all employees, no matter what position they hold.
30.3 Policy
30.3.1 The Information Security Manager will organize at least one workshop per year and the attendance of every employee will be mandatory.
30.3.2 In the case where an employee has not attended the workshop, his/her respective manager will be informed.
30.3.3 If necessary, the Information Security Manager takes help of brochures, posters and/or special security awareness screen saver to increase the information security.
30.3.4 A security awareness booklet and brochure will be given to every new employee. The last page will be the undertaking that need to be signed by the person.
30.3.5 It is the responsibility of every individual to keep him/herself up to date through involvement in security program training.
30.3.6 Any security breach or query about security shall be communicated to the Information Security Manager immediately. Knowledge of security policies will be assessed during appraisal of the employee.
30.4 Enforcement
In case of a policy violation, disciplinary action will be taken which may include the termination of employment.
30.5 Responsibility
All employees, especially the Information Security Manager and CIO.
Information Exchange
31. Information Exchange Related Policies
31.1 Purpose
This security policy is to maintain the security of Information and Software Exchange with in the organization and with any external entity.
31.2 Scope
This policy applies to parties whether they are vendors, contractors, consultant or outsourced professionals.
31.31.3 Policy
31.3.1 The exchange of information and software between organizations shall be based on a formal exchange policy and carried out in line with the exchange agreements. All such requirements shall be part of the SLA.
31.3.2 The media in transit if it contains sensitive information shall be encrypted.
31.3.3 If the information needs to be access to Internet proper control like “HTTPS” must be applied.
31.3.4 The E-mail server shall check the attachment for any malicious code.
31.3.5 No sensitive information or critical information shall be left at public printing facilities for Example: copiers, printers, fax machines, as they may be access by unauthorized persons.
31.3.6 The staff members shall not discuss confidential conversation in public places or open offices and meeting places with non-sound proofed walls.
31.4 Enforcement
A policy violation will be subject to disciplinary action, which may go so far as employment termination. For third party it may lead to contract termination.
31.5 Responsibilities
Department Heads, HR, Information Security Manager and CIO.
Mobile Computing and Communication
32. Mobile Computing and Communication Related Policies
32.1 Purpose
This policy is to ensure information security when using the mobile computing and communication.
32.2 Scope
This policy applies to notebooks, Tablet PC, Laptop, Smart phones, Smart Cards and similar devices.
32.3 Policy
32.3.1 When using mobile computing it shall be ensured that business information is not compromised.
32.3.2 The mobile computing device used shall have access control, malicious control protection and backup facilities.
32.3.3 It shall also have the capability to adopt cryptography techniques if required.
32.3.4 Special care shall be taken if the mobile device is taken to public places, meeting rooms and other unprotected areas outside the organization’s building.
32.3.5 The remote access to business information across public network using mobile computing custody shall only take place after successful a, and with suitable access control mechanism.
32.3.6 No mobile devices shall be connected to corporate network. The Wifi will have separate network. `
32.4 Enforcement
A policy violation will be subject to disciplinary action, which may go so far as employment termination. For third party it may lead to contract termination.
32.5 Responsibilities
Department Heads, HR, Information Security Manager and CIO.
Teleworking
33 Teleworking Related Policies
33.1 Purpose
This policy applies to personnel working remotely and at outside location.
33.2 Scope
This policy applies to parties whether they are vendors, contractors, consultant or outsourced professionals.
33.3 Policy
33.3.1 The Teleworking policy shall only be allowed if IT is satisfied that the appropriate security and arrangements and controls are in place.
33.3.2 The security control applicable for Teleworking are in protection against the theft of equipment and information, the unauthorized disclosure of information, unauthorized remote access to organization’s internal systems or misuse of facilities.
33.3.3 It shall be ensured that the dispute regarding the rights to intellectual property develop on a privately own equipment is addressed.
33.3.4 The organization shall ensure that only authorized software are used by the organization’s equipment. In case of Tele-Working. The policy must be enforced that no new software is installed by the user on organization’s equipment.
33.3.5 The anti-virus protection, malicious software and firewall requirements must be addressed.
33.3.6 Proper backup, Business Continuity, Revocation of Authority and access rights must be in place.
33.4 Enforcement
A policy violation will be subject to disciplinary action, which may go so far as employment termination. For third party it may lead to contract termination.
33.5 Responsibilities
Department Heads, HR, Information Security Manager and CIO.
Cryptography
34. Cryptography Related Policies
34.1 Purpose
This policy applies to protect the confidentiality, authenticity or integrity of information by cryptography means.
34.2 Scope
This policy applies to parties whether they are vendors, contractors, consultant or outsourced professionals.
34.3 Policy
34.3.1 The cryptography shall be applied based on risk assessment exercise.
34.3.2 The algorithm of encryption, the strength, the type and the number of bits of key required must be in line with the risk identified during risk assessment.
34.3.3 The cryptographic algorithm must be applicable to information which is stored as well as to the information which is transmitted over an unsecured network.
34.3.4 The cryptographic controls must be used to addressed following issues:
a. Confidentiality: Using encryption of information to protect sensitive or critical information either stored or transmitted.
b. Integrity/Authenticity: Using digital signature or message authentication codes to protect the authenticity and the integrity of stored or transmitted sensitive or critical information.
c. Non-repudiation: Using cryptography techniques to obtain proof of the occurrence or non-occurrence of an event or action.
34.4 Enforcement
A policy violation will be subject to disciplinary action, which may go so far as employment termination. For third party it may lead to contract termination.
34.5 Responsibilities
Department Heads, HR, Information Security Manager and CIO.
Capacity Management
35. Capacity Related Policies
35.1 Purpose
This policy is to minimize the risk of system failure because of poor capacity management planning.
35.2 Scope
This policy applies to all systems within the organization.
35.3 Policy
35.3.1 The use of resources shall be monitored, tuned and projections made for future capacity requirements to ensure the required system performance.
35.3.2 The detective controls shall be put in place to indicate problems as soon as they arise.
35.3.3 The particular attention needs to be paid to any resources with long procurement lead time or high cost.
35.3.4 The trends in usage, particularly in relation to business application or management information system must be captured, monitored and analyzed.
35.3.5 The controls shall be in placed to identify and avoid potential bottlenecks and depends on key personnel that might present a threat to system security or services.
35.4 Enforcement
A policy violation will be subject to disciplinary action, which may go so far as employment termination. For third party it may lead to contract termination.
35.5 Responsibilities
Department Heads, HR, Information Security Manager and CIO.
Additional Policies
36 Asset Management Policies
36.1 Purpose
This policy is to maintain the assets of the organization in a professional and secure manner.
36.2 Scope
This policy applies to all systems within the organization.
36.3 Policy
36.3.1 The inventory list of all assets shall be maintained and it must be classified into following:
a) Hardware
b) Network Equipment
c) Software
d) Information
e) Human Resources
Note: Although the network equipment’s are included in hardware but because of the importance and sensitivity, network equipment is categorized separately.
36.3.2 The Assets must have Asset Owner, who shall be accountable for their Asset. Asset Owner shall be responsible for assigning classifications to information assets based on the asset management policy; and responsible for protecting, managing and handling of critical information asset.
36.3.3 An Asset inventory shall be maintained, which shall contain, but not limited to:
a. Asset identification.
b. Asset description.
c. Asset location.
d. Asset classification.
e. Asset value.
f. Asset label.
g. Asset owner.
36.3.4 IT or the related department who are maintaining the assets are the Asset Custodian rather than Asset Owners.
36.3.5 The Asset Custodian are responsible for following:
a. Protecting information to ensure its confidentiality, integrity and availability.
b. Applying information security policies and best practices to the information.
c. Determining and documenting the requirements for authorized access to the information.
d. Providing backup and recovery of information.
e. Detecting and responding to security violations, security breaches and vulnerabilities.
f. Monitoring compliance with information security policies and best practices.
g. Reporting any suspected or actual security violations, security breaches, and incidences of compromised information to the information owner.
36.3.6 Individuals, groups, or organization’s authorized by the information owner to access information assets are the Information Users, who are responsible for:
a. Understanding the information asset classifications, abiding by the security controls defined by the information owner and applied by the information custodians.
b. Maintaining and conserving the information asset classification and labeling established by the information owners.
c. Contacting the information owner when information is unmarked or the classification is unknown.
d. Using the information only for approved purposes.
e. Reporting any suspected or actual security violations, security breaches, and incidences of compromised information to the information custodian or information owner.
36.4 Enforcement
A policy violation will be subject to disciplinary action, which may go so far as employment termination. For third party it may lead to contract termination.
36.5 Responsibilities
Department Heads, HR, Information Security Manager and CIO.
37. Risk Management Policies
37.1 Purpose
This policy is to minimize the risk to the organization by applying the relevant control.
37.2 Scope
This policy applies to all systems within the organization.
37.3 Policy
37.3.1 Risk Assessment must be performed for all information asset to minimize the risk exposure to the Organization.
37.3.2 Risk assessment must be conducted for assets, owned and leased by the Organization, whether developed in-house and/or operated by business partners.
37.3.3 Risk Assessment shall assess potential business impact, evaluating threats and vulnerabilities to meet the business requirement for information security in a cost-effective manner.
37.3.4 Risk Assessment process shall be conducted in a coordinated manner and involving all the stakeholders including business owners, systems owners, security analysts, operational risk management staff and other subject matter experts.
37.3.5 The Risk must be evaluated against the following:
a. Risk Appetite
b. Risk Tolerance
c. Risk Threshold
37.3.6 Proper Risk Treatment must be performed as per the procedure and Risk must be treated as one of the following:
a. Risk Acceptance
b. Risk Mitigation
c. Risk Transfer
d. Risk Avoidance
37.3.7 The Risk shall be mitigated by applying the controls to ensure that the Risk are in the Risk Appetite or Risk Tolerance limit of the Organization.
37.3.8 The Residual risk must be checked after the risk treatment.
37.3.9 The risk assessment exercise must be performed at least once in a year.
37.4 Enforcement
A policy violation will be subject to disciplinary action, which may go so far as employment termination. For third party it may lead to contract termination.
37.5 Responsibilities
Department Heads, HR, Information Security Manager and CIO.
38. Information Systems Policies
38.1 Purpose
This policy is to minimize the risk to Information Systems.
38.2 Scope
This policy applies to all systems within the Organization.
38.3 Policy
38.3.1 Information Systems assets must be properly classified and maintained. (An Information System is a group of components that interact to produce information).
38.3.2 The value of the Information Asset must be determined by their owners. The value of the asset increases in direct relationship to the importance, sensitivity of the information.
38.3.3 A Risk Assessment must be performed at least once in a year on all information assets and appropriate risk treatment must also be performed by applying relevant controls.
38.3.4 The lifecycle of the Information Asset must be determined and the decommissioning of the Information Asset must be performed to ensure that no information is compromised at the end of the lifecycle.
38.3.5 Information systems may not only include ICT components but also certain components outside the scope of ICT. Information System shall also include the information not residing on computer systems but are maintained manually.
38.3.6 Information System category and scope must be reviewed at a regular interval.
38.4 Enforcement
A policy violation will be subject to disciplinary action, which may go so far as employment termination. For third party it may lead to contract termination.
38.5 Responsibilities
Department Heads, HR, Information Security Manager and CIO.
39 Data Life Cycle and Retention
39.1 Purpose
This policy is to maintain the data classification and lifecycle for Information, Data and Intellectual Property of the organization.
39.2 Scope
This policy applies to all systems within the organization.
39.3 Policy
39.3.1 Data life cycle management (DLM) must be implemented to manage the flow of an information system's data throughout its life cycle.
39.3.2 The data must be classified as per the following tiers:

39.3.3 The Data be stored at the different storage media with appropriate response time which are in-sync with requirements of the Tiers and the technology deployed. As a rule, newer data, and data that must be accessed more frequently, is stored on faster, but more expensive storage media, while less critical data is stored on cheaper, but slower media.
39.3.4 Data migration from one tier to another shall be based on approved criteria.
39.3.5 Data must be secure while it is created, proceeded, stored and transferred.
39.3.6 Once the data is no longer needed it must be securely decommissioned and destroyed.
39.3.7 A Risk Assessment must be performed at least once in a year on all data and appropriate risk treatment must also be performed by applying relevant controls.
39.4 Enforcement
A policy violation will be subject to disciplinary action, which may go so far as employment termination. For third party it may lead to contract termination.
39.5 Responsibilities
Department Heads, HR, Information Security Head and CIO.
40. Privacy Policies
40.1 Purpose
This policy is to ensure the privacy of the sensitive information.
40.2 Scope
This policy applies to all systems within the organization.
40.3 Policy
40.3.1 The Information which is stored, processed and transmitted must be appropriately secured as per the risk assessment.
40.3.2 The information shall not be shared with any entity without the prior permission of the Information Owner.
40.3.3 All information must be stored on secure server and in a secure database, where only authorized programs must access the information only on need-to-know basis.
40.3.4 The information shall not be sold to any entity.
40.3.5 The information must be securely destroyed once it is no longer required or it has reached end of its life cycle.
40.3.6 In case the credit/debit card is used for certain payments, no credit/debit card number, expiry date or CVV number will be stored. The only information which can be stored is the name of the person, name of the credit/debit card company and the last 4 digits. (This policy is for future implementation, currently the credit card is not accepted through the web site)
40.3.7 The cookies must not be used to store any sensitive information nor should it collect any sensitive information for any third party.
40.3.8 The browsers used throughout the organization, must be configured so that accepting cookies feature is disabled.
40.3.9 Any breach of information primacy must be communicated to the Information security Officer in writing and it must be thoroughly investigated for the root cause analysis. Appropriate corrective and preventive action must be performed.
40.3.10 The only exception for the privacy policy is when certain information is asked by the legal authority (for example, police or court order) through legal process.
40.4 Enforcement
A policy violation will be subject to disciplinary action, which may go so far as employment termination. For third party it may lead to contract termination.
40.5 Responsibilities
Department Heads, HR, Information Security Manager and CIO.
41. Disaster Recovery Policies
41.1 Purpose
This policy is to minimize the risk of system failure because of poor capacity management planning.
41.2 Scope
This policy applies to all systems within the organization.
41.3 Policy
41.3.1 The human life safety is the first priority of the Disaster Recovery Plan (DRP) plan.
41.3.2 A formal risk assessment shall be undertaken to determine the requirements for the disaster recovery plan.
41.3.3 The goal of the DRP is to enable the organization to recover all critical infrastructure elements, systems and networks, in accordance with key business activities within Recovery Time Objective (RTO) limits. The main objective is to recover the core activates as per the risk assessment and business impact analysis.
41.3.4 It shall be ensured that the impact of any disruption is minimized and the risk is accepted by the senior management as per the risk assessment exercise.
41.3.5 All staff must be aware of the DRP and of their respective roles in executing it, and be ready to serve their assigned plan tasks, regardless of rank or position, in whatever capacity the Emergency Response Team sees fit.
41.3.6 The DRP Manager shall ensure that the proper media handling procedures are in place.
41.3.7 A comprehensive, tested, verified and validated Disaster Recovery Plan is must for the organization. The DRP will be tested periodically in a simulated environment to ensure it can be realistically implemented in emergency situations and that management and staff understands how it is to be executed.
41.3.8 Senior Management shall periodically monitor the progress of the DRP and will periodically review its relevance. Senior Management will be informed on a regular basis of progress in the development of the DRP and the test results of simulated emergency situations.
41.3.9 The DRP documentation shall be reviewed at least once in a year or after any major change in the organization.
41.3.10 Systems changes will be frozen for as long as the contingency is in effect.
41.4 Enforcement
A policy violation will be subject to disciplinary action, which may go so far as employment termination. For third party it may lead to contract termination.
41.5 Responsibilities
Department Heads, HR, Information Security Manager and CIO.
42. Clean Desk & Clear Screen Policy
42.1 Purpose
This policy has been developed to determine minimum requirements to maintain a "clean desk" - where sensitive / confidential information about our employees, intellectual property, customers or suppliers should be allocated on safe areas.
42.2 Scope
This policy applies to all employees within the organization.
42.3 Policy
42.3.1 Employees must ensure that all sensitive / confidential information, whether printed or electronic, is safe in their area of work at the end of the day and when or when they are away from the office for a long time.
42.3.2 The employee must secure the work computer if the working area is not occupied.
42.3.3 The computer must be turned off at the end of the working day.
42.3.4 Users shall ensure that unattended equipment has appropriate protection. A clear desk policy for papers and removable storage media and a clear screen policy for information processing facilities shall be adopted.
42.3.5 Remove any confidential or sensitive information from the office and keep it in the drawer when the office is not busy and at the end of the working day.
42.3.6 File cabinets containing confidential or sensitive information must remain closed and locked when not in use.
42.3.7 Keys used to access restricted or sensitive information should not be left at office.
42.3.8 Laptops must either be locked with a lock cable or locked away in a drawer.
42.3.9 It is strictly forbidden to leave passwords on sticky notes that are published on or under a computer, and should not be left in writing in an accessible place.
42.3.10 Prints that contain confidential or sensitive information should be removed immediately from the printer.
42.3.11 When disposing of the documents, the secret or sensitive parts should be shredded in the official shredding boxes or placed in secret insurance boxes.
42.3.12 Whiteboards that contain confidential or sensitive information should be scanned.
42.3.13 All portable computers such as laptops and tablets must be closed.
42.3.14 Mass storage devices such as CDs, drives, or electronic storage devices (Flash Drive) that contain sensitive information should be placed in a locked drawer.
A policy violation will be subject to disciplinary action, which may go so far as employment termination. For third party it may lead to contract termination.
42.5 Responsibilities
Department Heads, HR, Information Security Manager and CIO.
43. Log Management, Security Incidents & SIEM Policy
43.1 Purpose
This policy has been developed to ensure that the Logs are managed and protected securely. The policy also discusses the Security Incidents and the role of Log Management in handling such incidents along with Security Information and Event Management (SEIM) if fully implemented.
43.2 Scope
This policy applies to all employees within the organization.
43.3 Policy
43.3.1 The Logs of the servers and other important machines shall be managed securely.
43.3.2 The clock synchronization must be performed for all equipment as it is a pre-requisite for proper Log Management.
43.3.3 The Log must be pulled from the device to ensure that even if the devices are compromised the Log can be fetched.
43.3.4 Event logs recording user activities, exceptions, faults and information security events shall be produced, kept and regularly reviewed.
43.3.5 Logging facilities and log information shall be protected against tampering and unauthorized access.
43.3.6 System administrator and system operator activities shall be logged and the logs protected and regularly reviewed.
43.3.7 The Security Incidents are like any other incidents which may be reported to the service desk as service desks are single point of contact with the end users.
43.3.8 The Service Desk must have an interface with an Information Security officer to forward the Security Related Incident.
43.3.9 The Log viewer must co-relate all of the logs and classify them on the basis of priority.
43.3.10 Management responsibilities and procedures shall be established to ensure a quick, effective and orderly response to information security incidents.
43.3.11 Information security events shall be reported through appropriate management channels as quickly as possible.
43.3.12 Employees and contractors using the organization’s information systems and services shall be required to note and report any observed or suspected information security weaknesses in systems or services.
43.3.13 Information security events shall be assessed and it shall be decided if they are to be classified as information security incidents.
43.3.14 Information security incidents shall be responded to in accordance with the documented procedures as automated in the service desk.
43.3.15 Knowledge gained from analyzing and resolving information security incidents shall be used to reduce the likelihood or impact of future incidents.
43.3.16 It shall be ensured that the automated process exist for the identification, collection, acquisition and preservation of information which can serve as evidence. It is highly recommended to go for security Information and Event Management Tool to automate the process.
43.4 Enforcement
A policy violation will be subject to disciplinary action, which may go so far as employment termination. For third party it may lead to contract termination.
43.5 Responsibilities
Department Heads, HR, Information Security Manager and CIO.
44. Group Policies
44.1 Purpose
This policy controls the working environment of user accounts and computer accounts and provides centralized management and configuration of operating systems, applications, and users' settings in an Active Directory environment. A version of Group Policy called Local Group Policy ("LGPO" or "Local GPO") also allows Group Policy Object management on standalone and non-domain computers..
44.2 Scope
This policy applies to all systems within the organization.
44.3 Policy
44.3.1 Group Policy shall enforce controls what users can and cannot do on a computer system, which should include following:
a. Enforce a password complexity policy.
b. Prevent unidentified users from remote computers to connect to a network share.
c. Block access to the Windows Task Manager
d. Restrict access to certain folders.
e. Flash drive usage
44.3.2 Group Policy shall rely on Active Directory to distribute GPOs to computers which belong to a Windows domain.
44.3.3 Group Policy refresh default values (i.e., Microsoft Windows refreshes its policy settings every 90 minutes with a random 30-minute offset. On Domain controllers, Microsoft Windows does so every five minutes. During the refresh, it discovers, fetches and applies all GPOs that apply to the machine and to logged-on users.) shall be maintained. If there is change required, there must be Normal Change Request.
44.3.4 Group policy following hierarchy shall be maintained.
a. Local - Settings at the computer's local policy. (Windows Vista and later Windows versions allow individual group policies per user accounts.)
b. Site – These are the Group Policies associated with the Active Directory site in which the computer resides. (“The Active Directory site” is a logical grouping of computers and Systems. It is intended to facilitate management of those computers based on their physical proximity.) In case, multiple policies are linked to a site, they are processed in the order set by the administrator.
c. Domain – These are Group Policies associated with the Windows domain in which the computer resides. If multiple policies are linked to a domain, they must be processed in the order set by the administrator.
d. Organizational Unit - Group policies assigned to the Active Directory organizational unit (OU) in which the computer or user are placed. (OUs are logical units that help organizing and managing a group of users, computers or other Active Directory objects.) If multiple policies are linked to an OU, they must be processed in the order set by the administrator.
Important Note: The resulting Group Policy settings applied to a given computer or user are known as the Resultant Set of Policy (RSoP). RSoP information may be displayed for both computers and users using the gpresult command.
44.3.5 Resultant Set of Policy (RSoP) shall be audited at the regular interval.
44.4 Enforcement
A policy violation will be subject to disciplinary action, which may go so far as employment termination. For third party it may lead to contract termination.
44.5 Responsibilities
Department Heads, HR, Information Security Manager and CIO.
45. Identity Lifecycle Management (Including Deleting User)
45.1 Purpose
Identity Lifecycle Management, or ILM, purpose is to manage creation, management, coordination, restriction of identification, access and governance of identities.
45.2 Scope
This policy applies to all systems within the organization.
45.3 Policy
45.3.1 The first step for identity management is to request for system access using the user access form.
45.3.2 The access is approved by the relevant manager.
45.3.3 The request is forwarded to information security for the user creation which is part of the provisioning access.
45.3.4 The access is created with the default username and password.
45.3.5 The default username and password must be changed on a first login.
45.3.6 When a user is moving from one department to another department, the access must be updated.
45.3.7 When the employee leaves the organization, the access must not be deleted but it should be deactivated. The user is deactivated but not deleted, in order to make sure that the record exist for the future auditing.
45.4 Enforcement
A policy violation will be subject to disciplinary action, which may go so far as employment termination. For third party it may lead to contract termination.
45.5 Responsibilities
Department Heads, HR, Information Security Manager and CIO.
46 Database Policies
46.1 Purpose
This policy is to maximize the Database Security, irrespective of the platform.
46.2 Scope
This policy applies to all databases within the organization.
46.3 Policy
46.3.1 It is mandatory that the Database server and the Application server must not be running on the same server.
46.3.2 Strong encryption such as AES 256 must be used for all sensitive files and tables stored in the Database.
46.3.3 The backup of the Database must be encrypted using AES 256 or better.
46.3.4 The Web Application Firewall (WAF) must be running on all Database servers.
46.3.5 The debug or password recovery tools, utilities, and SDKs are removed or secured.
46.3.6 Database server must not be installed on the domain controller.
46.3.7 Database server authentication mode must be avoided and the windows authentication mode shall be preferred, where applicable.
46.3 .8 Unnecessary services shall be disabled on the database server.
46.3.9 All protocols except TCP/IP are disabled within SQL Server. Check this using the Server Network Utility. The TCP/IP stack is hardened on the database server.
46.3.10 Unused accounts are removed from Windows and SQL Server.
46.3.11 The latest patches must be installed for all Database servers and applied.
46.3.12 The privilege user must not be used for day-to-day operations. A least-privileged local/domain account is used to run the various Database services, for example, back up and replication.
46.3.13 The administrator account is renamed and has a strong password.
46.3.14 Null sessions (anonymous logons) are restricted.
46.3.15 Remote logons are restricted.
46.3.16 Log files are configured with an appropriate size depending on the application security requirement.
46.3.17 The latest patches must be applied.
46.3.18 The audit log must be enabled and secured. The audit logs shall be monitored on regular basis.
46.4 Enforcement
A policy violation will be subject to disciplinary action, which may go so far as employment termination. For third party it may lead to contract termination.
46.5 Responsibilities
Department Heads, HR, Information Security Manager and CIO.
47. Data Center Policy
47.1 Purpose
This policy is to minimize the risk of system failure because of poor capacity management planning.
47.2 Scope
This policy applies to all systems within the organization.
47.3 Policy
47.3.1 The Data center must have the proper Lightning, Grounding & Emergency Power Off (EPO)
47.3.2 When determining the adequacy of a structural floor to handle the weight of computer equipment, use the following pounds-per-square foot (lb/ft2), kilograms-per-square-meter (kg/m2), rating:
a) The floor loading of computer equipment should not exceed 50 lb/ft 2 (240 kg/m2) with a partition allowance of 20 lb/ft2 (100 kg/m2) for a recommended total floor load of 70 lb/ft 2 (340 kg/m2).
b) The raised floor weight plus the cable weight adds additional weight of 10 lb/ft 2 (50 kg/m2) uniformly across the total area used in the calculations.
i.This additional weight is included in the 70 lb/ft 2 (340 kg/m2) floor loading. The total area is defined as the machine area plus 0.5 service clearance.
ii.When the service clearance area is also used to distribute machine weight (weight distribution/service clearance), 15 lb/ft 2 (75 kg/m 2) is considered for personnel and equipment traffic. The distribution weight is applied over 0.5 of the service clearances up to a maximum of 30 inches (760 mm) as measured from the machine.
47.3.3 The floor loading capability should carry 80 to 125 pounds per square foot live load rating.
47.3.4 The Data center must have Standby Generator System and Transfer Switches
47.3.5 The Data center must have UPS in the configuration of N+1
47.3.6 The Data center should operate as a "sealed envelope," structurally and thermally, and should be separated from adjacent areas to allow for air conditioning, fire protection, and security. If the computer room must extend to the outside walls, eliminate the use of glass, even if it is bullet-proof glass or shield the space from view.
47.3.7 The floor-to-ceiling height must be sufficient to allow machine top covers to open for service and should be adequate to allow air circulation from the data processing machine. When planning a new data center, the recommended heights are 8.5 ft to 9.5 ft (2.6 m to 2.9 m) from the building floor or from the raised floor to the suspended ceiling, but higher ceilings are acceptable. (We may accept the minimum of 8 ft in special cases). If there is an exterior roof above the data center, it should have the space and load-bearing capability for large heat rejection equipment.
47.3.8 It shall be ensured that all not only the floors are furnished with anti-static material but also the furniture are Electrostatic discharge (ESD)-resistant.
47.3.9 The Data Center must support Data Center Disability Access Requirements. As per the internationally accepted best practices, the accessibility of the data center for the disabled person is a must. Special consideration shall be taken pertaining to ramps:
· An incline (1 inch rise per foot)
· A non-skid surface
· A run-out area (5 feet by 5 feet)
· Handicapped aids (handrails)
47.3.10 A raised floor system provides space for equipment cables and also serves as a supply air plenum for computer room air conditioning. Strong and reliable pedestals shall be used to support the floor panels. Pedestals must be firmly attached with adhesive to the structural floor. Caster point loads on some machines can be as high as 1,000 psi (455 kg). Therefore, the panels should be rated to handle 1,000 psi (455 kg) concentrated load anywhere on the panel with a 0.080 inch (2 mm) maximum deflection.
47.3.11 The data processing equipment can tolerate a considerable range of temperature and humidity, as prescribed in the equipment manufacturer's product specifications manual for each type of equipment. Generally, a data center air conditioning system should be designed for 72o F (22o C) and 45% relative humidity at altitudes up to 7,000 feet (2,150 m). The relative humidity of the air entering a piece of equipment should not be greater than 80%. Reference the equipment specifications for the individual requirements. This specification is an absolute maximum. Air temperature in a duct or an under floor air supply should be kept above the room dew point temperature to prevent condensation within or on the equipment.
47.3.12 Air conditioning monitoring instruments that respond to a plus or minus 2o F (plus or minus 1o C) temperature and plus or minus 5% relative humidity should be installed in data centers as monitoring devices. With choice, temperature and humidity recording instruments should be installed in a data center to provide a continuous record of the environmental conditions. Direct-reading instruments with a 7-day chart are also suggested in order to monitor the ambient room conditions. Any under-floor air conditioning supply should also be monitored.
47.3.13 Typical computer equipment operating environment range is shown in the following table.
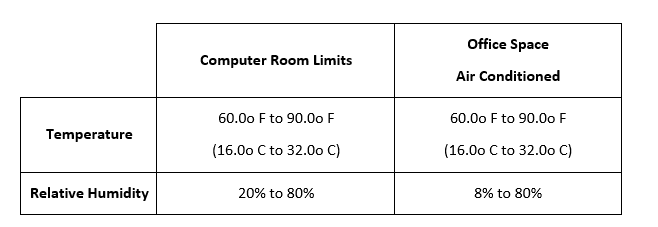
Under no condition of operation can the equipment input air and room air exceed 90.0o F (32o C). The relative humidity of the air entering a machine should never be greater than 80%.
The following table shows an example of the typical design criteria used in designing and preparing a data center.
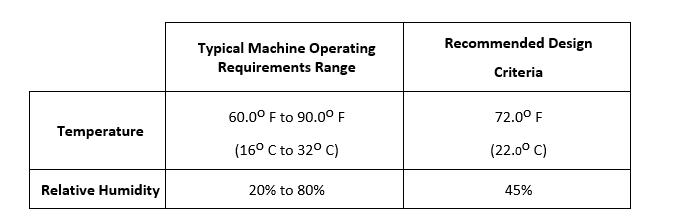
47.3.14 The air entering the machine must be at the conditions specified for machine operation before the power is turned on. Remember, that under no condition of operation May the machine input air and room air exceed the upper limit of machine operating conditions. This is the maximum operating temperature limit and should not be considered a design condition. When it is necessary to add moisture to the system for the control of low relative humidity, one of the following methods is most often used as an integral part of the CRAC unit:
· Spray system
· Quartz/ionization system (infrared)
· Water system
· Steam system
47.3.15 The Organization shall prefer FM 200 for Data Center. The FM-200® gaseous system uses a regulated greenhouse gas, under the Ozone Depleting Substances & Synthetic Greenhouse Gases (ODS & SGG) Management Regulations 1995. This gaseous system works in seconds and is readily suited to the protection of high value assets. The FM-200® provides total flood when used in; computer and electronic control rooms, telecommunication and switch rooms, data processing centers, vaults/tape storage, marine machinery spaces, chemical storage and clean rooms, medical laboratories and emergency power facilities. It uses a regulated greenhouse gas that are liquefied under pressure for storage These agents are classified as suitable for use in occupied areas and are considered to have no ozone depleting potential (ODP). The use of Halon and CO2 shall be avoided at all cost. The availability of Inergen is made from carbon dioxide, argon and nitrogen and does not break down under combustion and has no products of decomposition.
47.4 Enforcement
A policy violation will be subject to disciplinary action, which may go so far as employment termination. For third party it may lead to contract termination.
47.5 Responsibilities
Department Heads, HR, Information Security Manager and CIO
48 Proxy Policy
48.1 Purpose
This policy focuses on Proxy servers, which may be useful in business environments to restrict websites, analyze Internet traffic or for caching purposes.
48.2 Scope
This policy applies to all Proxies within the organization.
48.3 Policy
48.3.1 The Information Security Manager shall set up a proxy server. A proxy server acts as an intermediary between a less trusted network and a more trusted network.
48.3.2 The Information Security Officer shall ensure that administrative control and caching services are secure and not misused.
48.3.3 The Group Policy shall be utilized for the effective proxy control. The guidelines to be referred by IT are as follows:
a. Click Start – All programs – Administrative Tools – Group Policy Management.
b. Create or Edit Group Policy Objects.
c. Expand User configuration – Policies – Windows Settings – Internet Explorer Maintenance – Connection.
d. In right Pane Proxy Settings.
48.3.4 It is preferred to put a proxy server logically just behind the firewall.
48.3.5 46.5 Disallow the CONNECT command. Configure to only allow CONNECTs to specific ports as needed (e.g., a proxy server supporting SSL connections can allow connections to ports 443 and 563, with all other ports disabled for the CONNECT command)
48.3.6 46.5 The Proxy Server Log must be properly maintained and secured. The Log must be monitored on a regular interval. The abnormal behavior shall be investigated and rectified.
48.4 Enforcement
A policy violation will be subject to disciplinary action, which may go so far as employment termination. For third party it may lead to contract termination.
48.5 Responsibilities
Department Heads, HR, Information Security Manager and CIO.
49. Log Management, Security Incidents & SIEM Policy
49.1 Purpose
This policy has been developed to ensure that the Logs are managed and protected securely. The policy also discusses the Security Incidents and the role of Log Management in handling such incidents along with Security Information and Event Management (SEIM) if fully implemented.
49.2 Scope
This policy applies to all employees within the organization.
49.3 Policy
49.3.1 The Logs of the servers and other important machines shall be managed securely.
49.3.2 The clock synchronization must be performed for all equipment as it is a pre-requisite for proper Log Management.
49.3.3 The Log must be pulled from the device to ensure that even if the devices are compromised the Log can be fetched.
49.3.4 Event logs recording user activities, exceptions, faults and information security events shall be produced, kept and regularly reviewed.
49.3.5 Logging facilities and log information shall be protected against tampering and unauthorized access.
49.3.6 System administrator and system operator activities shall be logged and the logs protected and regularly reviewed.
49.3.7 The Security Incidents are like any other incidents which may be reported to the service desk as service desks are single point of contact with the end users.
49.3.8 The Service Desk must have an interface with an Information Security officer to forward the Security Related Incident.
49.3.9 The Log viewer must co-relate all of the logs and classify them on the basis of priority.
49.3.10 Management responsibilities and procedures shall be established to ensure a quick, effective and orderly response to information security incidents.
49.3.11 Information security events shall be reported through appropriate management channels as quickly as possible.
49.3.12 Employees and contractors using the organization’s information systems and services shall be required to note and report any observed or suspected information security weaknesses in systems or services.
49.3.13 Information security events shall be assessed and it shall be decided if they are to be classified as information security incidents.
49.3.14 Information security incidents shall be responded to in accordance with the documented procedures as automated in the service desk.
49.3.15 Knowledge gained from analyzing and resolving information security incidents shall be used to reduce the likelihood or impact of future incidents.
49.3.16 It shall be ensured that the automated process exist for the identification, collection, acquisition and preservation of information which can serve as evidence. It is highly recommended to go for security Information and Event Management Tool to automate the process.
49.4 Enforcement
A policy violation will be subject to disciplinary action, which may go so far as employment termination. For third party it may lead to contract termination.
49.5 Responsibilities
Department Heads, HR, Information Security Manager and CIO.
50 Additional Controls
50.1 Threat Intelligence
Purpose:
To ensure the organisation proactively identifies and mitigates potential threats through the use of threat intelligence.
Scope:
This policy applies to all departments and personnel involved in information security management.
Policy:
- The organisation shall implement a threat intelligence program to gather, analyse, and respond to information regarding threats that could impact the organisation.
- All relevant threat intelligence shall be shared with appropriate stakeholders to enhance preparedness and response efforts.
- Regular threat assessments shall be conducted, and the findings shall inform updates to security measures and protocols.
50.2 Information Security for the Use of Cloud Services
Purpose:
To secure the use of cloud services within the organisation by ensuring adequate information security measures are implemented.
Scope:
This policy applies to all departments utilising cloud services for data storage, processing, or management.
Policy:
- All cloud service providers must comply with the organisation’s information security standards.
- Data stored in the cloud must be encrypted both at rest and in transit.
- Access to cloud services shall be controlled and monitored to prevent unauthorised access.
- Regular security audits shall be conducted to assess the security posture of cloud services.
50.3 ICT Readiness for Business Continuity
Purpose:
To ensure the organisation's ICT systems are prepared to support business continuity in the event of disruptions.
Scope:
This policy covers all ICT systems critical to business operations.
Policy:
- The organisation shall maintain a Business Continuity Plan (BCP) that includes ICT readiness measures.
- Regular testing of ICT systems' resilience shall be conducted to ensure they can withstand and recover from disruptions.
- Backup systems and data recovery solutions shall be in place to minimise downtime during incidents.
50.4 Physical Security Monitoring
Purpose:
To enhance the security of physical premises through monitoring systems.
Scope:
This policy applies to all organisational facilities where sensitive information is handled or stored.
Policy:
- Surveillance systems, including CCTV cameras, shall be installed at key entry and exit points and areas with sensitive information.
- Access logs and surveillance footage shall be regularly reviewed to detect and respond to unauthorised access.
- Physical access controls shall be integrated with the monitoring systems to track and manage personnel movements.
50.5 Data Masking
Purpose:
To protect sensitive information by applying data masking techniques.
Scope:
This policy applies to all data processing activities involving sensitive information.
Policy:
- Data masking techniques shall be applied to protect sensitive information in non-production environments such as development and testing.
- Only authorised personnel shall have access to de-identified or masked data.
- Regular audits shall be conducted to ensure data masking controls are effective and compliant with data protection regulations.
50.6 Data Leakage Prevention
Purpose:
To prevent unauthorised disclosure of sensitive information.
Scope:
This policy applies to all systems, networks, and personnel handling sensitive data.
Policy:
- Data Leakage Prevention (DLP) tools shall be implemented to monitor and control the movement of sensitive information.
- Policies and procedures shall be established to identify, block, and report unauthorised data transfers.
- Regular training and awareness programs shall be conducted to educate employees on the importance of data protection.
50.7 Monitoring Activities
Purpose:
To ensure continuous monitoring of information systems to detect and respond to security incidents.
Scope:
This policy covers all information systems within the organisation.
Policy:
- A Security Information and Event Management (SIEM) system shall be implemented to collect, analyse, and report on security events.
- Continuous monitoring shall be conducted to identify suspicious activities and potential security breaches.
- Incident response procedures shall be established and tested regularly to ensure swift action during security incidents.
50.8 Web Filtering
Purpose:
To control access to web content to reduce the risk of exposure to malicious sites.
Scope:
This policy applies to all employees using the organisation's network and internet resources.
Policy:
- Web filtering solutions shall be implemented to block access to malicious and non-business-related websites.
- Policies shall be established to categorise websites and define access restrictions based on job roles and responsibilities.
- Regular reviews of web filtering rules and categories shall be conducted to ensure they are up-to-date and effective.
50.9 Secure Coding
Purpose:
To promote the development of secure software applications.
Scope:
This policy applies to all software development activities, whether in-house or outsourced.
Policy:
- Secure coding practices shall be integrated into the software development lifecycle.
- Developers shall receive regular training on secure coding standards and practices.
- Code reviews and security testing shall be conducted to identify and remediate vulnerabilities before deployment.
1. Introduction
This document defines how the ISO 27001 Implementation Project will be managed and implemented within the organization. This document is comprehensive to cover the requirement of ISO 27001. The procedures presented here are mainly based on the best practices as required by the standard.
The main focus of this document is to ensure that all best practices are compiled at a single place and they are accessible as and when required by the authorized users. This document is a live document it should be regularly updated as and when required.
Any modification to ISO 27001 Information Security Management System document shall be under change management process, where RFC shall be raised against any changed request.
2. ISO 27001 Implementation Project
2.1 Scope of Certification
"Provision of Information Security Management System for the management & operations Of Information Technology department of Norconsult Telematics, Riyadh Saudi Arabia"
This document covers the services offered by the organization as mentioned in the scope of certification. The main objective is to ensure that proper controls are applied to the critical assets of the organization, and the risk exposure is within the risk appetite as approved by the Senior Management
2.2 Scope of Standard Implementation
The scope of Implementation covers the complete Management and operation considering the Internal and External factors, all the relevant stakeholders including the customer, the senior management, suppliers, staff members, the environment and others. The scope of the standard although limited to IT, but it should act as a Centre of excellence for the best practices and a role model for the rest of the departments and groups.
These objectives will be documented and record should be maintained. The strategic plan shall be reviewed and updated to keep it in line with the objectives. Any change in the objective shall be approved by the Senior Management.
Following are the major components of ISO 27001 Implementation Project:
2.3 Management Commitment
The Senior Management shall ensure that a systematic review of performance of the program me is conducted on a regular basis. The Senior Management shall provide resources, time and supervision for the Information Security Management System. They will be involved in the management review process and shall ensure that the recommendations for ISMS improvement are implemented, and they are effective. The Management Review shall be performed at least once a year.
2.4 Management Representative
Management Representative shall have overall authority and responsibility for the implementation and management of the ISO 27001, specifically:
· Overall success of the implementation.
· Managing and coordinating the activities of the process owners.
· Integration of processes.
· Implementation and improvement of Management System.
· Compliance with the relevant requirements.
· Ensuring the Internal Audits is performed on regular intervals and Management Reviews are conducted.
2.5 Governance of Processes Operated by Other Parties
The third party and external suppliers shall be managed through the Vendor Management process. All the vendors and third party must have signed a contract (Underpinning Contract), which shall be reviewed on regular basis. It must be clear that the work may be outsourced to the third party or the vendor but the governance and the accountability still lies with the organization, which include demonstrating the process effectiveness, handling of exceptions, compliance and continual service improvements.
2.6 ISMS Policy
The information security is of prime importance. The information is the most critical of all Information Asset. The Information Asset of the organization must be protected within the legal and regulatory framework. The Senior Management is committed to provide sufficient resources for the Information Security as and when required.
2.7 ISMS Focus
· To develop internal control and to stop unauthorized and unauthenticated access to data, thereby ensuring the appropriate protection of critical assets.
· To protect the confidentiality and integrity of information assets
· To make sure that information is not revealed to unauthorized third parties during the process of transmission or as a result of unintentional actions.
· To ensure that all information security incident or exceptional events have appropriate reporting mechanisms.
· To continuously improve and strengthen the capabilities of the information security management system.
· To enhance professional knowledge and skills in terms of information security management and technology
· To ensure management system for information security is comprehensive and reliable.
· To make sure that critical business operations continue to be carried out in line with the ISO/IEC 27001 standard and to establish a sustainable environment for business that is effective and efficient.
· To establish SMART security goals annually through management and review meetings
2.8 ISMS Objectives and Targets
The objective of ISMS is to ensure following:
· Achieve the security of the organization ensuring zero-incident in a year.
· Perform Internal Audit at least once in a year.
· Perform Management Review at least once in a year.
· Ensure Risk Assessment is performed on yearly basis.
· Ensure Risk Treatment is followed by Risk Assessment.
· Conduct External Audit on yearly basis.
2.9 Information Security Projects and the Programs
Norconsult follows the PMI methodology where program is a collection of related-projects. As per Norconsult, the Information Security Program consists of following:
· Risk Assessment and Treatment
· Awareness
· Review by external entities
3. Documented Information Control (Documents plus Records)
The ISO 27001 Implementation Project adopted requires that all documents and records that make up the Management System (MS) must be controlled. Following are the principles for Management System:
· Must address all the “Shall” Clauses of the relevant standard.
· Should be readily identifiable and available.
· Must be dated, and authorized.
· Must maintain a version control.
· Life cycle, decommissioning and archiving methods must be clearly stated.
3.1 Creation of the Documented Information
The documents are created as per the requirements. All documents have version 0.x when they are in a draft format. The final version gets the version 1.x, and the numbers are step-up in the subsequent documents.
3.2 Documented Information Naming Convention
A standard naming convention is adopted for the Management System documentation. This will provide consistency of approach and version control.
· Naming Convention: ‘NT-ISMS-9999 Version Number’
Explanation:
· NT - ISMS 1000 Series: for ISO 27001 Implementation Project and Supporting Documents.
· NT - ISMS 2000 Series: for Information Technology Service Management
· NT - ISMS 3000 Series: for Business Continuity Documents
· NT - ISMS 4000 Series: is for Reference
· NT - ISMS 8000 Series: for Checklist
· NT - ISMS - 10000 Series: for Forms which may not be directly related to ISO 27001 Project.
Note: If any of the numbers is followed by “-R” it means that it is a record.
Although the above convention covers both “DOCUMENTS” and “RECORDS”; it is not mandatory format for records and logs as these will often be determined by other systems and software. It is highly recommended that the name of a log or record should be self-explanatory and meaningful.
Following are the documents in our Document Control:
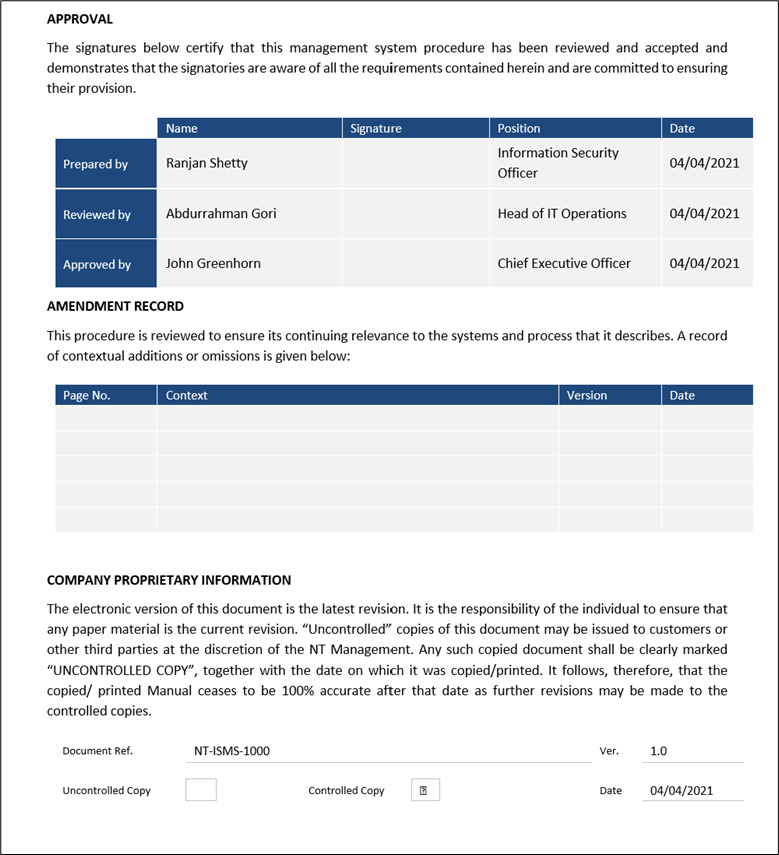
3.3 Maintenance of Documents
The final version of all documents must be stored electronically. Any change in the document must be under Change Control. A hard copy of document may also be maintained.
3.4 Disposal of Documents
All old versions of the printed documents must be securely shredded. The main shared folder must have only the final version of the documents. The old version must be moved to the archive folder.
3.5 Documents of External Origin
The documents that originate from the third party or outside source, and they become part of Management System must have a title page added which must comply with the organization documentation standard. If this is not possible, they should remain in the “Resource Folder” of the Management System.
4.Internal Audit
The objective of Internal Audit is to provide independent evaluation and assessments of the organization’s activities, operations, services and internal controls as per the best practices of the international standards. This will help to promote the integrity, effectiveness, efficiency, and compliance in all relevant operations. It will also help the management in their Management Review process.
· IT Internal Audit seeks will contribute in following areas.
· Ensure the proper implementation is in place.
· Validate that adequate safeguards exist over Assets.
· Verify continuous quality improvement process is in place.1
· Check for operational effectiveness and efficiency.
· Confirm adherence to the publish policies and procedures.
· Investigate non-compliance.
· The Internal Audit accomplishes its objective by carrying out an annual audit plan that utilizes the “Shall” clauses of the relevant standard.
4.1 Internal Audit Approach
Internal Audit will adopt the approach which is in appliance with the relevant standard. The internal staffs are trained to conduct Internal Audit and to report major non-compliance, minor non-compliance and observations in a predefined management approved template.
In this Internal Audit approach special emphasis will be given to risk. "Risk refers to the uncertainty that surrounds future events and outcomes. It is the expression of the likelihood and impact of an event with the potential to influence the achievement of an organization's objectives." In other words, risk is something that may impede the organization in achieving its objectives.
4.2 Internal Audit Strategy
Internal Audit is an independent function part of Plan-Do-Check-Act (PDCA) cycle. Internal Audit follows the mature approach and it renders impartial & unbiased feedback. Internal Auditors are independent of the activities they audit, this independence is essential to the effectiveness of the Internal Audit process.
The responsibility of Internal Audits is to serve the organization in a manner which is consistent with the best practices of the international standards. At a minimum it shall comply with the minimum requirement as specified in the standard.
The Audit should provide outstanding, cost effective, comprehensive coverage with the utmost professionalism and objectivity. .
The Internal Auditors are authorized to have full, free and unrestricted access to information including records, computer files, systems and services. The Auditors are also authorized to review and evaluate all policies, procedures, documents & records which are within the scope of Audit. To ensure the appropriate level of independence and objectivity, the IT Internal Auditors cannot Audit their own work.
4.3 Internal Audit Scope and Criteria
The scope of Internal Audit shall be comprehensive to enable the effective and efficient review of all operational and related activities within the scope. As most of the IT environment is centralized, so major focus would be at the main Data Center. However, the operations of the remote places may be covered, if the respective relevant equipment is at the main site.
The extent and frequency of Internal Audits will depend upon varying circumstances such as results of previous audits, relative risk associated with activities, materiality, the adequacy of the system of internal control, and resources available. Initially in the first year there will be four Internal Audits i.e. one in each quarter.
The audit criteria are to look for objective evidence against “shall” Clauses. It is required that all “shall” clauses are either met or there is a clearly defined road map for their implementation. The audit will focus on the critical components, which are vital for the smooth of operation.
4.4 Benefit of Internal Audit
The Internal Audit with help of the organization in following ways:
1. Ensure compliance with all “shall” clauses of the standard.
2. Review of the Strategy.
3. Review of the management system.
4. To access the management commitment.
5. Analyze the effectiveness of implementation.
6. Facilitate continual service improvement.
4.5 Internal Audit’s Objectives
The Internal Audit is conducted to assist the management to achieve sound managerial control over all aspects of the operations of the services as per standard. The overall objective of the exercise of Internal Audit is to assist management in the effective control by providing independent analysis, appraisals, advice and recommendations concerning the activities reviewed.
The attainment of the overall objective may involve following:
1. Ensure that the Risk Management exists in the organization.
2. Review the processes against the selected standard.
3. Review and appraise the adequacy and effectiveness of the system.
4. Check the relevance, reliability and integrity of the management system.
5. Assess compliance against the standards and best practices.
6. Review the means of safeguarding assets.
7. Appraise the economy, efficiency and effectiveness with which resources are employed.
8. Review operations to ascertain whether results are consistent with established objectives and goals and whether the operations are being carried out as planned.
9. Assess the adequacy of established systems and procedures.
10. Ensure the legislation and regulation, where applicable.
4.6 Internal Audit Process
The Internal Audit will be based on the following steps:
1. Develop the audit plan and coordinate the audit activity with the respective auditee.
2. Conduct the audit.
3. Analyze the audit result. Identify the corrective and preventive measures.
4. Compile the Report and present the report to the management.
5. Audit Procedure
The Internal Audit Procedure would be as follows:
Develop the Audit Plan and Coordinate with Auditee
The internal Audit shall be planned as per the scope of the standard. The audit schedule would be communicated to the auditee well in advance.
5.1 Conduct Audit
The auditor shall conduct the audit as per the audit plan following the regular standard. The auditor shall ensure that unvoiced and objective approach is followed throughout the audit. It should be noted that the audit is on “Sampling” basses and it is not “Population”. It is resumed that the sample is a true representative of the population, else there will be a risk of sampling error. The nonconformities shall be identified against the standard.
5.2 Analyze the Audit Result
The auditor shall objectively analyze the audit result. In case of any non-compliance the auditor shall ask the auditee about the corrective and preventive measures adopted. The auditor shall further analyze the effectiveness of all such measures.
5.3 Compilation of Audit Report
The Internal Audit report shall be compile summarizing all Non-Compliance Reports (NCRs), and observations. Nonconformities shall be communicated, prioritized and responsibility allocated for actions. The management responsible for the area being audited shall ensure that any corrections and corrective actions are taken without undue delay to eliminate nonconformities and their causes. Follow up activities shall include the verification of the actions taken and the reporting of results.
The result of the Internal Audits and management reviews, including nonconformities, concerns and action identified shall be recorded. The result and action shall be communicated to interested parties. The audit report shall be presented for the management review.
6. Non-Conforming Products or Services Handling Procedure
1. Non-Conforming Products or Services can be discovered during internal audit, a received product from supplier or in other circumstances.
2. When a Non-Conforming Product or Service is discovered, the person discovering the nonconformance, shall fill in the NCR- Non-Compliance Report.
3. All NCRs shall be reviewed by the concern staff the related corrective and preventive action shall be taken.
4. Once the corrective and preventive actions are complete the NCR must be closed.
5. In the subsequent internal audit the last period NCRs shall be reviewed to ensure that proper actions are taken.
7. Nomination of Auditor and Auditees
It is the responsibility of Head of Information Security to ensure proper planning of the Internal Audit. He shall also ensure that the Audit is conducted in a professional manner and the report of Internal Audit is communicated to the relevant stakeholders. He shall also ensure that all Audit records are maintain and are available, when required. The first audit will be conducted by Mr. Javed Abbasi
Following is the Matrix for the nomination of the first Auditee.
7.1 Auditee Matrix Template
Note: All the above auditors are competent and fully trained on the relevant standard as well as on internal Audit methodology.
7.2 High Level Auditing Activity Plan
For the Year 2021 high level audit plans is being developed. This is to ensure that there is proper direction for the organization. The High-level audit plan is as under:
Note: The Above matrix is for the planned audit only. Internal Audit would be regularly conducting surprise and un-planned audits as well.
8. Management Review
The top management shall review the ISMS at on quarterly bases after each internal audit exercise. This is to ensure the continuing, suitability, adequacy and effectiveness of the management system. The management review shall include consideration of:
1) Status of action from previous management review.
2) Changes in external and internal issues.
3) Information on the performance including trends in following area:
a) Nonconformities and corrective actions.
b) Monitoring and measurement evaluation results.
c) Audit results.
4) Opportunities for continual improvement
Management review shall consider the performance of the organization, including:
· Follow-up actions from previous management reviews
· The need for changes to the Management system, including the policy and objectives.
· Opportunities for improvement.
· Results of audits and reviews including those of keys suppliers and partners.
· The techniques, products or procedures which could be used in the organization to improve the performance and effectiveness.
· Status of Corrective actions.
· Results of exercising and testing.
· Risks or issues not adequately addressed in any previous risk assessment.
· Any changes that could affect the Management System.
· Adequacy of policy
· Recommendations for improvement.
· Lessons learned and actions arising from disruptive incidents.
· Emerging good practice and guidance.
The outputs of the management review shall include decisions related to continual improvement opportunities and the possible need for changes to the Management system and include the following:
a) Variations to the scope of the Management System.
b) Improvement of the effectiveness of the ISMS.
c) Modification of procedures and controls to respond to internal or external events that may impact on the ISMS, including changes to:
1. Risk reduction and security requirements.
2. Operational conditions and processes.
3. Legal and regulatory requirements.
4. Contractual obligations.
5. Levels of risk and criteria for accepting risks.
6. Resource needs.
7. Funding and budget requirements.
d) How the effectiveness of controls is measured.
The organization shall retain documented information as evidence of the results of management reviews. The organization shall:
a) Communicate the results of management review to relevant interested parties.
b) Take appropriate action relating to those results.
9. Improvement
9.1 Nonconformity and Corrective Actions
When nonconformity occurs, the organization shall:
a) Identify the nonconformity.
b) React to the nonconformity as applicable:
1. Take action to control and correct.
2. Deal with the consequences.
c) Evaluate the need for action to eliminate the causes of the nonconformity in order that it does not recur or occur elsewhere, by:
1. Reviewing the nonconformity.
2. Determining the causes of the nonconformity.
3. Determining if similar nonconformities exist or could potentially occur.
4. Evaluating the need for corrective action to ensure that nonconformities do not recur or occur.
5. Determining and implementing corrective action needed
6. Reviewing the effectiveness of any corrective action taken.
7. Making changes to the ISMS, if necessary.
d) Implement any action needed.
Corrective actions shall be appropriate to the effects of the nonconformities encountered. The organization shall retain documented information as evidence of:
a) The nature of the nonconformities and any subsequent action taken.
b) The results of any corrective action.
10. Continual Improvement
The organization shall continually improve the suitability, adequacy or effectiveness of the ISMS.
Note: The organization can use the processes of the ISMS such as leadership, planning and performance evaluation, to achieve improvement.
10.1 Continual Service Improvement Policy
The continual service improvement is mandatory to ensure that proper measures are taken to move the organization to the net higher level. The continual service improvement ensured increase of pro-activity and productivity with regards to delivery of services. It also ensures that there is proper understanding among the departments as what kind of improvements are really feasible. The continual service improvement helps to access if the organization is really meeting its objectives.
The main source of services improvement is the internal audit and the feedback from the stakeholders. Once identified service improvement plan should be prepared. The service improvement plan need to be short, direct and must mention what exactly need to achieved.
10.2 Process
· Audit Plan: The Management Representative shall establish an internal Audit IA audit plan annually and audits will be scheduled on the basis of the status and importance of activities and the results of the previous audits. Each activity must be audited at least twice per year.
Unscheduled audits may be initiated by the Management Representative in order to verify the effectiveness of corrective or preventive action. Where there are organizational changes or changes to the ISMS the audit plan must be updated and re-approved accordingly.
· Audits: The Management Representative shall assign the carrying out of internal audits to internal auditors who are independent of the activity or of those having direct responsibility for the activity being audited.
· Follow-up Audits: After the agreed time for completion of corrective actions required has elapsed, the Management Representative will initiate a follow-up audit to verify the implementation and effectiveness of the corrective action taken. The results of the follow-up audit shall be recorded on the original Audit Discrepancy Report maintained by the Management Representative for reference or further action as required. Should the agreed corrective actions not be complete or not be effective, the Management Representative will discuss further corrective action as Necessary and / or agree a new time frame for completion with the auditee concerned and the above procedure will be followed.
· Management Review: The Management Representative shall summarize the findings of internal audits, including resulting corrective / preventive actions, for presentation during Management Review. Should the agreed corrective actions not be complete or not be effective, the Management Representative will discuss further corrective action as Necessary and / or agree a new time frame for completion with the auditee concerned and the above procedure will be followed.
· Responsibilities: The Management Representative and Internal Auditors are responsible for the application of this procedure.
11. Human Resource and Training Requirements
It shall be ensure that the nominated staff members are fully qualified, trained and experienced. It is observed that the nominated staff have relevant domain knowledge, however they do lack training and education for the ISO certification initiative. Therefore, they are trained in the respective areas during the implementation of this project.
In future all such training must continue to ensure that proper skills set are maintained at all times. All training records shall be maintained and updated.
12. ISO 27001:2022 Alignment
This document has been updated to align with the latest ISO 27001:2022 standards. Key areas of alignment include:
1. Enhanced risk management framework to identify, assess, and manage information security risks across the organisation. This includes a systematic approach to risk treatment and continuous monitoring.
2. Strengthening the role of top management in supporting and promoting the information security culture, ensuring the integration of ISMS requirements into the organization's processes.
3. Adoption of a comprehensive incident response and management process to ensure quick identification, reporting, and mitigation of security incidents.
4. Implementation of data protection measures to comply with legal, regulatory, and contractual obligations, ensuring the confidentiality, integrity, and availability of information.
5. Regular internal and external audits to verify compliance with ISMS policies and procedures, with a focus on continual improvement based on audit findings.
6. Ensuring that all staff receive adequate training and awareness on information security practices, roles, and responsibilities to foster a culture of security within the organization.
7. Continuous improvement of the ISMS through regular review, monitoring, and adaptation to changes in the threat landscape and business environment.
13. Appendix to Supplier Agreement
It is expected that supplier shall ensure following:
Information Security Related Requirements
a) Supplier shall ensure whenever they are accessing the organization asset the aspects or the confidentiality, Integrity and Availability are addressed.
b) All staff of assigned or outsourced must be qualified, trained and experienced. They must have also common understanding of Information Technology best practices. They must be ITIL Foundation and ISO 27001 Foundation certified to have a common understanding of the best practices. If anyone is deployed in application area, they must be at least TOGAF Foundation Certified.
c) Supplier must have NDA for all staff deployed to our premises.
d) If supplier or their staff comes across any the risk it should be reported to us immediately.
e) Organization resources must be used for the business purpose and no misuse of the resources in any way must be allowed.
f) Supplier shall ensure the continuity of the operations and must have tested business continuity plan.
ITSM Related Requirements
g) Maintain an updated document which clearly define the scope of the services with clearly defined Dependencies between services, processes and mentioning if anything is outsourced or subcontracted parties.
h) Roles and Responsibility Matrix with mapping of Requirements to be fulfilled by the supplier staff.
i) Service targets and Workload characteristics.
j) Clearly defined interfaces between service management processes operated by the supplier and other parties.
k) Contract exceptions and how these will be handled.
l) Supplier should submit the report on monthly basis against the SLA, Service Targets and workload characterizes.
m) Activities and responsibilities for the expected or early termination of the contract and the transfer of services to a different party.
n) Service provider shall also submit the report of the subcontractor, if applicable.
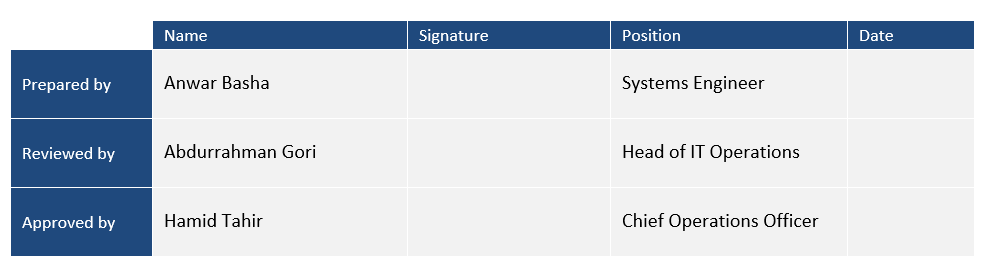
1.Data Masking
This control requires NT to mask data based on NT’s topic-specific policy on access control and other related topic-specific policies, and business requirements, taking laws and regulations into consideration.
2. Purpose
The purpose of this control is to limit the exposure of sensitive data including PII, and NT to comply with legal, statutory, regulatory and contractual requirements.
3. Scope
This control is applicable to only to data that is identified as PII or sensitive or specified in business requirements or contractual obligations as sensitive and require data masking.
4. Objectives
Sensitive information should not be available without topic specific policy for access control and data masking and presenting only the data that is required to perform task at hand.
5. Classification as Sensitive
Data that needs to be masked must be identified and classified as sensitive as per the below guidelines.
(1) Data that could be deemed personally Identifiable Information (PII).
(2) Privacy Sensitive Data.
(3) Financial Data or Intellectual Property.
(4) Data mentioned as Sensitive in the Contracts.
(5) Any data that Management classifies as Sensitive.
6. Types of Data Masking Methods
Data masking is a crucial aspect of data security, especially when handling sensitive information. Where the protection of sensitive data (e.g. PlI) is a concern, NT should consider hiding such data by using techniques such as data masking, pseudonymization or anonymization.
The following are the Data Masking Techniques that can be used by NT depending on requirements and will be decided by Head of IT Dept.
1. Tokenization: Tokenization is a method that replaces sensitive data with tokens, which are randomly generated and have no meaning. The original data is stored securely in a separate location, while the tokens are used for processing and storage, reducing the risk of data breaches.
2. Encryption: Encryption is a widely used data masking method that converts sensitive information into an unreadable format using algorithms. Only authorized users with the decryption key can access the original data, ensuring confidentiality and data security.
3. Masking: Masking involves obscuring parts of sensitive data with characters such as asterisks or X's. This method is commonly used in scenarios where the full data is not required for processing, reducing the risk of unauthorized access.
4. Shuffling: Shuffling is a data masking method that involves rearranging the order of characters within a data set. This technique helps protect sensitive data while maintaining its integrity and usability for processing purposes.
5. Redaction: Redaction is a process of permanently removing sensitive information from documents or files. This method is commonly used to ensure compliance with privacy regulations and avoid unauthorized access to confidential data.
6. Noise addition: Noise addition is a technique that introduces random data to the original information, making it harder for attackers to decipher the sensitive data. This method helps enhance data security and protect against unauthorized access.
7. Anonymisation: This technique fundamentally and irreversibly alters data in a way that it can no longer be directly or indirectly identified.
8. Pseudonymisation: This technique uses an alias in place of data. It replaces data with an alias. If you know the algorithm used to create the alias it is possible to recreate the data. When this technique is used, every effort is taken to protect the algorithm.
7 Considerations for implementing Data Masking Methods
The following points should be considered when implementing data masking techniques:
a) Not granting all users access to all data, therefore designing queries and masks in order to show only the minimum required data to the user.
b) There are cases where some data should not be visible to the user for some records out of a set of data; in this case, designing and implementing a mechanism for obfuscation.
c) Any legal or regulatory requirements (e.g. requiring the masking of pricing / payment information during processing or storage).
d) Level of strength of data masking, pseudonymization or anonymization according to the usage of the processed data.
e) Access controls to the processed data.
f) Agreements or restrictions on usage of the processed data.
g) When using pseudonymization or anonymization techniques, it should be verified that data has been adequately pseudonymized or anonymized. Data anonymization should consider all the elements of the sensitive information to be effective.
h) If needed third party commercial software to be procured for this purpose.
8. Process Compliance
The Head of IT Dept. or his delegated team will verify compliance to this process through approved Data masking methods. Detailed Data Masking action taken reports and logs will be maintained and updated with feedback to the Head of IT Dept. Having masked or generated test data helps NT to comply with privacy regulations like GDPR.
8.1 Exceptions
Any Exception to the process must be approved and recorded by the Information Security Manager in advance and reported to the Management Review Team.
8.2 Non-Compliance
An Employee found to have violated this process may be subject to disciplinary action, up to and including termination of employment.9. Exit
The effectiveness results are recorded, analysed and appropriate action taken for further improvement.
Data Masking action taken report prepared and shared with Head of IT Dept.
11. Review and Update
The Data Masking techniques and pprocedure shall be reviewed annually or when significant changes occur in the organization’s environment, technology, or regulatory requirements or when serious breach occurs or a security/sensitive/regulatory incident occurs.
Updates to the procedure shall be approved by the Information Security Officer and senior management.
12. Other Documents for Reference
(1) Section 5, Information safeguarding Policy
(2) Section 39, Data Life Cycle and Retention Policy in ISMS policy manual.
(3) Data Masking Action Taken Report
13 Data Masking Action Taken Report
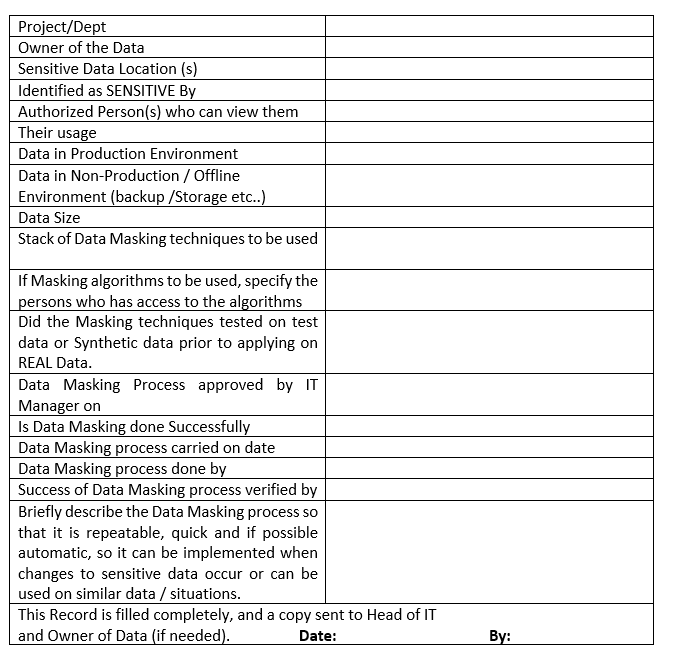

1.Data Leakage Prevention
This control requires NT to apply preventive measures to systems, networks and any other devices that process, store or transmit sensitive information.
2. Purpose
The purpose of this control is to prevent and detect the unauthorised disclosure and extraction of information by individuals or systems.
3. Scope
This control is applicable to data stored or processed in Systems, Devices, Networks that is identified or classified as sensitive.
4.Objectives
NT to implement a solution/tool based on its own set of circumstances. Most likely a DLP solution or Endpoint Protector tool to be used based on risk, classification and business need.
5. Implementation Considerations
To prevent or reduce data leakage considering the risks exclusive to operations, NT should:
(1) Organise /Identify /Classify data according to industry standards (PII, commercial/financial data, production/process data) to assign different levels of risk.
(2) Identify and Classify data as sensitive according to legal, regulatory and contractual requirements.
(3) Scrutinise diligently data outlets that are highly used and liable to leakage (i.e. emails, inward and outward file transfers, USB gadgets, cloud storage).
(4) Before any large-scale exports occur, require authorisation from the data holder.
(5) Encrypt any backups that have sensitive data. Ensure that all confidential info is safeguarded.
(6) Construct gateway security and leakage prevention measures to protect against external influences, including (but not restricted to) industrial espionage, sabotage, commercial interference and IP theft.
6.Data Leakage Prevention Tool
A Data Leakage Prevention Tool (DLP) is a specific tool that has been designed to track, detect and protect information based on rules using technology.
These tools can often be applied to structured and unstructured data. They can detect and / or prevent the disclosure of sensitive data, for example sending information to, or from, personal and cloud emails, and sending information to cloud storage devices. Data leakage prevention tools are intrinsically intrusive and should be employed and managed in accordance with any applicable regulations or legislation concerning user privacy.
At Present NT Doesn’t have DLP tool but is considering implementation of DLP solution in future.
NT will be implementing the traditional methods of data leakage prevention such as:
a) The locking down, or preventing the use of, attached media such as external hard drives and USB devices.
b) Restriction of Printing of sensitive/confidential documents.
c) Eencrypt data at rest or in transit where needed.
d) Conducting risk assessment.
e) Implement and communicate NT Topic specific policy on access control.
f) Evaluate all permissions.
g) Implement Robust Authentication like MFA.
h) Run effective and continuous security awareness training
i) Moving towards zero trust approach (Never Trust-Always verify)
j) Monitor Network Access
k) Secure Endpoints
l) Check the above controls working by conducting regular internal audits.
6. Process Compliance
The Head of IT Dept. or his delegated team will work on Evaluating and finding suitable Data Leakage Prevention tool. Meanwhile traditional methods at endpoints shall be enforced to prevent Data Leakage.
6.1 Exceptions
Any Exception to the process must be approved and recorded by the Information Security Manager in advance and reported to the Management Review Team.
6.2 Non-Compliance
An Employee found to have violated the restrictions or bypassed the process may be subject to disciplinary action, up to and including termination of employment.

1. Monitoring Activities
This control provides processes and tools to make sure that NT IT Dept. have enforced monitoring of Networks, systems and applications for anomalous behaviour and appropriate actions taken to evaluate potential information security incidents.
2. Purpose
To detect anomalous behaviour and potential information security incidents.
3. Scope
Applies to NT’s on-prem Production servers (Active Directory (AD) DC servers), Cloud production environments, network firewall, and cloud solutions.
4. Objectives
Regular monitoring and measurement of processes, systems, and networks to ensure that they are functioning as intended. Identify any deviations or weaknesses in logs, event/activity monitors, performance monitors to take corrective actions to mitigate risks and improve the security posture.
5. Ownership
Monitoring Activities is solely administrative task that are carried out by system administrator and fall under network/systems management and maintenance protection. Therefore, the Head of IT, or an equivalent in the organisation, should have responsibility of Control 8.16 Monitoring Activities.
6.Implementation of Monitoring Activities
The monitoring scope and level should be determined in accordance with NT business and information security requirements and taking into consideration risk assessment, relevant laws and regulations. Monitoring records should be secured and maintained for 4 months.
6.1 Considerations for inclusion within the monitoring system
1. outbound and inbound network, system and application traffic.
2. access to systems, servers, networking equipment, monitoring system, critical applications, etc.
3. critical or admin level system and network configuration files.
4. logs from security tools [e.g. antivirus, IDS, intrusion prevention system (IPS), web filters, firewalls, data leakage prevention.
5. event logs relating to system and network activity.
6. use of the resources (e.g. CPU, hard disks, memory, bandwidth) and their performance.
6.2 Establishing Baseline
NT should establish a baseline of normal behaviour and monitor against this baseline for anomalies. When establishing a baseline, reviewing utilization, access times of systems and networks at normal and peak periods should be considered.
6.3 Anomalous Behavior to be Monitored
1. Sudden closure or termination of processes and applications
2. Network traffic that is recognized as emanating to and/or from problematic IP addresses and/or external domains
3. Well-known intrusion methods (e.g. DDoS)
4. Malicious system behaviour (e.g. key logging)
5. Network bottlenecks and high ping and/or latency times
6. Unauthorized or unexplainable access to and/or scanning of data, domains or applications
7. Any attempts to access business critical ICT resources (e.g. domain controllers, DNS servers, file servers and web portals)
7.Monitoring Tools
The use of monitoring tools is clearly recommended. NT IT Dept. will use some of these built into systems and operating systems like Event Viewer and Performance Monitor, Resource Monitor and Sophos Control Centre’s Diagnostics and Reporting tool.
NT shall consider off the shelf, dedicated Monitor/Alert solutions in future that need to be able to handle large volumes of information and include real time notifications. Alerts should be configured and implemented and set against pre-defined thresholds.
7.1 Monitoring security optimization
Effective Monitoring can be achieved by having following SW/Tools, NT shall consider.
1. The use of dedicated threat intelligence systems and intrusion detection systems.
2. The use of machine learning platforms.
3. IP management platforms and email security software support whitelists, blacklists, block lists, and allow lists.
4. The integration of logging and monitoring activities into a single end-to-end process.
5. Dedicated to the detection and prevention of well-known intrusion methods and malicious activity, such as the use of botnets or denial of service attacks.
8. Trained Staff
Staff will be trained to be able to use tools and interpret information and appropriately respond. This can include the management of false positives, which do happen.
9. Continuous Monitoring
The standard advocates for continuous monitoring, in real time or at periodic intervals.
10. Monitored Devices/Applications
10.1 Windows Servers
The following in-house production servers are monitored.
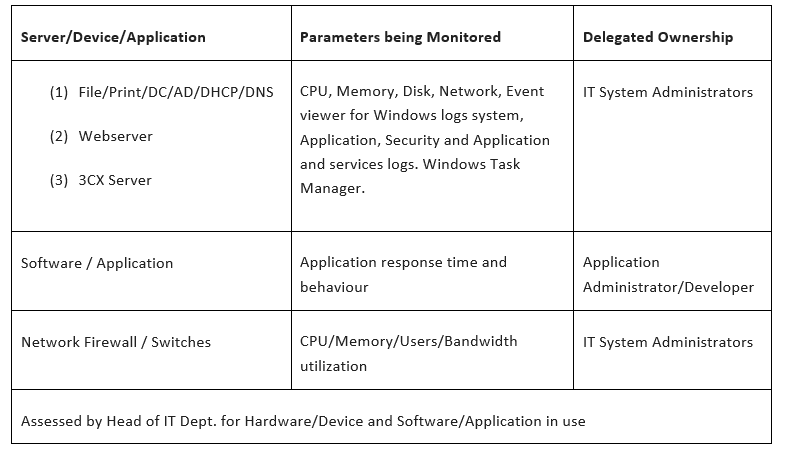
10.2 Cloud Infrastructure
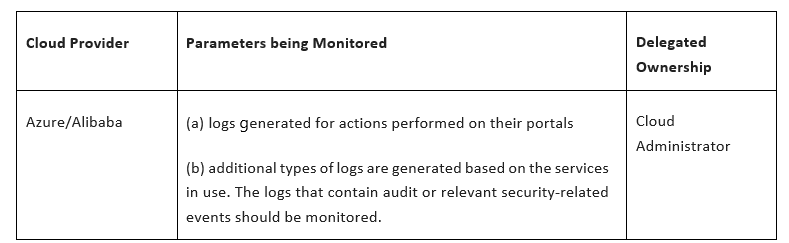
10.2 Office 365
Office 365 – Active Directory – Login Monitoring by IT System Administrators
Office 365 – Azure Active Directory – Login Failures by IT System Administrators
Office 365 – Azure Active Directory – Risky Logins by IT System Administrators
11. Baselines and Thresholds
11.1 Following for Windows AD/DC Server
If CPU usage consistently above 50% and Memory usage above 95% means it crossed baseline.
11.2 Following for Web Server
If CPU usage consistently above 90% and Memory usage above 90% means it crossed baseline.
11.3 Following for 3CX Server
If CPU usage consistently above 50% and Memory usage above 50% means it crossed baseline.
11.4 Network Firewall
The following Graphs show typical day afternoon usage, taken as baseline.
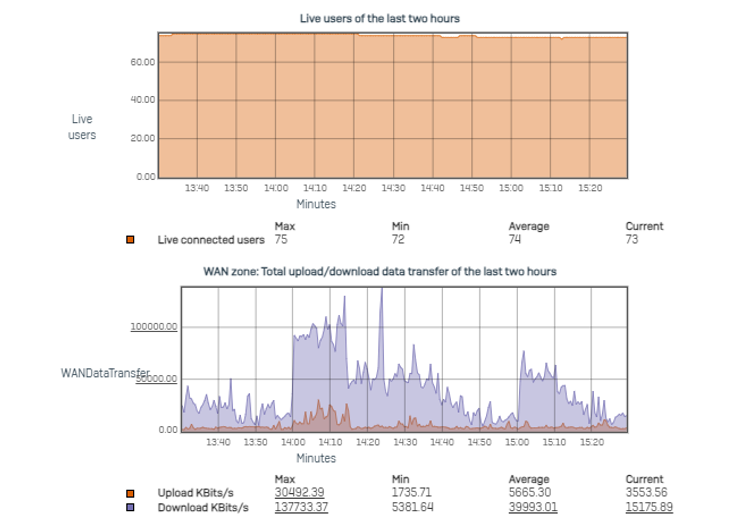
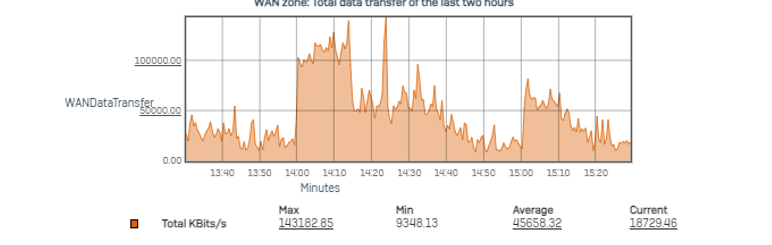
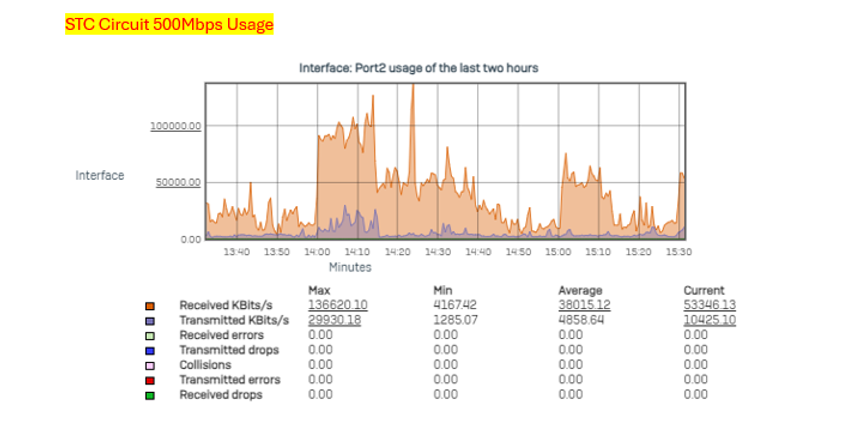
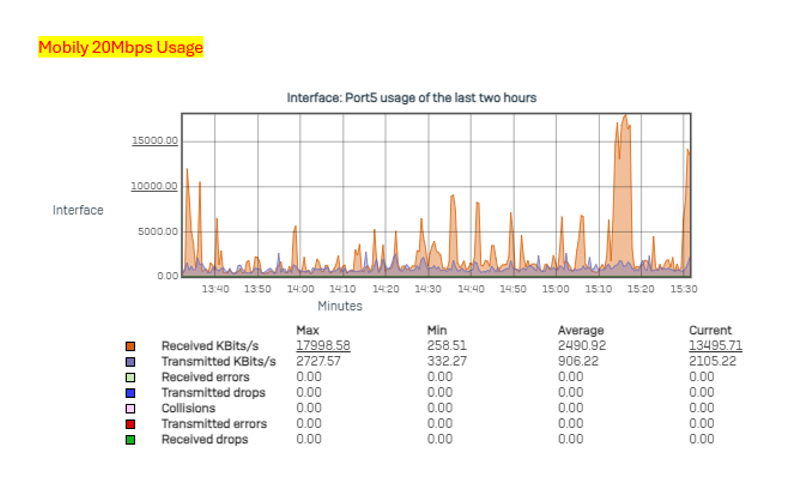
11.5 Firewall Usage Thresholds
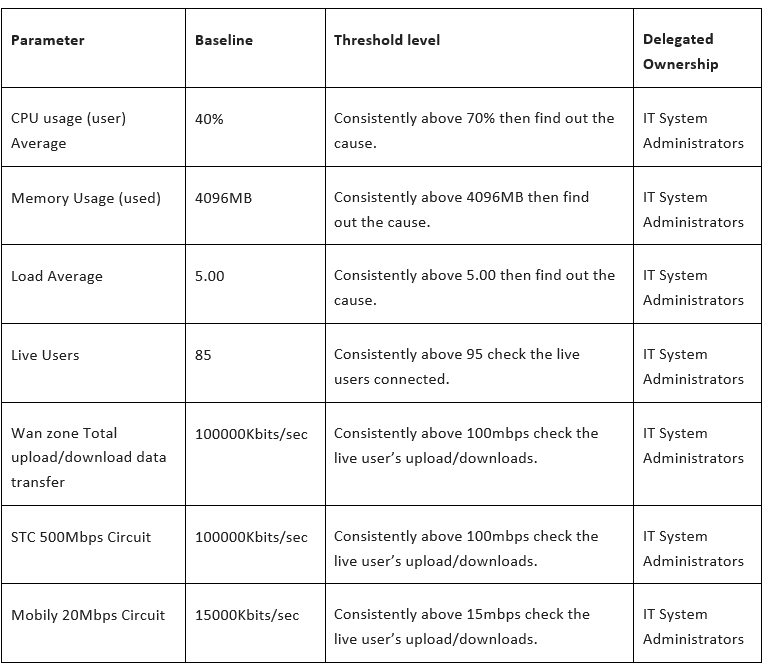
Existing baseline configurations must be reviewed at least annually to ensure they are still applicable.
12. Security Controls for Log Information
NT IT Dept. intends to implement the following for protection of the log information:
encrypting log information.
storing log information in a secure location.
maintaining tight controls over who has access to log information.
The purpose of this provision is to prevent unauthorized individuals from accessing or altering log information, which could be used to cover up malicious activity.
13.Process Compliance
The Delegated Owners shall monitor the above parameters regularly every 2-3 hours and any anomalies found to take the corrective active and inform the Head of IT Dept.
13.1 Exceptions
Any Exception to the process must be approved and recorded by the Head of the IT and reported to the Management Review Team.
13.2 Non-Compliance
An Employee/delegated Owner found to have violated this process may be subject to disciplinary action, up to and including termination of employment.
14. Output
The effectiveness, results are recorded, analysed and Monitoring Activities file updated and Version document with date for reference.
15. Review and Update
The Monitoring Activities of critical assets and production systems shall be reviewed annually or when significant changes occur in the organization’s environment, technology, or regulatory requirements or when major update needs to be implemented, or a security/Threat incident occurs.
16. Other Recommendations.
IT Dept shall study and give options for implementing SIEM (Security Information and Event Management) tool.
Centralized Repository of logs/Events with proper security controls and retention system shall be considered.

1.Segregation of Networks
This control requires NT IT Dept. to group information services, users, information systems and then put those groups on different networks.
2. Purpose
To split the network in security boundaries and to control traffic between them based on business needs.
3. Scope
Applies to NT on premises Wired + Wireless, Wan and VPN network.
4.Ownership
Segregation of Networks is solely administrative task that are carried out by system administrator and fall under network/systems management and maintenance protection. Therefore, the Head of IT, or an equivalent in the organisation, should have responsibility.
5. Implementation of Segregation of Networks
This can be achieved through several methods such as:
- VLANs (Virtual Local Area Networks): VLANs allows to create multiple virtual networks on a single physical network, allowing to separate different network segments.
- Firewalls: Firewalls can be used to segment a network by controlling access between different parts of the network.
- DMZ (Demilitarized Zone): A DMZ is a subnet that is used to isolate publicly accessible services, such as web servers, from the rest of the network.
- VPN (Virtual Private Network): VPNs allow remote users to access the internal network securely, while keeping the internal network separate from the public internet.
The segregation of networks can improve the overall security of a network by reducing the attack surface, and by making it more difficult for an attacker to move laterally through the network. Additionally, it provides more granular control over access to network resources, and it allows for the implementation of different security measures for different parts of the network.
6. Implementation Considerations for NT Network
1. Internal Network Resources are confined to LAN through Cisco Switches.
2. Publicly accessible resources are placed in Demilitarized Zone.
3. Wan links are connected in External network zone.
4. Wireless Network Users are connected only after authentication.
5. Guest wireless users have limited connectivity to only external/internet zone.
6. VPN users are securely authenticated using the secure VPN client and given access to the resources they have permission to access.
7. Firewall Implementation
NT has segregated the network based on its business needs and security concerns into the following by using Sophos XG 210 UTM at perimeter level.
1.Internal Network
2.DMZ
3.External/internet connection
4.Wan Link1
5.Wan Link2
6.VPN Zone
Internal network is further divided into LAN and Wireless. Wireless network has 2 different SSIDs.
NTSA Wi-Fi and NTSA_ Guest Wi-Fi. Both have different IP address ranges.
Anyone connected to NTSA Wi-Fi network requires password then needs authentication through Firewall and Microsoft Azure services. After successful authentication the user is allowed to use the resources, he has permissions to access.
For Users connecting through NTSA_Guest Wi-Fi, requires password to connect but has limited access to internet with bandwidth and application access control restrictions implemented.
Access control and traffic shaping and traffic filtering is implemented using firewall rules at different zones.
8. Connecting to NTSA Wi-Fi
Following picture shows the authentication screen.
9. Connection using Sophos VPN Client
Following Pictures show connection using Sophos VPN client
10. Monitoring of Firewall / Unified Threat Management Device Activity
The NT IT Dept. regularly monitors the firewall/UTM for any anomalies on perimeter /user level using Sophos Control center, as shown in below picture.
11. Proposed improvements
(1) Sophos XG 210 UTM is coming to EOL in March 2025 needs to be replaced with a new model. NT IT Dept. considering different options to meet current and future Security requirements and local compliance and regulations.
(2) NT actively considering implementation of VLANs if necessary.
(3) Actively Considering IDS/IPS system with alert and alarms.
12. Review and Update
The Segregation of Networks shall be reviewed annually or when significant changes occur in the organization’s environment, technology, or regulatory requirements or when major change needs to be implemented, or a security/Threat incident occurs.

1. Secure Coding
This control provides processes and tools to make sure that NT IT Dept. have applied secure coding principles for software development.
2. Purpose
To ensure software is written securely thereby reducing the number of potential information security vulnerabilities in the software.
3. Scope
Applies to NT’s in house developed software, procured from 3rd party developers, open-source software and SW products and services supplied by the organization to others/clients.
4. Objectives
Using techniques and methods to prevent security vulnerabilities from being introduced into the code during the development process. This can be achieved by following the standards, guidelines and best practices including testing and reviewing the code to identify and fix any security issues before deployment.
5. Ownership
Chief information security officer should be responsible for taking appropriate steps to ensure compliance with 8.28 Secure Coding, which requires developing and implementing secure coding principles and procedures throughout the organisation.
6. Implementation of Secure Coding
NT IT Dept. has established organization-wide processes to provide good governance for secure coding. The processes are given below and depend on NT business and information security requirements and taking into consideration risk assessment, relevant laws, regulations and intended deployment environment.
(1) Planning and before Coding.
(2) During Coding.
(3) Review and Maintenance.
6.1 Planning and before Coding
Secure coding principles should be used both for new developments and in reuse scenarios. These principles should be applied to development activities both within NT and for products and services supplied by NT to others.
Planning and prerequisites before coding should include:
1. NT specific expectations and approved principles for secure coding to be used for both in-house and outsourced code developments.
2. Common and historical coding practices and defects that lead to information security vulnerabilities.
3. Configuring development tools, such as integrated development environments (IDE), to help enforce the creation of secure code.
4. Following guidance issued by the providers of development tools and execution environments as applicable.
5. Maintenance and use of updated development tools (e.g. compilers).
6. Qualification of developers in writing secure code.
7. Secure design and architecture, including threat modelling.
8. Secure coding standards and where relevant mandating their use.
9. Use of controlled environments for development.
6.2 During Coding
IT Development Team should consider the following during coding:
1. Secure coding practices specific to the programming languages and techniques being used.
2. Using secure programming techniques, such as pair programming, refactoring, peer review, security iterations and test-driven development.
3. Using structured programming techniques.
4. Documenting code and removing programming defects, which can allow information security vulnerabilities to be exploited.
5. Prohibiting the use of insecure design techniques (e.g. the use of hard-coded passwords, unapproved code samples and unauthenticated web services).
Testing should be conducted during and after development. Static application security testing (SAST) processes can identify security vulnerabilities in software. Before software is made operational, the following should be evaluated:
1. Attack surface and the principle of least privilege.
2. Conducting an analysis of the most common programming errors and documenting that these have been mitigated.
6.3 Review and Maintenance
After code has been made operational:
1. Updates should be securely packaged and deployed.
2. Reported information security vulnerabilities should be handled.
3. Errors and suspected attacks should be logged and logs regularly reviewed to make adjustments to the code as necessary.
4. Source code should be protected against unauthorized access and tampering (e.g. by using configuration management tools, which typically provide features such as access control and version control).
5. Any updates, patches, fixes shall be documented and version control to be updated with approvals.
7. Secure Coding Checklist
IT Dept. Shall consider the following checklist while developing the applications or Coding.
1. Input Validation: For input validation, SW developers need to conduct data validation on the authenticated server, determine trusted and untrustworthy data sources, specify accurate character sets and encode data into common characters before validating. In case of input rejection, there must be a validation failure.
2. Authentication: Another important factor to maintain the security of the code is authentication. It is crucial to authenticate all the pages as well as resources and enforce the authentication system on a trusted system. After that, connection can easily establish and use standard authentication services. Another important thing to consider while authenticating is to segregate authentication logic from the resource that is being requested. If the app going to develop has a credential store to manage, it should ensure that the passwords are stored cryptographically to enhance security. Only use HTTP POST requests to transfer authentication credentials.
3. Password Management: When it comes to passwords, they should be concealed on the user's screen, and if someone is trying to access the account with the wrong credentials the account should be disabled for a certain time period to discourage brute force of password guessing. Temporary passwords should have a short expiration time and users must be verified in case of password reset. Highly recommended to use multi-factor authentication for highly sensitive or transactional accounts.
4. Access Control: While developing an app make sure to restrict access to protected URLs, functions, services, object references, application data, user and data attributes, and security configurations to authorized users only. Moreover, the app should deny all access if the security configuration information cannot be accessed.
5. Error Handling: Most software errors are caused by bugs, which can lead to vulnerabilities. Keeping a log of errors and handling them accordingly are two of the best ways to minimize their impact. Error handling attempts to prevent catastrophic failures by identifying errors in the code before they occur. Using error logging, developers can diagnose errors and mitigate their effects. To comply with secure coding standards, it is necessary to document and log all errors, exceptions, and failures.
6. Data Protection: To improve data protection, Development team should encrypt highly sensitive information on the server-side by using cryptographic hashes and protect server-side code from being downloaded by the user. Disabling the auto-complete feature on forms containing sensitive information can also help in enhancing security.
7. Communication Security: Implement encryption for sensitive data transmission by incorporating Transport Layer Security (TLS) certificates preferably Ver 1.2 and Ver 1.3
8. System Configuration: System configuration can be secured by using the latest versions of frameworks, servers, and other system components, or removing unnecessary files, functionalities, test codes, etc., from HTTP response headers. Provide access to only authorized development and test groups and isolate development environments from the production network. Development environments are seldom as secure as production environments, which enables attackers to identify shared vulnerabilities or exploit them. It is thus imperative to implement a software change control system to manage and track changes in both production and development environments.
9. Database Security: For database security, use strongly typed queries, use input and output validation and use secure credentials to access the database. Also change or remove the default passwords of the database with strong passwords or multi-factor authentication. Keep the passwords in encrypted file with secure access to authorised users.
8 Recommended Coding Practices
The following are the general coding practices that programmer/developer should follow:
• Always use tested and approved codes rather than unmanageable code.
• Do not allow the app to directly issue commands to the operating system using initiated command shells instead use task specified APls that conduct tasks related to the OS.
• To verify the integrity of libraries, interpreted codes, configuration files, and executables use hashes or checksums.
• Protect shared resources and variables from ill-suited intersecting access.
• Don't pass user-provided data to a dynamic function.
• Users should not be able to alter existing code or develop new ones.
• Review all third-party code, applications, and libraries to ensure safe functionality and business necessity.
• Use cryptographic signatures for code in case of automatic updates and determine signature verification by clients.
9. Exceptions
Any Exception to the process / recommendations must be approved and recorded by the Head of the IT and reported to the Management Review Team.
10. Non-Compliance
Any SW developer/programmer/Project team lead found to have violated this process may be subject to disciplinary action, up to and including termination of employment.
11. Output
The effectiveness, results are recorded, analysed and Secure Coding Activities file updated and Version document with date for reference.
12. Review and Update
The Secure Coding Process for development/test and production systems shall be reviewed annually or when significant changes occur in the organization’s environment, technology, or regulatory requirements or when major update needs to be implemented, or a security/Threat incident occurs, or a vulnerability found in deployed applications.
13. Other Recommendations.
Xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
SW development Team has to verify this document.
xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
1. Security Control Effectiveness Monitoring Procedure
The Security Effectiveness Monitoring Procedure is to ensure that the Information Security Controls are effective, and they are giving the desired results.
2. Purpose
The purpose of this document is to establish a procedure for monitoring the effectiveness of security controls implemented within the organization to ensure they are functioning as intended and to maintain compliance with ISO 27001:2022. This procedure aims to identify weaknesses or gaps in security controls, assess their performance, and provide recommendations for improvements.
3. Scope
This Procedure is applicable to all Security Controls as adapted for the scope of ISO 27001 Project.
This procedure applies to all information systems, processes, and assets covered by the organization's Information Security Management System (ISMS). It includes all departments, employees, contractors, and third-party service providers involved in the handling of sensitive information.
4. Incident Response Goals
• Verify that Security Controls are to giving desired results.
• Reduce the number of Security Incidents
• Prevent the reoccurrence of security related issues
• Improve the security posture
• Keep management informed of the situation.
5. Roles and Responsibilities
Head of Information Security
- Oversee the implementation and execution of the security control effectiveness monitoring procedure.
- Ensure that regular reviews and assessments of security controls are conducted.
- Report findings to senior management and recommend necessary improvements.
IT Security Team:
- Conduct regular monitoring and testing of security controls.
- Document findings and provide technical support for remediation efforts.
- Assist in developing and implementing corrective actions for identified weaknesses.
Department Managers:
- Ensure that their departments comply with the security control monitoring procedures.
- Cooperate with the IT Security Team during assessments and provide necessary information.
- Implement recommended corrective actions within their areas of responsibility.
Internal Audit Team:
- Conduct independent reviews and audits of security controls.
- Verify compliance with the Security Control Effectiveness Monitoring Procedure.
- Report findings to the Information Security Officer and senior management.
6. Entry: Monitoring and Evaluation Process
Planning and Scheduling:
- A security control monitoring schedule shall be established at the beginning of each fiscal year, covering all critical areas and systems.
- Ad-hoc reviews may be conducted in response to security incidents, changes in the threat landscape, or updates to compliance requirements.
Control Identification and Documentation:
- Identify and document all security controls implemented within the organization, including their purpose, configuration, and expected outcomes.
- Maintain an inventory of controls mapped to ISO 27001:2022 Annex A controls.
Monitoring and Testing Techniques:
- Continuous Monitoring: Implement automated tools to continuously monitor network traffic, system logs, and access controls for anomalies or unauthorized activities.
- Periodic Testing: Conduct scheduled tests such as vulnerability assessments, penetration testing, and control effectiveness evaluations.
- Manual Reviews: Perform manual checks and reviews of critical security controls, configurations, and policies.
Data Collection and Analysis:
- Collect data from various sources, including monitoring tools, system logs, and audit trails.
- Analyze data to identify trends, anomalies, or deviations from expected behavior.
- Evaluate the effectiveness of controls based on the analysis results.
Reporting and Documentation:
- Prepare a Security Control Effectiveness Report summarizing the findings, including identified weaknesses, their impact, and recommended corrective actions.
- Distribute the report to relevant stakeholders, including the Information Security Officer, IT Security Team, and senior management.
Corrective Actions and Improvement:
- Develop and implement corrective actions to address identified weaknesses or gaps in security controls.
- Track the progress of corrective actions and ensure timely resolution.
- Update policies, procedures, and controls based on lessons learned and continuous improvement feedback.
7. KPIs
The Head of Information Security shall review the effectiveness of the information security control as through following channels:
• The number of security incidents and occurrence of related issues as generated by the systems.
• Security Incident reported by staff and stakeholders
• Security Effectiveness as observed by the senior management.
The Key Performance Indicators (KPIs) for the effectiveness of information security are as follows:
Information Security Control Effectiveness Matrix.
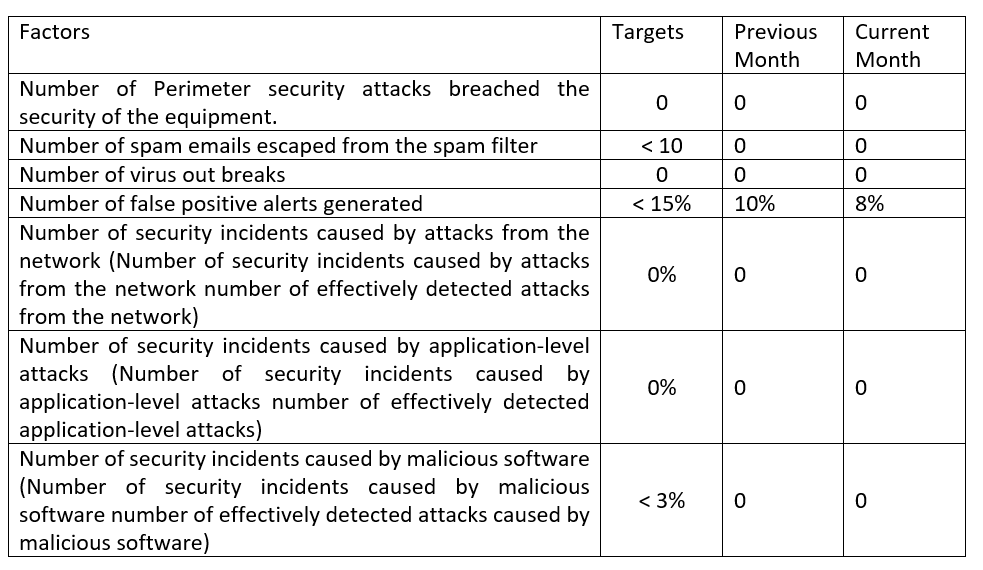
8. Exit
The effectiveness results are recorded, analyzed and appropriate action taken for further improvement.
9. Output
Filled Information Security Control Effectiveness Matrix.
10. Review and Update
The Security Control Effectiveness Monitoring Procedure shall be reviewed annually or when significant changes occur in the organization’s environment, technology, or regulatory requirements.
Updates to the procedure shall be approved by the Information Security Officer and senior management.
11. Definitions and Terminology
Security Controls: Measures or mechanisms that protect information assets from threats and vulnerabilities.
Monitoring: The process of continuously observing systems, networks, and controls to identify and respond to security events.
Effectiveness: The degree to which a security control achieves its intended purpose and objectives.
ISO 27001:2022: An international standard for information security management systems, providing a systematic approach to managing sensitive information.

Introduction
This checklist is developed to assist the implementation of ISO 27001 Standard, and the filled checklist will also act as a record for the implementation, internal and external audit.
In this version the controls are mapped to iso 27001 in two categories which are as follows:
a. Network related control
b. General Control Applicable to Network
This document should be reviewed and updated on regular basis, just ensure that the latest information is available to secure the critical asset of the organization.
Network Specific Controls
A.13 Communications security
A.13.1 Network Security Management
Objective: To ensure the protection of information in networks and its supporting information processing facilities.
A.13.2 Information transfer
Objective: To maintain the security of information transferred within an organization and with any external entity.
ISO 27001:2022 Alignment
This document has been updated to align with the requirements of ISO 27001:2022. The key areas of alignment include:
1. Enhanced risk management practices, including regular risk assessments and reviews.
2. Updated controls for network security management to ensure robust protection of information assets.
3. Implementation of comprehensive information transfer policies to safeguard data exchange with external entities.
4. Strengthening of confidentiality and non-disclosure agreements to reflect current best practices.
5. Continuous monitoring and improvement processes to ensure compliance and effectiveness of security measures.
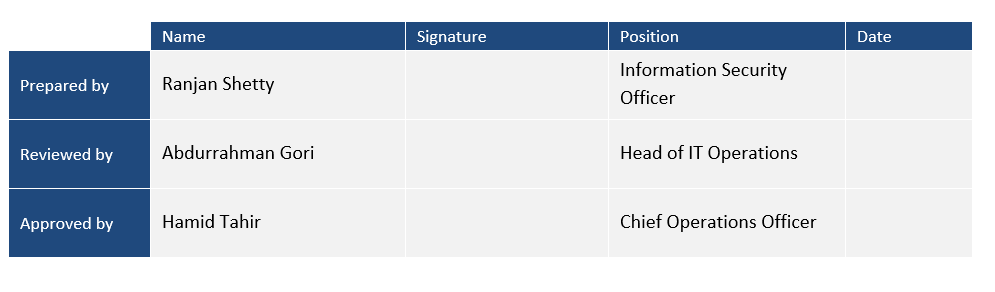
1.Introduction
This document ensures that the minimum-security requirements are being addressed regarding Applications & Databases.
The document is part of the Information Security Management System; this document shall be under the document control. Any change to this document must be informally initiated as a change request. The document shall then be updated, and previous versions must be archived.
This document must be reviewed at least on yearly basis.
2. Undertaking and Confirmation
We hereby confirm following:
1. All critical and high vulnerabilities regarding Applications & Database are closed, verified & validated.
2. The Application & Database is monitored for the major vulnerabilities on a regular interval.
3. All new Applications & Databases are assessed, and vulnerabilities are addressed and closed, unless there is a technical limitation or business justification. In that case, Risk Acceptance is signed.
4. In case of Major Change in the Applications & Databases, the vulnerabilities are re-assessed and addressed.
5. Log of the Applications & Databases are reviewed on regular basis.
6. The best practices are followed for the Application & Database architecture and design. Any change request to Application architecture and configuration settings is assessed for the impact and the concerns are addressed in the change request.
7. The compliance of the Application & Database policy is ensured by the relevant staff members. If there is any exception, it is mentioned in the exception section with justification and Risk Acceptance.
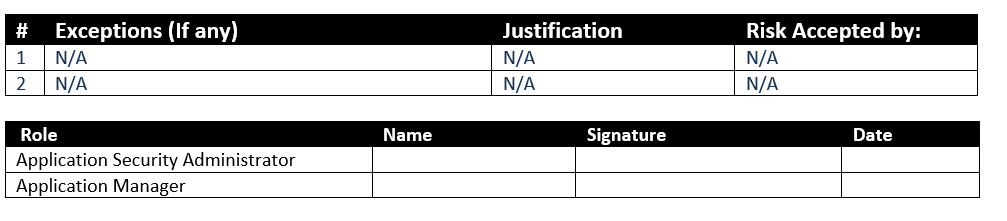
3. Application & Database Security Assurance
Insecure applications open your organization up to external attackers who may try to use unauthorized code to manipulate the application to access, steal, modify or delete sensitive data.
3.1 Common Application & Database Security Controls Status
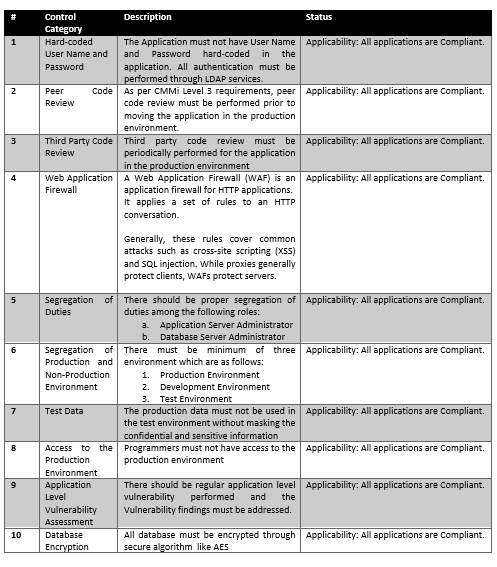
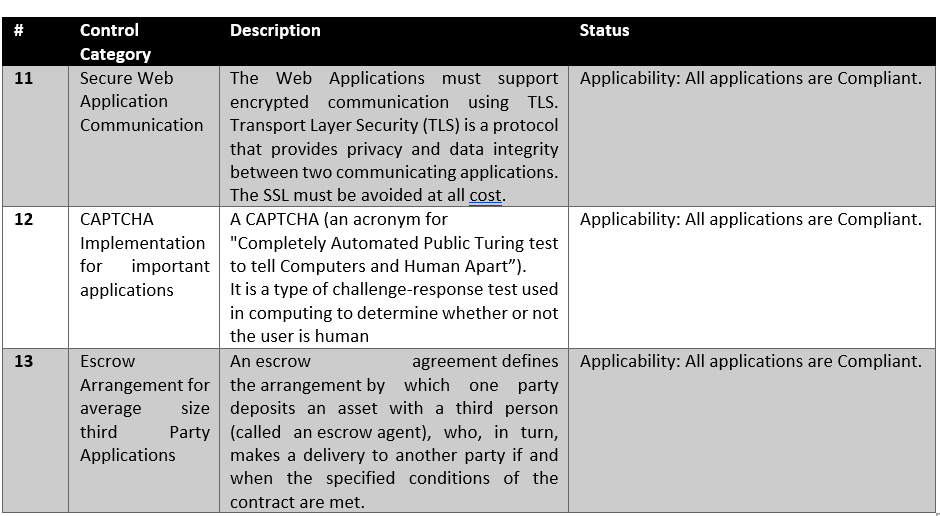
OWASP & Other Application/Database Vulnerability Status
The Open Web Application Security Project (OWASP) publishes a list of the top 10 application security risks.
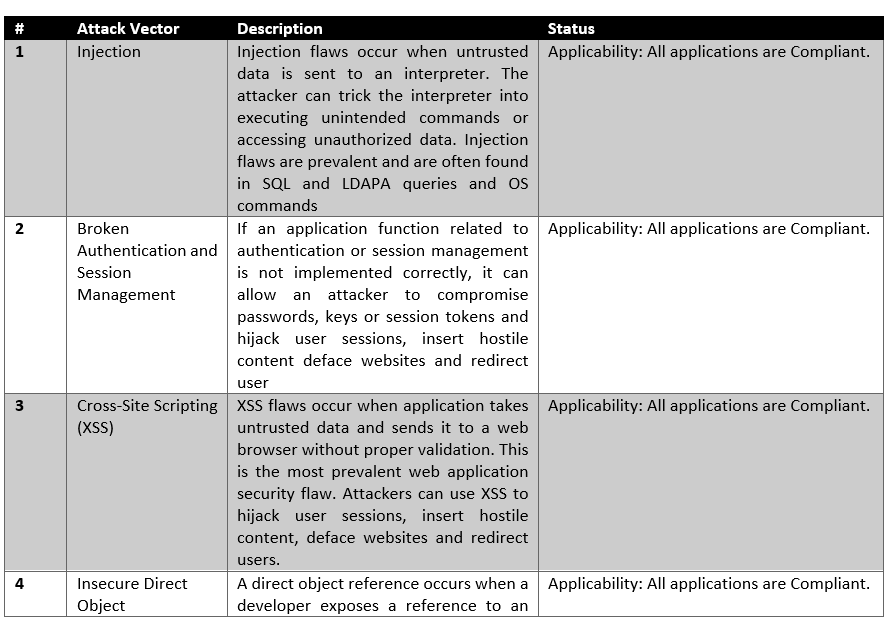
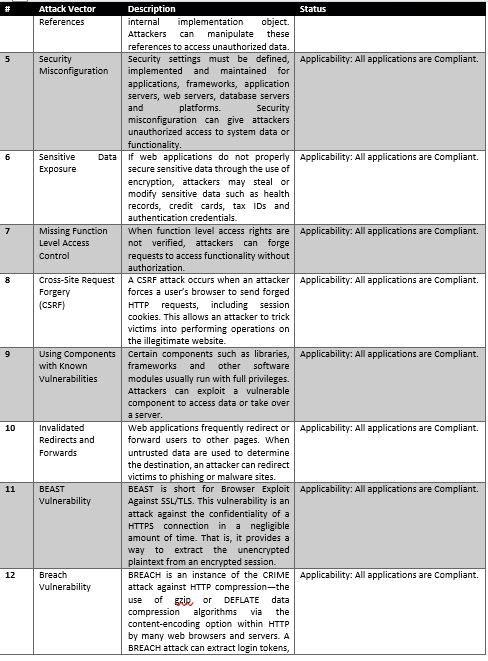

Note: Attack vector - A path or route used by the adversary to gain access to the target (asset). There are two types of attack vectors: ingress and egress (also known as data exfiltration).
4.ISO 27001:2022 Alignment
This document has been updated to align with the latest ISO 27001:2022 standards. Key areas of alignment include:
1. Implementation of robust access control measures to ensure only authorized users have access to applications and databases, including the use of multi-factor authentication and role-based access controls.
2. Regular security assessments and vulnerability scans of applications and databases to identify and address security weaknesses promptly.
3. Adoption of secure coding practices to minimize vulnerabilities, with an emphasis on protection against common threats such as SQL injection, cross-site scripting (XSS), and other OWASP top 10 vulnerabilities.
4. Enhanced encryption standards for data at rest and in transit to protect sensitive information, utilizing industry-standard encryption algorithms.
5. Comprehensive logging and monitoring of application and database activities to detect and respond to unauthorized access and suspicious activities.
6. Implementation of secure backup and recovery procedures to ensure the integrity and availability of data, with regular testing of recovery processes.
7. Continuous improvement of security measures through regular updates, patch management, and adherence to the latest security best practices.
5. Appendix: Application Audit Checklist
o the application shall not have username and password hardcoded; the authentication must be performed through Lightweight Directory Access Protocol (LDAP).
o The application shall not show any information till the Log-on process is complete.
o The application shall display a general notice warning that the computer should only be accessed by authorized users.
o The application shall not provide help message during the log-on procedure that would aid an unauthorized user.
o The application shall validate the log-on information only on completion of all input data. If an error condition arises, the system should not indicate which part of the data is correct or incorrect.
o The application shall protect against brute force log-on attempts.
o The application shall log unsuccessful and successful attempts.
o The application shall raise a security event if a potential attempted or successful breach of log-on controls is detected.
o The application shall display the following information on completion of a successful log-on:
· Date and time of the previous successful log-on.
· Details of any unsuccessful log-on attempts since the last successful log-on.
o The application shall not display a password being entered.
o The application shall not transmit passwords in clear text over a network.
o The application shall terminate inactive sessions after a defined period of inactivity, especially in high risk locations such as public or external areas outside the organization’s security management or on mobile devices.
o The application shall restrict connection times to provide additional security for high-risk applications and reduce the window of opportunity for unauthorized access.
1.Introduction
This checklist is developed to assist the implementation of ISO 27001 Standard, and the filled checklist will also act as a record for the implementation, internal and external audit.
This document should be reviewed and updated on regular basis, just ensure that the latest information is available to secure the critical asset of the organization.
HR Department Checklist
A.7 Human resource security
A.7.1 Prior to employment
Objective: To ensure that employees and contractors understand their responsibilities and are suitable for the roles for which they are considered.
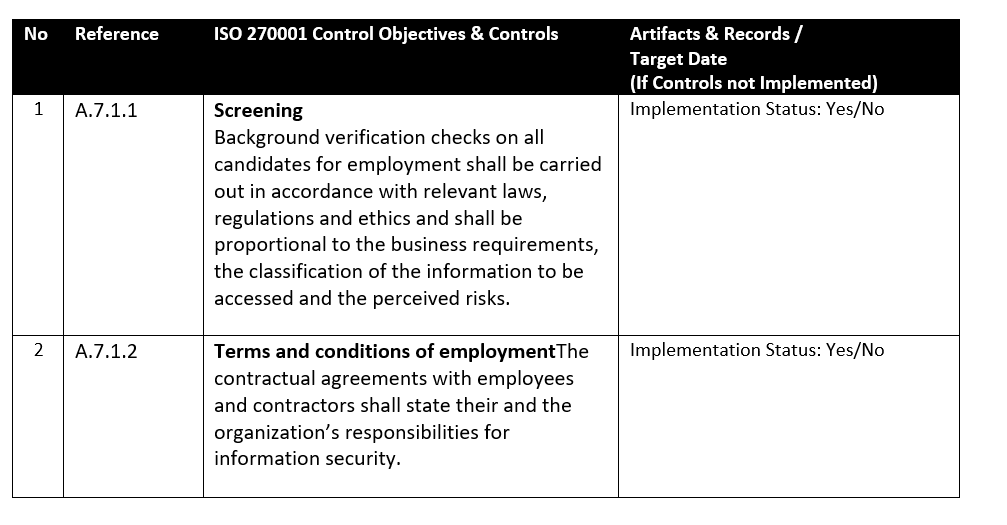
A.7.2 During employment
Objective: To ensure that employees and contractors are aware of and fulfil their information security responsibilities

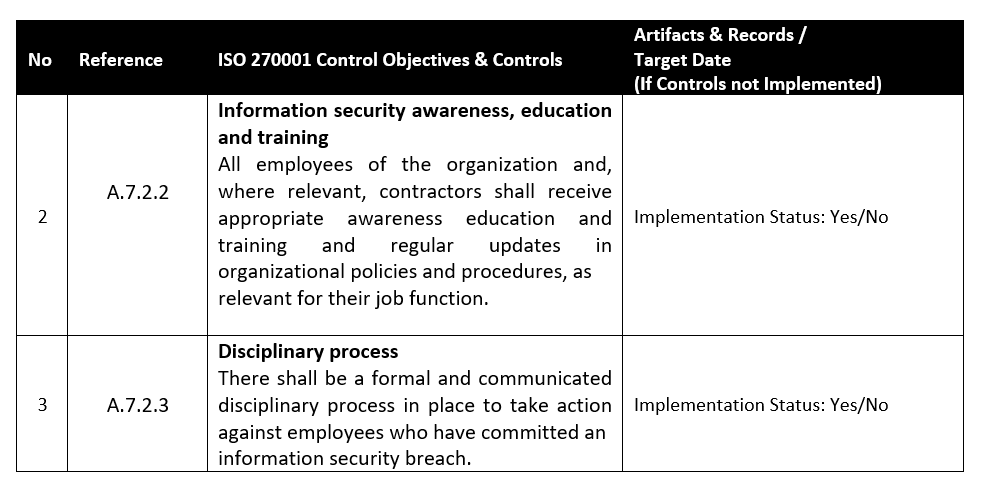
A.7.3 Termination and change of employment
Objective: To protect the organization’s interests as part of the process of changing or terminating
employment.
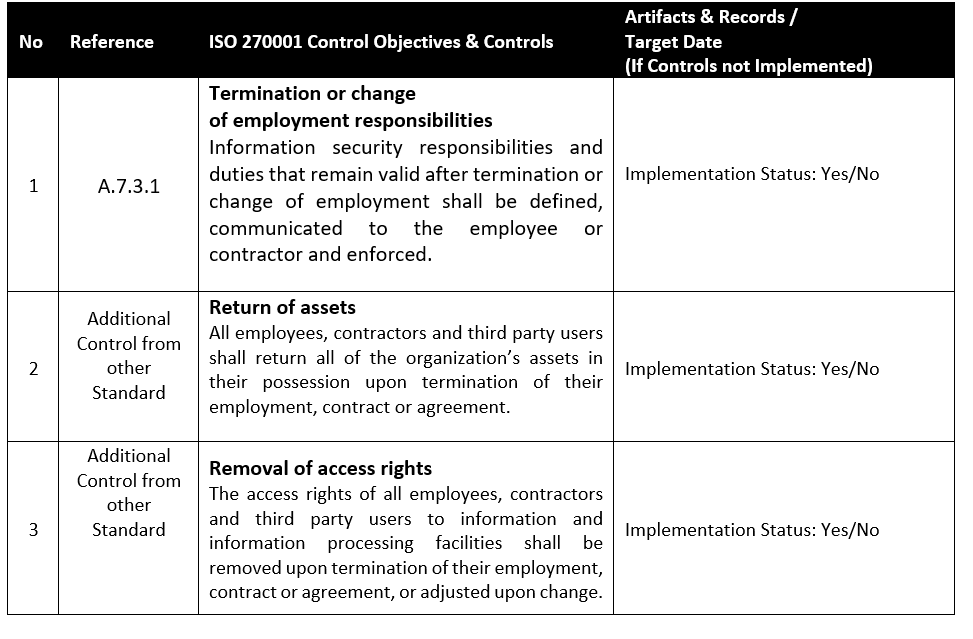
ISO 27001:2022 Alignment
This document has been updated to align with the latest ISO 27001:2022 standards. Key areas of alignment include:
1. Enhanced procedures for screening and onboarding to ensure the suitability of candidates and employees for their roles, taking into account the classification of information they will access.
2. Strengthened employee and contractor agreements to clearly define responsibilities for information security, including confidentiality obligations.
3. Implementation of comprehensive information security awareness, training, and education programmes, ensuring all personnel understand and adhere to security policies and procedures.
4. Establishment of a formal disciplinary process to address violations of information security policies, ensuring consistent and fair application.
5. Procedures for managing information security during termination or changes of employment, including the secure return of assets and the removal of access rights.
6. Continuous monitoring and improvement of HR security policies to align with evolving security threats and organisational needs.
1. Introduction
This control provides processes and references for Continuous monitoring of NT Office Premises located in AL Jumaiah Building in Al Mohammadian Area in Riyadh, Saudi Arabia.
2.Policy Statement
We at NT
want to ensure that Premises Shall be continuously monitored to prevent, detect
and deter unauthorized physical access.
3. Scope
NT HQ physical premises should be monitored by surveillance systems, which includes video monitoring and recording systems such as CCTV, Physical security verification and authorization of guests, maintenance personal, employees and external authorised personnel to access premises.
3.1 Assumptions
• Existing CCTV Camera system working and recording plus play back is working.
• CCTV Camera system is being monitored from multiple screens.
• Door Access Control / Entry System is functional.
• Authorized Entry Register is maintained at entry points.
4. Perimeters for monitoring
4.1 External access control and monitoring
• NTHQ main door is access controlled and opened only with employee having authorised access card, upon tapping with employee authorised card at the sensor the door access system checks and allow the door to open.
• In case a guest or maintenance personal etc, the person will use the Video Door phone at entry point and speak to the attendant at reception with purpose and request to allow access to enter the premises.
• CCTV Camera recording is ON, and the monitoring person or receptionist has seen the person requesting entry and checks with the concern employee to verify the person requesting access at the door to allow or not.
4.2 Internal access control and monitoring
• Critical areas to monitor inside premises are IT Data centre and the management plus HR area.
• In case a guest or employees or external person is authorised to enter the premises, the visitor is accompanied to the concerned person he intends to meet, or he will be made to wait in waiting area and accompanied to meeting room to meet the employee.
• The waiting area is monitored and continuously recorded.
• Entry into the Management/HR section is controlled by access card, only authorised persons are allowed to enter.
• IT area room access is restricted and only allowed to be accessed by IT Personal.
• IT Data Centre is always locked, and entry/exit entries are recorded in logbook.
5. Video Surveillance and Recording
• A high-quality video surveillance and recording system by HikVision is installed in NT HQ covering all door entry points in 1st, 4th and 5th floors and reception/waiting area in 4th floor.
• CCTV Camera live stream is available in multiple locations, receptionist in 1st and 4th floor and in IT/Admin desktops for monitoring purpose.
• Period checking of playback is done by IT dept to verify the recording of all 4 cameras.
6. Access control
• Access control to the premises is by access card system and controlled by Admin department.
• Monitoring access control and generating reports/verifying access, entry and exit is done by admin dept.
7. Not Controlled or Covered by NT
• Access control to the building, parking area is done by building security.
• First point of Access Control/Security is at the entrance of the building by security guard. If in doubt or suspicious personal or carrying parcels or delivery items, the building security will call NT admin to check visitor credentials before giving permission to enter the building.
• All Courier / Delivery personnel are restricted by building security to the main entrance in ground floor.
• Delivery of oversized items or material is restricted from basement entrance, which is controlled by building security.
• Periodic checking of Fire and Alarm systems for building is through building management system.
8. Proposed Enhancements
• Alert/Alarm system in case of intrusion or suspicious activity.
• Alarm and response system in case of building power failure.
• UPS or power backup for recording equipment.
9. Output
• Continuous Video Recording and Monitoring system in place.
• Periodic checking and playback are done by IT dept.
1. Introduction
This document ensures that the minimum-security requirement is being addressed regarding routers, switches & wireless access points. The documents must be updated after every major VA/PEN test is performed.
The document is part of the Information Security Management System, this document shall be under the document control. Any change to this document must be informally initiated as a change request. The document shall then be updated, and previous versions must be archived.
This document must be reviewed at least on yearly basis.
2.Undertaking and Confirmation
We hereby confirm following:
1. All critical and high vulnerabilities regarding routers, switches and wireless access points are closed, verified & validated.
2. Routers, switches and wireless access points is monitored for the major vulnerabilities on a regular interval.
3. All new routers, switches and wireless access points are assessed and vulnerabilities are addressed and closed, unless there is a technical limitation or business justification. In that case, Risk Acceptance is signed.
4. In case of Major Change in the routers, switches and wireless access points, the vulnerabilities are re-assessed and addressed.
5. Log of the routers, switches and wireless access points are reviewed on regular basis.
6. The best practices are followed for the routers, switches and wireless access points architecture and design. Any change request to routers, switches and wireless access points architecture and configuration settings is assessed for the impact and the concerns are addressed in the change request.
7. The compliance of the routers, switches and wireless access points policy is ensured by the relevant staff members. If there is any exception, it is mentioned in the exception section with justification and Risk Acceptance.
3. Enabled Services: Enabled/ Disabled Services on Network Devices
While there are some services that are required to be enabled for WAN connectivity, remote management, monitoring/ logging, and gaining high availability for user connectivity, some services are unneeded on the network devices. Unneeded services, especially those that use UDP, are infrequently used for legitimate purposes. These unsecure services may be used maliciously to launch Denial of Services (DoS) and other attacks against the network. The below table shows the services, protocols and TCP ports which are authorized to be enabled for different devices.
3.1 Enabled Protocols/Services
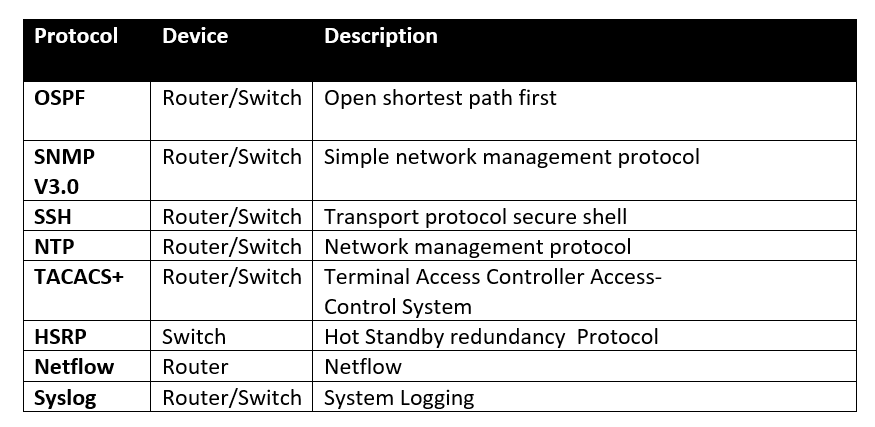
3.2 Disabled Services
The table shows the services and protocols required to be disabled in order to secure access to routers and switches
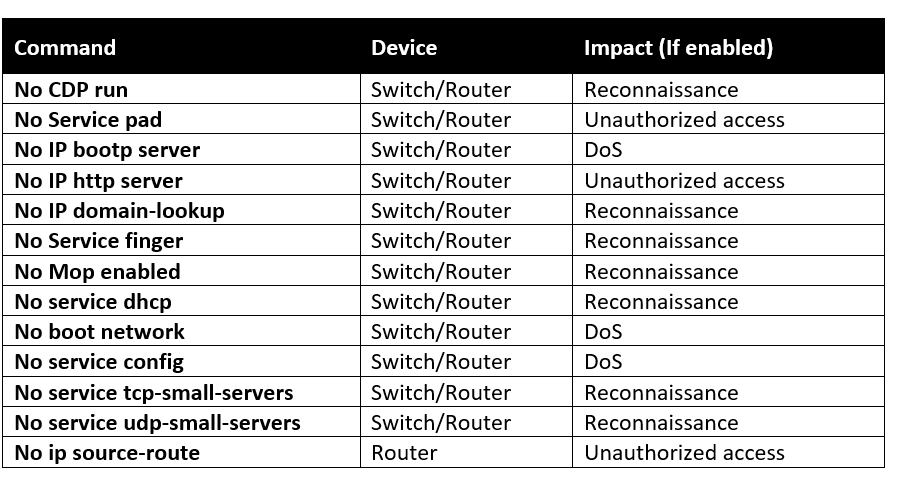
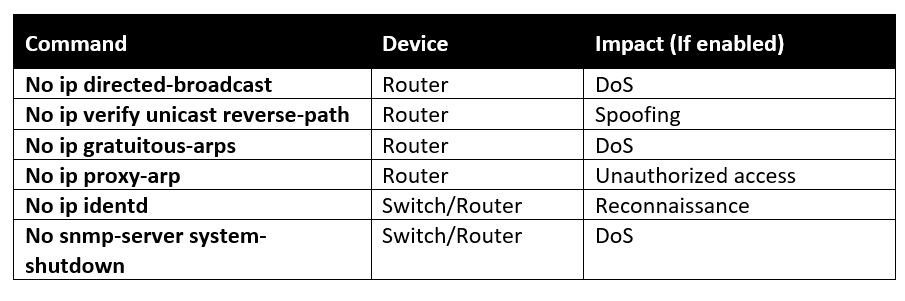
Important Note:
The commands above instruct on how to secure Cisco routers and switches; however, not all commands will work on every device series (router/switch) or on every IOS version, but they will have their own replacement on different IOS versions.
4. Router and Switch Configuration and Security Baseline
4.1 Access Control
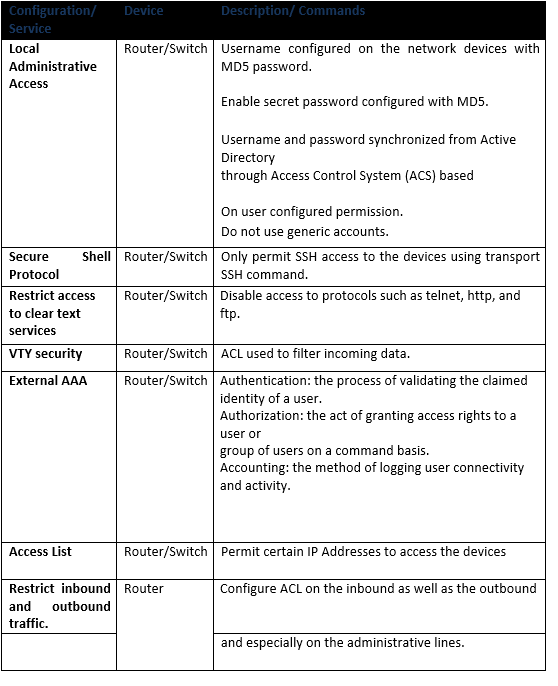
4.2 Password Configuration
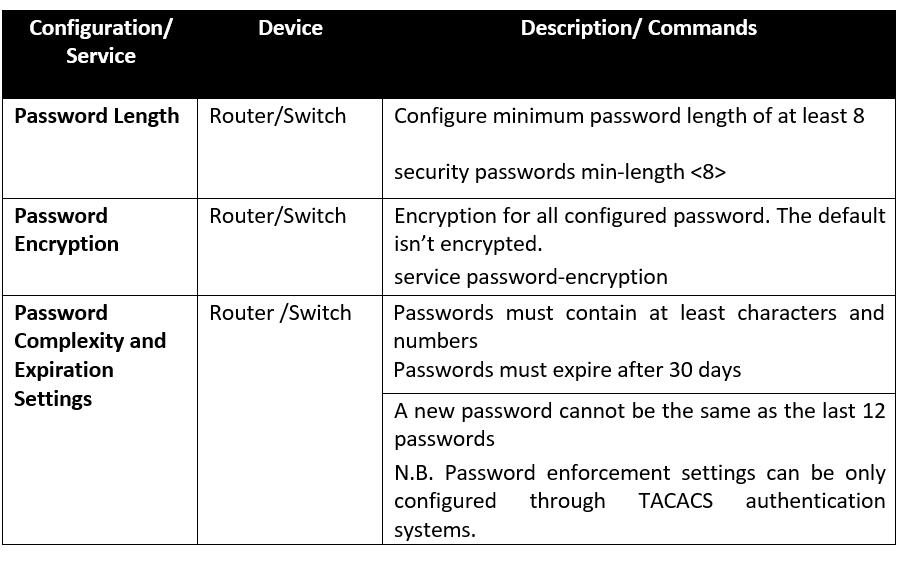
4.3Management Configuration
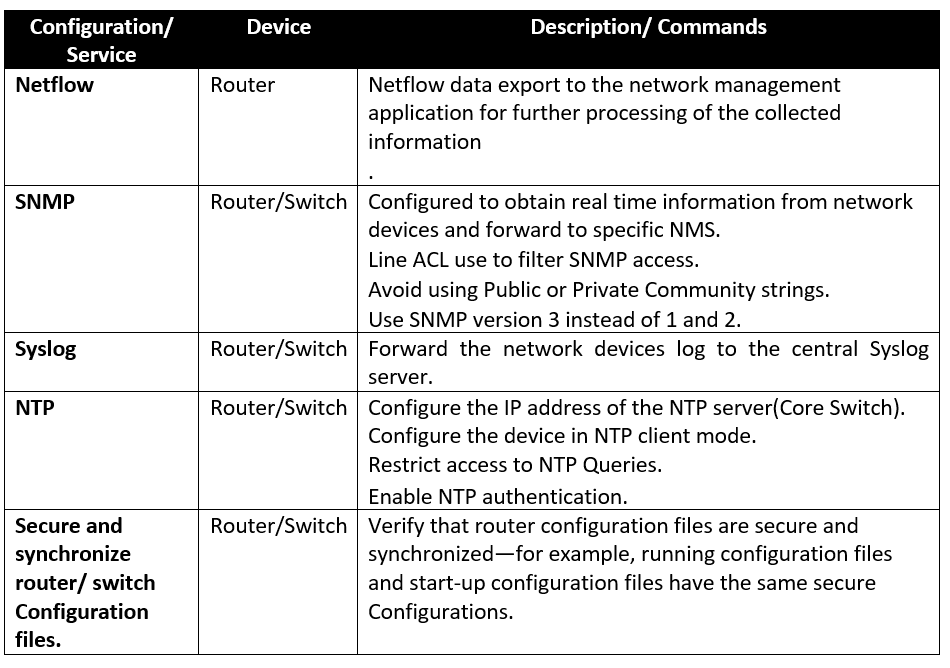
4.4LAN Configuration
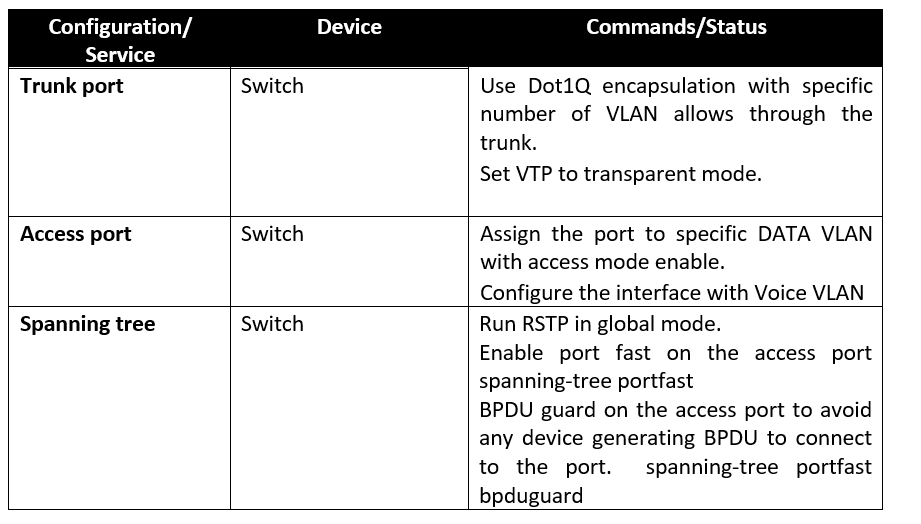
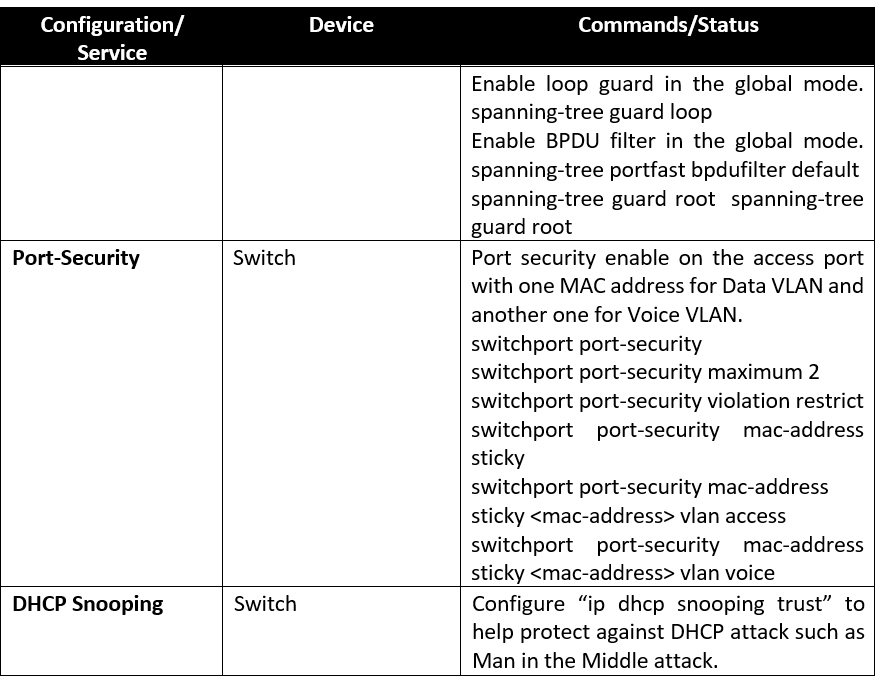
4.5 WAN Configuration
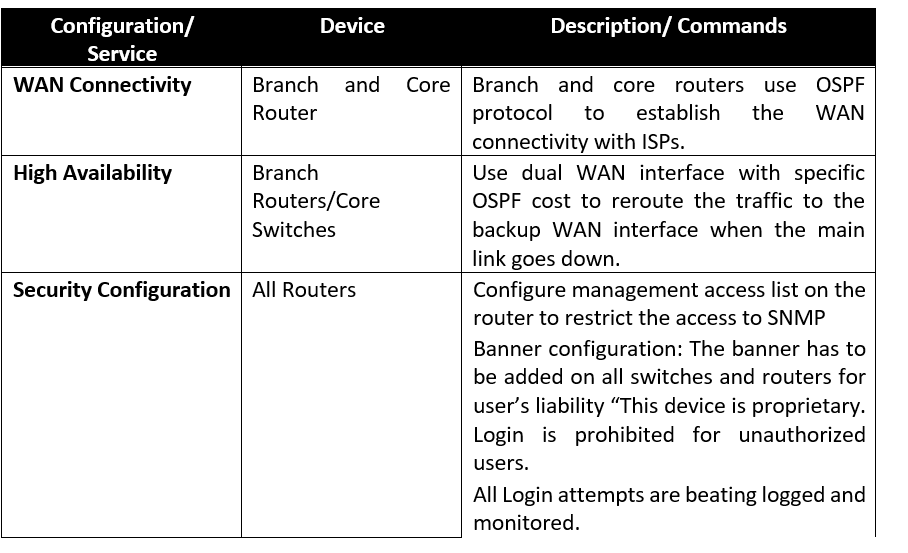
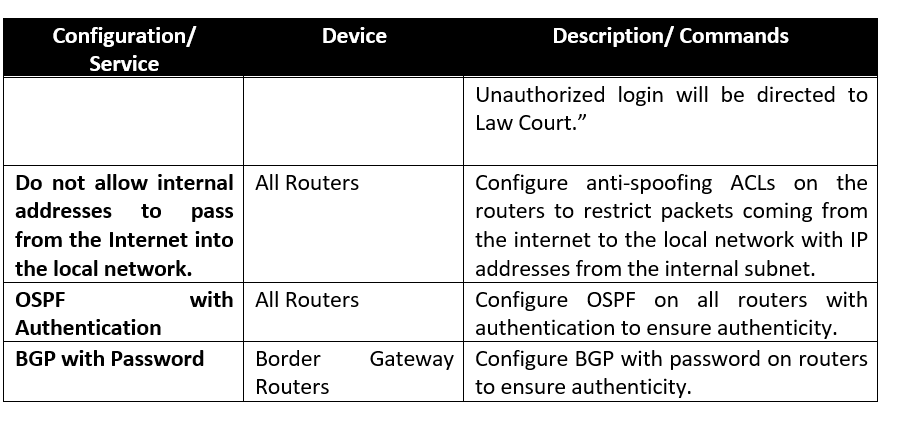
5. New Installation Guidelines
Installing switches/Routers at new locations, replacing old and/or defected switches requires the following:
· Complete the change request forms and submit it .
· For new installations, test functionality and connectivity to the WAN/LAN.
· Make sure the IOS coming with the appliance or the one that will be installed is up to date as per the vendor recommendation.
· Never install a switch with default factory settings on the LAN.
· Always change default usernames/passwords and SNMP community strings.
· Set the local username and password for the administrator account in the event the ACS server goes offline.
· Make sure that every password configured is complaint with the password policy.
· Configure service password encryption to encrypt SNMP, TACACS+ and any other password.
· Enable the secret password configured with MD5 functionality.
· Configure a secure local username and password with MD5 functionality.
· Configure Authentication, Authorization, and Accounting (AAA) on the router to validate the Claimed identity of a user, grant access rights to a user or group on a command basis, and define the method of logging user connectivity and activity.
· Add the ACS authentication server configuration to the new router/switch.
· Apply all network standard baseline configurations stated in the above section.
· Add any new switch or router to the fault management tools.
· Ensure all devices are connected to UPS and mounted properly in the communication rack.
6.Logging and Monitoring Guidelines
· Activity logging must be enabled on all routers and switches.
· Logging must be centralized on a secure management system
· All Log events with severity (0-7) have to be reviewed and monitored on daily basis.
· All logs should have a retention period.
7. Network Incident Report and Change Management
· All network incidents should be documented and reported through SIRT weekly meetings. Any configuration or network design change on the switch or router must be go through change management process.
8.Decommissioning and Physical Placements
Configuration settings must be erased / cleared upon retiring or decommissioning of any switch or router.
9. ISO 27001:2022 Alignment
This document has been updated to align with the latest ISO 27001:2022 standards. Key areas of alignment include:
1. Implementation of enhanced access control measures for network devices, including the use of multi-factor authentication and role-based access controls to restrict access to routers, switches, and wireless access points.
2. Strengthened security for device configurations, including the requirement for encryption of all management traffic and the use of secure protocols (e.g., SSH, SNMPv3).
3. Regular monitoring and auditing of network devices to detect and respond to unauthorised access attempts and configuration changes.
4. Comprehensive logging and monitoring policies to ensure that all critical events are logged and retained for a defined period to support incident response and compliance audits.
5. Secure decommissioning practices for network devices, ensuring that all sensitive information is securely erased before disposal or reuse.
6. Continuous improvement of network security practices through regular vulnerability assessments, penetration testing, and adaptation to new threats and vulnerabilities.
10. Appendix A: Cisco Logging Levels
The following table describes Cisco’s logging levels in details, so please make sure to log the traffic that is really useful in case of incidents and/ or administrative tasks:
11. Appendix B: Key Terms
Router is a network device that forwards packets from one network to another. Based on internal routing tables, routers read each incoming packet and decide how to forward it. The destination address in the packets determines which line (interface) outgoing packets are directed to.
Switch is a device that channels incoming data from any of multiple input ports to a specific output port that will take the data toward its intended destination.
Branch Router is a device used to forward branch user’s traffic to other destination.
Core Router is a device that forwards packets to computer hosts within a network (but not between networks). A core router is sometimes contrasted with an edge router, which routes packets between a self-contained network and other outside networks along a network backbone..
Third Party Router is a device that forwards traffic from an external network (un- trusted) to the network.
Internet Router is a device that forwards internet traffic, external email to the core network, and advertises the public Web Sites to the Internet.
Core switch is a device that provides scalability, high availability, and fast convergence to the network. It is the backbone for connectivity and the aggregation point for the other layers.
Access switch is a device that aggregates end users or servers and provides an uplink to the Core switches. It is considered as the point of entry into the network for end devices/users such as: branch users, floor users, and data center servers.
Introduction
The Information Security Framework is one of the first initiatives to establish a reliable and scalable Information Security Infrastructure. It shall address the issue of securing Organization critical information assets, in terms of Confidentiality, Integrity and Availability.
Information Security Framework lays a strong foundation for the Information Security Management System (ISMS). This framework provides groundwork for proper information security governance, risk management and regulatory compliance.
This Information Security Framework is living document and must be updated on regular basis. This framework should be reviewed at least once in a year or when there is any significant change in the organization.
Executive Summary
Norconsult is a progressive and ambitious organization offering various solutions to several departments in Saudi Arabia. The organization is eager to secure all products and services offered to the customers in order to meet the user’s requirements. The Senior Management recognizes the importance of information security and is aware of repercussions resulting from lack of improper security measures.
The organization realizes that user’s confidence is of paramount importance for the organization to succeed and to excel in the current ever changing environment. One of the key factors, which will build user confidence, is the implementation of a comprehensive Information Security Framework (ISF). ISF lays a strong foundation for the robust information security for the organization, which may be certified against ISO 27001 standard. Information Security Framework has all necessary components to address information security governance issues.
Vital Components of Information Security Initiative
- Information Security Organization
- Roles and Responsibilities – RACI table
- Information Security Framework Cycle
- Non-Disclosure Agreements
- SLA with other Departments
- Continual Service Improvement and Review Procedure
Benefits of Information Security Framework
Following are advantages of the Framework
- Provides structure and a roadmap to help to manage security in a way that supports competitiveness and growth
- Helps identify gaps in capabilities.
- Helps reach the desired security posture that meets business requirements
- Helps prioritize security initiatives
- Simplifies and speeds up the planning and execution of an enterprise-wide security program
- Establish a comprehensive approach to Information Security based on best practices.
The Information Security framework should not be considered as isolated document. The ISF is the integral part of Information Security Management System (ISMS) which cover a wider scope. This document is a living document and it must be updated whenever, there is any major change in the organization. It is highly recommended that this document must be reviewed at least once ion a year to be ensure that all information is correct and up-to-date
Information Security Organization
The Senior Management strongly supports Information Security initiatives in the Organization and are aware of their responsibilities. This Information Security Organization is to address the need of Organization Information Security in a professional manner by qualified, trained and experienced staff members.
Information Security Governance like other governance issues is the responsibility of Sr. Management. Information Security Department will be headed by Information Security Manager who will be responsible to address all Information Security governance issues. Information security is everyone’s responsibility and the senior management expectations are clearly defined in the Corporate Security Policy and Acceptable Usage Policy (AUP).
Information Security Manger (ISM) is fully authorized to set the policies, which shall be applicable to the entire organization. ISM and his team shall initiate, deliver and coordinate information security activities for the Organization to minimize the risk exposure, meet the business requirements and to address the regulatory obligations.
ISM may on his discretion delegate activities to third party but the accountability will stay with department. He may seek specialist information security advice from external security specialists or groups, including relevant authorities.
ISM have to keep the department up-to-date regarding industrial trends, monitor standards and assessment methods and apply them in the organization as per the business need and defined risk threshold and management approved risk tolerance levels. ISM has to further ensure following:
1. Information security goals are identified, meet the organizational requirements, and are integrated in relevant processes;
2. Information Security Policy and Procedure are up-to-date.
3. Information Security Policy is implemented and security activities are executed in compliance with the information security policy.
4. Systems are in place to handle non-compliance.
5. Identify significant threat changes and exposure of information and information processing facilities to threats.
6. Risk Assessment is conducted regular intervals and relevant controls are applied to ensure controls are within the defined and accepted Risk threshold.
7. ISM has enough resources to do the job.
8. Specific roles and responsibilities for information security across the organization.
9. Information Security Awareness, education, and training plans are in place and effective.
10. Implementation of information security controls is coordinated across.
11. Effective systems are in place to handle information incidents.
12. Confidentiality and Non-Disclosure Agreement (NDA) are in place and are reviewed at periodic interval.
13. Access to the third party is controlled and monitored.
14. All identified security requirements should be addressed before giving customers access to the organization’s information or assets.
Security Organization improvement initiatives shall be reviewed by independent third party every year.
Roles & Responsibilities
Here are the roles and responsibilities of the Information Security Personnel.
Information Security Officer

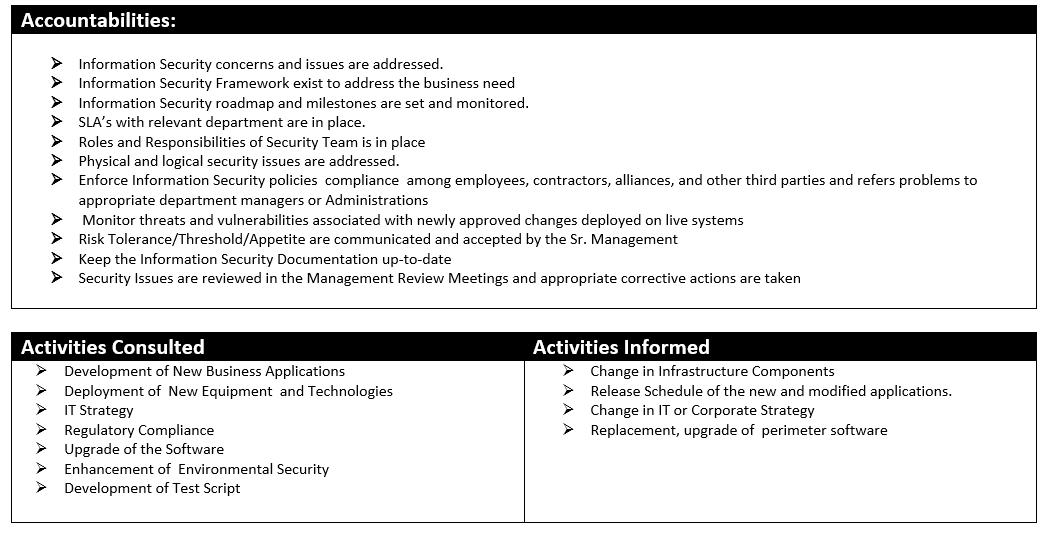

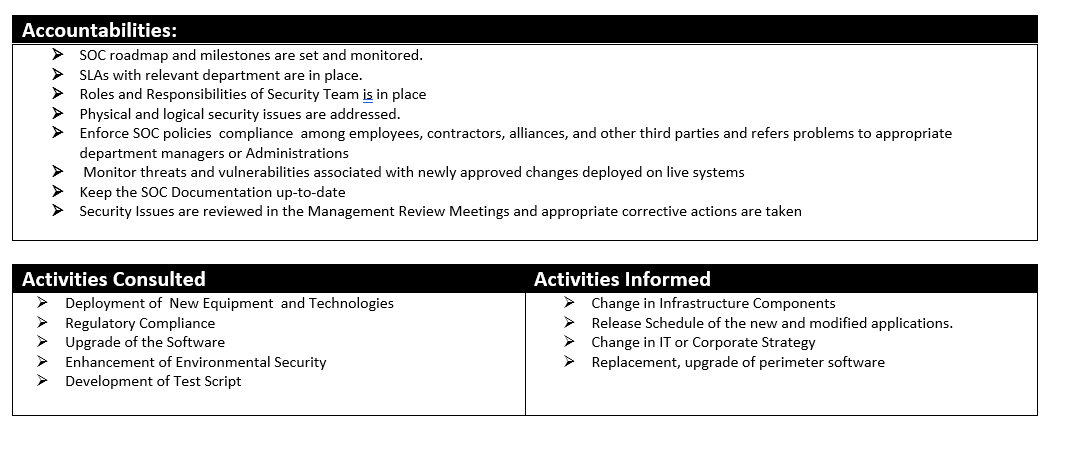
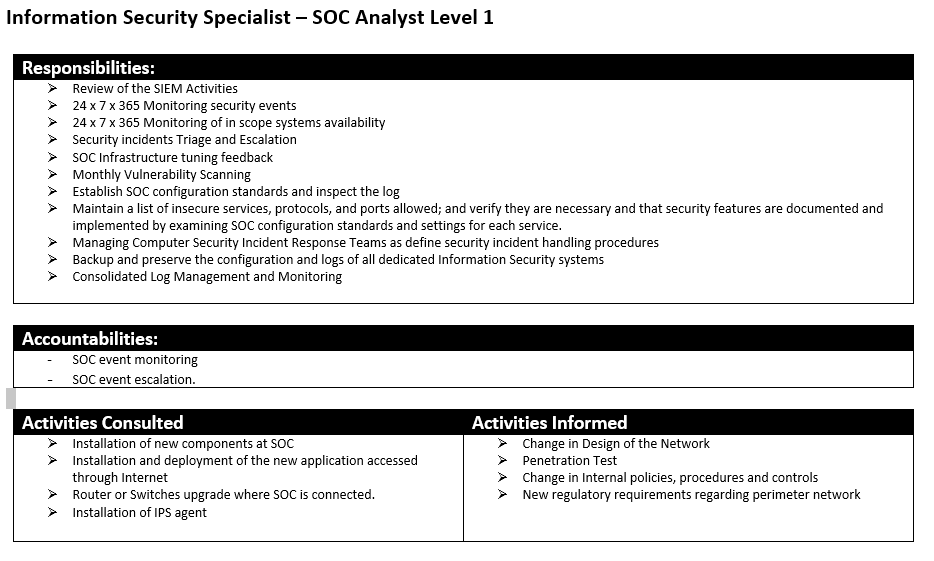
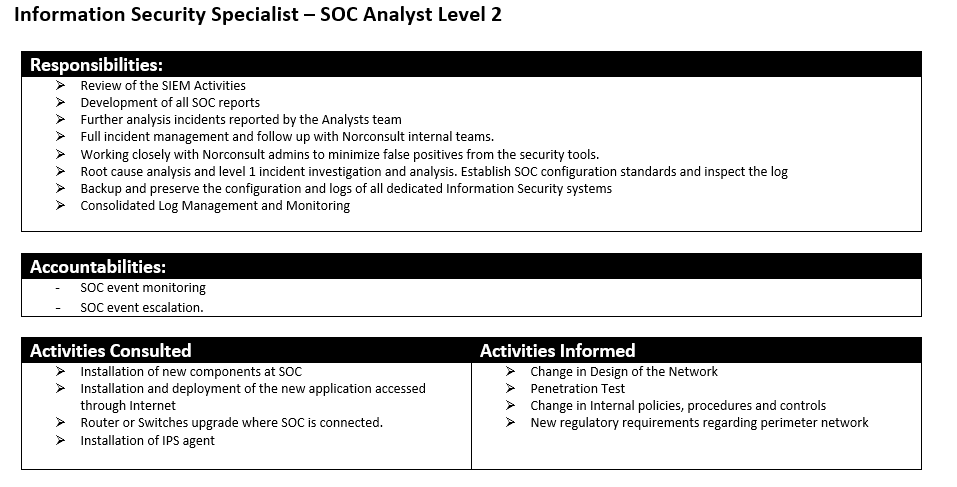
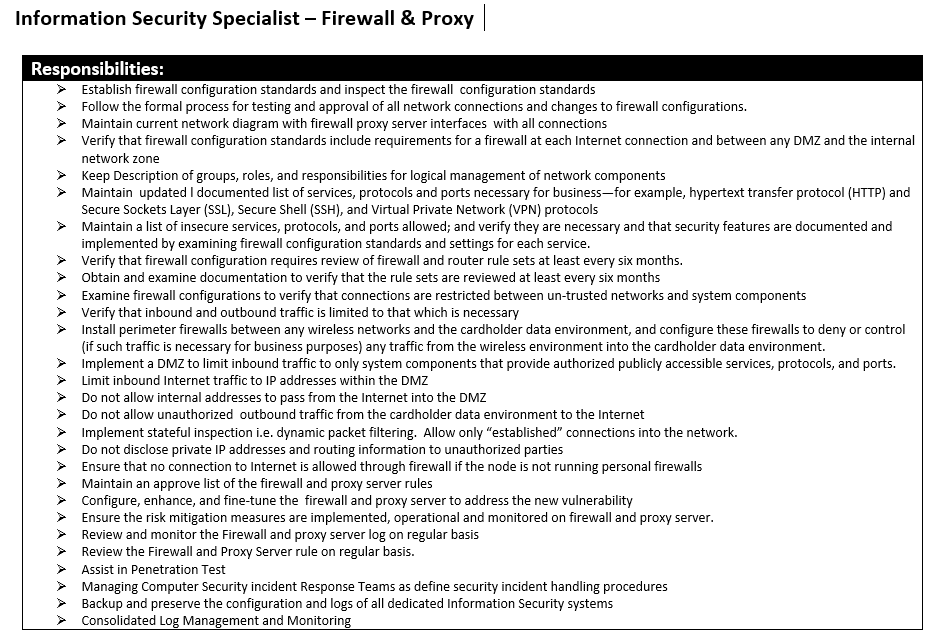
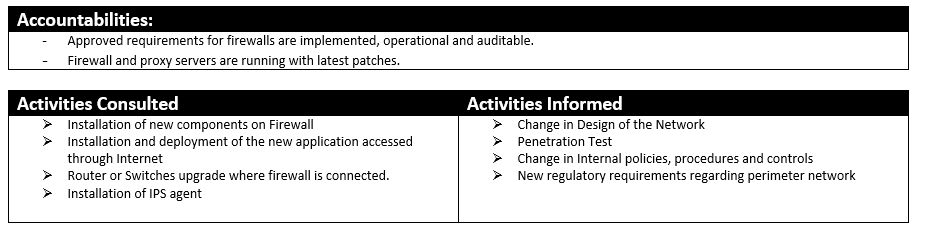
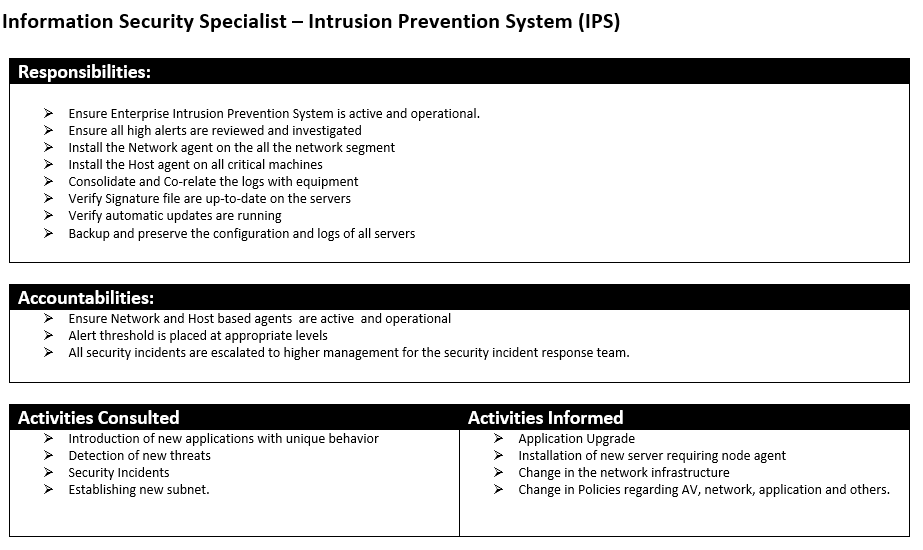
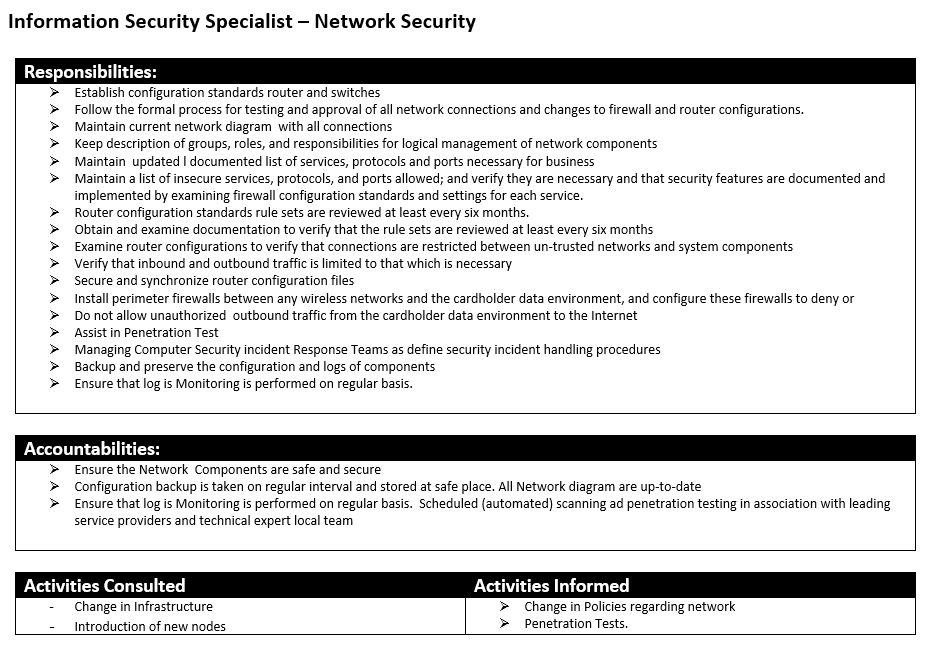
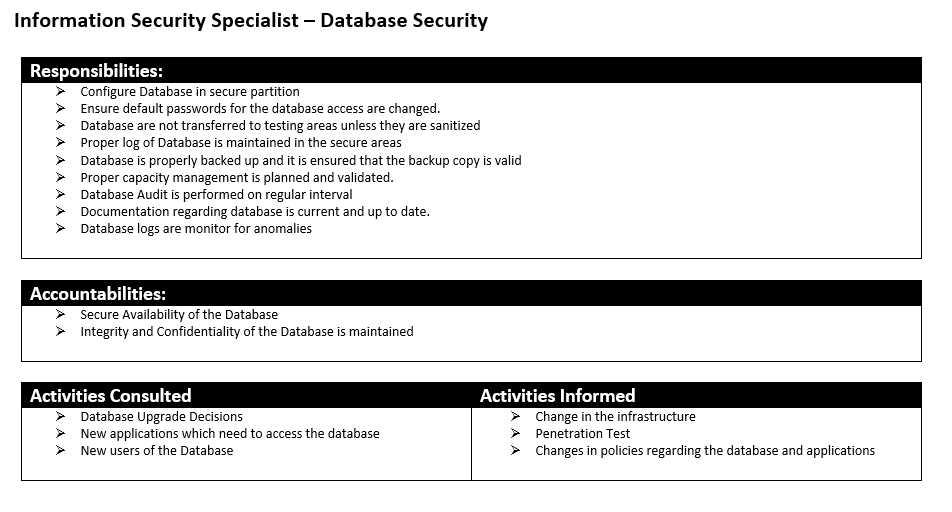
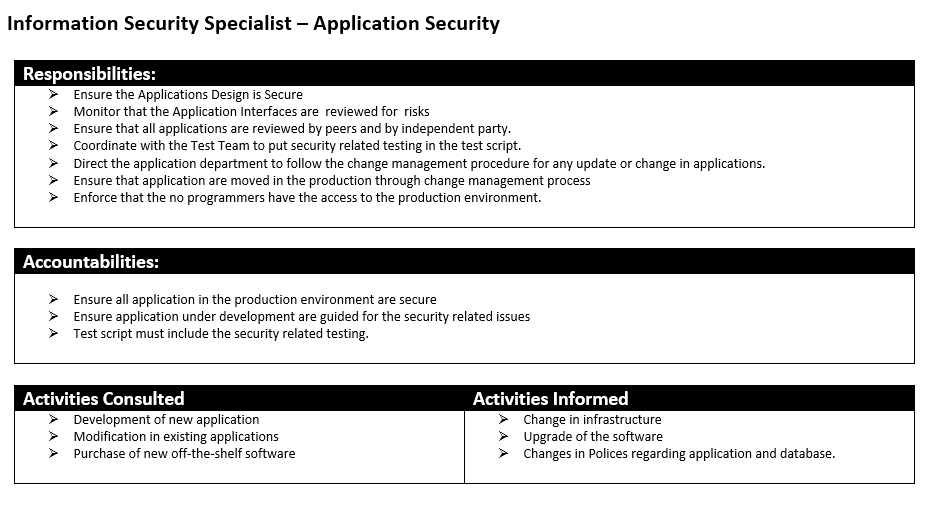
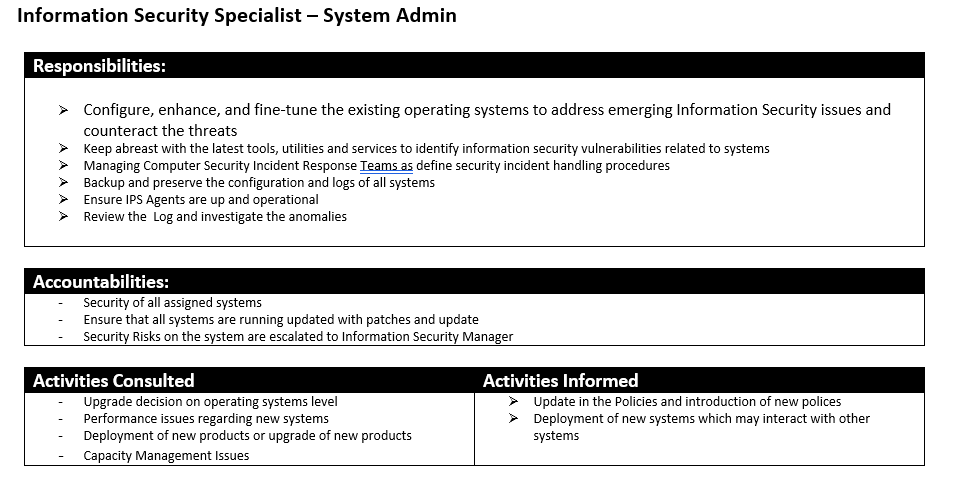
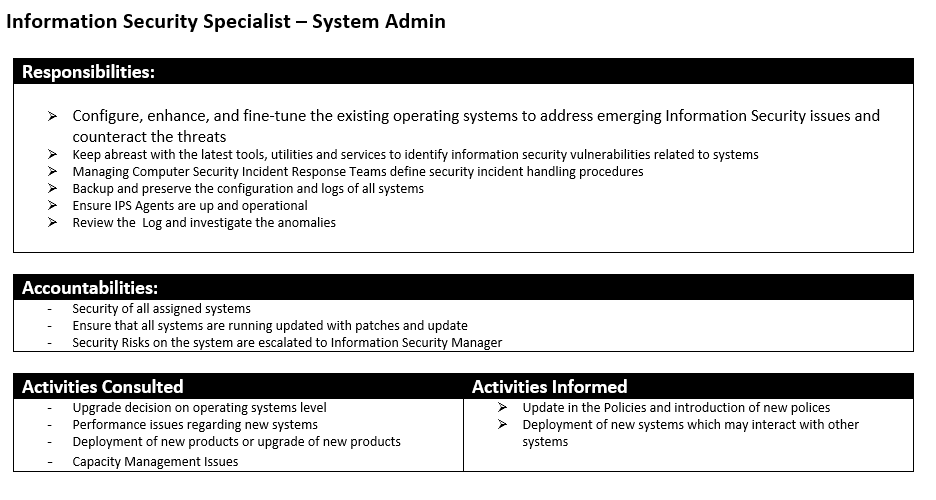
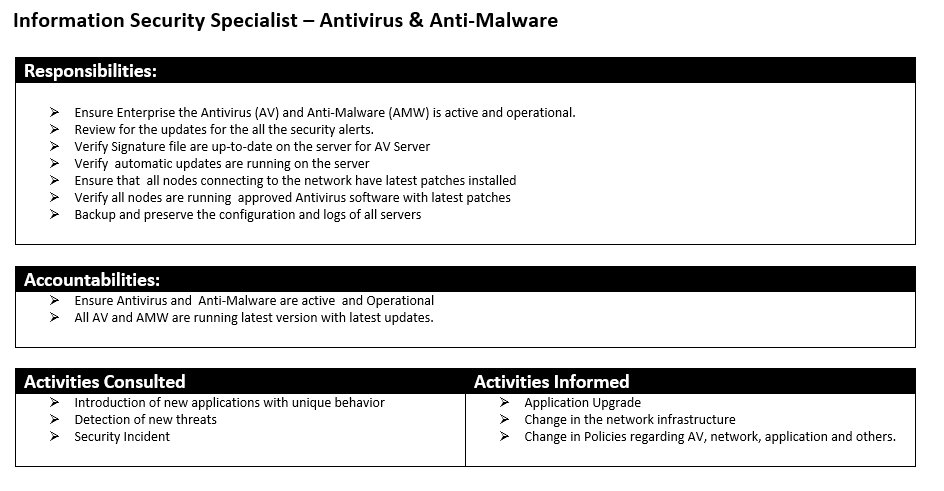
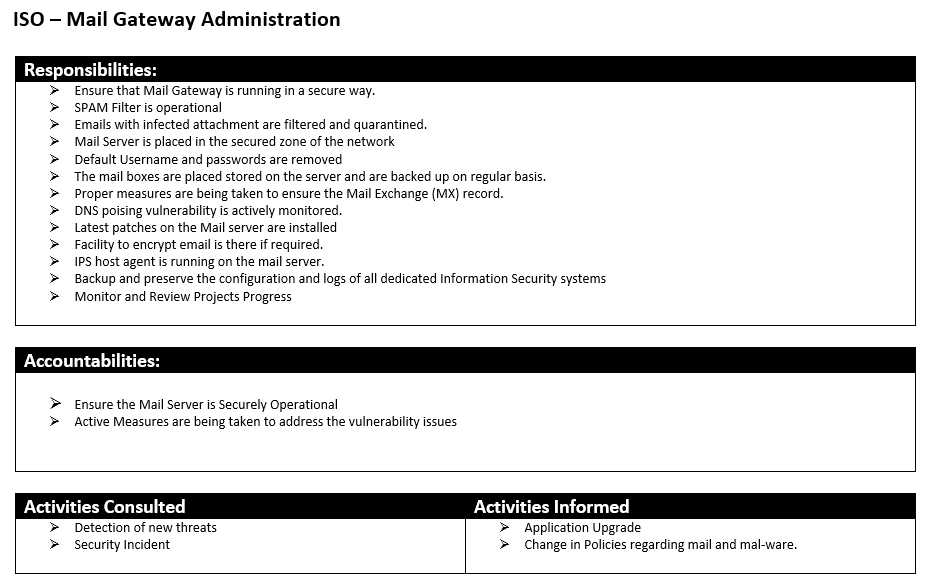
RACI Matrix
Responsible, Accountable, Consulted, and Informed (RACI) matrix which is also known as Responsibility Assignment Matrix (RAM) or Linear Responsibility Chart (LRC), shall describe the participation of the employees in completing the tasks during the predefined procedures. RACI is a very useful tool which is used to clarify the roles and responsibilities in cross-functional/departmental projects and processes
The matrix is typically designed a vertical axis (left-hand column) of activities performed during the process and a horizontal axis of roles as illustrated in the matrix bellow. RACI is an acronym derived from the four key responsibilities known as Responsible, Accountable, Consulted and Informed.
Responsible
Responsible is the person who performs the activities and procedures to achieve the desired task. This is a typically role with a participation type of responsibility, however, others roles can be delegated to assist in the work required.
Accountable (also Approver or final Approving authority)
Accountable is the person who is ultimately accountable for the correct and thorough completion of the procedure and activities. In other words, an Accountable shall sign off (Approve) the work that Responsible person provides to him. It shall ensure that there is only one Accountable specified for each procedure
Consulted
Consulted is a person whose opinions is used in order to complete the procedures or required tasks in appropriate manner.
Informed
Informed are the persons, who are kept up-to-date on the progress of the procedure, often only on completion of the procedures or activities.
Mapping of the Current Designation/Staff to the Roles
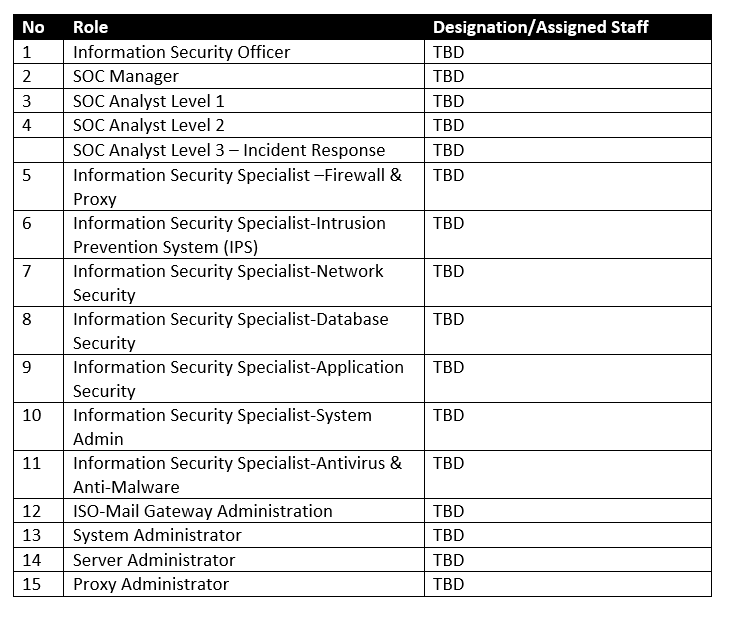
RACI Explanation for the ISD
R = Responsible, this is the person who is doing the actual job. There should be at least one person for each activity however there will be more than one person are possible as per the business case.
A = Accountability, which means the person will be solely answerable for the activity. RACI cannot have more than one “A” per activity.
C = Consulted.
I = Informed
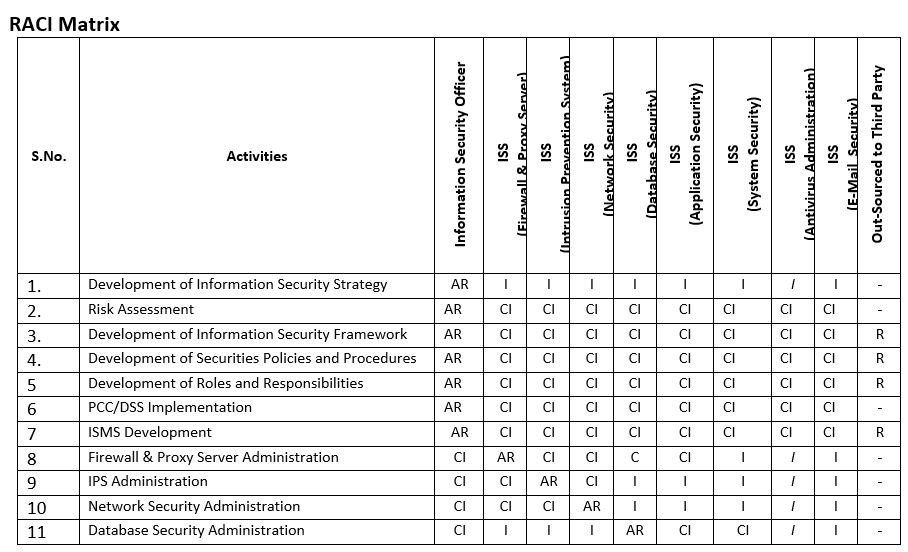
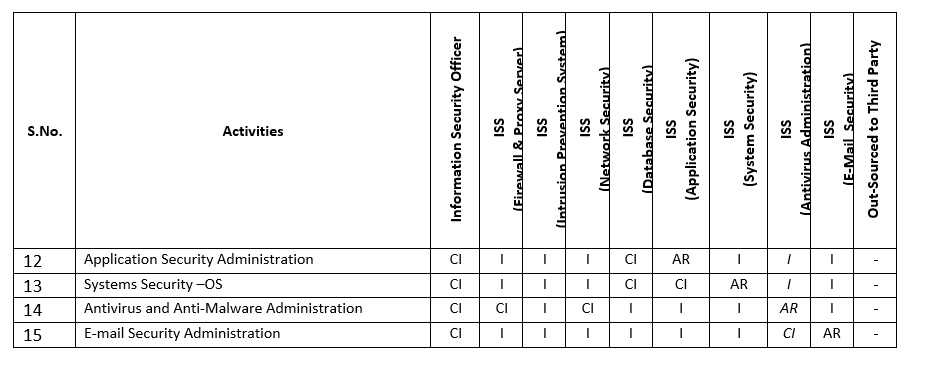
Information Security Framework
Information Security Framework
Information Security Framework shall facilitate in maintaining a secure and reliable environment. The framework provides a clear direction to effectively implement the strategy of Security and also helps to communicate the design and architecture of the critical components to the organization Staff Member.
The aim of the Framework is to secure organization’s assets, systems, infrastructure, applications and processes. Information Security Framework specifies the four major components and the sequence among them. It also mentions the different items within each of the component for clear understanding. Various management controls (Administrative, technical and physical) and tools are utilized to classify data and perform risk analysis and assessments with continuous monitoring for compliance. The overall framework can be summarized as follows:
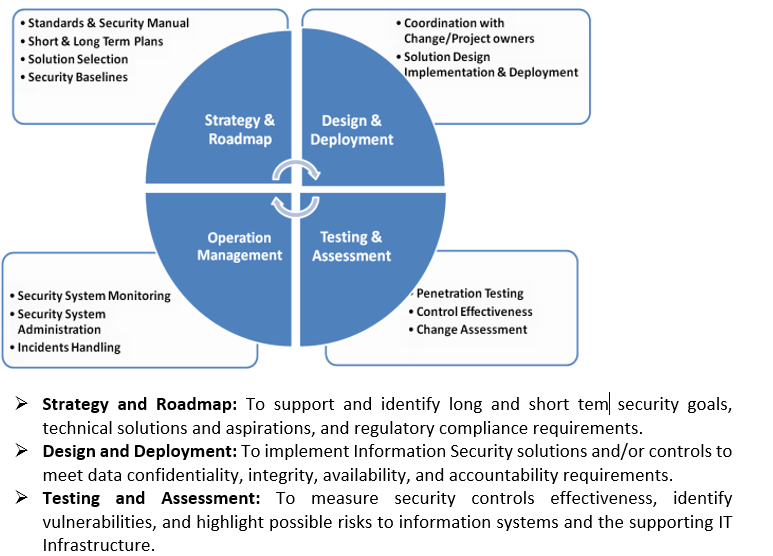

Break-Down of Security Management Framework
Strategy and Roadmap
To support, identify long-term, and short-term security goals, technical solutions, aspirations, and regulatory compliance requirements.
Following are the components of Strategy and Roadmap:
Standards & Security Manual: Standards and security manual shall be developed as per the industry best practices and must be approved by the senior management. The manual shall be based on the PDCA (Plan, Do, Check, Act) cycle. This manual must be circulated to the relevant stakeholders and training session must be held. The periodic review of the manual must be performed on at least yearly basis.
Short & Long Term Plans: This section shall help Information Security Department to align its operations with the business to achieve the desired objectives. Short-term plan shall be developed for one to three years and the long-term plan shall focus on objectives beyond three years. These plans shall be reviewed on yearly basis and adjustment must be performed. These plans provide the strategic directions in order to achieve their objectives.
Solution Selection: For the solution selection, initial requirements shall be collected from the relevant stakeholders. Multiple vendors shall be asked to respond to RFP (Request for proposal). The received RFP shall be evaluated on the predefined criteria. After evaluating the vendor and short-listing the vendor, proof of concept shall be requested. The proposed solution shall be assessed for the feasibility and later purchase order may be issued.
Security Baseline: Security baseline shall define the minimum-security requirements for organization and must be used as a reference for maintaining the desired security level. These baselines must be short and concise. Baselines must be reviewed and updated on at least yearly basis.
Design and Deployment
To implement Information Security solutions and/or controls to meet confidentiality, integrity, availability, and accountability requirements.
The components of Design and Deployment are as follows:
Coordination with Change/Project owners: For the coordination with change owner, RFC (Request for Change) shall be prepared and assessed for the impacts by change manager. It shall be ensured that the change is formally authorized and approved. Once the change is implemented, exhaustive test must be performed prior to the rollout to production environment.
The coordination with the project owners is of critical importance; the projects must be following the IPECC (Initial, Planning, Execution, Control, Closure) cycle. Information Security Department shall be involved from the planning phase and must review the execution phase thoroughly to ensure that project is progressing as per the project plan. Security concerns regarding projects must be identified and documented. Periodic review of the control must be performed. Progress of the project shall be monitored and identified. Security concerns must be noticed and shall be followed up till they are resolved.
Solution Design: The solution design is a key component for overall framework. The solutions shall be compatible with the existing components and equipment. The organization shall follow the best practices of TOGAF for solution design in future. TOGAF shall ensure the compatibility with other components besides ensuring the overall security.
Implementation & Deployment: The implementation shall be performed as per the approved project plan. It must be ensured that the implementation criteria are approved from all stakeholders. Implementation may be executed through a combination of internal and external resources. Post implementation review shall be performed and the outcome must be documented to ascertain the effectiveness of the solution.
The deployment of the solution must be the combination of the change and release management. It must be ensured that all solutions are exhaustively tested and approved by the stakeholders before moving it to production environment. It must be ensured that the rollback procedures are in place if the deployment is unsuccessful. All stakeholders shall also be informed regarding the deployment and their impact. Helpdesk must be trained and educated to handle any incident as the result of new deployment.
Testing and Assessment
To measure security controls effectiveness, identify vulnerabilities, and highlight possible risks to information systems and the supporting IT Infrastructure.
Penetration Testing: The penetration testing must be performed from external network (public) and also within the internal network. An automated testing facility must be availed to perform more frequent testing on planned and ad-hoc basis. High and medium alerts shall be exhaustively analyzed and the related vulnerability must be identified. Proper controls and measures shall be placed to close the vulnerabilities.
Control Effectiveness: The logical follow-up of risk assessment is to select the appropriate controls that reduce the exposure to the threat. It is required to periodically assess the effectiveness of the control to ensure that no new threat or vulnerability has breached the acceptable risk threshold. The control effectiveness shall be checked on periodic basis to analyze their effectiveness using the current and historical data.
Change Assessment: Change assessment is a process to review the effectiveness of the change and benchmark the results against the expected outcome. If the change is not performed properly and the desired results are not obtained, it may result in loss of time and resources as such tasks might be performed again. The “Post Change Review” is an integral part of change assessment, which shall ensure that all changes are assessed against the impact and effectiveness. The changes, which are less effective or with negative effects, shall be identified and corrective, must be taken.
Operation Management
To operate and maintain Information Security solutions and /or controls to meet data confidentiality, integrity, availability, and accountability requirements.
Operation Management components are following:
Security System Monitoring: Security System Monitoring shall ensure that the security equipments are closely monitored on daily and weekly basis. Log monitoring must be performed for problems, events, incidents and alerts. In case, any suspicious behavior is detected, corrective actions must be taken. Additional controls shall be applied and assessed for effectiveness.
Security System Administration: Security System Administration shall ensure the secure smooth operations of the organization critical components. USA Rainbow Series publications are considered to be an authority on Information Security. The Orange Book of Rainbow Series (as a best practice) specifically asks to separate the system administration with security administration;. Security system administration shall ensure that all equipment are properly administered, configured, operational, monitored and controlled. Proper backup must be taken every night. It must be ensured that the patches and service packs are installed.
(Security) Incidents Handling: It should be noted that Security Incidents Management (SIM) is different from IT Service Management (ITSM) Incident Management. SIM shall track the incident by opening a security incident ticket. The identified incidents shall be assigned for the resolution to the delegated staff. As per the best practices, all SIM incidents must be followed by a root cause analysis to ensure that not only services are brought back as soon as possible but also the vulnerability is fixed. The incident or event shall be closed after the verification of SIM resolution.
Non-Disclosure Agreement
Non-Disclosure Agreement for Vendor, Contractor and Third Party
WHEREAS:
The Vendor is currently in discussions for the possible supply of products or services to Norconsult relates to non-disclosure of certain confidential information for the purpose of exploring a potential business relationship between the parties (the “Permitted Purpose”). In each case, the party disclosing the information is the “Disclosing Party” and the party receiving the information is a “Receiving Party”.
In consideration of the mutual covenants and agreements hereinafter set forth, the adequacy of which are acknowledged, the parties agree as follows:
1. “Confidential Information” will mean any and all tangible and intangible information, whether written, oral or in any other medium, originated by or uniquely within the knowledge of the Disclosing Party and not generally available to third parties. Confidential Information may include, without limitation, any and all trade secrets, financial information, know-how, designs, methodologies, processes, manuals, marketing information, price lists, customer lists, supplier lists, employee information, computer programs, and systems designs.
2. The Receiving Party will keep the Confidential Information in strict confidence, using the same standard of care as it does with respect to its own Confidential Information, but in no event less than a reasonable degree of care. The Receiving Party will permit only those of its employees, agents, representatives, attorneys, consultants, and financial advisors access to the Confidential Information who has a bonafide need to know in connection with the Permitted Purpose, provided that all such persons must be required to comply with the terms of this Agreement with respect to such Confidential Information.
3. Confidential Information will not include any information that the Receiving Party can demonstrate:
· Was publicly known at the time of disclosure by the Disclosing Party, or becomes publicly known through no fault of the Receiving Party;
· Was rightfully received from a third party without a duty of confidentiality.
· is already known to the Receiving Party at the time of receiving such Confidential Information or is independently developed by the Receiving Party without reference to the Confidential Information.
· is permitted to be disclosed by written consent of the Disclosing Party; or;
· is required to be disclosed by an order of a governmental agency, legislative body or court of competent jurisdiction; provided that the Receiving Party provides the Disclosing Part with prompt notice of such requirement, so that the Disclosing Party may seek an appropriate protective order and/or waive compliance with this Agreement.
4. Disclosure by the Disclosing Party of Confidential Information does not constitute a warranty that the Confidential Information is accurate, complete, or adequate for the purposes contemplated by the Receiving Party. Confidential Information is provided “AS IS”.
5. This Agreement shall not be construed to limit either party’s right to independently develop or acquire technology without use of the other party’s Confidential Information. The Disclosing Party acknowledges that the Receiving Party may currently or in the future be developing information internally, or receiving information from other parties, that is similar to the Confidential Information. Accordingly, nothing in this Agreement will be construed as a representation or agreement that the Receiving Party will not develop or have developed for it products, concepts, systems, or techniques that are similar to or compete with the products, concepts, systems, or techniques contemplated by the Confidential Information, provided that the Receiving Party does not violate any of its obligations under this Agreement in connection with such development.
6. This Agreement commence on the date first written above and will continue through the duration of the business relationship between the parties and for a period of three (3) months thereafter, unless terminated by ten (10) days’ written notice. The obligations with respect to the treatment of all Confidential Information that is received under this Agreement shall survive termination and shall remain in effect for a period of three (3) years from the date of first receipt of such Confidential Information.
7. The Confidential Information will remain the exclusive property of the Disclosing Party, and no copies will be made or retained without the written consent of the Disclosing Party.
8. Upon termination of this Agreement or at any time upon written demand by the Disclosing Party, all Confidential Information, together with any copies, memoranda, notes and photographs thereof, will, at the Disclosing Party’s option, be returned or destroyed by the Receiving Party. The return of any Confidential Information will not relieve the Receiving Party of its obligation to maintain the confidentiality of the Confidential Information for the full period contemplated by this Agreement.
9. Neither party has any obligation to enter into any further agreement with the other except as such party in its sole judgment may deem advisable. Neither Party shall be obligated to compensate the other for exchanging any information under this Agreement.
10. This Agreement contains the entire understanding and agreement of the parties with respect to the disclosure of the Confidential Information and supersedes all prior agreements and discussions concerning the subject matter hereof, whether oral or written. This Agreement may not be modified or amended except in a writing executed by both parties. This Agreement will be binding upon the successors and assigns of each party.
11. This Agreement will be governed by and interpreted in accordance with the local, national and international laws, without regard to its principles of conflicts of law. The parties agree that a breach of this Agreement is likely to cause irreparable harm to the Disclosing Party for which money damages alone would be an inadequate remedy. Accordingly, the parties will be entitled to specific performance and injunctive or other equitable relief as a remedy for breaches of this Agreement.
12. If any provision of this Agreement is held illegal or unenforceable by any court of competent jurisdiction, such provision will be deemed separable from the remaining provisions hereof.
13. Vendor will not make any copies or otherwise reproduce any material that contains the confidential information.
IN WITNESS WHEREOF, the parties hereto have caused this Agreement to be executed by their respective duly authorized representatives as a contract under seal as of the date first set forth above.